The cybersecurity industry is filled with terms. To stay fluent, one must stay abreast of these terms and their definitions. If your security partner informs you about activity within your environment, you will need to speak their language. One question we often hear is, “what is the difference between a cybersecurity event and an incident?”
Cybersecurity event and incident are both terms that describe the activity in your technology environment. These terms are similar and often confused. In this blog, we will define both terms so you can speak fluently about your cybersecurity.

What Is a Security Event?
A security event is a change in the normal behavior of a given system, process, environment or workflow.
In other words: when something happens, it’s an event.
An event can be either positive or negative. An average organization experiences thousands of events every day. These cybersecurity events can be as small as an email, or as large as an update to your firewalls.
Examples of a cybersecurity event:
- An employee flags a suspicious email.
- Someone downloads software (authorized or unauthorized) to a company device.
- A security lapse occurs due to a server outage.
What Is an Alert?
An alert is a notification of a cybersecurity event. (Or, sometimes, a series of events.) You can work with your security provider to determine which types of events you want to monitor with alerts. Depending on your Security Information and Event Management (SIEM) software and support, you can send alerts to any relevant parties who need to take action.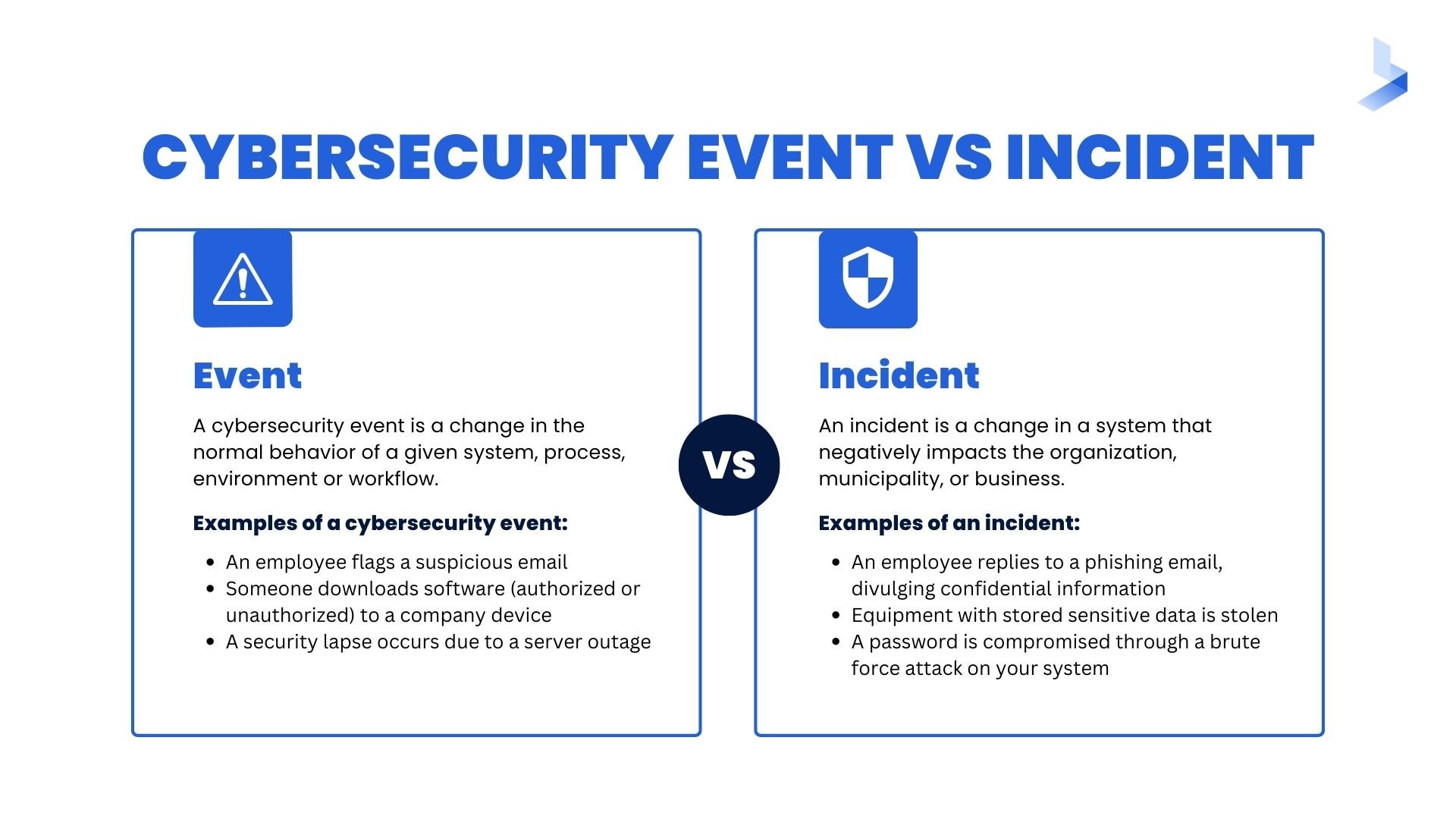
What Is a Security Incident?
A security incident is a change in a system that negatively impacts the organization, municipality, or business. For example, an incident might take place when a cyber attack occurs.
Note: an attempted breach is not the same as an actual breach. This means, if you count breach attempts as incidents, you may have more incidents than what actually occurred. This mistake creates white noise and alarm fatigue. It also makes the collected incident data less valuable.
Examples of a cybersecurity incident:
- An employee replies to a phishing email, divulging confidential information.
- Equipment with stored sensitive data is stolen.
- A password is compromised through a brute force attack on your system.
| Related Reading: What is an Example of an Incident? |
Security Incident vs Event: What's the Difference?
All security incidents are events, but not all events are incidents.
A cybersecurity event can include a broad range of factors that affect an organization. Security events happen all the time, with hundreds, thousands and even millions occurring each day. An event may need examination to determine whether it poses a security risk or needs documentation. With the extensive amount of events that occur in one day, automated tools like SIEM software are often used to select which ones require attention.
Incidents refer to the more specific events that cause harm to your environment. Security incidents typically happen less often than cybersecurity events.
A security incident always has consequences for the organization. If an event causes a data or privacy breach, it immediately gets classified as an incident. Incidents must get identified, recorded, and remediated. This is why monitoring security events is so important. Organizations must take a proactive approach to lookout for events that could cause serious problems.
How to Handle Security Events and Incidents
Cybersecurity events and incidents are handled in different ways.
Dealing with an incident is more urgent than dealing with an event. However, steps still exist to help respond to events. For example, you might:
- Run scans to detect any viruses or malware.
- Review files and folders to check for suspicious activity.
- Monitor accounts and credentials for unauthorized changes.
- Perform a traffic analysis.
Having the right cybersecurity event incident management system is essential. Manually dealing with the number of events that occur in one day isn’t practical.
An automated system filters out the events that aren’t important. Then, the system compares the events to your business’ everyday activity. This allows you to turn your attention to the events and incidents that matter.
However, these systems cannot run on their own. Both systems need configuration and maintenance to stay effective.
Some organizations have the staff and resources to manage these operations in-house. Others outsource this work to a managed service provider that operates their security systems for them.
Have A Security Incident Response Plan
When dealing with an incident, you need a security incident response plan. An incident response plan outlines the steps you need to take when an incident occurs.
A security incident response includes a number of different variables. Variables like, who should take care of which tasks and how to respond to prevent future incidents.
When responding to a security incident, you need to identify any threats and take steps to contain any infections. After eradicating these threats, it’s important to recover any affected systems. Finally, perform a review to see if there are any lessons that can be learned.
Once an incident has been flagged, the goal is to resolve it as quickly as possible. Sometimes a temporary fix is required until a more permanent solution is implemented. The most important goal is to limit any damage and to prevent the problem from getting worse.
You can outsource your incident management, but it’s important to remember that an incident can affect an organization in many ways. Everyone should know their role in the resolution. It’s helpful if all employees know how to respond when an incident occurs. For example, you might need your customer service representatives to let customers know about an issue that is affecting operations.
If you do partner with a security expert, be sure they understand your environment, your needs, and the way you do business. A great cybersecurity expert will monitor all the events on your system and alert you to any troubling. They will also resolve any incidents before they cause harm to your organization.
Ready to learn more about BitLyft Cybersecurity? Sign up for a free demo, and we’ll schedule a short conversation to learn more about how we can help you.









