6 Ways to Drastically Improve Your SIEM Experience

 By
Jason Miller
·
5 minute read
By
Jason Miller
·
5 minute read
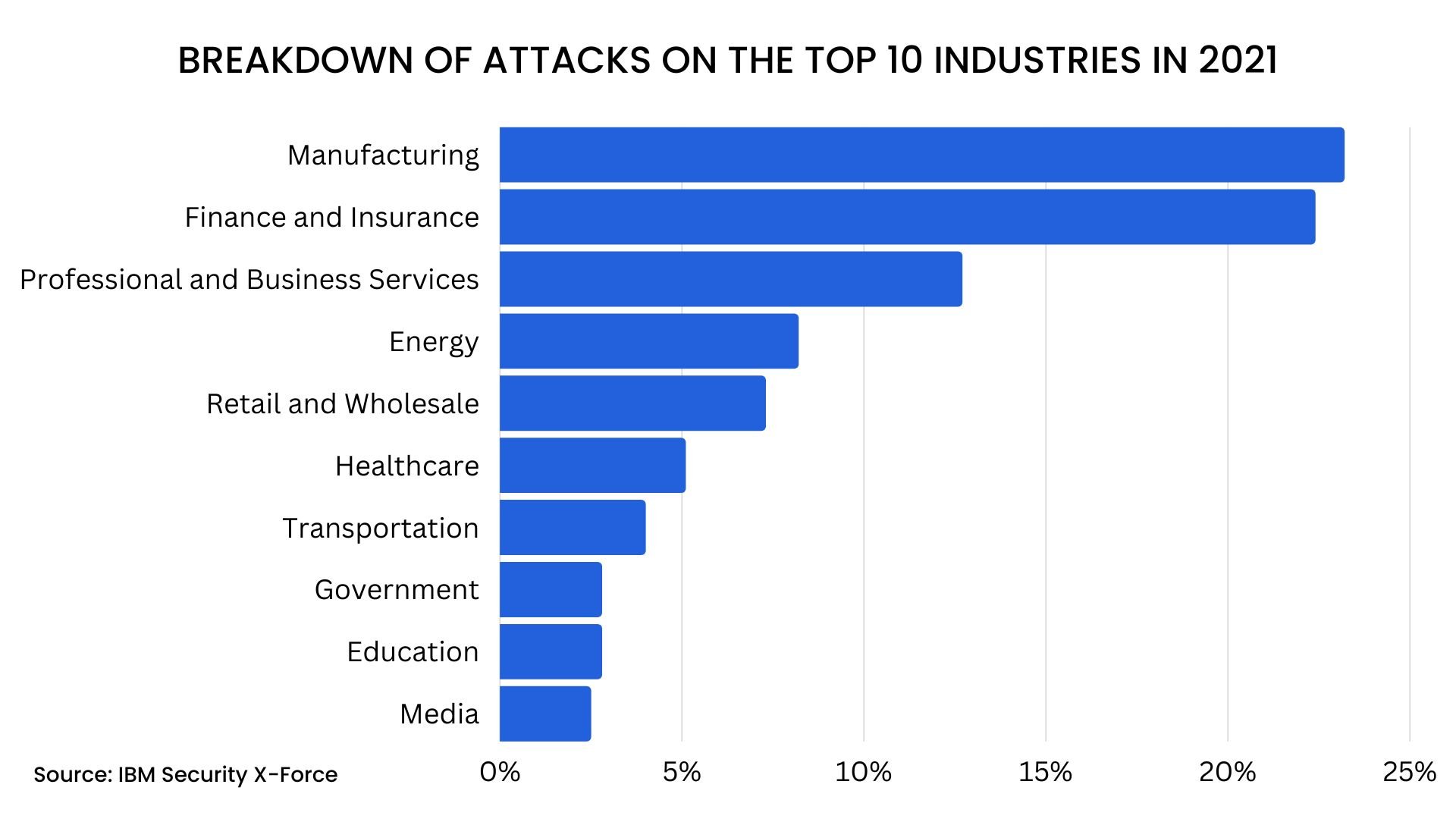
Did you know that cybercriminals tend to target manufacturing, finance, and business services the most?
You need to defend your business from external threats that constantly seek to attack its digital assets. Security information and event management (SIEM) technology can help you do that.
SIEM manages your network and data activity. It provides real-time protection from cyber threats. However, you need to make sure your SIEM is up to date.
Are you looking for ways to improve your SIEM experience? If so, you've come to the right place. In this guide, we'll explain how to make a SIEM that's out of date better.
1. Collect Valuable Data
A SIEM is a powerful tool for keeping your network safe from cyber attacks. However, to maximize its potential, it is important to collect data that is both relevant and actionable.
One way to improve your SIEM experience is to focus on collecting data that will help you identify potential threats. This may include data such as:
- User activity SIEM logging
- System performance data
- Network traffic data
Collecting data from all points in your network is vital for getting the most out of your SIEM experience. Make sure to look for any gaps in your data collection, and plug them with the proper equipment. You should consider all your security devices when expanding your data collection, such as:
- Firewalls
- Antivirus software
- Intrusion prevention systems (IPS)
By doing this, you will have a much more complete picture of activity on your network, allowing you to better detect and respond to potential threats.
One effective approach is to first prioritize the data according to its value. This means identifying the most important indicators of compromise and focusing on collecting data that pertains to those indicators.
2. Analyze What’s Happening
One of the benefits of SIEM software is that it provides visibility into what’s happening on your network. However, simply collecting data is not enough.
You need to make sure that you’re analyzing the data to look for trends and patterns. This will help you to identify potential security threats and take action to mitigate them.
SIEM tools come with a variety of built-in reporting and analytics tools. Make sure that you’re taking advantage of these tools to get the most out of your data. By using the right tools, you can quickly identify trends and anomalies, and take appropriate action to protect your network.
The threat landscape is constantly changing, and new threats are constantly emerging. To ensure that your SIEM solution is effective, it’s important to keep it up to date with the latest information about threats and vulnerabilities. This will help you to quickly identify and respond to new threats as they arise.
3. Build Actionable Alerts
Your SIEM security is only as good as the alerts it generates. If you're constantly inundated with low-quality alerts, you're not going to have a very good experience.
On the other hand, if your alerts are actionable and relevant, you're going to be much more likely to use your SIEM regularly. So how can you build better alerts?
First, start by identifying what kinds of events you want to be alerted about. There's no point in creating an alert for every single event that occurs; you'll just end up with too many false positives.
Events you should keep an eye on include:
- Suspicious user activity
- Abnormal system performance
- Failed login attempts
- Unexpected network traffic
Be sure to test your rules before making them live; nothing is worse than rolling out a new rule and then realizing that it's generating too many false positives.
To test your rules, you can use a SIEM tool's built-in testing functionality, or you can create a test environment that simulates your production environment. Whichever method you choose, make sure that your rules are generating the right alerts before making them live.
However, one of the best ways to do this is through automation. An effective SIEM solution will allow you to automate many of the tasks associated with managing alerts, including:
- Generating alerts
- Assigning alerts to the right people
- Investigating and responding to alerts
By automating these tasks, you can free up your team's time so that they can focus on more important things. And by making sure that your alerts are actionable, you can improve your SIEM experience and make it more likely that you'll use your SIEM solution on a regular basis.
4. Use Good Data
There are a few things you can do to make sure you're getting the most out of your SIEM security solutions.
First, ensure that all of your data sources are properly configured and collect the right data from your SIEM log management. This seems obvious, but it's often overlooked.
In order to do this, you need to have a good understanding of what data you need to collect, and how to configure your data sources to collect that data.
If you're not sure what data you need to collect, start by looking at the types of events that you want to be alerted about.
For each type of event, determine what information would be most useful in investigating that event. Once you have a good understanding of the data you need to collect, you can begin to configure your data sources.
Some common data sources include:
- Firewalls
- Intrusion detection/prevention systems
- Web proxies
- DNS servers
- Event logs
In addition to configuring your data, make sure you have a good understanding of your organization's security posture.
What are your biggest risks? What are your critical assets?
This will help you prioritize the data that's most important to your SIEM.
Finally, don't forget to tune your SIEM regularly. As your organization changes, so does the data that's important to you. By keeping your SIEM up-to-date, you can be sure you're always getting the most out of it.
5. Run Blue Purple and Red Team Exercises Often
Any business that collects and stores sensitive data needs a SIEM system. SIEM provides real-time analysis of security alerts generated by network hardware and applications.
But putting SIEM into effect can be daunting, and even with SIEM in place, many companies are still struggling to keep their data secure. By running these exercises regularly, you can ensure that your SIEM system is always up to the challenge of keeping your data safe.
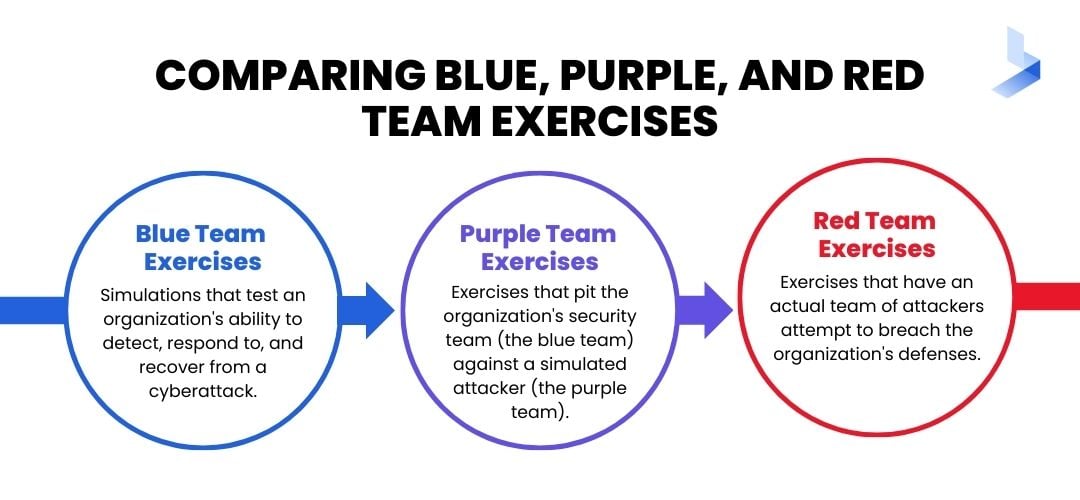
Blue team exercises are simulations that test an organization's ability to detect, respond to, and recover from a cyberattack.
Purple team exercises pit the organization's security team (the blue team) against a simulated attacker (the purple team).
Red team exercises go one step further by having an actual team of attackers attempts to breach the organization's defenses.
All three types of exercises are important for testing different aspects of an organization's security posture. Blue team exercises help to identify gaps in detection and response, purple team exercises help to assess the effectiveness of security controls, and red team exercises provide real-world validation of an organization's defenses.
But putting SIEM into effect can be daunting, and even with SIEM in place, many companies are still struggling to keep their data secure. By running these exercises regularly, you can ensure that your SIEM system is always up to the challenge of keeping your data safe.
6. Make Future Decisions
As the world increasingly relies on digital systems and data, business cybersecurity has become an essential field. While it is important to focus on current threats and cybersecurity best practices, it is also essential to stay ahead of the curve and anticipate future trends. This way, companies and individuals can be proactive in their approach to cybersecurity, rather than reactive.
One major trend that is currently emerging is the move toward outsourcing security operations.
By 24/7 monitoring of digital systems, outsourced SOCs can identify potential threats quickly and mitigate them before they cause damage. This type of proactive approach is becoming more and more common as businesses realize the importance of cybersecurity.
Another big trend that is likely to impact the future of cybersecurity is the increasing use of SIEM log management. This technique allows organizations to track the activity on their systems and identify patterns that could indicate a security threat.
By understanding where threats come from, organizations can be better prepared to protect their systems in the future.
As digital technologies continue to evolve, so too will the landscape of cybersecurity. By staying up-to-date with new trends and developments, companies and individuals can ensure they are better prepared to protect their systems against future threats.
Improve Your SIEM Experience Today
If you want to improve your SIEM experience, there are a few key things you can do. From collecting valuable data to running blue team exercises, these tips will help you get the most out of your SIEM system.
Are you looking to outsource your SIEM solution? Try our demo today and see how we can help you improve your SIEM experience.

