Managed Cybersecurity Services

 By
Jason Miller
·
4 minute read
By
Jason Miller
·
4 minute read
Companies desperately need help with managing their cybersecurity program. Not only are threats continually evolving, but the quantity of resources that firms must throw at the problem is tremendous – too much, in some instances.
This is where hybrid or “co-managed” cybersecurity can help. With co-managed security, your firm owns the SIEM but gets help from the MSSP who manages it through their SOC. In short, your organization shares monitoring duties with a third party, getting the assistance you need to process logs and respond to threats, should they occur.

Custom solutions are often beneficial to companies with specific needs. Your firm, for instance, may have developed a comprehensive approach through a variety of SIEM software but doesn’t have the human resources to process all of it. The idea is to get the labor-saving benefits of an off-the-shelf (or fully-outsourced) solution while at the same time, retaining control over the type of security your firm uses.
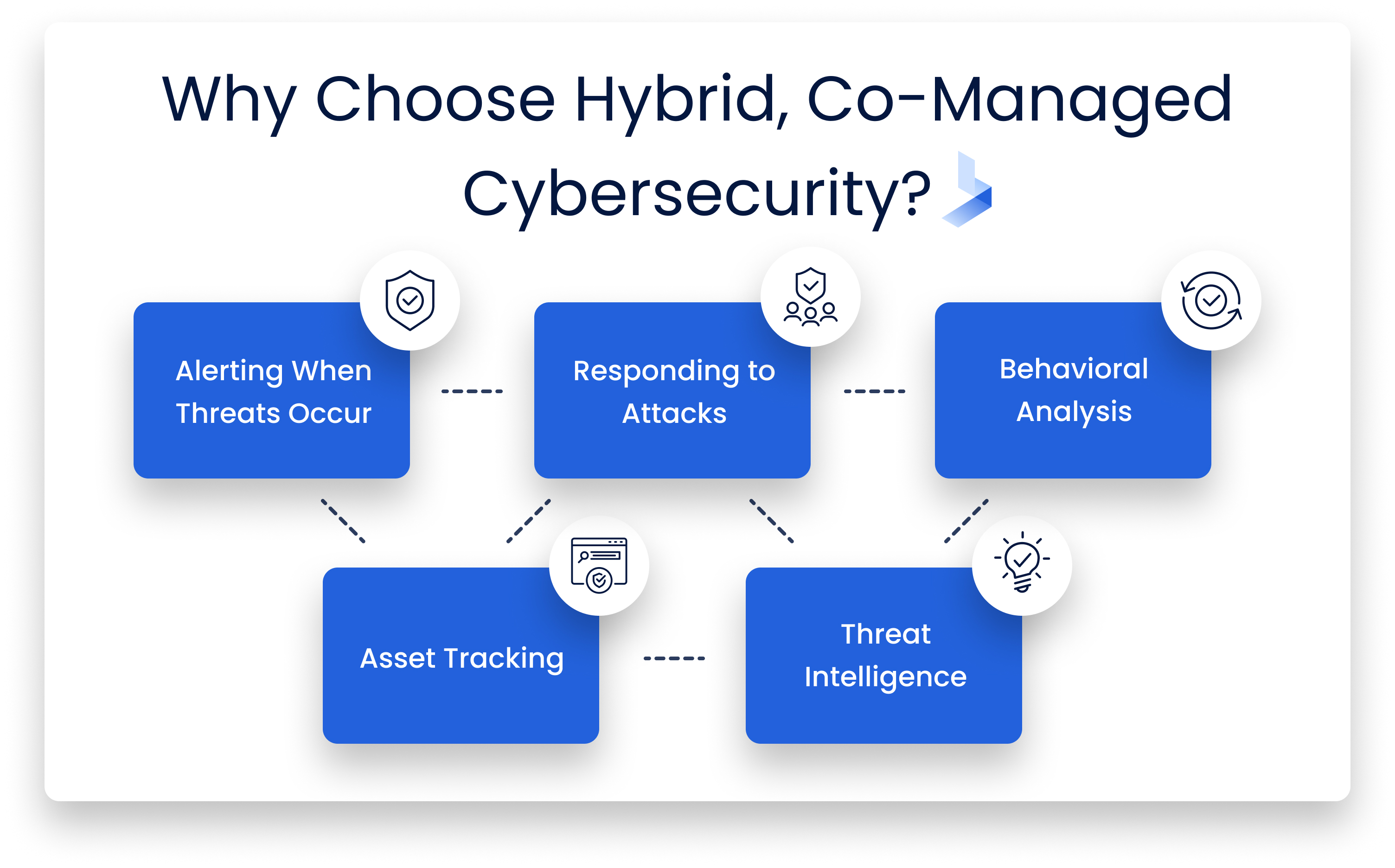
Why Choose Hybrid, Co-Managed Cybersecurity?
The Client and the MSSP Share the Duties of Monitoring the Secure Environment
While not always the case, the MSSP and the client share the duties of monitoring the company network. As with any specific IT service, there are often options that allow you to control how much monitoring is done by the third-party company and how much you do in-house.
One of the beautiful things about hybrid managed cybersecurity services is that they are SIEM agnostic. In other words, it doesn’t matter what software you’re currently using; a professional, third-party organization, like BitLyft, will be able to incorporate it into its processes and take over some or all of the monitoring duties for you.
For firms, this is good news. Companies don’t have to change their existing SIEM systems or retrain their in-house staff to conform to the requirements of the MSSP. What’s more, many MSSPs can provide cloud-based versions of SIEM software. This allows companies to retain their existing product stack but experience all of the advantages of holding it in the cloud, such as rapid security patches and updates, and quickly software changes (should they require it).
Alerting When Threats Occur
Managed cybersecurity services not only protect against threats but alert companies when one occurs. MSSPs are usually better than the firms they serve at doing this because they have dedicated analysts who use SIEM software to keep themselves apprised of any unusual activity on the network. Often a firm doesn’t know that it’s been the victim of an attack until the MSSP sends its report, by which time, the problem is resolved.
SIM, or Security Information Management, services can often overwhelm in-house analysts with alerts. In an ideal situation, the analyst would investigate every item on their log, but all too often, it grows faster than they can process, leading to dangerous backlogs.
This should not occur using a hybrid cybersecurity solution in combination with an MSSP. The MSSP efficiently processes all of the events in the log and helps to use SIEM software more intelligently, adjusting it so that it doesn’t create false or redundant alerts for regular, everyday activities.
Responding To Attacks
Responding to attacks is a challenge for the vast majority of firms. The initial issue that they face is detecting attacks in the first place. Companies can often go months without launching an adequate response because they are unaware of a breach. The threat remains dormant, collecting information or using company resources, and only after a long period is it discovered. At this point, the damage is done. MSSPs working in conjunction with company SIEMs can often identify threats in real-time, preventing them from becoming established, and providing value to hackers.
Responding to attacks can be more complicated if the company’s security posture or systems is fragmented. Attacks on certain parts of the network may be easier to detect than problems on another.
For instance, many companies are often unaware of the true extent of the data that they hold. This lack of awareness exposes them to risk of losing data that they did not know they had because they do not fall under the umbrella of their existing security controls. One of the jobs of an effective MSSP, therefore, is to seek out these silos and bring them into the general security framework.
When an attack does occur, it’s often difficult to know how to respond, especially if it is something new that a company hasn’t seen before. Responding, therefore, can take weeks of planning and development, putting business continuity at risk.
MSSPs, however, often have tools that they can deploy to quickly counter new threats, helping companies respond before attackers can do more damage. These tools include things like reverse engineering malware to find out how it breached company network security or sandboxing threats to work out how they will interact with company systems. MSSPs can then offer solutions and upgrades to the firms SIEM, making it more robust in the future.
Handling Other Cybersecurity Duties
Managed security services also offer a range of other security services that might be difficult or too costly to implement in-house.
Behavioral Analysis
It’s not just hackers or malicious software that can compromise the security of your business network, but the actions of authorized network users too. MSSPs use special behavioral analysis tools to detect unusual patterns of behavior and create reports for CIOs and CISOs for immediate review.
Asset Tracking
As discussed, one of the most significant issues that companies face is fragmented data. Unrecognized and reported data left outside of the security controls makes it easy for cybercriminals to collect and distribute. MSSPs use assets tracking to evaluate a network, identify data silos, and bring them under a single security dashboard, while at the same time, creating additional value for the company.
Threat Intelligence
MSSPs provide a general service designed to protect networks from generic threats. But some managed security services offer threat intelligence consulting and implementation where they seek to find out specific threats facing a particular company and then put in place systems to resolve them.
How BitLyft Cybersecurity Can Help
BitLyft Cybersecurity offers Co-Managed Cybersecurity to help businesses of all sizes to safeguard their systems, protect their networks and ensure no cybercriminals can steal their data. With experienced specialists helping to manage your business’s defenses and answer any security-related questions and concerns you may have, it’s the ideal solution for a convenient and flexible cybersecurity solution.
Our services aim to provide you with a simple no-nonsense solution to keep your business safe from online threats. If you’d like to learn more, don’t hesitate to get in touch with us today to speak to one of our friendly representatives. We’ll help explain the services we offer and how they can be customized to your exact needs.
