Security: How do Cyber Criminals Attack?

We often need to think about security in the context of both physical security and digital security. The act of a cyber attack is typically not a singular event. Oftentimes we see hackers using multiple levels of probing before they execute their attack. We are going to reference each action that happens during the typical cyber-attack and relate it to the physical security of your home.
The Drive-by Scan:
If you are connected to the internet you are susceptible to all sorts of drive-by attacks and drive-by scans. These scans are an initial phase of data gathering and investigation that are typically being executed by a bot. In the physical realm, this is where a criminal may be driving by in their car looking at your house. They may be looking in the windows or the door and seeing what shape they are in. They are looking to see if you might have a window open that they might be interested in.
On the digital side of that analogy would be where a threat takes and runs a scan against your public IPS or your public assets and understands what ports you have open, or what ports you are having services to that might have SSL certificates or not. The threat then starts to understand a little bit about your footprint from a digital perspective.
The Deeper Scan
At this point, they have garnished enough information about your environment and move on to a deeper investigation. We call this a deeper scan. To relate this to the physical side, this would be where somebody would pull in your driveway. They might even walk up to your door and, and act like they are dropping something off.
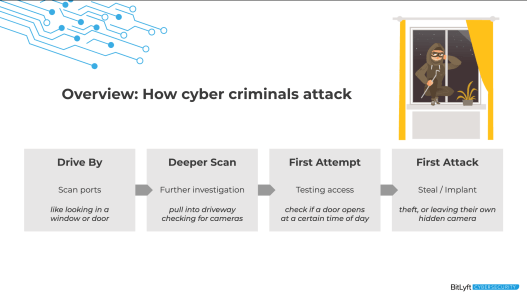
Next is where a bot has done all of its work and a deeper level scan will be started by an actual human being. This is the first time the attacker attempts to access your environment. In the physical realm, this is where we would see somebody walk up to the door, they might even test the door, or walk around your back of your house and they notice that you had a door that was unlocked.
The First Attempt
Everybody, at some point in time, becomes comfortable with their current security configuration. When people begin to become complacent then they start leaving a door or window unlocked when they leave. In the digital realm, this is happening a lot. Not everybody realizes that a criminal hacker can gain access to an environment and you might not even know it. A hacker may gain access to your environment and not even touch anything. They looked around and they got back out, which then tends to lead into the attack.
The First Attack
Over the course of the last week or two, they have noticed that you have made zero changes. They have figured out your configuration that you are comfortable with. The attackers then go in and they start the attack. We have seen this with a prospective client. It was discovered by a digital forensics firm that the attack happened over the course of multiple months. After the first attack, they were able to ransom the environment. The prospective client then either had two choices. They could either pay the ransom or they could do a restore of their data and servers.
