Cybersecurity Solutions for Higher Education Institutions
THE STATE OF CYBERSECURITY IN HIGHER EDUCATION
Educational institutions are faced with ever increasing pressure to adopt new technology to support the digital learning spree, all while being asked to keep it secure with a shortage of cybersecurity professionals.
Compliance requirements like GLBA, PCI, HIPAA, and FERPA put more pressure on institutions to increase security measures to protect necessary functions of faculty and students.
We equip you with a security operations center to extend your team with tools and resources to provide visibility, detection, and remediation. This way you can stay focused on graduating students and cutting edge research.
Cybersecurity Resources for Colleges and Universities
Higher Ed Institutions Need SIEM Software
Higher education institutions, or HEIs, are responsible for collecting and storing different types of sensitive information. Keeping this information secure is essential. However, the nature of colleges and universities can make these requirements difficult.
Cybersecurity Resources for Colleges and Universities
SOC as a Service Improves Security in Higher Ed
Finding an affordable, efficient solution can be a challenge for higher education institutions. Tight budgets and staffing constraints can make an in-house cybersecurity team ineffective or too expensive to keep in place.
Cybersecurity Resources for Colleges and Universities
How Colleges and Universities Can Maintain GLBA Compliance
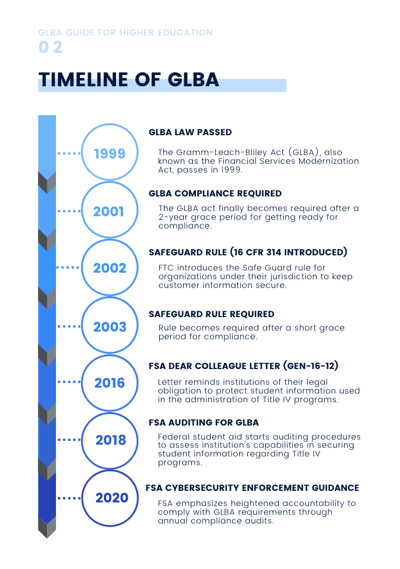
The Gramm-Leach-Bliley Act addresses a variety of consumer financial privacy concerns, including those related to the transfer and safety of personal and financial information of college students. Higher education institutions must follow the regulations outlined by this act or risk facing serious consequences
GLBA Guide for Higher Education: A helpful step by step guide for meeting GLBA compliance requirements.
GLBA rules and regulations have gone through changes throughout the years. In this guide, you'll learn a short history of GLBA changes and why it matters now more than ever to ensure you meet compliance.
What's Included:
- Key considerations for GLBA Rules
- Best practices for institutions
- GLBA Compliance Checklist


What Our Partners Say About BitLyft
“Before we had BitLyft helping us, we would spend hours with multiple departments working on each individual account compromise. With the help of BitLyft, we’ve been able to come up with a process that has narrowed that down to reaction before the compromise even happens.”
Higher Education
What Our Partners Say About BitLyft
“Having a partner like BitLyft eases that unsettled feeling in your mind and you can sleep better at night.”
Higher Education
What Our Partners Say About BitLyft
“BitLyft provides that extra set of eyes and expertise we’re not able to have on staff.”
Higher Education
Most websites will list the logos of their clients to help sell their products and services. We don’t believe in using our customers' logos to easily inform threat actors about your tech stack. Your privacy and security matters, even in our marketing. If you’re interested in learning about who we work with, let’s start a conversation.



