Breaking Down the Biden National Cybersecurity Strategy: Key Takeaways

 By
Emily Miller
·
7 minute read
By
Emily Miller
·
7 minute read
On March 2, 2023, the White House released its National Cybersecurity Strategy. The overarching goal of the plan is to "create a defensible, resilient digital ecosystem" that makes attacks too costly to be lucrative, protects sensitive information, and limits the impact of cyber threats on individuals and organizations. To achieve this, the Biden administration calls for an approach that rebalances the responsibility to defend cyberspace and realigns incentives to favor long-term investments.
Cyberattacks in recent years on critical infrastructure and government agencies have spurred the need to develop regulations across all industries. Although the attacks on the Colonial Pipeline and JBS Foods weren't terribly sophisticated, the effects were wide-reaching and revealed the potential for devastating attacks in the future. Sophisticated ransomware attacks targeting industries that range from healthcare to public schools are increasingly being attributed to nation-state actors. With so many critical sectors facing vulnerabilities, the cybersecurity strategy calls for enforceable regulations to protect all industries.
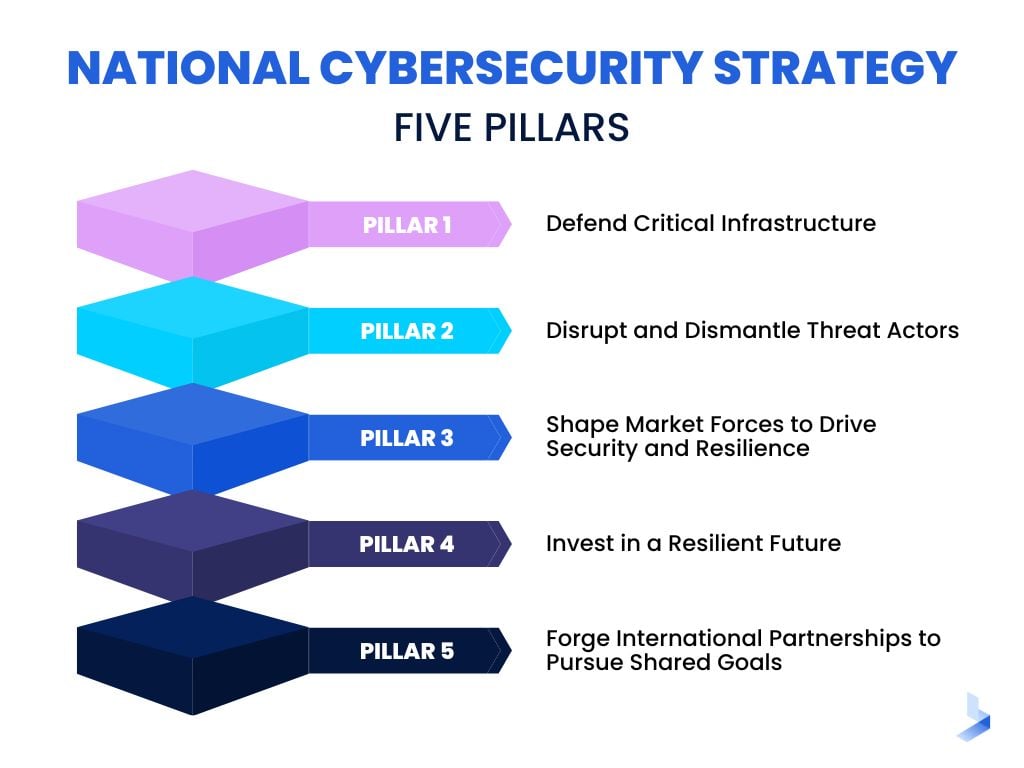
Achieving this level of security is a tall order and it will affect all organizations in both the public and private sectors. The strategy is divided into five pillars with distinctive goals for implementation. Here, we'll summarize the five pillars of the National Cybersecurity Strategy and clarify how it affects organizational cybersecurity in the future.
The Five Pillars of the National Cybersecurity Strategy
Pillar One: Defend Critical Infrastructure
Critical infrastructure in the US depends on third-party systems and tools to effectively distribute essential services and supplies. In the past, the protection of these systems was largely dependent on voluntary participation. This section outlines objectives to develop minimum cybersecurity requirements for critical infrastructure and notes that increased collaboration will be needed with private sectors to achieve goals.
Objectives include:
- 1.1 Establish Cybersecurity Requirements to Support National Security and Public Safety
- 1.2 Scale Public-Private Collaboration
- 1.3 Integrate Federal Cybersecurity Centers
- 1.4 Update Federal Incident Response Plans and Processes
- 1.5 Modernize Federal Defenses
Pillar 2: Disrupt and Dismantle Threat Actors
The goal of Pillar 2 is to unite resources to make cyberattacks so expensive that they are no longer profitable or a means of reaching disruptive goals. Collaboration across government, public, and private sectors are a major part of achieving this goal. Other requirements include new policies to improve the speed and scale of breach notifications and to create regulations for IaaS providers.
Objectives include:
- 2.1 Integrate Federal Disruption Activities
- 2.2 Enhance public-Private Operational Collaboration to Disrupt Adversaries
- 2.3 Increase the Speed and Scale of Intelligence Sharing and Victim Notification
- 2.4 Prevent Abuse of US-Based Infrastructure
- 2.5 Counter Cybercrime, Defeat Ransomware
Pillar 3: Shape Market Forces to Drive Security and Resilience
Pillar 3 focuses on accountability for long-term resilience. The objectives will shift responsibility from the end user to organizations and developers. Objectives outline the need for national data security guidelines that follow established frameworks. Additional areas note the need for software and IoT devices to be manufactured with reasonable security features in place. Federal grants will be put in place to help fund these investments.
Objectives include:
- 3.1 Hold the Stewards of our Data Accountable
- 3.2 Drive the Development of Secure IoT Devices
- 3.3 Shift Liability for Insecure Software Products and Services
- 3.4 Use Federal Grants and Other Incentives to Build in Security
- 3.5 Leverage Federal Procurement to Improve Accountability
- 3.6 Explore a Federal Cyber Insurance Backstop
Pillar 4: Invest in a Resilient Future
This section is designed to create regulations for a secure and resilient digital network in the future. Objectives work toward collaboration from industry leaders, academic leaders, and other countries for a global approach to improved and proactive cybersecurity. The objectives in this pillar focus largely on broad initiatives that will strengthen digital networks internationally for proactive protection. From regulations for emerging technologies to protecting clean energy devices and preparing for a post-quantum future, this pillar will likely introduce a variety of new regulations for all emerging products and processes.
Objectives include:
- 4.1 Secure the Technical Foundation of the Internet
- 4.2 Reinvigorate Federal Research and Development for Cybersecurity
- 4.3 Prepare for Our Post-Quantum Future
- 4.4 Secure Our Clean Energy Future
- 4.5 Support Development of a Digital Identity Ecosystem
- 4.6 Develop a National Strategy to Strengthen our Cyber Workforce
Pillar 5: Forge International Partnerships to Pursue Shared Goals
The final section addresses the importance of cybersecurity on an international level to address transnational and nation-state attacks. The objectives in pillar 5 describe collaborative efforts to build stronger international cybersecurity regulations. As countries work together to pursue a more secure digital future, regulations are likely to be more aligned. This will require all organizations to meet new requirements. It is noted that not all allies have the same resources. As such assistance will be extended to advance shared goals across nations. A big part of addressing critical vulnerabilities is the need for a more secure global supply chain.
Objectives include:
- 5.1 Build Coalitions to Counter Threats to Our Digital Ecosystem:
- 5.2 Strengthen International Partner Capacity:
- 5.3 Expand US Ability to Assist Allies and Partners:
- 5.4 Build Coalitions to Reinforce Global Norms of Responsible State Behavior:
- 5.5 Secure Global Supply Chains for Information, Communications, and Operational Technology Products and Services:
Key Impacts and Takeaways
The 35-page document certainly covers a lot of ground and identifies some of the major vulnerabilities in current cybersecurity strategies. While there are many objectives that call government agencies to take action, there is no doubt that organizations across all industries will be affected by the sweeping changes called for in the cybersecurity strategy. The framework identifies technology as critical infrastructure and immediately notes the need for minimum security regulations across all sectors to drive better cybersecurity practices at scale. These areas are most likely to have a direct impact on cybersecurity requirements for organizations across public and private sectors.
Minimum Regulations Across All Industries
Where voluntary guidelines have widely shaped cybersecurity in the past, new regulations will require critical infrastructure and private companies to adopt specific standards. These requirements are designed to align cybersecurity regulations for a unified approach to protection and will likely be based on existing frameworks like NIST and CISA Performance Goals.
The call for harmonized, collaborative cybersecurity efforts means that private sectors, public sectors, and international partners are more likely to share similar regulations. To prepare for these requirements, organizations can start implementing security measures based on existing national and global frameworks.
Defending Critical Infrastructure
Rightfully, the cybersecurity strategy opens with objectives to support national security and public safety through regulations to secure critical infrastructure. These agencies have relied largely on voluntary guidelines to shape cybersecurity efforts in the past, leading to lax policies and ineffective security. Recent attacks have made it abundantly clear that this approach is not effective against modern cyberattacks.
The administration calls for minimum security standards that are based on existing frameworks. Owners and operators will likely be required to adopt NIST standards (and possibly additional guidelines) to comply with these new regulations. This will require considerable effort as some critical infrastructure sectors currently lack minimum security standards. Efforts beyond these frameworks are also encouraged and will be supported by the administration. This could signal the potential for grants or tax breaks for such efforts.
Like other areas in the strategy, the defense of critical infrastructure calls for resilience. It emphasizes that regulations must be agile enough to adapt to adversaries' tactics, and systems must be designed to fail safely and recover quickly. Future security solutions for critical infrastructure will require tools and processes that identify malicious activity and automatically respond to attacks before damage is done.
Shifting Accountability
Rebalancing the responsibility to defend cyberspace is noted as one of two fundamental shifts required to improve defenses. The goal is to shift responsibility from end users to the parties most capable and best positioned to make the digital ecosystem more secure.
Pillar 3 focuses heavily on this shift with objectives that cover data security, software development, and the vulnerability of IoT devices.
A call to "hold the stewards of data accountable" directly states that national requirements to secure personal data will be consistent with NIST guidelines. As such, organizations across private and public sectors can expect new regulations.
The third objective in the third pillar calls to shift the liability for insecure software products and services. While the requirement is mitigated by the recognition that "companies that make software must have the freedom to innovate," it mandates that companies that fail to live up to the duty of care they owe consumers will be held liable. This will put a considerable security burden on software developers and engineers.
IoT devices are highlighted in this pillar too. However, it largely looks toward the future with requirements focusing on emerging technologies. Funding will likely be available for research and development efforts that focus on designing these devices with greater security features built-in.
International Collaboration
Throughout the entire document, collaboration is a big theme. Most notable is the call for international partnerships that will increase protection against multi-national attacks and nation-state actors. Pillar 2 addresses efforts to make cyberattacks so expensive they're no longer worth carrying out. It calls for international efforts to take down botnets and seize ransoms from attacks.
Pillar 5 defines objectives to forge international partnerships for shared intelligence, strengthening the resilience of allies, reinforcing global norms, and securing global supply chains. On the surface, these objectives seem targeted directly at government agencies. However, collaborative efforts to harmonize cybersecurity regulations, are likely to mean new regulations that span across countries. While there aren't specific regulations outlined for this collaboration, it's possible that regulations may be more closely aligned with GDPR and NIS2 (expected to go into effect in the fall of 2024).
Objective 5 directly notes the importance of securing global supply chains. The vulnerability of the supply chain has been recognized in several high-profile attacks with far-reaching consequences. This section plans for the implementation of best practices in cross-border supply chain risk management. Perhaps more importantly, it discusses the possibility of shifting supply chains to flow through partner countries and trusted vendors. In other words, companies that fail to meet compliance requirements and countries that don't agree to become trusted partners will lose the opportunity to participate in global supply chains. This could mean big impacts on trade and the closure of individual companies.
Aligning Your Cybersecurity Posture with the National Cybersecurity Strategy
The National Cybersecurity Strategy calls for collaboration for a united approach to fight cyberattacks. It also makes it clear that all service providers have a responsibility to provide adequate security for sensitive data and effective security measures in the development of software and IoT devices. There's no doubt that it will take years to implement the sweeping changes described in the new framework. However, organizations across all industries will be affected. Investing in adjustments that improve your cybersecurity posture can help you avoid unexpected impacts as new regulations are rolled out.
Improving the cybersecurity ecosystem calls for a harmonious approach to reduce the burden of compliance. While the framework addresses cybersecurity on a national level, it can act as a roadmap for individual organizations, offices, and agencies. Managed Detection and Response (MDR) is a comprehensive cybersecurity solution that provides 24/7 protection for your entire network and even ensures you don't fall victim to supply chain attacks. By investing in an outsourced, always-on service, you can have a robust shield against ransomware, stop social engineering attacks before they become a threat, and maintain complete protection against endpoint attacks.
The combination of human intelligence and modern technology provided by MDR allows you to carry your cybersecurity responsibilities without placing extra burdens on your team. Wondering how you can get a jumpstart on the compliance regulations that will be implemented in relation to the National Cybersecurity Strategy? Get in touch with the cybersecurity experts at BitLyft to learn about how BitLyft AIR provides unbeatable protection while helping you maintain the most up-to-date compliance regulations for your industry.

