Vulnerability Scanning: Here's Everything You Should Know

 By
Jason Miller
·
10 minute read
By
Jason Miller
·
10 minute read
Hackers work hard. A well-protected organizational network has defenses to protect all endpoints, infrastructure, and devices. Yet, cyberattackers work tirelessly to find flaws in software or organizational processes that can be exploited to allow vulnerability and malicious entry. Vulnerabilities are flaws within a network's software, infrastructure, or processes that can be used by hackers to infiltrate a network. Software developers and cybersecurity professionals examine and test software, devices, and processes to uncover potential weaknesses that could be exploited by bad actors. When these weaknesses are discovered, updates and patches are released to repair the flaw.
Vulnerability scanning is an important part of effective cybersecurity. Understanding how to perform and use vulnerability scans can provide an important layer of protection to keep your network secure. Our introduction to vulnerability scanning will help you understand what vulnerability scans are, why they're important, and how they can be used as a vital part of the way you protect your network against hackers.
What Are Vulnerabilities?
Flaws that hackers or research professionals have exposed are called known vulnerabilities. Thousands of types of software exist, and hundreds of various vulnerabilities are uncovered each month. It is impossible for any IT or security team to manually keep track of all the known vulnerabilities that can be exploited within a company network. For this reason, known vulnerabilities often go undiscovered by network users and get exploited by attackers.
Vulnerability scans check specific parts of your network for flaws that are likely to be exploited by threat actors to gain access or carry out a known type of cyberattack. When used properly, they can provide an important layer of cybersecurity to help keep your company's sensitive data safe. Like most elements of cybersecurity, vulnerability scans are tools that provide the best results when chosen carefully and used the right way. Yet, with a variety of available options and different types of scans, it can be difficult to know what's best for your network.
What Is Vulnerability Scanning?
In the same way as network users, IT professionals, and cybersecurity experts learn about potential vulnerabilities, attackers can find information about potential ways to infiltrate business networks. Even worse, threat actors who wish to breach a system can purchase information about exploiting known vulnerabilities, and even zero-day vulnerabilities on the dark web. Known vulnerabilities provide one of the easiest ways for attackers to gain access to organizational networks to perform high-level cyberattacks once the perimeter is breached. Many known flaws have already been exploited by cybercriminals, making it easy for other criminals to use the same methods of attack.
Vulnerability Scan as a Test
A vulnerability scan is a high-level automated test that searches for known vulnerabilities within your system and reports them. Some vulnerability scans can identify as many as 50,000 known weaknesses that can be exploited by attackers. Vulnerability scans can be performed both inside and outside the network (internally and externally) to reveal different types of weaknesses. External scans are used to identify vulnerabilities that can be accessed from the internet, while internal scans can reveal vulnerabilities that hackers can use to move laterally within the network. A scan might take a few minutes up to hours to complete and will provide a report of known vulnerabilities that need to be addressed. When these scans are performed routinely, they can provide information that helps IT teams and cybersecurity experts protect companies against cyberattacks.
While vulnerability scans are automated tests that can typically be performed without interrupting workflow performance, they are not a magic bullet against all known vulnerabilities. To be effective, vulnerability scanners need to know what to scan and when to perform a search. Scans are completed by a vulnerability scanner that must be optimized to check specific areas of your organizational network for known flaws. When the scan is complete, it provides a logged summary of alerts to be investigated. It's important to remember that vulnerability scans are designed only for the detection of flaws that could be exploited by hackers. After a scan is complete, the results must be used to actively eliminate the vulnerabilities through patches, updates, or other cybersecurity measures.
What Does Vulnerability Scanning Do for Me?
Cyberattackers use a variety of methods to breach systems. Weak passwords, IoT devices, unprotected endpoints, phishing emails, social engineering, etc., are all ways that attackers can take the first step toward launching an attack. Known vulnerabilities are weaknesses that have already been uncovered and made public. These vulnerabilities typically already have a solution like a patch or an update for the software in question. When your network has known vulnerabilities that haven't been addressed, these weaknesses are like an open door for hackers.
Over 8,000 vulnerabilities were published in Q1 of 2022. The US government's National Vulnerability Database (NVD) which is fed by the Common Vulnerabilities and Exposures (CVE) list currently has over 176,000 entries. Considering the deluge of information provided in these lists, slogging through a list of known vulnerabilities to then search for potential risks within a network would be impossible. Vulnerability scanning uses available information about known vulnerabilities to automatically check a specific network for risks and provide a detailed report about flaws that exist. IT teams and cybersecurity professionals can use this information to repair the system in a way that eliminates the risk of these vulnerabilities being exploited by an attacker.
Severities
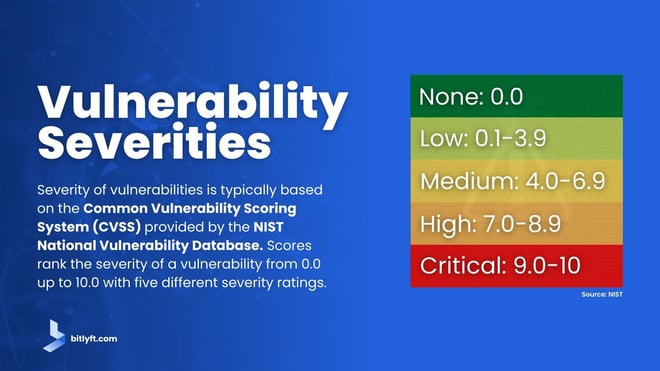
An actionable vulnerability scan report identifies vulnerabilities that could pose a threat to your system, tells you the severity of each vulnerability, and provides remediation suggestions. The severity of vulnerabilities is typically based on the Common Vulnerability Scoring System (CVSS) provided by the NIST National Vulnerability Database. Scores rank the severity of a vulnerability from 0.0 up to 10.0 with five different severity ratings.
- None: 0.0
- Low: 0.1-3.9
- Medium: 4.0-6.9
- High: 7.0-8.9
- Critical: 9.0-10.0
The ratings are based on the factors of exploitability, scope, and impact. Essentially they describe how easily a vulnerability can be exploited, whether it can be spread across the attack surface, and the severity of damage an attack can cause by exploiting the vulnerability. Since the metrics are based on these specific factors, they provide a clear explanation of the dangers of a specific vulnerability. Often, multiple vulnerabilities are revealed with a single scan. The context provided in the report can help IT teams resolve the most critical issues first.
Why are Vulnerability Scans so Important?
Three-fourths of attacks in 2020 took advantage of vulnerabilities that were at least two years old. Many of these flaws could have been detected by vulnerability scans long before they were exploited by attackers. In fact, it's possible that many businesses without sufficient cybersecurity practices in place are unaware of the way even the most public attacks are carried out. Consider the WannaCry attacks that first occurred in 2017. Microsoft was aware of the theft of hacking tools targeted at its operating systems and had released patches months before the attacks occurred. While it might not be a surprise that the majority of organizations failed to patch systems within a couple of months, it's startling to consider that 26% of companies remain vulnerable to WannaCry malware because they have not patched the vulnerability it exploits.
The Victims
Systems that connect to the internet are constantly under attack. Threat actors target companies large and small for a variety of reasons. It ranges from entertainment to an interest in sensitive data or major financial gains. The global interconnections achieved by the internet allow hackers from thousands of miles away to infiltrate your system and launch an expensive attack. Hackers can utilize the dark web to sell, trade, and purchase illegal products. With this, cybercrime has become more attainable for various criminals. Data breach costs rose to $4.24 million in 2021. For many companies, the effects of an attack are so catastrophic that they never recover.
Hackers are aware of the lucrative potential of launching an attack on any business. The dark web allows even those who aren't particularly tech-savvy to purchase information and codes to successfully launch complex attacks. As a result, hackers continually search for networks that provide easy access through unpatched software or legacy systems. The reality is that if you're not performing vulnerability scans on your network, someone else is. For many companies, the results of a vulnerability scan could be the difference between repairing a flaw and recovering from an attack.
Types of Vulnerability Scanners
Like most cybersecurity tools, vulnerability scanners are not a one-size-fits-all solution. Different scans target various areas of your network infrastructure, based on your organizational needs. Some companies are forced to depend on multiple vulnerability scanners to provide a comprehensive view of all the vulnerabilities that exist within a network. To determine the types of vulnerability scanners that best fit your needs, it's important to examine the use cases for each type. There are five basic types of vulnerability scanners.
Network-Based Scanners
A network-based vulnerability scanner is used to search an entire network, including all devices and applications for vulnerabilities. This scanner creates an inventory of devices and the vulnerabilities in each of them. It can be helpful for discovering unknown or unauthorized perimeter points or connections to insecure networks of business partners like vendors and shipping partners.
Host-Based Scanners
These are used for finding vulnerabilities in workstations and servers. It also checks the security configurations and patch history of a server or workstation.
Application Scanners
These are used for scanning apps and websites. They are designed to find vulnerabilities in third-party software and programs utilized within your network environment.
Wireless Scanners
These scanners work to identify vulnerabilities that can allow attackers to easily breach your system. Wireless scanners identify unauthorized access points in a network and find inconsistencies in security configurations.
Database Scanners
Your database houses a wealth of sensitive information. Database scanners identify weak points in a database that could allow attackers to access and change or remove data. Additional database vulnerabilities can provide attackers with ways to control data servers or access other areas of the network through lateral movement that begins at the database.
Some scanners perform multiple types of scans, while others perform a specific task. Beyond the types of scanners that are available, it's important to consider the types of scans that must be performed to provide comprehensive protection for your entire network, including endpoints like remote devices, and IoT devices.
Internal vs. External Vulnerability Scans>
An external vulnerability scan is performed from outside your network and targets IT infrastructure that is exposed to the internet. This includes websites, ports, services, networks, systems, and applications that need to be accessed by external users or customers. External scans can also detect vulnerabilities in perimeter defenses like firewalls.
Internal scans are performed from inside the network and allow you to detect vulnerabilities that leave you susceptible to damage once an attacker breaches the network. Internal scans can help detect vulnerabilities that can be exploited by insider threats or hackers or malware that has already made it past your perimeter defenses. Many modern attacks begin with a perimeter breach that allows an attacker to move discreetly through an organizational network to reach sensitive data or a higher level of authority. Internal vulnerabilities make such lateral movement possible.
If you compare the network vulnerabilities to the physical security system of a company, external vulnerabilities are like blind spots left by security cameras or flaws in your alarm system. Internal vulnerabilities are those that would allow an attacker to have access to your company's most expensive assets once inside the building. From this perspective, it's easy to see why internal and external vulnerability scans are both important.
Authenticated vs. Unauthenticated Vulnerability Scans
Also referred to as credentialed or non-credentialed scans refer to the level of credentials required to perform a scan. Unauthenticated scans require no credentials and do not provide trusted access to the systems being scanned. These scans provide more of an outside view and would allow users to detect vulnerabilities in the same way they're detected by potential attackers. However, unauthenticated scans provide a limited view of a network's total vulnerability exposure.
Authenticated scans require users to log in with a specific set of credentials. These scans provide a user's eye view of the environment for a more complete picture of vulnerabilities. Credentialed scans are typically performed by an impartial viewer with no connections to the network (like a third-party professional) for an impartial view of the entire system.
In the same way that both internal and external scans are important, both credentialed and non-credentialed scans have a place in securing your network.
Top Vulnerability Scanning Tools
When it comes to vulnerability scanning tools, there is no shortage of options for organizations to try. However, not all scanners provide the same abilities. To determine the scanners best for your organization, it helps to compare some of the most popular tools available.
Intruder
A top-rated vulnerability scanner, Intruder scans your publicly and privately accessible servers, cloud systems, websites, and endpoint devices. Intruder proactively detects misconfigurations, missing patches, application bugs, and more. A 30-day free trial is available.
Nessus
A widely used open-source vulnerability assessment tool, Nessus detects software flaws, missing patches, malware, and misconfiguration errors across several operating systems. With 450 compliance and configuration templates provided, Nessus is an option that might be best used by experienced security teams.
Acunetix
Although it only scans web-based applications, Acunteix utilizes a multi-threaded scanner that can crawl across hundreds of thousands of pages rapidly and identifies common web server configurations.
Burp Suite
A web vulnerability scanner, Burp Suite performs automated enterprise-wide scans that can check for SQL injection, cross-site scripting, and other vulnerabilities. It is also used for compliance and security audit purposes. Although there is a free version available, the Enterprise Edition is recommended for the best results.
Netsparker
A website scanner, Netsparker utilizes automated web application security scanning capabilities and can be integrated with third-party tools. Since it doesn't have the range of some other products, Netsparker is a better choice for SMBs instead of large enterprises.
How Often Should You Perform a Vulnerability Scan?
It only takes a single vulnerability to allow an attacker to breach your network, and thousands of vulnerabilities are discovered each year. Unfortunately, a vulnerability scan only provides information about the risks that exist when the scan is performed. While current vulnerability data is important, continual scanning would drain resources, slow systems, and generate a significant amount of false positives. Since emerging threats can be exploited during scan gaps, it's recommended that internal and external vulnerability scans routinely. Routine scans can be automated to run on a schedule like once a month or once a quarter. Some organizations are subject to compliance regulations that state how often vulnerability scans must be performed.
Beyond routine scanning, there are other reasons to search for vulnerabilities in your network. For instance, significant network changes could result in the occurrence of new vulnerabilities. After a significant change in your network like adding new servers or system components, upgrading products, adding applications, or altering interfaces, your network should be scanned for vulnerabilities.
It's important to repair flaws to eliminate vulnerabilities after vulnerability scans are performed. After patches or updates are applied, another scan should be performed to ensure the remediation of all vulnerabilities.
Vulnerability Scanning as Part of a Layered Cybersecurity Solution
Cybercrime affects more than 80% of businesses throughout the world today. The rate of cybercrime increases each year and has exploded in recent years due to a variety of factors. The new technology provides ways for businesses to perform more efficiently. It also offers improved ways for hackers to perform illegal actions online. It's estimated that 75.44 billion IoT devices will be installed worldwide by 2025. These devices often have limited security protocols and can act as entry points for attackers to breach a network. Furthermore, cybercrime has become an organized business in which cyber criminals sell and trade various illegal products and services.
Known vulnerabilities provide an easy target for cybercriminals and lucrative dark web-based markets allow more people to learn about these vulnerabilities each year. Routine vulnerability scanning can help your organization take the first steps toward creating a secure perimeter to avoid such breaches. However, vulnerability scans are only a single part of a complete cybersecurity solution.
Modern systems are continually changing. A scan only represents the known vulnerabilities within a set scope of your network environment at the time the scan was performed. While scanning tools perform automated checks for known vulnerabilities, the results of the scan are limited in scope as well as quality depending on how the scanner is optimized and the depth of the database it draws from. Like most cybersecurity tools, effective vulnerability scanners are not one-size-fits-all preconfigured solutions. They are sophisticated tools designed to be optimized to work with unique business networks. It's likely that your vulnerability scanners will need to be optimized by a security expert and scan reports will need to be reviewed by security analysts.
The Solution
Without a comprehensive cybersecurity solution, vulnerability scans can offer a false sense of security that leaves your organization open to attack. Vulnerability scans reveal known flaws and the threat level they can carry based on the ways hackers exploit them. The reports provided by these scans are designed to create a roadmap for improvement to be carried out by cybersecurity experts.
A comprehensive cybersecurity solution uses vulnerability scans alongside tools that constantly monitor your network and provide real-time incident response. At BitLyft, it's our goal to provide customers with a complete cybersecurity solution that offers the same security as an on-prem SOC to keep attackers from reaching your organization's most critical assets. We provide unparalleled protection for organizations of all sizes by delivering the best people and software to remediate most cyberthreats in seconds. BitLyft offers vulnerability scanning as a part of their complete cybersecurity solution, schedule a needs assessment with our team of cybersecurity experts to learn more.

