Cyber Threat Hunting: What You Need to Know

Cybersecurity research typically leads to valuable information about high-value tools used in threat detection and response. While these tools are a vital part of any complete cybersecurity solution, such information fails to acknowledge the many threats that could be lurking in your network. Advanced Persistent Threats (APTs) are high-level, sophisticated attacks that can take months to reach an objective.
Sophisticated attackers who leverage these threats take considerable pains to enter your network unnoticed and move discreetly through your network to gain information or advanced permissions while planning a particularly lucrative attack. Not surprisingly, an attack that takes so much time and effort to produce ample payoff for attackers is likely to include considerable damage and expense for your network. Unfortunately, hackers are very adept at exploiting user or security vulnerabilities to get past the tools in your cybersecurity stack to launch these attacks.
This is where cyber threat hunting comes in. At its core, threat detection and response is a defensive practice that begins when an alert is triggered after a suspicious activity is recognized. At the opposite end of the spectrum, cyber threat hunting is a proactive approach performed by cybersecurity experts to actively seek out threats that have already breached the network. The most effective use of cyber threat hunting is a continuous process that utilizes human expertise alongside technical tools and industry information to seek out potential attacks before they cause damage.
Like many parts of effective cybersecurity, a majority of organizations mistakenly believe cyber threat hunting is only necessary for financial institutions or high-level corporations. However, the availability and use of advanced cyberattacks are growing and these attacks are just as likely to be used on SMBs that present a potentially easier target.
The world saw an alarming 105% surge in ransomware cyberattacks in 2021. Governments worldwide saw a 1,885 increase in ransomware attacks, and the healthcare industry faced a 755% increase in those attacks as well. There were many events that contributed to the rise in attacks, and they are unlikely to slow down. Ransomware has become an industry that allows even those with little technological knowledge to purchase tools that lead to successful attacks. 37% of companies were targeted by ransomware in 2021, with an average ransom of 170,404 paid. Sadly, only 8% of companies recovered all data after paying the ransom demanded. Most ransomware attacks go completely unnoticed until a ransom note is issued. Unfortunately, at this point, the battle has already been lost. Alongside ransomware, phishing, malware, and data breaches were some of the most common cyberattacks in 2021.
Cyber threat hunting seeks out indicators of compromise that exist before ransomware is implanted or access to sensitive data is achieved. For organizations to have comprehensive protection that prevents sophisticated attackers from reaching their objectives, it is a critical part of a complete cybersecurity solution. This guide is designed to help organizations understand what cyber threat hunting is, how it works, common misconceptions about the practice, and what is needed to perform effective cyber threat hunting.
What is Cyber Threat Hunting?
The idea of threat hunting certainly sounds more exciting than data analysis or information mining. After all, the cybersecurity specialists that conduct threat hunts are investigating criminals in action. The truth is, cyber threat hunting is the practice of proactively searching for signals that suggest a threat is lurking within a network. It is accomplished with the use of log data, external data, advanced tools and software, and technical cybersecurity education and experience.
Many business leaders researching effective cybersecurity solutions are aware of the deluge of email phishing attempts that occurred in 2021. Yet, the focus on the prevalence of phishing fails to emphasize the ever-important point that a successful phishing attempt is often only the first step in a bigger attack. When an attacker exploits user behavior or endpoint vulnerabilities to enter a network, they can often lurk undetected in the system for weeks or months before discovery. This time is spent quietly advancing access, siphoning data, or setting the stage for a significant attack. A cyber threat hunter uses the data gathered by an efficient security system to search for clues of a discreet attacker lurking in the network. Like sophisticated cyberattacks, threat hunting must be performed by humans to effectively search for hidden actions or patterns of human attackers that might have gone undetected by software or algorithms.
Threat Hunting Methods
Threat hunters work on the assumption that adversaries are already in the system. Investigations are initiated with different tools and methods to find varying evidence of a threat. The methods of threat hunting typically fall into three main categories.
Structured Hunting (Hypothesis-Driven Investigation)
This type of threat hunt is often triggered by new information about an evolving threat or existing attack. The information provides a focus for the hunt which is typically carried out with the use of tactics, techniques, and procedures (TTPs) most likely to be used in the type of attack. The most common foundations for developing a hunting strategy based on TTPs include:
- The Intrusion Kill Chain
- The MITRE ATT&CK Framework
- The Mandiant Attack Lifecycle
Unstructured Hunting (Time Sensitive Hunting)
This method of threat hunting is based on known indicators of compromise (IOC) or indicators of attack (IOA). IOAs and IOCs act as a trigger to guide the hunt to uncover clues that suggest malicious activity is occurring within a network. With an understanding of the exact type of attack in question, threat hunters look for pre and post-detection patterns that could be hidden in log data.
Situational or Entity Driven Hunting (Advanced Analytics Hunt)
This method uses an organization's environment and potential vulnerabilities to search for potential attacks. It typically utilizes cybersecurity tools, like the organization's SIEM system, and third-party data, like crowd-sourced attack data to sift through massive amounts of information to detect irregularities.
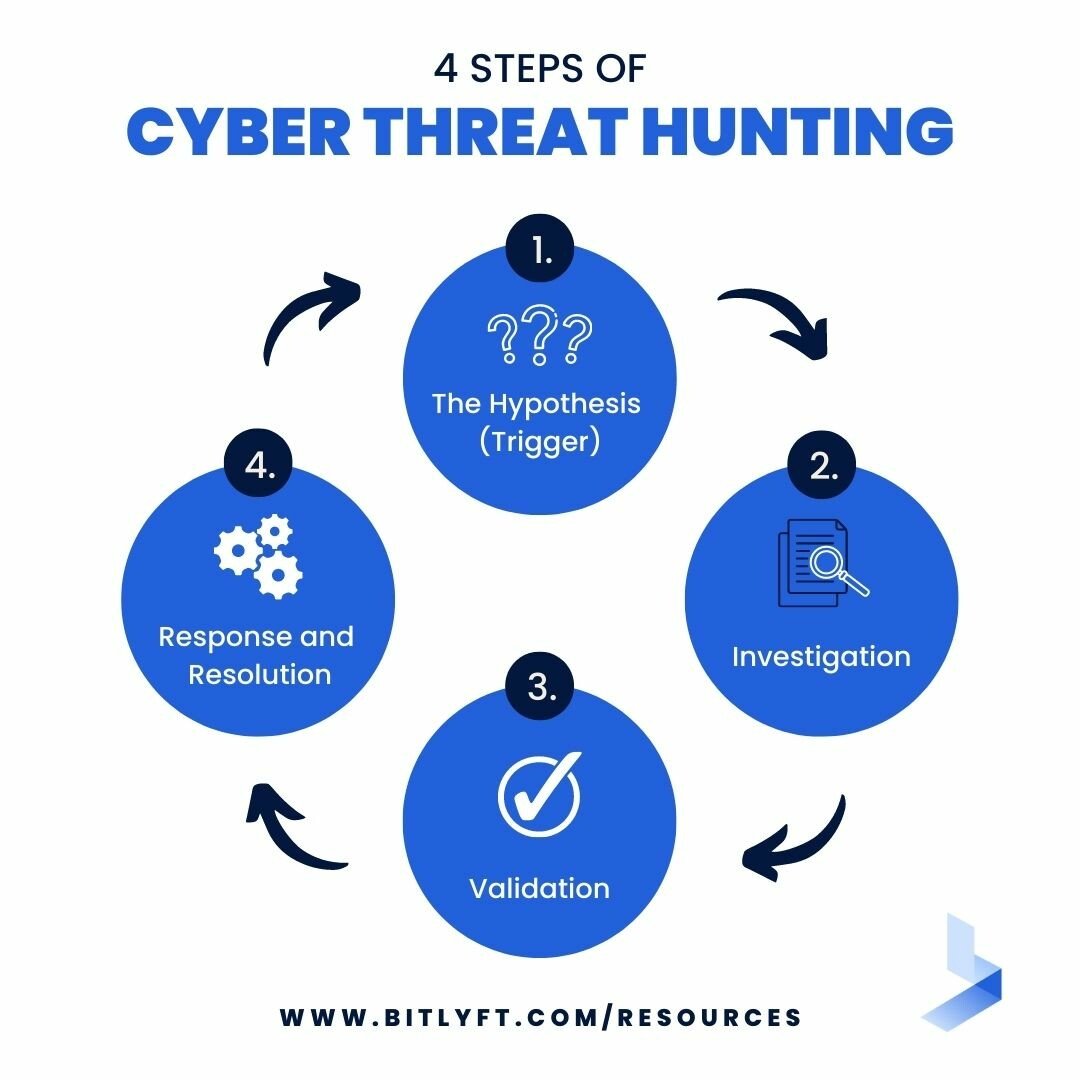
Steps of Cyber Threat Hunting
Similar to the way any hunt is approached, threat hunters use specific practices to increase efficiency and effectiveness. No matter which method, or combination of methods, a threat hunter uses, the process of cyber threat hunting involves three basic steps.
The Hypothesis (Trigger)
Whether a scheduled process or an IOC launches your threat hunt, the search begins with a specific event or hypothesis about a new or existing threat. The hypothesis can include known TTPs and third-party data for assistance in outlining potential clues. An effective hypothesis suggests a named threat has already compromised the network and develops a plan to search for evidence.
Investigation
This step requires the hunter to sift through log collection data with the use of tools and technology to rule out the suspected threat or develop a complete picture of malicious activity.
Response and Resolution
The data from the investigation can now be put to use to mitigate a threat or report the findings of the search. Data that suggests malicious activity can be entered into automated tools to further tune the system to automatically respond and react to the specific threat in the future. New intelligence will be communicated to security teams enabling them to react promptly and mitigate the threat. When the system is fully restored, the details will be carefully documented and used to eliminate vulnerabilities and catalog previously unknown threats.
Signs Threat Hunters Watch For
As a hunter, it's essential to know what you're looking for. While professionals with considerable IT knowledge can learn the art and science of threat hunting, experienced threat hunters know what types of signs to watch for when seeking potential threats. In threat hunting, these signs are known as indicators of compromise (IOCs) or indicators of attack (IOAs). IOCs are pieces of forensic data that identify potentially malicious activity on a system or network. These clues are usually discreet and identify activities early in the attack process that could lead to a data breach or system compromise. IOAs focus on identifying real-time activity while an attack is in progress. IOAs are typically more focused on why something is happening than what happened. Examples of the red flags threat hunters seek during the hunting process include:
- Unusual outbound network traffic
- Irregularities in privileged user account activities
- Multiple failed log-in attempts
- Geographical irregularities
- Increased database read volume
- Mismatched port application traffic
- Repeated requests for file transfer
- HTML response sizes
- Unusual DNS requests
- Unexpected patching or updates
- Bundles of data in the wrong place
- Mobile device profile changes
- Web traffic with inhuman behavior
Common Misconceptions About Cyber Threat Hunting
With a name like threat hunting, it should come as no surprise there are several misconceptions about how the process works or if it's even relevant in today's sophisticated cybersecurity landscape. The reality is, that the human element will always be an essential part of cybersecurity, and threat hunting is a relevant process that can uncover and eliminate ADPs before damage occurs in your network. Here's the truth about some of the most common misconceptions about cyber threat hunting.
Cyber Threat Hunting Can Be Replaced With Technology
Along with the idea that threat hunting is an outdated process, many company leaders assume modern technology can be used to replace threat hunting actions. These misconceptions suggest that AI, endpoint detection, or other tools can replicate human psychology. The truth is, that many modern technological cybersecurity tools are used in the process of threat hunting, but the activities must include human experience and observation for success. Each tool in your cybersecurity stack has a job to do, and threat hunting is used to detect the activities of bad actors who have gotten past these tools.
Threat Hunting is Only Required Once
Many organizations believe that certain cybersecurity practices like gap analysis and threat hunting are a one-time benchmark process. The truth is, like technology, cybersecurity is always evolving. To be effective, threat hunting should be a continuous process that seeks to improve an organization's cybersecurity posture and identify sophisticated and evolving attacks. A single anomaly can cost an organization millions, and a successful hunt can spread data that protects hundreds of companies across industries.
Threat Hunting is the Same Thing as Penetration Testing
Penetration testing has some of the same concepts as threat hunting but they have different objectives. Penetration testing is designed to identify weaknesses in your own network. Threat hunting is the act of detecting suspicious behavior that signifies an attack in progress. While both practices can improve your overall cybersecurity posture, pen-testing helps you keep out attacks and threat hunting identifies attacks that have gotten past your defenses.
Threat Hunting is a Completely Manual Process
Like data analysis, threat hunting requires scrutinizing large amounts of data which is impossible to do without powerful tools. Threat hunters combine education and experience with analytical tools to help identify malicious activity. While threat hunting can't be entirely automated, it's definitely not a fully manual process.
Threat Hunting is a Waste of Time
This myth comes in a variety of forms that suggest threat hunting is:
- Too expensive
- Not worth the time
- Too complex
- Just a trend
A limited cybersecurity budget is at fault for many of these misconceptions. The suggestion is that available funds should be spent on tools. However, while threat hunting doesn't always uncover an attack, it is an important contributor to the overall process of keeping your network safe. Threat hunting addresses the most modern and sophisticated cyberattacks to further advance cybersecurity technology and stop advanced threats in progress.
Threat Hunters Need a Dedicated Platform to Hunt
Trade shows and certain security vendors might have organizational leaders believing that threat hunting can only be performed on a dedicated platform. This isn't true. In fact, the most advanced threat hunting practices depend on experience and traditional tools like SIEM, EDR, SOAR, and CTI. While this doesn't mean that platforms dedicated to threat hunting are useless, it's important to know that a tight cybersecurity budget doesn't have to be spent on extra tools.
Resources Required for Actively Hunting Cyberthreats
By now it's clear that there's nothing simple about threat hunting. Not surprisingly, it takes a careful combination of resources to perform effective cyber threat hunting. Essentially, threat hunters are required to hunt for dangers that they aren't sure even exist. This requires a collection of effective tools, frameworks, and methods for hunting threats. Threat hunting falls into these basic categories.
Human Expertise
Threat hunting is a human-led process that relies on the knowledge of human behavior and cybersecurity experience. Sophisticated hackers are continually devising new methods and tools to compromise organizational networks in ways that provide a big payday. To understand the nature of these attacks, human threat hunters must think like threat actors to identify actions that signify an attack. This process requires the use of highly technical cybersecurity tools and considerable time for hunters to sift through large amounts of information without missing important clues.
Threat hunting is not a process that can be effectively performed by any IT professional with security knowledge. While IT professionals can learn the methods of threat hunting, a successful hunt relies on knowledge of the network and an understanding of what to look for.
Tools and Technology
To effectively research through all the data that is gathered from your network activities, threat hunters need modern tools and software. All networks collect a wealth of data related to the activities that take place every day. This data is exported to your cybersecurity system to be categorized and normalized for use by your security professionals. These tools and technologies are commonly used by professional threat hunters.
SIEM
Your SIEM system is the hub of your security solution. The information it supplies can help you stay one step ahead of the attackers trying to access sensitive data in your network. When you use threat models like those in the MITRE ATT&CK framework to configure your SIEM you can streamline threat hunting with convenient workflows, easy-to-use dashboards, and content designed to help you eliminate false alerts and save time. While most SIEM systems must be used alongside the MITRE ATT&CK framework, Securonix SIEM is automatically aligned with MITRE ATT&CK, to trigger alerts based on threat chain models
Third-Party Information (Cyber Threat Intelligence)
When organizations can collaborate and share information, this combined intelligence can be used to automate security systems. Cyber Threat Intelligence (CTI) is a body of information describing attempted and successful breaches. This database is used to configure automated security systems that use machine learning and artificial intelligence to sift through data and detect suspicious behavior. Threat hunting takes advantage of CTI to conduct a system-wide search for hidden threats.
Machine Learning
While AI isn't a replacement for threat hunting, different types of machine learning are a crucial part of the process. With proper configuration and optimization, SIEM systems use machine learning to trigger alerts that launch time-sensitive threat hunts. CTI can also be integrated into security systems to trigger automatic alerts and actions to respond to known threats or potentially suspicious activity. Finally, the results of successful threat hunts can be used to further advance cybersecurity tools designed to bolster organizational network defenses.
Data From Your Network
It's true that cyber threat hunting is the act of identifying active attacks. However, like other cybersecurity activities, detection relies on data that describes the actions that take place across your network. Ample log collection from your SIEM system identifies all of the events that take place across the network. Without a properly optimized system, you run the risk of failing to collect data that signal suspicious behavior.
Threat hunting is a complex process that takes time, resources, and dedication. The tools and resources used in the process are typically siloed and require the threat hunter to manually combine them for an effective solution. This can be difficult for organizations without a fully staffed security operations center. Organizations that aren't adequately staffed to accomplish this may choose a managed security solution.
BitLyft Leverages a Combination of Tools and Knowledge for Cyber Threat Hunting Success
Effective cybersecurity solutions take a strong proactive and defensive approach against cyberattacks with a collection of modern technological tools and the experience of highly trained cybersecurity professionals. At BitLyft, we have a deep understanding of the ways CTI can work with an advanced SIEM to enhance the process of threat hunting. CTI gives you intelligence and accuracy through data warehousing (IPs, URLs, domains, and other contextual metadata information) and integrates into the SIEM, SOC, and SOAR components of our platform.
Our managed cybersecurity services utilize the power of Securonix SIEM, the only SIEM that is fully integrated with the MITRE ATT&CK framework and UEBA capabilities. Security automation through our Central Threat Intelligence platform to make the time between detection and immunization seconds. CTI through BitLyft means we take action before threats happen. We utilize threat information from all users and clients on our platform (as well as outside sources) to validate the threat as real and useful. Our central threat intelligence stores this information in a data warehouse and through our AIR modules, automatically updates each client with proactive protection. This gives you the preemptive advantage against attackers through "herd" immunity rather than just reacting to threats once they've already attacked.
When these tools are properly configured, organizations have the advantage of proactively addressing threats. Our experienced threat hunters work with the most up-to-date tools to rapidly find clues and stop an active attack before damage occurs. Cyber threat hunting is one of the most effective ways to protect your organization against sophisticated, low, and slow attacks breaching protected networks. It is a pivotal part of a comprehensive business cybersecurity system.
If you're unsure about your cybersecurity posture or whether your business is prepared to face the advanced cyberattack landscape and evolving threats to modern enterprises, don't wait to become a victim. Schedule an appointment with BitLyft to learn how we can help you protect your business from new and evolving cyberattacks.
