BC-ware: Protecting Your Business from Business Email Compromise (BEC)

 By
Emily Miller
·
6 minute read
By
Emily Miller
·
6 minute read
Imagine this, you are the finance manager at a Fortune 500 company. You’re getting ready to head out for lunch and you receive an urgent email from the CEO.
Will you transfer $120,000 to the vendor we’ve been working with? Our account is past due, and payment needs to be made before the end of the day.
The email seems legitimate: it contains the company logo, the CEO's signature and it’s even regarding a company you’ve recently worked with. So what do you do? You send over the money. Little do you know, you were just the victim of a Business Email Compromise scam. Your company is out of $120,000. And you? Potentially out of a job.
This is the harsh reality that many businesses face when it comes to Business Email Compromise (BEC) scams. In fact, according to the FBI, BEC scams cost businesses more than $43 billion between June 2016 and December 2021. When you consider the level of sophistication involved in these attacks, it’s no wonder how much money cyber criminals are able to get out of their victims.
%20Stat.jpg?width=1280&height=720&name=Business%20Email%20Compromise%20(BEC)%20Stat.jpg)
In this article, we'll help keep you from becoming the next BEC victim by providing you with a number of best practices for protecting your business from this growing threat.
Understanding Business Email Compromise
Before diving into best practices, it’s important to understand what a business email compromise is and how to spot a potential attack. BEC scams are a type of social engineering attack that targets all types of businesses and organizations. These attacks take advantage of human nature and trust with an email communication that is designed to trick victims into transferring money or sensitive information. BEC scams typically fall into five different categories including: CEO fraud, invoice fraud, vendor email compromise, account compromise and business service scams.
5 Types of BEC Attacks
Despite having the same end goal, each BEC scam comes with its own unique set of characteristics. Familiarizing yourself with the different types of Business Email Compromise is crucial for protecting your organization from these types of attacks.
- CEO Fraud: Like the example used earlier, this type of BEC attack involves hackers impersonating a company's executive, usually the CEO, to request sensitive information or money transfers from employees. This scam is particularly effective because employees often have a high level of trust in their CEO and likely to comply with requests.
- Invoice Fraud: This type of BEC scam involves hackers intercepting and altering invoice payments, directing them to their own accounts. This scam is particularly effective because it can be difficult for employees to detect the alteration. The scammer may also use the company's own branding and logos to make the invoice look legitimate.
- Vendor Email Compromise: This type of BEC scam involves hackers tricking employees into transferring money to a fraudulent vendor by impersonating a legitimate vendor. This scam is particularly effective because vendors are often trusted parties that employees are used to working with.
- Account Compromise: This type of BEC scam involves hackers gaining access to a company's email account, then using that access to request money or sensitive information. This scam is particularly effective because it can be difficult to detect, as the requests may appear to come from a legitimate source.
- Business Services Scams: This type of BEC scam involves hackers tricking employees into transferring money to a fraudulent business service provider. This can happen by phishing emails, phone calls, or online forms that request for personal information or payment.

How to Identify a BEC Scam
When working to prevent a BEC scam, there are several distinguishing factors that can help you identify a scam. Knowing these signs in addition to the general types of BEC scams gives you an additional advantage when working to avoid an attack.
Red flags may include:
- Requests for urgent or unexpected money transfers: BEC scammers often use a sense of urgency to trick employees into transferring money or sensitive information.
- Requests for sensitive information: BEC scammers may ask employees for sensitive information, such as login credentials, social security numbers, or bank account information.
- Requests from unfamiliar or unexpected sources: BEC scammers often impersonate executives, vendors, or other trusted parties.
- Requests for secrecy or confidentiality: BEC scammers may ask employees to keep the request a secret or to avoid discussing it with anyone else.
- Requests that deviate from standard procedures: If a request deviates from standard procedures, it may be a sign that it is a scam.
- Requests that come from free email services: Requests that come from free email services like Gmail, Yahoo, etc.
How to Prevent Business Email Compromise
Preventing BEC scams requires a multi-faceted approach that includes employee education and training, implementing security protocols, creating an incident response plan, and regularly reviewing and updating security measures.
Conduct Employee Trainings

One of the most effective ways to prevent BEC scams is to educate and train employees on how to recognize and respond to potential scams. These trainings should provide information on common red flags of BEC scams, such as urgent or unexpected money transfer requests, requests for sensitive information, and requests from unfamiliar or unexpected sources. Other topics may include phishing, password management, social engineering, and mobile device security.
An organization should conduct cybersecurity trainings for its employees on a regular basis, at least annually. It's important to keep in mind that cybersecurity threats are constantly evolving, so regular training helps keep employees aware of the latest threats and best practices for protecting the company's data and systems. Additionally, it's good practice to provide refresher training or additional training sessions when new technologies or threats arise. This will help ensure that employees are aware of the latest risks and how to mitigate them.
Implement Security Protocols

Implementing security protocols can also help prevent BEC scams. This can include measures such as two-factor authentication, email encryption, and email filters and spam blockers. Additionally, it is important to have an incident response plan in place, so that employees know what to do if they suspect a BEC scam. This should include steps to notify IT and legal department, change all relevant passwords, and contact financial institutions. You can download a free copy of our Major Incident Post-Mortem Template here.
Regularly reviewing and updating security measures is also important to protect a business from BEC scams. This can include assessing the effectiveness of current security protocols, identifying potential vulnerabilities, and implementing new measures as needed. By taking a proactive approach to preventing BEC scams, businesses can reduce the risk of falling victim to these types of attacks.
Use a Strong Privileged Access Management (PAM) Solution

Finally, a strong privileged access management (PAM) solution can help prevent business email compromise by providing an additional layer of security for sensitive information and money transfer requests. PAM solutions typically include features such as multi-factor authentication, role-based access controls, and session monitoring, which can help to prevent unauthorized access to sensitive information and financial systems. For example, by implementing multi-factor authentication, PAM solutions can help to ensure that only authorized users are able to access sensitive information and financial systems, even if they have the correct login credentials.
Additionally, PAM solutions can also help to prevent BEC scams by providing real-time visibility into user activity and detecting suspicious behavior. For example, by monitoring user activity, PAM solutions can detect and alert on patterns of activity that may indicate a BEC scam, such as a request to transfer money to an unfamiliar account. This allows organizations to quickly detect and respond to BEC scams, minimizing the damage caused.
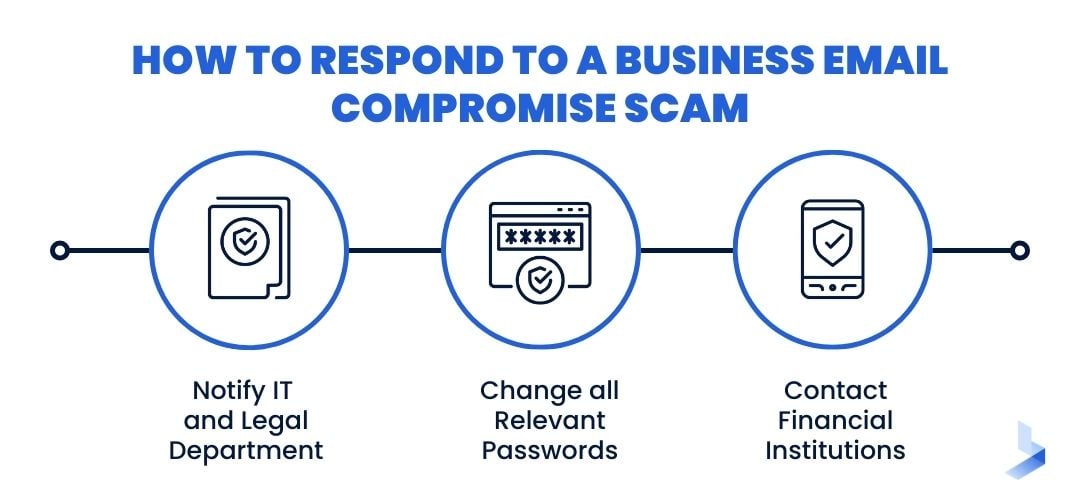
How to Respond to a Business Email Compromise Scam
If a BEC attack is suspected, it's important to take immediate action to minimize the damage. The following are some steps that should be taken if a BEC scam is suspected:
- Notify IT and legal department: As soon as a BEC scam is suspected, it's important to notify the IT department and legal department so that they can take steps to secure the company's networks and systems.
- Change all relevant passwords: All relevant passwords should be changed immediately, including email, banking, and other sensitive accounts.
- Contact financial institutions: If money has been transferred as a result of a BEC scam, it's important to contact financial institutions as soon as possible to try to recover the funds.
In addition to taking these steps, it's also important to report the BEC scam to the authorities. The FBI's Internet Crime Complaint Center (IC3) is a good place to start. Reporting the scam to the authorities can help them investigate and potentially catch the perpetrators.
A Small BEC Scam Can Lead to Major Consequences
At the surface level, a BEC scam may seem like a simple cyberattack. However, a “simple” BEC attack can lead to a number of other devastating effects for businesses. These consequences may include include account compromise, financial loss, and damage to the company's reputation. Additionally, the hacker may use the information obtained through the initial attack to gain access to the company's network and steal other confidential data, such as intellectual property or personal information of employees and customers.
Completely stopping a business email compromise scams from entering an organization's network can be difficult. These scams often involve sophisticated social engineering tactics that are designed to bypass traditional security measures. By understanding the tactics used by hackers and implementing strong email security measures, you can greatly reduce the risk of falling victim to a BEC attack. However, it is important to remember that no security measures are 100% effective, and businesses should have a plan in place to detect and respond to any potential threats.
Stop a BEC Attack with Managed Detection and Response
Managed detection and response (MDR) is a proactive approach to cybersecurity that provides businesses with around-the-clock monitoring of their networks and systems for signs of suspicious activity. This approach is particularly effective in preventing BEC attacks, as it allows businesses to detect and respond to any suspicious activity before it can cause significant harm.
Maintaining a proactive approach is key when protecting your business from BEC scams. Contact us today to learn more about how you can protect your organization through our MDR solution.
