Cybersecurity Executive Order: How To Respond

 By
Emily Miller
·
7 minute read
By
Emily Miller
·
7 minute read
Have you ever had your details compromised online? These cyber-attacks are on the rise in the wake of Russia's invasion of Ukraine.
While the federal government has responded to these threats with new legislation, it's up to individual agencies and their employees to implement these protocols via a Cybersecurity Executive Order.
So what are these cybersecurity protocols that it suggests? And how should you respond to them? Keep reading to find out more.
Executive Order (EO): 14028 Strengthening Cybersecurity of Federal Networks
This EO is a step in the right direction. It establishes a baseline of cybersecurity standards for Federal agencies.
Cybersecurity professionals should be able to identify and mitigate threats. Every layer of an organization's IT infrastructure.
The best response to a breach is prevention through multiple layers of security controls. Be sure to implement these before an attack occurs.
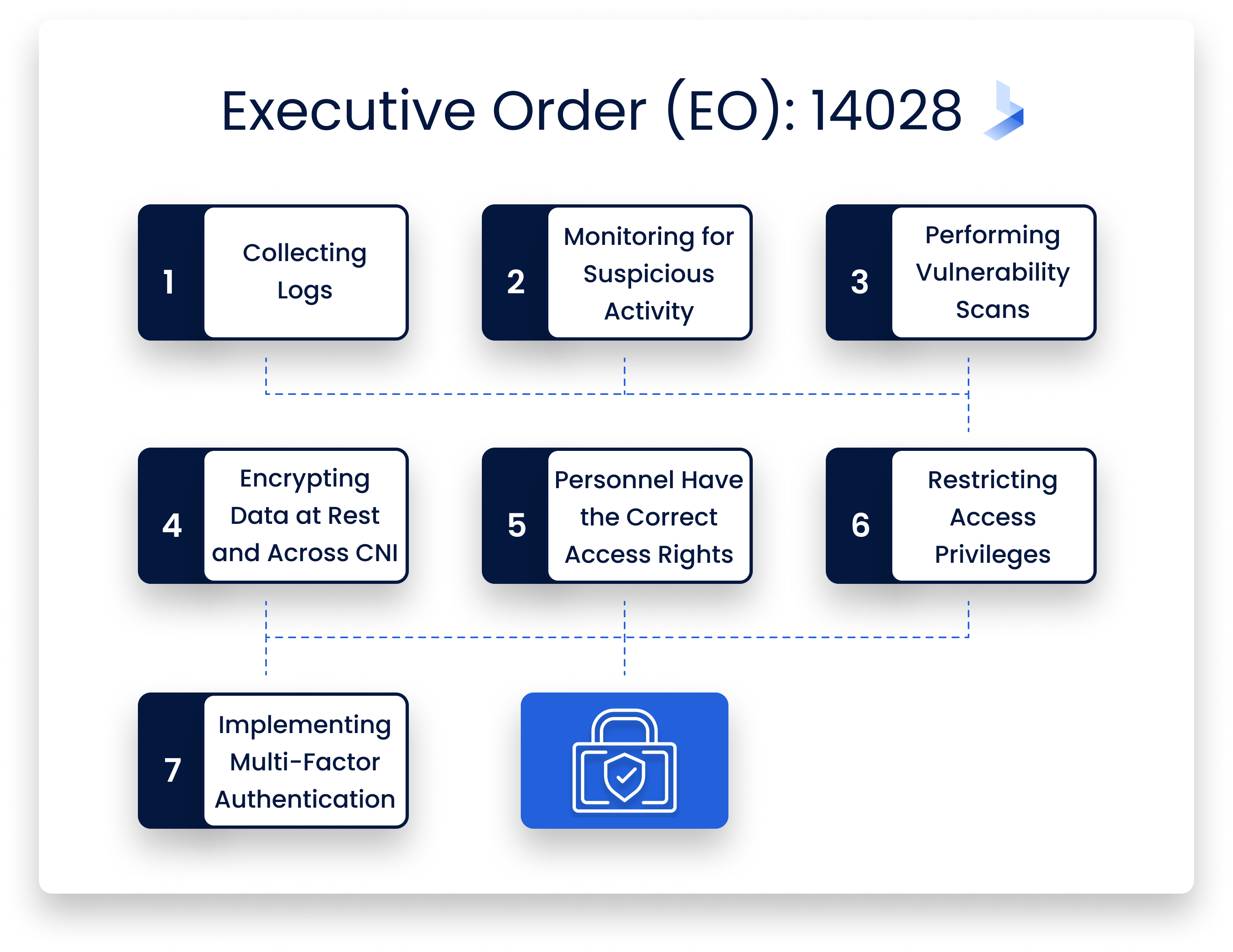
This Executive Order requires Federal agencies to implement basic cybersecurity measures such as :
- Collecting logs
- Monitoring networks for suspicious activity via sensors like firewalls
- Performing vulnerability scans on systems connected to critical infrastructure networks (CNI)
- Encrypting data at rest and in transit across CNI
- Ensuring that all personnel have appropriate access rights based on their role
- Restricting physical access privileges where possible
- Implementing multi-factor authentication whenever possible
All of this is now mandatory. Federal agencies will fine those that don't do this.
EO 14028: The Basics
EO 14028-is named Improving the Nation's Cybersecurity. It is an important step in establishing a baseline of cybersecurity standards for Federal agencies.
This EO establishes a framework to protect Federal IT networks. This includes those outside of agency control. Examples include contractors and non-profit organizations. As well as those that receive certain types of funding.
It also calls on agencies to identify risks, and prioritize efforts based on risk management principles. As well as to improve information sharing with owners/operators of critical infrastructure. They must also promote awareness and training among employees.
Governments should prioritize those who have access to sensitive information. Or those with access to systems at risk from cyberattacks (such as contractors).
Furthermore, they must improve incident response capabilities. This includes across all levels within an organization. The EO develops strategies for defending against adversarial actors. Especially those attempting malicious activity against government IT networks.
EO 14028 Is An Extension of Executive Order (EO) 13800
EO 14028 is an extension of the May 2019 Executive Order (EO) 13800. This is "Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure."
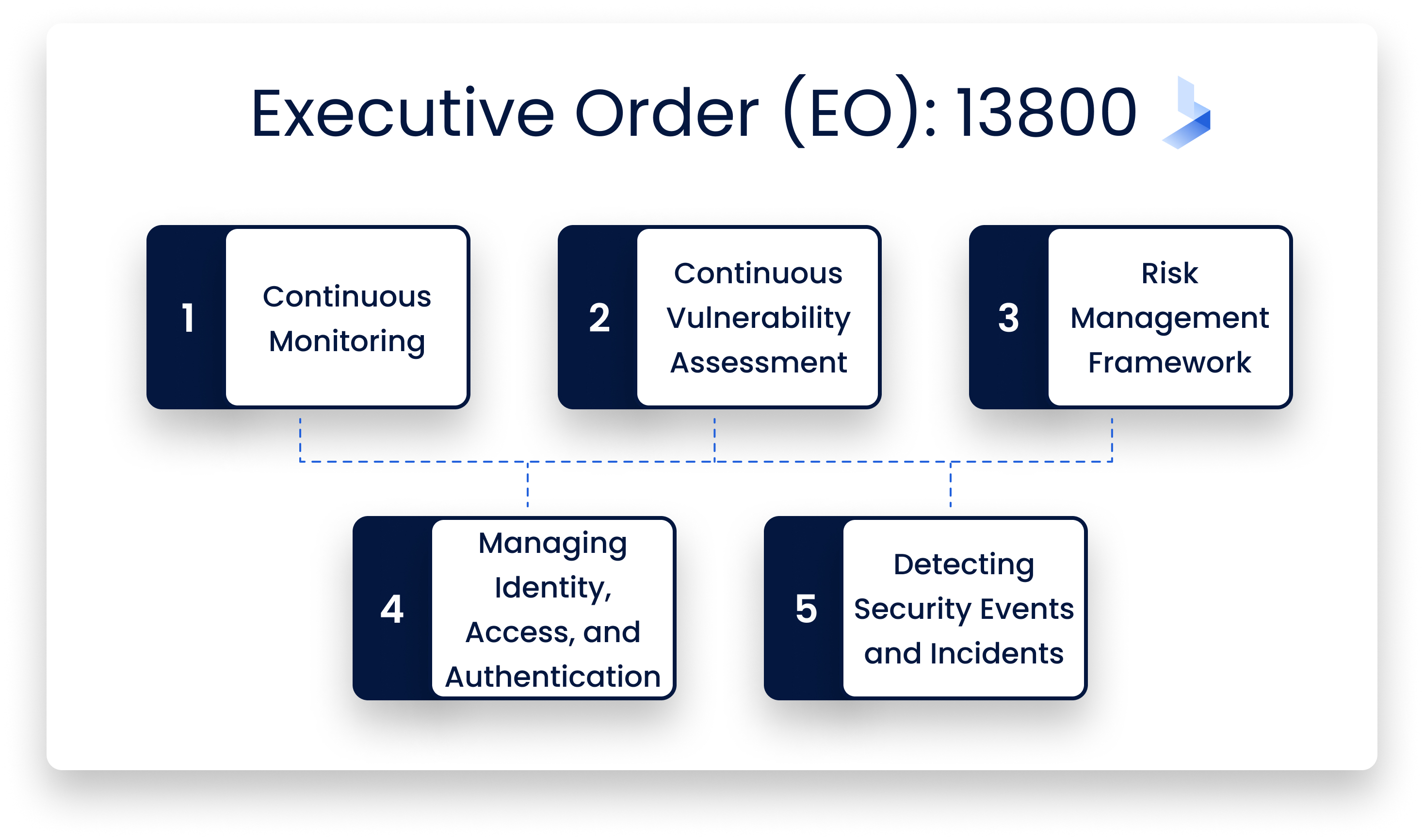
That first EO established a detailed program requiring federal agencies to implement five key cybersecurity initiatives. These are:
Continuous Monitoring
All federal agencies must monitor their network traffic to identify and analyze suspicious activity. They must then take appropriate actions in response.
The idea is that cybersecurity is not reactionary but a continuous process. This way you can nip potential pitfalls in the bud.
Continuous Vulnerability Assessment
All federal agencies must perform regular checks for known vulnerabilities in their networks. They must scan for indicators that could indicate unauthorized access attempts or exploitable weaknesses.
If you detect any vulnerabilities, it is important to resolve them within 90 days. That is unless mitigating conditions apply that justify a longer period.
Risk Management Framework
All federal agencies must develop policies for identifying, assessing, and managing cyber risks. They must prioritize resources. They must also take appropriate measures to reduce risk to acceptable levels.
Furthermore, they should routinely report on performance against these plans. Finally, they must document compliance with relevant laws or executive orders.
Managing Identity, Access, and Authentication
Identifying and authenticating users is a critical part of managing identity, access, and authentication (IAM).
IAM is the process of granting and controlling access to systems and information. This is based on a user's identity. It's also a key component of the NIST Cybersecurity Framework.
An example: when you log into Facebook, your account allows you to post status updates. These include "like" posts from friends or family members.
How can you securely use these functions? One that doesn't compromise your privacy or data security needs? Facebook must first verify that the person logging into their platform is actually who they say they are.
This process involves two steps. The first is identification (verifying someone’s identity). Secondly, authentication. This is verifying someone has approval for using their account.
Detecting Security Events and Incidents
To detect and respond to security events and incidents, you will need the ability to monitor the organization's information systems for events that may indicate a malicious attack or breach. You will also need the ability to detect and respond to potential threats promptly.
The goal is to be able to detect and respond to security events and incidents across the entire organization promptly.
Protecting the Confidentiality, Integrity, and Availability of Data and Systems
The Executive Order requires agencies to implement a risk-based approach. This approach protects the confidentiality, integrity, and availability of data and systems.
This means that you need to identify your sensitive information assets within the agency. Those would be things like trade secrets or classified documents. And then protect them in such a way that makes sense for each type of asset.
You also need to consider where your store sensitive information. Whether it’s in paper form or electronic form. How many copies exist? Who has access to those copies? How long does it stay around? Finally, you need to ask whether you retain backups for five years or longer); etc.
Ensuring Continuous Monitoring and Rapid Response
It’s not always easy to tell the difference between an incident and a potential incident. Here are some examples of potential incidents.
Your security operations center (SOC) detects malicious activity on one of your servers. But you can’t confirm whether this is a false alarm or a real attack.
You read a news article about how hackers broke into another company that is similar to yours.
You should log these incidents for further investigation. However, you don't need to suspend your operations. This could have a detrimental effect on your department when the chances of there is a major issue.
Six Months Later - The Third Act Begins
Biden issued Executive Order 14028 in December 2021. It further extends the May 2019 Executive Order (EO) 13800. It centers around "Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure."
That EO establishes a detailed program. It requires federal agencies to implement five key cybersecurity initiatives:
- Improved monitoring of security controls across the entire system lifecycle including vendor management
- Certification of compliance with cybersecurity standards for each acquisition category
- Contractor-delivered services must meet baseline requirements for data protection and third-party risk assessment
- Automated vulnerability scanning tools
- Implementation of multi-factor authentication using strong authenticators
How did we get here? In May 2019 the White House released Executive Order 13800. This required cyber officials within each federal agency to implement five key cybersecurity initiatives.
The first four were mandated by that document. Improved monitoring of security controls across the entire system lifecycle. This is including vendor management. It also includes certification of compliance with cybersecurity standards for each acquisition category (e.g., personal identity verification).
Furthermore, it includes contractor-delivered services which must meet baseline requirements. These include data protection and third-party risk assessment; and automated vulnerability scanning tools. All of this is designed to mitigate the true cost of a cybersecurity breach.
The White House Issued a New Executive Order (EO) On January 8, 2021
In response to recent cyber incidents across the federal government, the White House issued a new executive order (EO) on January 8, 2021.
EO 14028 was titled Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure. It takes an important step in establishing a baseline of minimum cybersecurity standards for Federal agencies. It also establishes a framework by which citizens' data can be protected from malicious activity by nation-state actors.
These four key initiatives established by EO 13800 are still required:
- Automated Continuous Diagnostics and Mitigation (ADDM)
- Cybersecurity Framework
- Risk Management Framework
- Continuous Monitoring
There is also an incident Response Plan. This is designed to create and maintain an incident response plan. This includes strategies for serious attacks that threaten to take the whole Federal government offline.
What It Means for Government Agencies
For government agencies, the Executive Order mandates that cybersecurity programs be based on a risk management framework. This means that agencies must identify assets and capabilities they want to protect.
Then they must prioritize them. After that, they can create policies and procedures that reflect this prioritization.
Agencies are also required to have a continuous monitoring capability. They can detect cyber incidents as soon as possible.
This is whether from outside attackers or internal sources. These may have been compromised by malware. For an agency's response efforts to be effective, these detection tools must be integrated into its incident response plan (IRP).
Agencies are also required to have plans for responding to cyber threats from both internal sources and external actors. This includes developing strategies for defending against such threats before they occur such as:
- Identifying options for preventing such incidents
- Preparing responses in case of attacks
- Ensuring rapid recovery following an attack
Restoring Normal Operations After an Attack Has Ended
Respond quickly if critical information is compromised during an attack. Containing damage caused by an attack. This includes data loss.
This can be done by limiting exposure through encryption techniques where possible while maintaining usability at all times.
What It Means for Those Affected
The order requires “any organization operating critical infrastructure” to implement cybersecurity measures. These include protecting their networks and data. Key components to remember:
- Keep your data safe.
- Protect your organization's network
- Safeguard your organization's critical infrastructure
Essentially, what it means is that there is an onus on federal agencies to implement round-the-clock security. There is a duty of care that centers around preventive measures rather than reactionary measures.
This is important as more and more of our world relies on online and cloud bases businesses, especially in a post-pandemic world.
Don't be alarmed if you're a cybersecurity professional wondering how to implement these new measures. Follow these steps to avoid burnout.
How to Respond
To respond to a cybersecurity incident, you'll need to:
- Identify the threat
- Identify the risk
- Determine an appropriate response
- Implement your chosen response
Once you've taken these steps, monitor and evaluate your response over time. You can then re-evaluate it if circumstances change. This is a process known as continuous monitoring.
Cybersecurity is an ongoing process. Once you're aware of an incident, take the first step. Identify the threat. Take a moment to pause and identify what happened. This will help you understand what's going on. You can then figure out how best to respond.
Now that you've identified the threat, take stock of what's at stake. Understand what steps are needed to protect yourself from further damage. Finally, consider hiring a professional to help with your response.
You've identified the threat, determined the risk, and figured out how to respond. Now it's time to implement your response.
A good response will take into account all of the information you've gathered. It should include which steps are needed to protect yourself from further damage
The Cybersecurity Executive Order Keeps Us All Safe
By now, most people know about the cybersecurity executive order that Trump signed in May 2016.
It calls for a federal agency to develop a plan to protect America's critical infrastructure from cyber-attacks. The issue has drawn bipartisan support in Congress. It was endorsed by both Hillary Clinton and Donald Trump during their campaigns for president in 2016.
It increases the nation's cybersecurity and that helps keep the world safe.
For more on the latest trends in cybersecurity, be sure to sign up for our newsletter.
