Cybersecurity Priced Your Way
At BitLyft, protection fits your budget and your style. True MDR, powered by BitLyft AIR®, delivers top-tier managed security tailored to your needs - no guesswork required.

Basic
$25.99
per user per month
SOC 2 Type 2 Certified
CMMC Level 2 Equivalent
Managed attack surface

Plus
$30.99
per user per month
Offline Protections
AI Driven Threat Detection
Behavioral Analysis

Premium
$38.99
per user per month
Vulnerability scanning for Mac,
Windows, and Linux
Implement privileged access
management
Custom classifiers for sensitive data
types
Billed Monthly or Annually, 12 or 36 Month Commitment, Contact Sales for 36 Month Discounted Commitments. Subject to Minimum Number of Users.
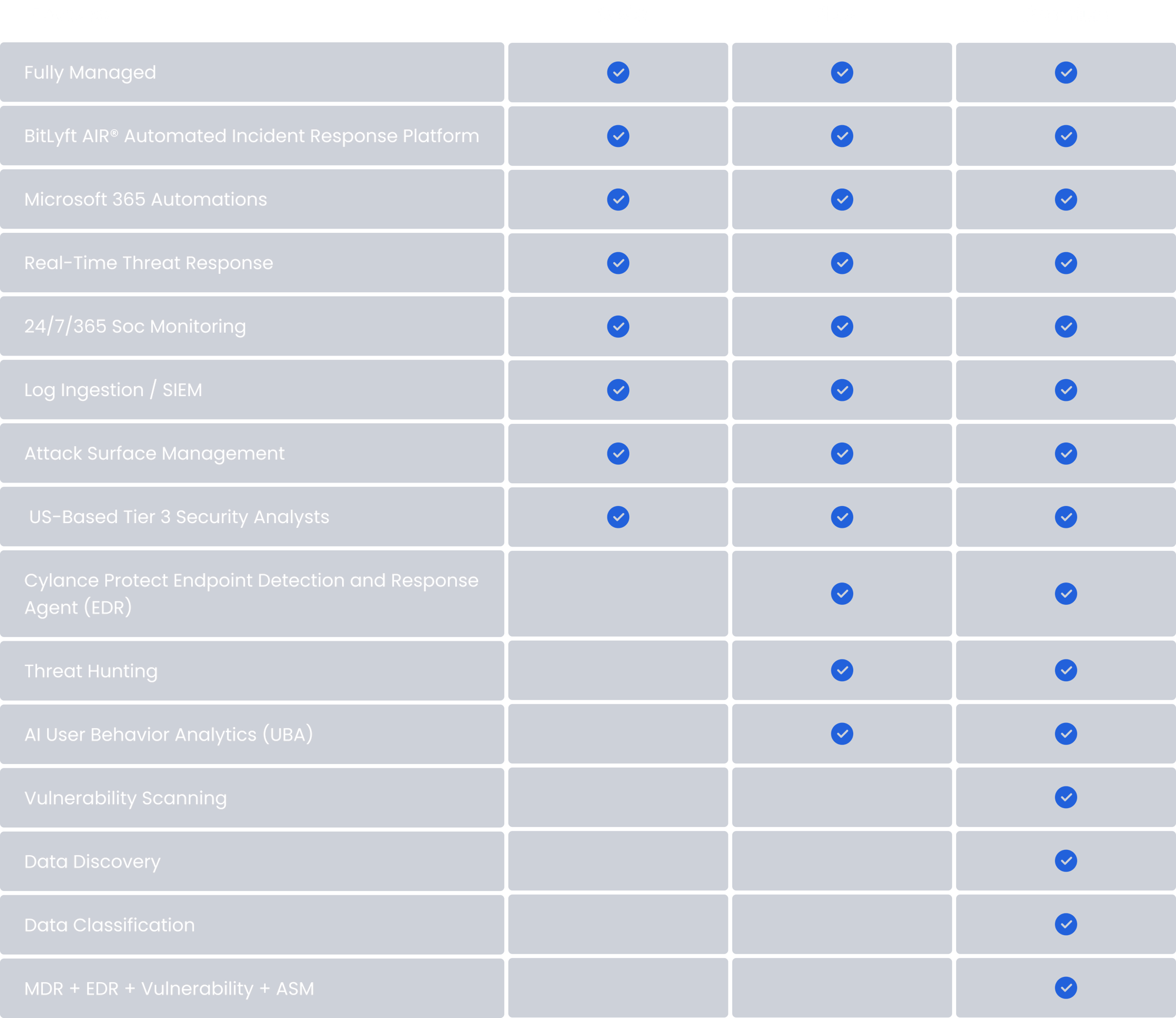
Features
-
Fully Managed
-
BitLyft AIR® Automated Incident Response Platform
-
Microsoft 365 Automations
-
Real-Time Threat Response
-
24/7/365 Soc Monitoring
-
Log Ingestion / SIEM
-
Attack Surface Management
-
US-Based Tier 3 Security Analysts
-
Cylance Protect Endpoint Detection and Response Agent (EDR)
-
Threat Hunting
-
AI User Behavior Analytics (UBA)
-
Vulnerability Scanning
-
Data Discovery
-
Data Classification
-
MDR + EDR + Vulnerability + ASM
Basic
Plus
Premium
Talk To Sales
Frequently Asked Questions
Do you offer vulnerability scanning?
Yes, we can include vulnerability scanning a'la cart. Pricing is based on the number of devices and frequency.
Is there an annual contract?
Our service is typically based on annual contracts paid monthly. Contact us for further pricing discounts for longer-term contracts.
What is the threat feed sync?
We utilize our Central Threat Intelligence (CTI) to curate a contextualized and validated threat feed. This is sourced from users on our platform, as well as OSINT and other validated threat sources to provide proactive protection.
Are there any professional service onboarding fees?
Our professional service onboarding fees are competitive with the industry. In order to give an accurate setup fee, we will need to do a scoping call to understand the scale and complexity of your environment.
Is there really unlimited automation?
Yes. We are interested in keeping mean time to detection (MTTD) and mean time to remediation (MTTR) as quick as possible through automation. We'll set up automations that make the most sense for your unique environment.
Does BitLyft offer a Partnership Program?
Yes, BitLyft proudly offers a comprehensive partnership program. We collaborate with businesses to deliver top-tier cybersecurity solutions and foster mutual growth. Explore partnership opportunities here.
Ready to Secure Your Business?
True MDR, Powered by BitLyft AIR®, gives you fully managed security with the flexibility to scale.
What’s included in True MDR Basic
Get started with a rock-solid foundation—everything you need for essential managed security:
BitLyft Managed Security Services
-
Fully Managed Offering
-
Managed Attack Surface
-
Security Operations Center
24/7/365 monitoring, management of the SIEM Platform, and mitigation of emerging threats -
Components, including alarm tuning and any needed custom parser creation
-
Central Threat Intelligence data feed
-
Reporting and dashboards
-
Unified Logging from every source
-
Threat Hunting
-
Incident Response
-
Network Detection + Response
-
M365 Detection + Response
-
Microsoft Azure Detection + Response
-
AWS Detection + Response
-
Endpoint Detection + Response
-
Firewall Detection + Response
BitLyft AIR® and SIEM Management
-
Optional AWS hosting in GovCloud (CMMC Requirements Met)
-
365 days of data retention
-
USA-based citizens as employees
-
Licensing based on Gb/day
-
Anomaly Detections (AI/ML)
-
Collector Management
-
Compliance + Reporting
-
Correlation Engine
-
Data Enrichment Engine
-
Data Visualization Engine
-
Security Incident Alerts /Triggers
-
Integrated Threat Intelligence, GEO IP Feeds, Lookups
-
Log Archival and Restoration
-
REST API’s
-
Role-based Access Control
-
Malicious Script Trigger Notifications
-
Defined Search and Dashboard Parameters
-
Security Analytics
-
SOAR Integration
-
Technical Support
What’s Included in True MDR Plus
Step up your game—includes everything in Basic, plus extra firepower:
Cylance
-
Fully Managed Offering
-
AI Driven Threat Detection: Uses artificial intelligence to predict and prevent threats
-
Offline Protections: Provides protection even when the endpoint is offline, unlike traditional signature-based solutions
-
Behavioral Analysis: Detects threats based on behavioral patterns rather then relying solely on known signatures
-
Suitable for devices with high-performance needs
-
Prevents reinfection during the recovery process from backups
-
Analysis of files an processes
-
Aggregates data from all endpoints and can send information to a Security and Event Management (SIEM) tool
What’s Included in True MDR Premium
Go all-in—includes everything in Basic and Plus, topped with elite protection:
Data Discovery
-
Fully Managed Offering
-
Custom classifiers to classify your private sensitive data by type
-
High capabilities in image recognition Low volume of false positives with ongoing support for continual fine tuning
-
Visibility in hybrid environments with remote users and cloud applications
-
Executive reporting and easy-to-use query selection for detailed operational reporting
Identity Access Management
-
Implement privileged access management solutions
-
Low volume of false positives with ongoing support for continual fine tuning
-
Cloud access audit capability through Microsoft 365 and Google Workspace
-
Permissions scanning across hybrid environments
-
Simple to understand who can access and who has accessed sensitive data
Risk-Based Vulnerability Management
-
Vulnerability scanning for Mac, Windows, and Linux endpoints
-
Custom classifiers to classify your private sensitive data by type
-
High capabilities in image recognition Low volume of false positives with ongoing support for continual fine tuning
-
Visibility in hybrid environments with remote users and cloud applications
-
Executive reporting and easy-to-use query selection for detailed operational reporting