How to Improve Security with the NIST Cybersecurity Framework

 By
Emily Miller
·
7 minute read
By
Emily Miller
·
7 minute read
Cybersecurity is top of mind for many business owners. As cyberattacks continue to expand and evolve, businesses of all sizes in all industries are at risk. While business owners and CEOs understand the need for adequate cybersecurity, it can be challenging to even know where to begin. Today's modern enterprises depend on cloud-based environments, third-party apps and platforms, and extensive amounts of data. Creating a comprehensive cybersecurity program that addresses all potential risks is intimidating. This is where a trusted framework like the NIST cybersecurity framework comes in.
If you're searching for cybersecurity solutions or preparing for new compliance regulations, you've likely heard of the NIST cybersecurity framework. However, understanding how the framework is designed to improve cybersecurity and exactly how to use it for your unique business needs can be challenging. This guide can help you understand exactly what the NIST cybersecurity framework is, why it can be a benefit to your organization, and how to use the framework to improve your organization's security.
What is the NIST Cybersecurity Framework?
The NIST cybersecurity framework is a guide to help businesses of all sizes develop and implement a strong cybersecurity posture. It was created in response to Executive Order 13636, signed by President Obama in 2013, to help private and public sector entities defend against cyber threats. Version 1.1 of the framework was adopted April, 1 2018.

Designed to act as a roadmap to identify security risks and apply relevant security actions, the framework is a set of processes that can help organizations measure their current cybersecurity system and identify steps for improvement. While implementing the NIST cybersecurity framework is voluntary, it is increasingly becoming an accepted standard by which to measure cybersecurity efforts.
The framework's flexible nature allows it to be used by organizations of all types and sizes to address their unique level of risks and vulnerabilities. In the most basic sense, the NIST cybersecurity framework is an outline of best practices that can be customized to provide industry-recognized cybersecurity solutions that align with the risks and budget of any organization.
Benefits of Implementing the NIST Cybersecurity Framework
The NIST framework is a globally recognized set of instructions that describe how to build a cybersecurity program. It is designed to be customized to the risk level, size, industry, compliance regulations, and needs of each specific business. As such, implementing the NIST cybersecurity framework provides organizations with many benefits.
- It's easy to understand and use. The NIST framework is broken down into organized sections, using non-technical language.
- It offers a way to clearly understand current security risks. In order to protect your network, you need to know the potential dangers. The framework outlines a way to identify all company assets and their relevant risks.
- Your organization can achieve a recognizable standard of cybersecurity. The NIST framework was developed with the experience of IT professionals around the world. As a result, it's used by all types of businesses. The implementation of the framework provides you with a universal language to communicate your cybersecurity efforts with business partners and customers.
- It enables faster business growth. As the NIST framework becomes more widely adopted, your organization's position can be an important part of connecting with clients, suppliers, and vendors. When you've adopted the NIST framework, your organization is less likely to present a supply chain risk.
- Organizations can rapidly address immediate risks. The time for cybersecurity implementation is now. If your organization is in the process of adopting or expanding a cybersecurity solution, evaluating immediate risk can make the difference between falling victim to an attack and preventing one.
- It allows organizations to measure the ROI of cybersecurity investments. The cybersecurity sector is overloaded with tools and solutions that promise effective protection against modern cyberthreats. Yet, when it comes to cybersecurity tools, more is not always better. The ability to evaluate how new tools will affect your current cybersecurity posture can help you avoid poor investments.
Overview of NIST Cybersecurity Framework
The NIST cybersecurity framework is designed to be easy to understand and use. To accomplish this, the framework is divided into three main components (core, implementation tiers, and profiles), which are further broken down into functions, tiers, and organizational profiles. As you learn more about the components of the NIST framework, it becomes easier to use.
Framework Core
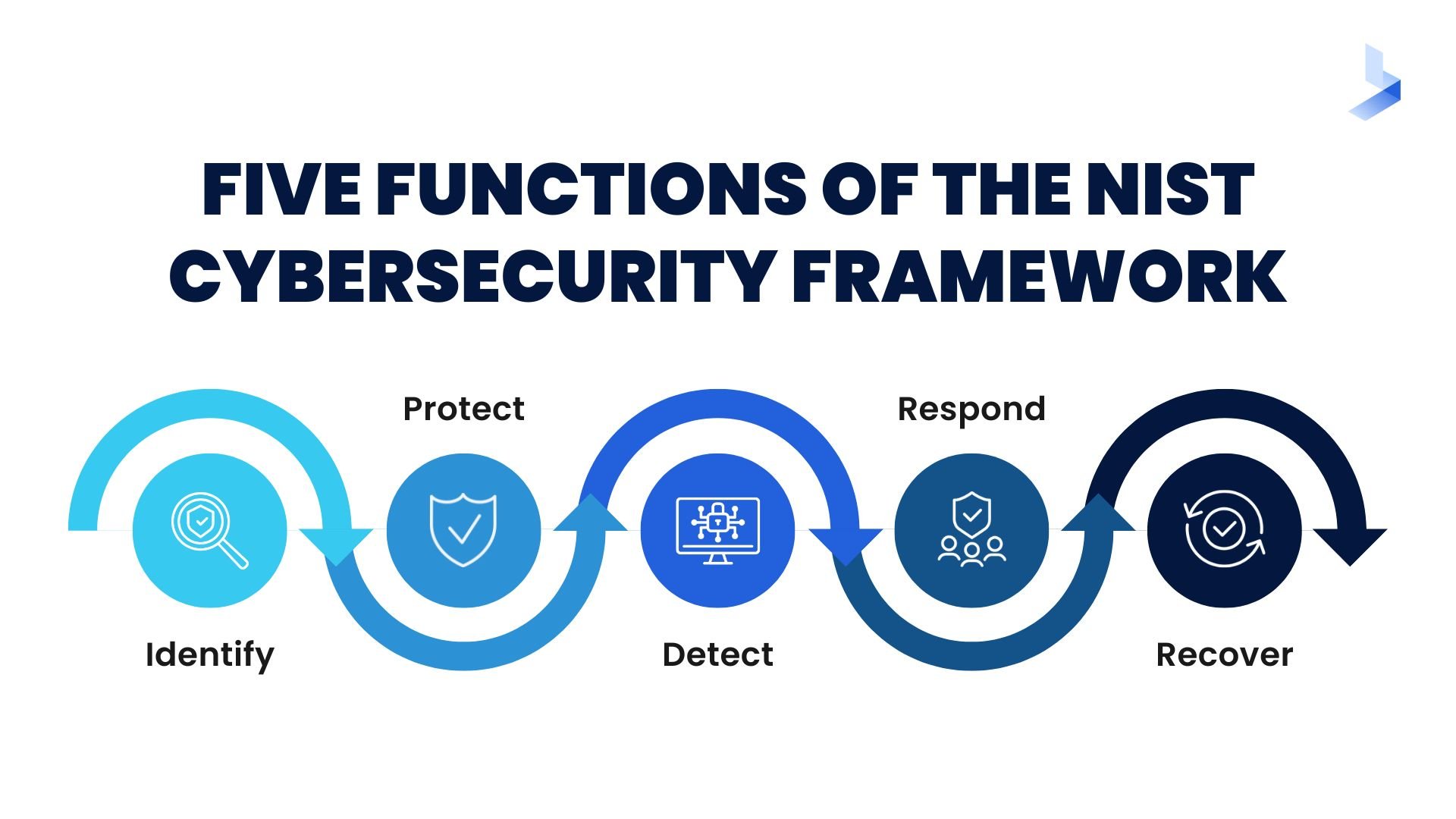
To understand the framework core, it's important to remember that the framework is outcome-based. The framework core provides a set of activities that are tied to cybersecurity objectives or goals. To help organizations understand the process of developing a comprehensive cybersecurity program that eliminates gaps, the core organizes objectives into functions which are further broken down into categories and subcategories.
The five functions of the framework core and their categories include:
Identify
- Asset Management
- Business Environment
- Governance
- Risk Assessment
- Risk Management Strategy
- Supply Chain Risk Management
Protect
- Identity Management and Access Control
- Awareness and Training
- Data Security
- Information Protection Processes & Procedures
- Maintenance
- Protective Technology
Detect
- Anomalies and Events
- Security Continuous Monitoring
- Detection Processes
Respond
- Response Planning
- Communications
- Analysis
- Mitigation
- Improvements
Recover
- Recovery Planning
- Improvements
- Communications
These categories are further broken down into subcategories. The 108 subcategories are outcome-driven statements that apply to the ways an organization can achieve specific objectives.
Framework Profile
Profiles work to help organizations further customize the objectives to their unique needs. They are a way to align organizational requirements and objectives, potential risks, and available resources against the desired outcomes provided in the framework core. Each profile includes the core elements relevant to your organization and your business requirements, risk tolerance, and the resources available to accomplish objectives. The profiles can be altered as necessary. For instance, you may choose to add or remove categories or revise resources in a new profile for a comparison of possible outcomes.
Since the framework is voluntary, there is no set way to use the profiles. Often, they are used to compare a current profile with a target profile. A current profile outlines the cybersecurity outcomes your organization is achieving at present. The target profile describes the actions required to achieve your organization's cybersecurity goals. The completion of both profiles provides a gap assessment of sorts that will help you identify the exact steps you need to take to eliminate vulnerabilities or meet compliance goals.
Framework Implementation Tiers
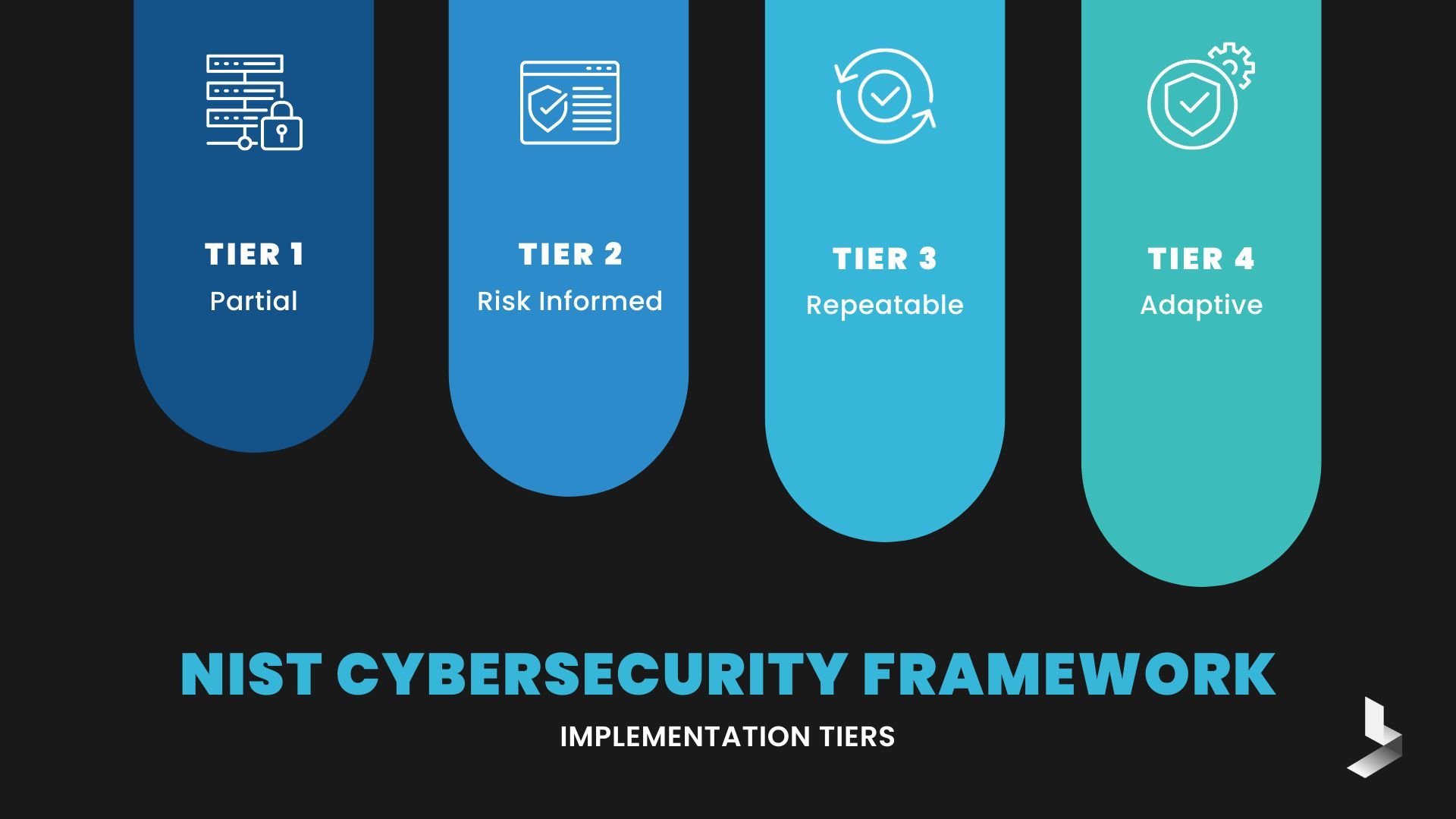
Implementation tiers describe the maturity level of an organization's risk management practices. Since cybersecurity is a constantly evolving endeavor, tiers work to measure progress in reducing cybersecurity risks. There are four tiers that range from partial to adaptive. While Tier 4 is the highest level, it's not necessary for organizations to attempt to reach Tier 4 implementation. Instead, the goal is to assess whether your current activities are appropriate for your regulatory requirements and desired risk level while maintaining a realistic budget.
NIST framework implementation tiers include:
- Tier 1: Partial - Informal risk management and security processes are typically performed in a reactive manner without risk prioritization.
- Tier 2: Risk Informed - Risk management processes are generally approved by management, but not standardized for organization-wide use. While there is a general awareness of risk, partial processes prevent actions from being carried out effectively.
- Tier 3: Repeatable - Organization-wide policies are formalized and repeatable. Tier 3 usually comes with an understanding of the organization's role in its security ecosystem and policies that are routinely updated based on business requirements and the changing threat landscape.
- Tier 4: Adaptive - Organization-wide practices and policies that adapt based on previous and current cybersecurity practices. These policies implement a process of continuous improvement and provide robust security against relevant risks. Tier 4 includes a clear understanding of the company's position in its ecosystem and the ability to share real-time information to help partners avoid risks.
How to Implement the NIST Cybersecurity Framework
For organizations that are unsure about their current cybersecurity posture or are concerned about existing vulnerabilities, the NIST cybersecurity framework provides an ideal place to start. The framework is a risk-management approach to cybersecurity that uses a common language to allow staff at all levels within an organization—and at all points in a supply chain—to develop a shared understanding of their cybersecurity risks. The NIST framework can be used by organizations of all sizes, regardless of industry to clarify their current cybersecurity posture and outline steps for improvement. Taking these steps can help you implement the NIST cybersecurity framework within your organization.
Assess Your Cyber Risk
To establish an effective cybersecurity solution, it's essential to understand your risks, how your current cybersecurity efforts are working, and your cybersecurity goals. Every organization has unique risk levels, assets to protect, and compliance requirements. To conduct a risk assessment, you'll need to identify your company's assets and the policies you use to protect sensitive data. Begin with a list of all devices (including endpoints) on your organizational network. Identify which devices are used to store and share sensitive data. Once you have a clear list of your organization's assets, you can define the current cybersecurity practices used to protect your network. Determine the security effectiveness of organizational policies, so you can map out next steps for improvement.
A risk assessment is a complex task that takes considerable time and effort. More importantly, it requires professionals to view organizational procedures from a completely unbiased perspective to determine areas for improvement. For these reasons, risk assessments are often carried out by third-party cybersecurity professionals.
Creating a Framework Profile
Framework profiles allow organizations to create a detailed plan or roadmap for reducing cybersecurity risk. Use the information derived from your risk assessment to align with the subcategories in the framework core to create a current state profile.
After developing an initial profile that depicts your current state, it's a good idea to create a target profile that will depict your organization's cybersecurity goals. To create a target profile, define mission objectives for specific cybersecurity goals. By identifying mission objectives, you can prioritize cybersecurity processes by risk level. Tailor the NIST framework profile categories as needed to make them relevant to your business objectives. Upon completion of the target profile, it's essential to examine the gap and devise a plan to reach your target profile.
Implementing Security Controls
With a clear picture of where your organization stands and your potential risks, you can create a plan to eliminate vulnerabilities and adopt a comprehensive cybersecurity program that will protect your network. Begin at the top of the framework to establish policies to protect identified assets. These policies should include roles and responsibilities. With clear policies in place, implement actions and tools to protect sensitive data and manage devices. Train users to ensure all employees have a clear understanding of the importance of these new policies and how they're used. As the policies are rolled out, encourage feedback from users and conduct tests to find and repair flaws. Test and update response plans before an attack occurs. Ensure recovery plans are updated to avoid data loss in the event of an attack.
Initial implementation of security controls based on the NIST framework can be a cumbersome process with many steps. However, it's important to remember that the process is a continually evolving and ongoing requirement to tailor your cybersecurity to your business's changing needs.
The NIST cybersecurity framework integrates industry standards and best practices to help all types of organizations manage their cybersecurity risks. The common language used in the framework allows staff at all levels and third-party supply chain partners to develop a shared understanding of cybersecurity risks and how to respond to them.
While the NIST cybersecurity framework is a great place to start when you're implementing a cybersecurity program or working to improve your security efforts, it is not designed to be a replacement for your current cybersecurity efforts. If you're concerned about your cybersecurity posture and how modern cyber risks can affect your organization, BitLyft can help. Get in touchtoday to learn about comprehensive cybersecurity designed to protect every corner of your network.
