How SaaS Security can Fix Your Blind Spots

 By
Jason Miller
·
3 minute read
By
Jason Miller
·
3 minute read
Detect blind spots in your security can be hard. Because, well, you can’t see them. More businesses of all sizes are relying on Software as a Service (SaaS) applications. This includes things like Cloud storage apps and project management software. These are valuable tools for keeping our day-to-day operations running smoothly, but they can also pose a security risk. We entrust these SaaS applications with a lot of sensitive data, but how do we make sure that it’s protected?

SaaS security recognizes the blind spots created by a SaaS environment and ensures you have the right practices and tools in place to fix them.
Let’s look at how you can use SaaS security to ensure that your organization is protected from security risks such as leaking data, unknown gaps, unauthorized access, and malware.
Identify the right SaaS providers
Many of the risks and blind spots created by a SaaS environment happen at the service provider level. They are the ones who determine which security features the application allows. SaaS security is, in part, about creating standards for service providers that allow you to choose from the plethora of applications out there with security in mind.
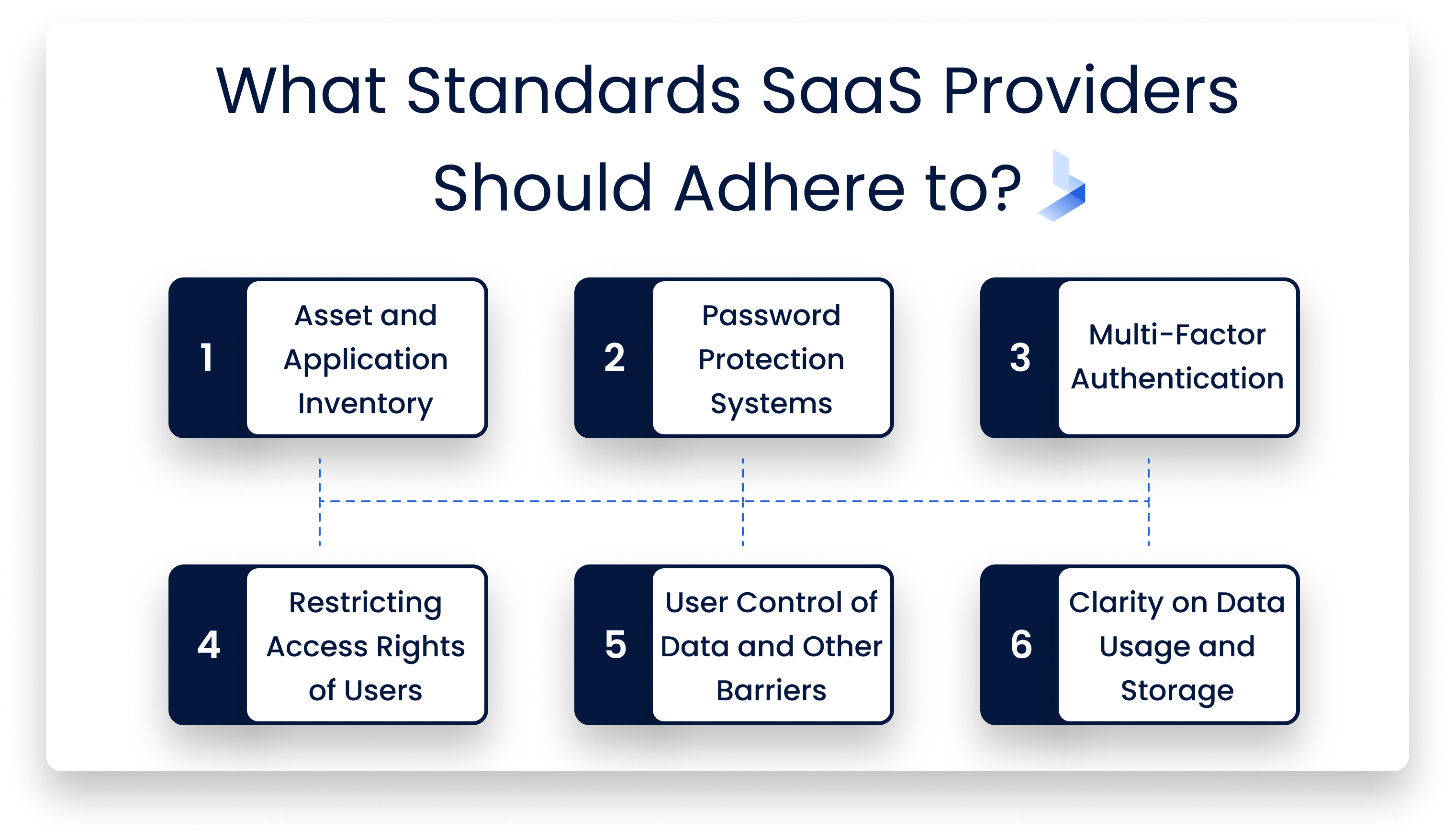
Some of the standards you should adhere include:
- Asset inventory and application inventory
- Good password protection systems
- Multi-factor authentication
- White listing and black listing of user access, geolocation knowledge
- user control such as data protection and accessibility barriers
- clarity on how data is stored, transferred, backed up, and restored
Good SaaS providers should be as clear as possible on how they can help you secure your data.
Control who does what on which app
One of the big blind spots in SaaS is users’ access. You may have trouble determining who has access to do what on each application. SaaS security can help you identify and manage the applications that allow the allocation of different levels of accounts, each with their own access permissions to carry out different processes.
Furthermore, you can create a clear policy on which applications are allowed to be used for any given process and which aren’t. You can prohibit access to unsanctioned applications. This way, you have the tools to maintain usage control and visibility. Cloud access security brokers can help you quickly identify unauthorized SaaS tools, meaning you can replace them with those that offer the access and visibility controls you need.
Diversify your data distribution to limit your risk
SaaS applications don’t offer full visibility or control over how the data is managed within their applications. Therefore it is really important to be mindful of how much sensitive data you keep on any one SaaS service.
SaaS security can involve creating a policy on which data is and isn’t stored through Cloud-based systems. Personal and proprietary data should be stored on local servers, instead, where you have a greater control over the security environment.
Make sure you don’t have more admins than you need
Admin accounts are needed to ensure the level of access that other users have. However, unnecessary admin privileges among your team can provide a lot of risk. Even inadvertently, this level of access allows users to make changes that could make the whole SaaS system more vulnerable, especially since app super admins may not be working in concert with your IT team.
SaaS security can help you better recognize who has which roles in apps, and can put in place granular admin access, so different users have different levels of control based on their need and placement with the IT team. Primarily, only your IT security team should have super admin access. If you’re using tools that don’t allow for granular admin role control, then only those working closely with the IT/security team should have super admin accounts.
Ensure ex-employees don’t retain access to confidential data
Recently, some organizations have faced security threats from ex-employees who have retained access that they should no longer have, allowing them to tamper with, delete, or steal data maliciously.
SaaS security includes a strong off boarding process that allows your IT team to quickly recognize when user access rights need to be changed. Off boarding is a manual, time-consuming process, so it’s essential to ensure multiple people are able to share the load of off boarding.
Implementing the SaaS Security that you need
SaaS apps bring risks. SaaS security mitigates those risks. It includes informing users and the IT team of those vulnerability to create safer policies around their use. It also supplies the right tools to provide added security when needed. For instance, Integrating your SaaS CRM tools with your SIEM solutions can help you better monitor apps you have less control over and find threats more quickly.

If your organization is relying on SaaS software, then you need to start implementing SaaS security as soon as possible. Otherwise, all the blind spots mentioned above pose a significant threat to your business.
Our services aim to provide you with a simple no-nonsense solution to keep your business safe from online threats. If you’d like to learn more, don’t hesitate to get in touch with us today to speak to one of our friendly representatives.
