Why MITRE ATT&CK Is Important for Security

 By
Jason Miller
·
7 minute read
By
Jason Miller
·
7 minute read
The number of ways online attackers can invade and exploit a network is huge and growing. Keeping track of them when planning cybersecurity or diagnosing an attack is a massive task. MITRE recognized this problem and created the ATT&CK knowledge base. The name stands for Adversarial Tactics, Techniques, and Common Knowledge, which explains the gratuitous-looking ampersand.
The focus of ATT&CK is on advanced persistent threats (APTs) — malware that remains active but undetected in a target system for a long time. APTs are often very expensive because the attacker has time to grab large amounts of data. By keeping a low profile, an APT can stay in operation for weeks or months, delivering valuable data to the attacker or performing tasks like mining cryptocurrency or sending spam.
The first version, for internal use, was created in September 2013. The public release in May 2015 was originally specific to Windows. Since then, MITRE has added data for Linux, Mac, and cloud threats. A separate matrix was added for mobile threats in 2017.
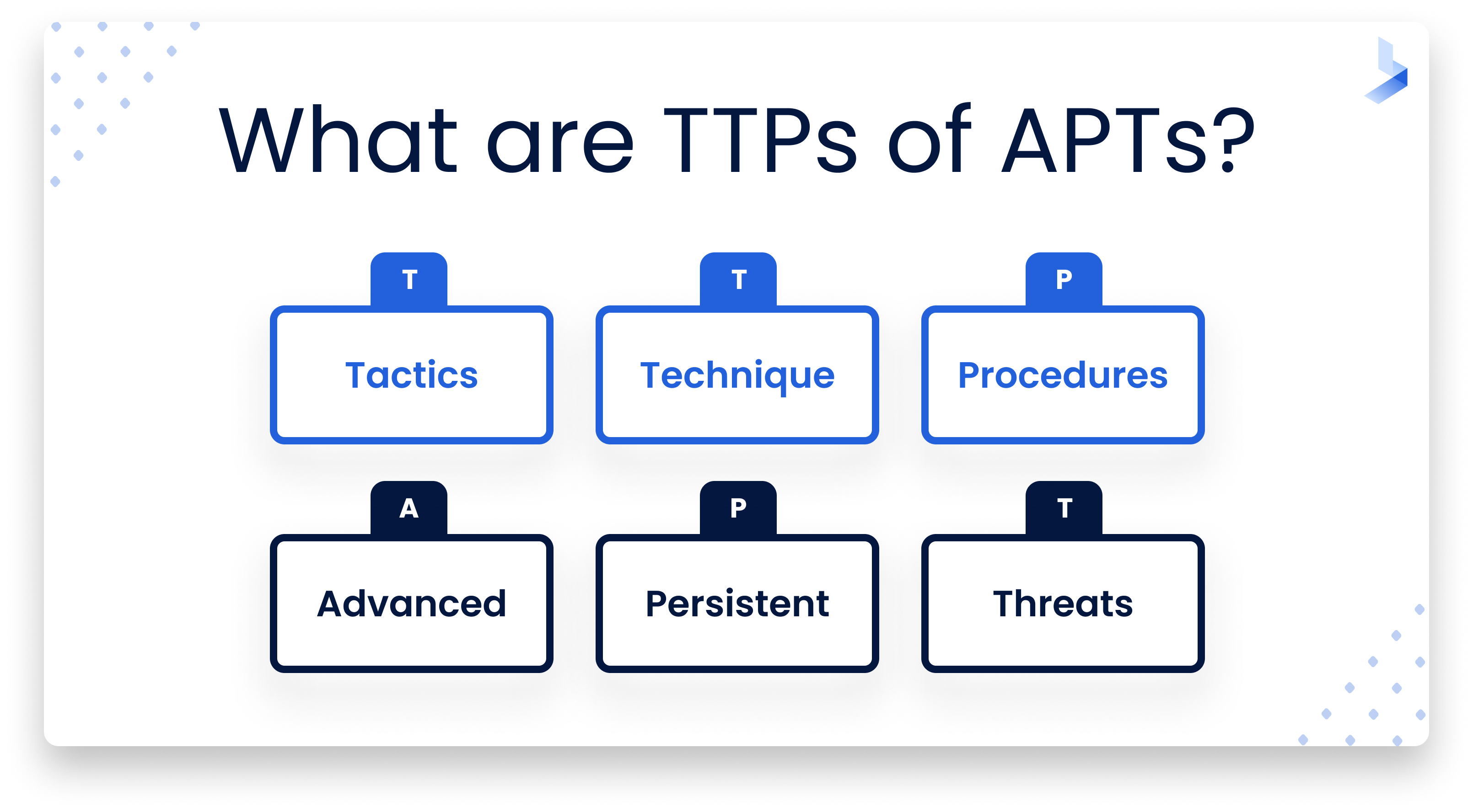
Tactics, techniques, and procedures
The knowledge base categorizes and documents the tactics, techniques, and procedures (TTPs) of APTs. It organizes them in a matrix to aid in grouping and relating them. Navigating the matrix makes it easier to understand how these three levels relate to one another.
- Tactics are objectives that an adversary aims for. Examples include discovering information, persisting in the target network, and exfiltrating data.
- Techniques are the methods used to achieve a tactical goal. The tactic of persistence relies on techniques such as account manipulation, installing logon scripts, and modifying system firmware. Many techniques are divided into sub-techniques.
- Procedures are specific actions for implementing techniques. They generally refer to software designed to carry the technique out.
Start by familiarizing yourself with the tactics. The number of techniques is huge, especially counting all the sub-techniques, and browsing through all of them can be bewildering. Once you have an idea of what the tactics mean, you can better orient yourself through the lower levels.
There are three matrices in the knowledge base. The most widely used is the Enterprise matrix. In addition, MITRE supplies a Mobile matrix and a PRE-ATT&CK matrix. The latter deals with tactics and techniques which lead up to compromising a target system.
A structured approach
The information in ATT&CK is compiled from many sources. The primary sources are generally written reports, which are thorough but require careful reading to understand. Different reports may talk about the same threats under different names. ATT&CK doesn’t replace these reports, but it provides a more structured way to describe their central features.
Identifying a threat by its name or names and its key features makes it easier to determine which parts of the literature are relevant to it.
Approaching from the other end, the ATT&CK matrix aids in identifying a tactic or technique and listing the threats that use it. This allows for a better organized start when tracking down the source of a detected behavior.
Still another approach is to start from a technique and find out what other techniques are associated with it. Procedures may involve more than one technique, and if analysis discovers one of them, it’s a good idea to look for associated ones. An APT uses multiple tactics in its effort to acquire data, conceal itself, and acquire additional footholds.
RELATED: MITRE ATT&CK, SIEM, and SOC for Better Security
ATT&CK Navigator
The information is available in several different ways. The easiest to examine casually, but still a powerful tool, is the ATT&CK Navigator, which lets you view the tactics and techniques as a table. The Enterprise ATT&CK Navigator has 11 columns, one for each of the tactics and many techniques under them. It’s a somewhat complex Web application, and it will take some time to get comfortable with it.
The toolbar gives you options for viewing and filtering techniques. You can, for instance, view only the ones that apply to a particular platform. In addition, you can assign scores and comments to items. A search function helps to find techniques.
Some techniques have a gray bar to their right. Clicking on this brings up a list of sub-techniques. It may not be obvious, but right-clicking on a technique or sub-technique brings up a menu. You can select the item, add it to an existing selected set, or remove it from the selection. You can also choose “View technique” or “View tactic” and open a page of information on the item.
The changes that you make aren’t persistent in the browser. Do whatever work you need in one session and then export it. The navigator supports these export options:
- JSON data. When you save a layer this way, you can import it to the Navigator later on. JSON is a convenient format for manipulation with custom tools.
- Excel spreadsheet. This is useful for handling the data offline. Scores aren’t exported.
- SVG image. This view-only option is useful for presentations.
Layers are a highly useful feature. You can have as many as 10 open at once. Layers can be created from existing ones in the Navigator, or they can be imported from saved JSON files.
A new layer can be a combination of existing layers. This is where you really see the power of the scoring feature. Items on each layer can get a score, and a combination layer can assign scores as arithmetic functions. Each score value can have a distinct color as a visualization aid. By putting these features together, you could create a combined layer that shows selected techniques from the first layer in red, ones from the second layer in blue, and ones that appear in both layers in yellow. If it helps, you can devise even more complex combinations with color visualizations.
Accessing ATT&CK as STIX data
Impressive as the navigator is, it’s best suited for manual work, not for integration with other tools. Another way to access the information is through the TAXII 2.0 server. The server uses a REST API and returns data in STIX 2.1 format. STIX is a specialization of JSON for cyber threat intelligence.
TAXII is suited for making MITRE ATT&CK data available to tools for further processing. A front end can support queries to suit a network’s needs. It can convert the data to any required format and move data into a threat intelligence system.
The STIX data is stored in a GitHub repository and can be accessed directly without using TAXII. A Python code library is available for creating access scripts.
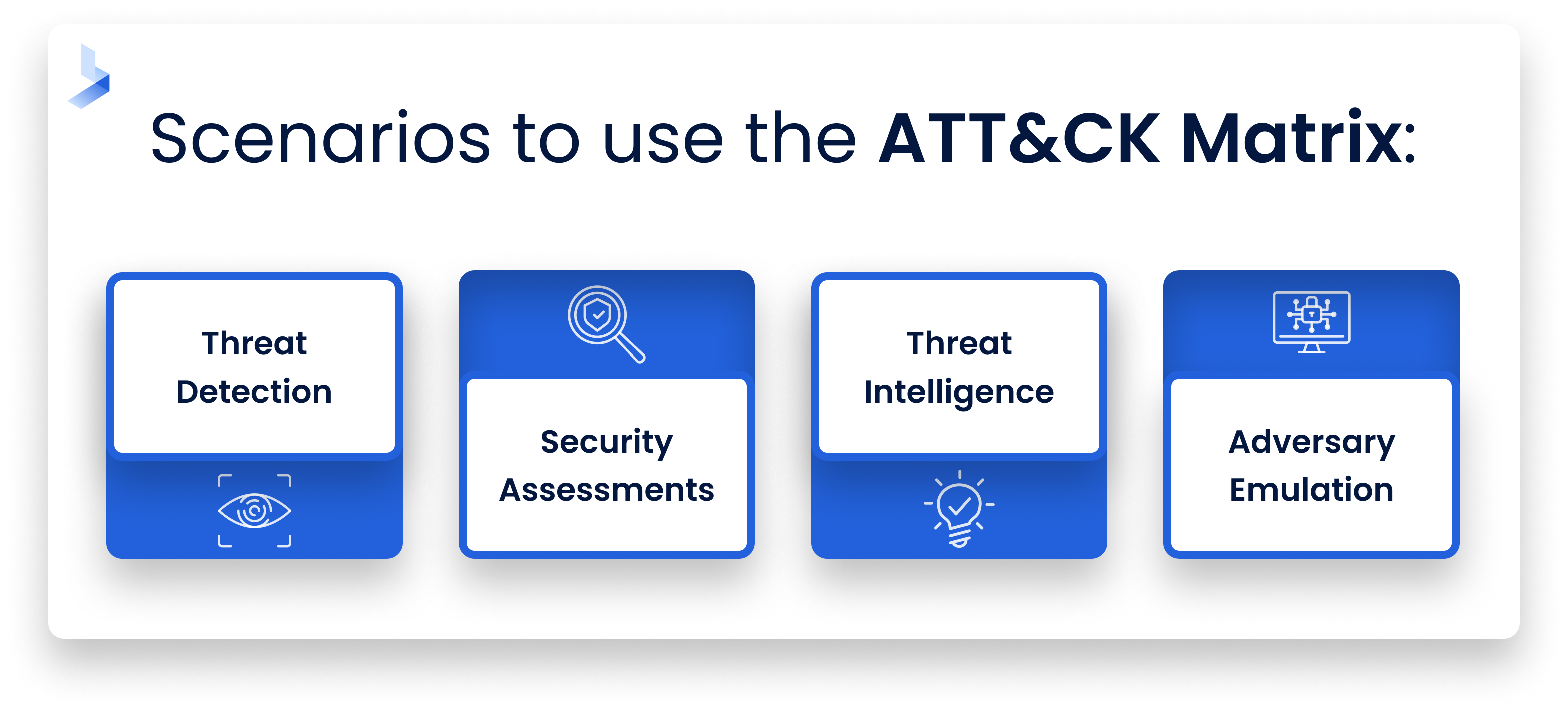
Scenarios for using the ATT&CK Matrix
That’s a lot of power, but how do you use it in practice? ATT&CK is valuable for prevention and mitigation. Let’s look at some use cases.
Threat detection
APTs are, by design, hard to detect. Ongoing monitoring, logging, and analysis are necessary in order to catch APTs promptly. The ATT&CK data helps in designing the process.
At one time, the preferred way to detect threats was by signature. Distinctive bit patterns or file names indicated the presence of specific threats. As the variety of attacks has grown and new ones appear more frequently, this approach is no longer sufficient. The creators of a threat change its details over time so its signature isn’t consistent.
A behavior-based approach will catch more kinds of malicious activity. ATT&CK enumerates techniques and describes data collection methods that can identify them. This information provides a basis for setting up data collection, deploying tools, and creating scripts to identify and report threats.
If analysis narrows down the threat to a particular piece of malware, the Software page will have additional information on it. This information includes the techniques it uses, groups that use it, and references providing more information.
Not every behavior described in the matrix constitutes a threat. Analysis needs to keep false positives to a minimum while not missing actual threats. This requires fine-tuning which is specific to the systems being protected.
Security assessments
The bigger picture in cybersecurity includes measuring the quality of your defenses and identifying gaps. One way to do this is to define an ideal security posture and measure its differences from the current state. ATT&CK data is valuable in defining this target and enumerating shortcomings.
Looking at the differences one technique at a time is a systematic approach that avoids the feeling of being overwhelmed. It will take time to cover them all, but each step points the way to improvements or confirms the adequacy of the current setup. Not all vulnerabilities are equally important, and you should build a set of priorities rather than addressing everything at once.
The Mitigations page lists actions that can remove threats or prevent them from taking effect. Each mitigation’s individual page lists the techniques which it counters. Some mitigations itemize software that implements them. The lists aren’t exhaustive, and you should do research to choose the best currently available mitigation tools.
Mapping your deployed security processes against ATT&CK techniques is helpful in identifying points where threat detection can improve. Running a comparison periodically identifies new issues that need addressing.
Threat intelligence
Good defense doesn’t just react to attacks. It assesses what the enemy is up to and lets you anticipate where the next attack could come from. ATT&CK provides a list of groups believed to be threat actors. The definition of “group” is broad; it’s a “set of related intrusion activity.” Usually, little is known about a group’s method of operation; it could be a government-run organization, a geographically scattered set of hackers sharing information, or a very active individual. Some groups provide software and services to freelance criminals for a price.
The Groups page includes a search function. Searching on keywords such as “financial,” “government,” and “healthcare” helps to spot groups that could have a special interest in your operations. From there, you can look at their techniques and review your defenses against them.
The Software page covers tools and malware which adversary groups use. Not all of it is malicious as such. Some tools are useful for gathering system information for either benign or hostile purposes. For example, a port scan lets you enumerate your open ports so you can protect them, but an attacker can use the same tool to target its penetration attempts.
Once you have identified a group or software that needs further study, you can look for information on it from other sources. The group page lists the name or names which it’s known by; some groups have many names. Gathering information on them from external sources gives you additional details and perhaps more recent information on their activity.
Attacks can come from many directions, so focusing on one or a few groups while ignoring the rest isn’t a good strategy. However, if a group is currently a major threat in your industry, you need to stay up to date on it.
Adversary emulation
The best defense is a good offense, and sometimes that means offense against your own network to see how well it stands up to the attack. Adversary emulation and penetration testing are related but distinct ways of doing this. Penetration testing focuses on finding weaknesses to target; adversary emulation uses threat intelligence to simulate the attacks that real-world intruders use.
ATT&CK information has clear value in emulating an adversary. After threat intelligence identifies potential attackers of interest, emulating their techniques can show how well a network’s defenses will stand up to them. The emulation, of course, is designed not to harm production systems. It can stop short of harmful actions or run against a test system.
If the test shows that the defense is inadequate, the next step is to improve your defenses and try again. If the protective measures thwart the emulated attack, the process can continue with other adversaries of interest.
Improving your security posture
Cybersecurity is an ongoing process. You need to regularly examine your site’s security posture and identify areas that need improvement. The ATT&CK matrix is valuable for creating and updating a threat intelligence repository. Understanding it thoroughly takes a lot of study and experimentation with various approaches. It’s a serious investment of time to make it an effective part of a security strategy, but the effort is worth it.
The best place to start is with a cybersecurity assessment so that you know how well your current defenses work and identify the highest-priority areas for improvement. Contact us to set up a professional, independent assessment of your systems’ security.
