Network Security Facts and Myths

 By
Emily Miller
·
3 minute read
By
Emily Miller
·
3 minute read
Network security is a key component in any organization’s IT strategy. By definition, the term refers to the practice of preventing and protecting a network from unauthorized intrusions. Network security is a fairly broad term and covers a variety of hardware and software technologies and physical security. Included under the network security umbrella are devices like intrusion detection and prevention systems (IDS/IPS), firewalls, encryption, anti-malware software, etc. The primary purpose of these security systems is to monitor and protect the integrity of a network.
While network security is certainly required in any IT strategy, many myths exist around its function and efficacy. Let’s take a look at some of these common myths and separate fact from fiction.
Myth: Having a network security strategy is enough.
Fact: As mentioned, network security is a key component for any security strategy. However, only employing a few network security devices does not completely protect an environment. These tools, although effective, only perform one function. Many companies will install a network device and assume their entire environment is covered. This is a mistake. They forget to consider the various avenues of entry that a cyber criminal can target. Yes, installing a firewall is effective, but not for an entire network. Yes, installing antivirus software is effective, but again, not enough for an entire network. These tools only cover a very small portion of data that needs protection.
Another mistake organizations frequently make is not considering the amount of time and effort it takes to manage their network security tools once they are installed. For instance, businesses will install an IDS or IPS thinking it will alarm them to any breaches they need to be aware of. Yes, it will alarm them. In fact, it will alarm them for any and every slight movement in their network—critical and non-critical. Have you ever heard of alarm fatigue? Yep. It’s a real thing.
Organizations can receive so many alarms that they either begin to ignore them or run out of the time to check everything. Once alarm fatigue sets in, we’ve actually seen IT personnel turn off alerts just so they can catch up with previous detections. Sometimes, staff even forgets to turn the IDS/IPS back on. At this point, a major threat could go unnoticed. Unfortunately, there is no “set-it-and-forget-it” technology in security. Devices can manage a lot, but you will always need people to double check your work.
Myth: Network security is the same as cybersecurity.
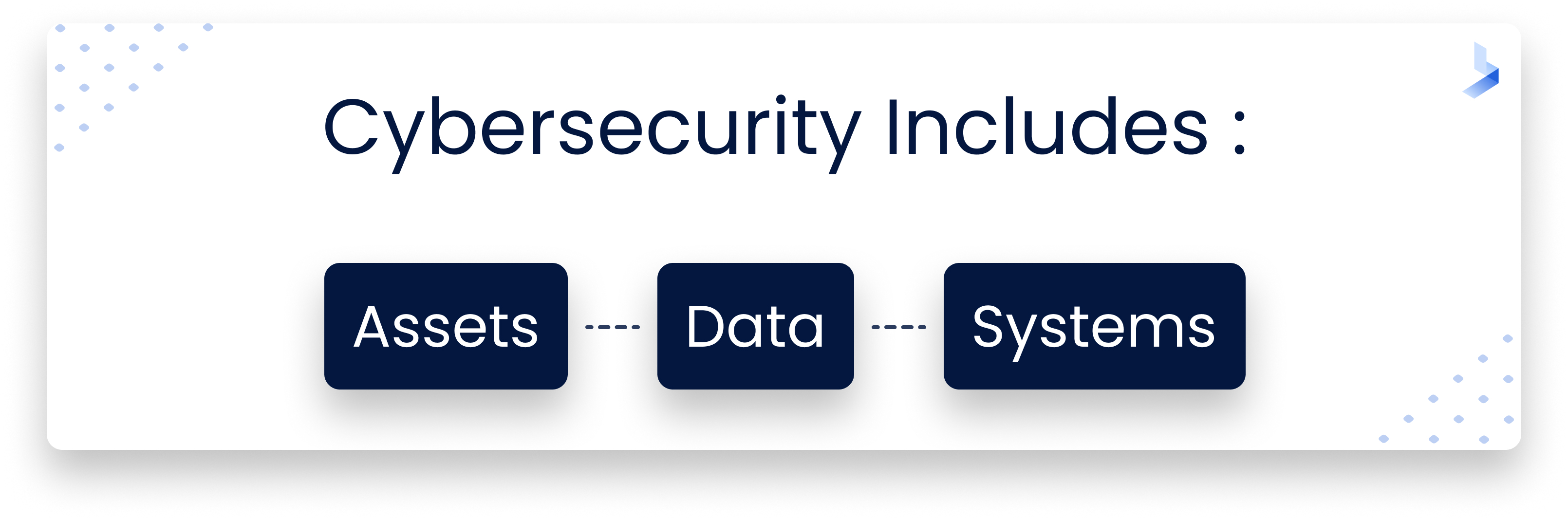
Fact: Network security and cybersecurity are very similar in function. However, there are three characteristics that set them apart. These characteristics include assets, data and systems. In network security, the primary assets covered are those that exist internally. This includes network controls (802.1x), port-based network access control, data transfer, network segmentation and network devices. Network security also monitors the communication between devices and keeps track of where the data is flowing to and from. Finally, it keeps track of who is accessing which networks and through which devices. Again, many organizations stop here. They will implement many of these network security components, but fail to focus on the cybersecurity side.
What’s the difference anyway? The primary difference between network security and cybersecurity is the location of the data it protects. Network security is more internal facing while cybersecurity is more external facing. The goal of cybersecurity is to protect internet-connected devices and apps from external digital attacks. Those digital attacks may include phishing and ransomware. Social engineering is another key component of cybersecurity. While network security is more device focused, cybersecurity is more people focused. Educating users within your network plays a key role in the prevention of cyber attacks. Cyber criminals will employ a number of tactics to try stealing sensitive data. Part of cybersecurity is getting into the minds of these hackers to stop an attack before it even starts.
An integrated approach
As you can see, protecting an organization’s sensitive data requires a multi-faceted approach. One strategy is not enough to cover all the various entry points of a potential network breach. To properly combat cyber attacks and network intrusion, many strategies are needed. A company needs network security, but they also need cybersecurity. And they need a team of highly-skilled professionals to carry out these tasks. If this seems like a lot of responsibility, it is. That’s why companies like BitLyft exist. We help bear the burden of our partners by assisting with our 24/7 network threat monitoring and detection systems. To learn more about our intelligent SOAR platform, contact us today.

