Malware: An Evolving Cyber Threat
 By
Emily Miller
·
5 minute read
By
Emily Miller
·
5 minute read
The internet is an increasingly important part of our lives, from how we communicate to how we work and how we shop. Unfortunately, with its many advantages, the internet is also rife with potential threats, particularly in the form of malware.
The statistics surrounding malware should be a cause for concern for any Internet user. With up to 560,000 pieces of malware currently in existence and ransomware attacks occurring every 60 seconds, it is safe to say that the threat of cyber attacks has never been more pertinent.
However, the more you know about malware, the more preventative measures you can take to avoid the often overwhelming costs and damage from an infection.
What is malware?
A contraction of the words “malicious” and “software,” malware is precisely what its name implies: an intrusive form of software designed specifically to cause damage to servers, leak sensitive information, or generally interfere with a device’s privacy or safety in some way. It is often installed without the main user’s consent or knowledge and can remain hidden without detection for quite some time.

What does malware do?
Malware is capable of all sorts of things, though none of them are good. Hackers may be able to use it to wire funds to third parties or even steal personal data and sensitive information like passwords. This may lead to fraud or identity theft. In some cases, though, hackers use malware out of nothing but spite, intending to wipe important data from your computer or restrict your access merely to cause frustration to their victims.
Since malware operates in the background of your processing system, you may notice significant performance issues from your computer or network when infected by malware. This slowness can be an indication that you have caught a virus of some sort.
Seven types of malware
There are various types of malware, each designed to accomplish different goals in different ways. Let’s quickly run through some of the most common forms of malware you might encounter.
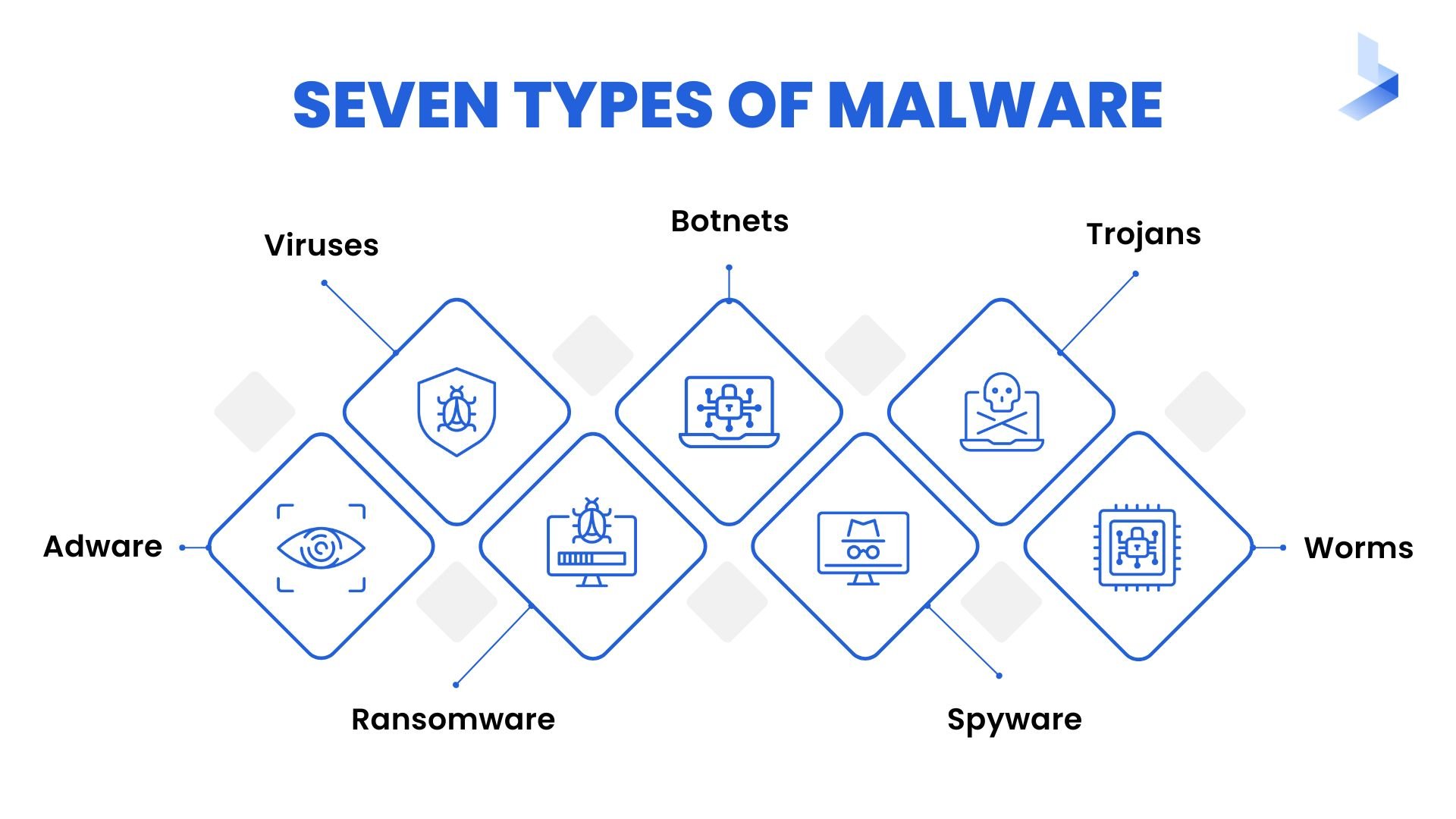
- Viruses: The purpose of a virus is to interrupt your computer or network’s processing. This results in hindering performance issues and sometimes information loss. Typically, a virus will be spread via a file or document that is sent from host to host.
- Botnets: Botnets are used to take over a group of devices, effectively turning them into zombies controlled by a hacker that can be used for some sort of scam or cyberattack. The collection of devices works together to send spam, steal data, or access sensitive information.
- Trojans: Derived from the Ancient Greek story that led to the fall of Troy, Trojans or Trojan horses are a form of malware that appears to be legitimate when you initially download them, only to turn sinister later on. They may claim to perform a useful or even harmless function while in reality, taking control of your device behind the scenes.
- Worms: Worms, sometimes considered a subset of the Trojan horse form of malware, are distinct for their ability to self-replicate and spread to other devices while continuing to wreak havoc on the original host device simultaneously. They require no human activation to begin replicating and spreading.
- Spyware: As its name implies, spyware is designed with the intent of gaining access to personal or sensitive information inside a computer or network. Usually, this information will then be forwarded to a third party for malicious purposes.
- Adware: Adware aims to generate revenue for its developer by forcing advertisements onto your screen, usually via a web browser. These ads may take the form of pop-ups or banners and can be excessive to the point of filling the entire screen.
- Ransomware: While most types of malware operate in the background, ransomware makes its presence known right away. The goal of ransomware is to block a user’s access to a network or device until a sum of money has been paid. The software may also threaten to disclose a user’s personal information if the ransom is not paid.
How does malware work?
Malware can infect your devices in various ways, whether via spam emails, other software bundles or compromised web pages. Once the virus is in your device, it may take over your system or operate quietly in the background to achieve its goals.
How does malware spread?
As we mentioned, some forms of malware can self-replicate and spread on their own. However, the most common ways to spread malware are typical via emails, text messages, USB drives, hacked web pages, or other software. In some cases, an unsuspecting software bundle may contain malware in addition to other programs. These often come from third-party sites or peer-to-peer sharing networks.
How does malware infect systems?
Many forms of malware infect a system by exploiting its vulnerabilities. These vulnerabilities typically exist within the device’s security functions and are essentially a hole in the software that allows malicious software to infiltrate and gain access to the device and its data.
How does malware evade detection?
Malware may utilize different methods to avoid detection once it has successfully infected a device. Let’s take a look at a few examples.
- Timing methods. The malware evades detection by limiting the amount of time it is being analyzed by a virtual sandbox. It may do so in any of the following ways:
- Scheduling execution for a particular date and time.
- Delaying analysis by taking advantage of CPU cycles.
- Stopping analysis by putting the device into an extended sleep.
- User interaction. Some malware may suspend execution when normal interactions between the user and the device occur, such as scrolling, clicking, or moving the mouse. Since the system appears to be running without issue, users may not notice the malware infection slowly taking root behind the scenes.
- Encryption. Parts of the malware are encrypted to avoid detection, making them appear harmless or confusing the analysis by being difficult to understand. The malware then decrypts when it is time to execute.
- Fragmentation. The malware itself may be split up into smaller parts and dispersed. As the sandbox analyzes each individual piece, they appear to be harmless. However, once the pieces are able to reassemble, execution of the malware will occur.
- Suspension. Malware may be able to recognize the presence of a sandbox that could analyze and detect it. If so, it will suspend execution to avoid detection until it has fully infected the host device.
The impact of malware
A malware infection is a very real threat that could negatively impact not only your devices themselves but also your personal security and the security of your larger organization. A new malware attack occurs every 39 seconds on the Internet, meaning that it could happen to any Internet user, including yourself if the proper preventative measures are not in place.

The cost of malware
The cost of repairing a malware infection can be immense, especially in the event of infection via ransomware. You could expect to pay anywhere from thousands to millions in ransom to retrieve control of your devices. Not to mention, some hackers may still refuse to unlock the files after your ransom has been paid, with up to 30% of ransomware victims reporting that they did not regain access despite paying in full.
The damage caused by malware
Aside from the corruption of your devices, malware can also interrupt the daily proceedings of both your personal life and your business. When you try to use your devices, you may be met with extremely slow processing speeds, slowing down your productivity. You may also lose access to important files and suffer from identity theft or fraud as a result of leaked information.
The threat posed by malware
Malware is a threat to the livelihood of any business that relies on the Internet for communication, storage of information, and more. And, in an increasingly global economy, that applies to practically all businesses.
A malware infection can put your business activity on hold for weeks or even months at a time. It can also drastically impact revenue with repair costs or ransom payments, and it may result in the personal information of yourself and your employees falling into malicious hands.
How to avoid malware
Cyberattacks are on the rise, especially in the wake of the pandemic. Attacks utilizing malware and ransomware make up 17% to 19% of cyberattacks, respectively, making them two of the most common threats. In a potentially dangerous online environment, learning to protect yourself from malware infection has never been more essential.
Perhaps the most efficient way to avoid malware is to install a security system on your device. However, there are other preventative measures you can take as well that may give you an added layer of protection against harmful cyberattacks:
- Only download software directly from reliable sources.
- Avoid clicking on any pop-up advertisements or banners.
- Never click links sent via emails or text messages, especially from unknown senders.
- Pay close attention to each step when installing new software.
- Keep computer software updated.
- Install and utilize a firewall.
Conclusion
Knowing the dangers posed by malware, any and all Internet users should proceed with caution when downloading files, opening emails from unknown senders, or clicking ads on web pages. Much like preventing an illness, taking preventative measures like these online is often a safer and more cost-effective solution than repairing damages after malware infection has already occurred.
For more valuable information about malware and other forms of cyber attacks, check out our resources page.
