SOC for Cybersecurity

 By
Jason Miller
·
3 minute read
By
Jason Miller
·
3 minute read
In today’s world, information systems are incredibly interconnected, but this comes with a price. Because most organizations conduct some portion of their business in cyberspace, they open themselves up to a new level of risk. Who they are, what they do, and what information they possess can make businesses targets for malicious attackers. Reputation damage, disruption of business operations, fines, litigation, and loss of business can all be consequences of a cybersecurity attack. It’s more important than ever to demonstrate the extent and effectiveness of your organization’s cybersecurity risk management program.
SOC for Cybersecurity is a reporting framework for cybersecurity risk management processes and policies. It is designed to help strengthen cybersecurity programs. Introduced and designed by AICPA, it’s a solution delivered by independent CPAs to review, examine, and provide feedback on existing cybersecurity controls and systems.
What is a Cybersecurity Risk Management Program?
It is the organization’s collection of processes, policies, and controls that are put in place by management in order to protect against cybersecurity threats. It includes the systems used (apps, networks, devices, etc.), the information stored on and transmitted between systems, and user habits.
A cybersecurity risk management program is designed to protect your company’s systems and information from security threats and incidents. It’s responsible for helping the cybersecurity team detect, investigate, react to, mitigate, and ensure recovery from security events. It also includes measures that are put in place to detect and stop attacks before they are able to cause any damage.
About SOC for Cybersecurity
SOC (System and Organizations Control) for Cybersecurity is an investigation and examination process by which a cybersecurity’s cyber risk management program can be measured, inspected, and reported on. As such, it’s designed to better communicate the effectiveness of existing IT security risk management efforts to analysts, directors, regulators, and other relevant parties. To put things simply, it acts as a “gut check” for an organization’s cybersecurity practices.
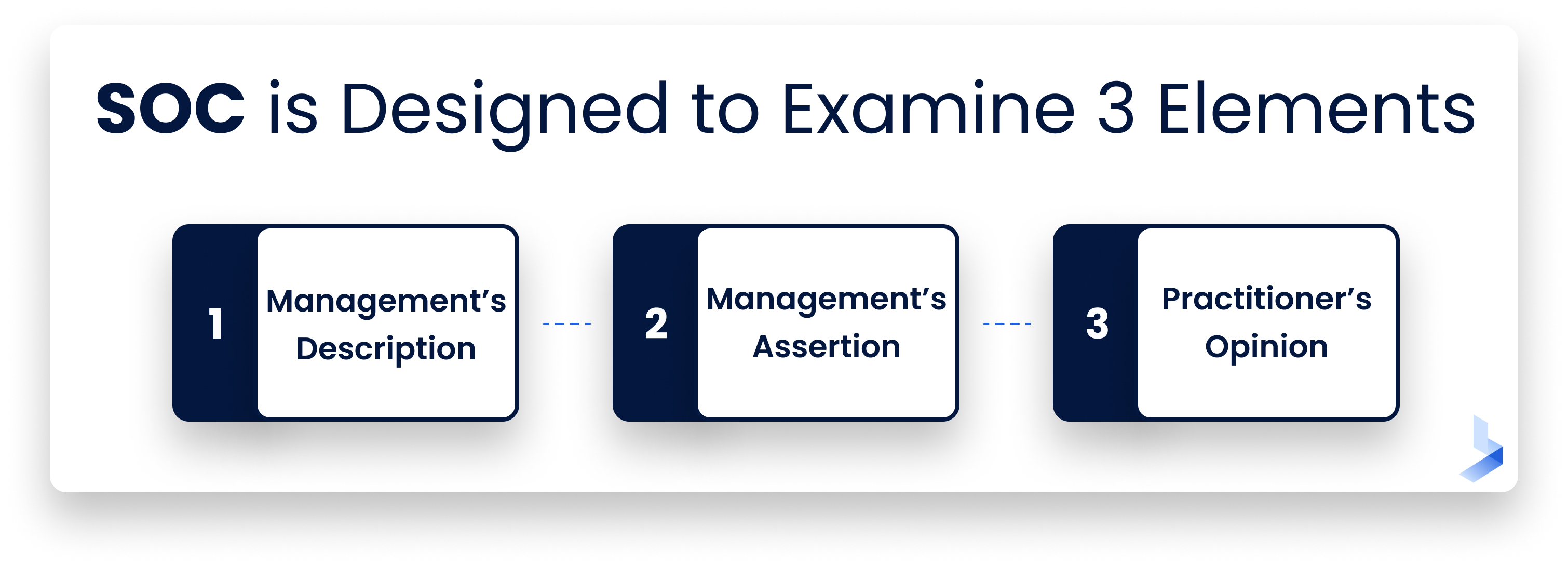
As a reporting process, SOC for Cybersecurity is designed to examine three elements in particular:
Management’s Description: Prepared by management, this is a description of the overall scope of the cybersecurity management risk program. It includes major cybersecurity policies, processes, and procedures, ways that the organization manages these risks, and the methodology used to determine which systems and data are sensitive. This is designed to provide a context to better understand the cybersecurity risk management program.
- Management’s Assertion: The management makes an assertion of how effective the cybersecurity risk management program is, as well as what the cybersecurity objectives of the organization are, and whether they are met or not.
- Practitioner’s Opinion: This is like the Management’s Assertion, but from the perspective of the CPA, on whether existing controls work in reaching the stated cybersecurity objectives.
It is important to note that the SOC for Cybersecurity doesn’t detail the controls, how they are tested, or the results of tests. Instead, it is meant for general use to show whether they are effective or not. Similarly, it does not focus on compliance with regulations and laws or privacy and processing integrity criteria. It does however, examine the effectiveness of controls that do contribute to those topics.
Do you need the SOC for Cybersecurity examination?
Digital security threats are on the rise and organizations of all sizes and in all industries need to ensure effective cybersecurity. While other IT security examinations focus more closely on the security controls, testing methodology, and so on, SOC for Cybersecurity is meant to highlight the effectiveness of existing controls for the benefit of a more general audience. As such, it’s a way of informing management, board members, analysts, investors, clients, and regulators on the health of your cybersecurity systems.
It can also be used to highlight the strengths of existing cybersecurity systems, show potential vulnerabilities, and determine what is needed to correct them. Cybersecurity teams can better make a case for new solutions and technology that they need to further improve their cybersecurity.
The Benefits of SOC for Cybersecurity
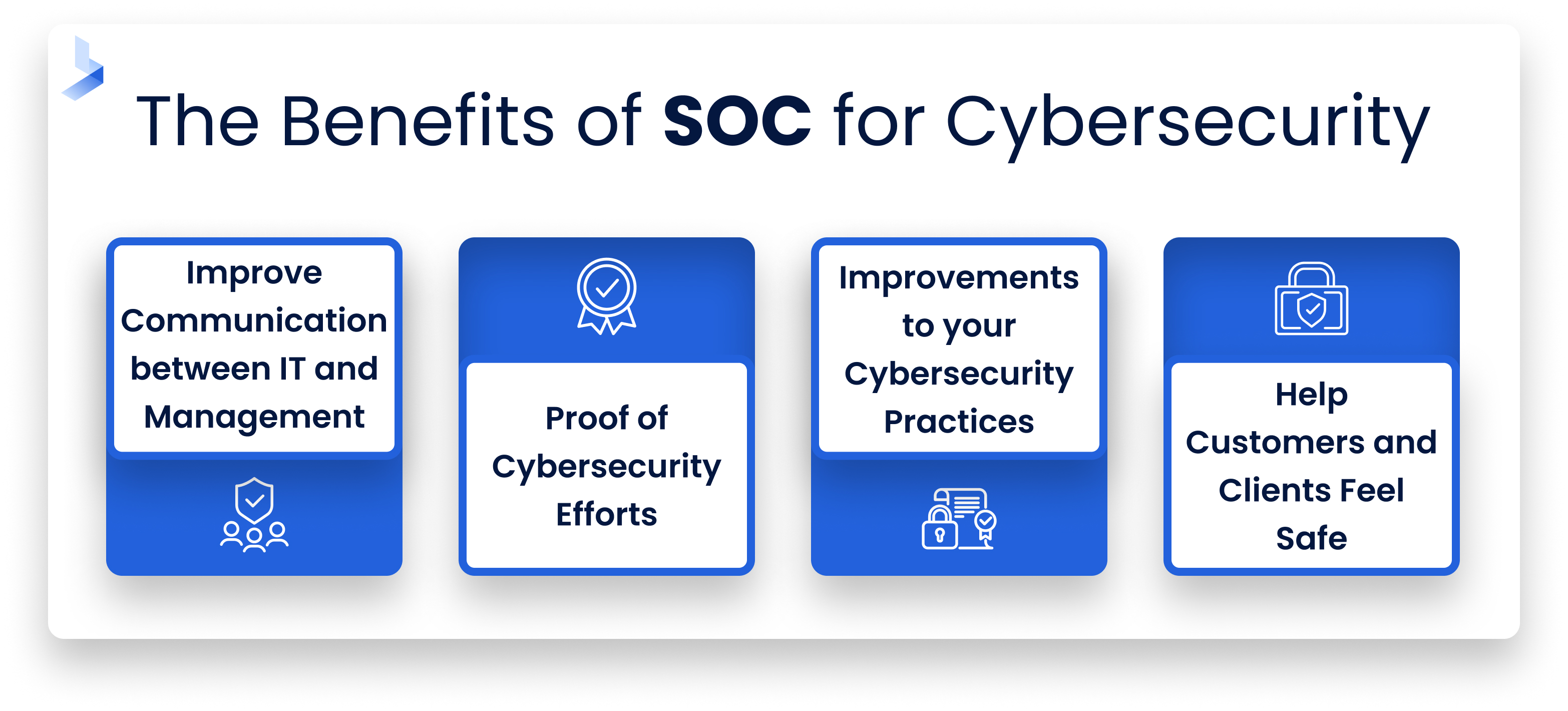
SOC for Cybersecurity examinations create a framework and language for understanding cybersecurity issues that is common to both the IT team and those that they work with. Here are some more benefits:
- Improve communication between the IT and management: The SOC for Cybersecurity provides common ground for communicating on cybersecurity issues and controls so improvements and changes can be better implemented in the future.
- Proof of cybersecurity efforts: Like other certifications and examinations, SOC for Cybersecurity demonstrates the efforts of the IT team to create a safer security scope. Furthermore, this can help improve reputation and trust from customers, clients, and partners.
- Ensure improvements to your cybersecurity practices: During the SOC examination, you may discover issues that could lead to data breaches. Addressing these issues will improve your security.
- Help your customers and clients feel safe: The results of SOC for Cybersecurity can help your customers rest easy about the fact their data is in good hands.
How to get a SOC for Cybersecurity
A SOC for Cybersecurity examination is carried out in cooperation with an independent CPA approved by the AICPA to carry out the examination. It’s important to find a certified, qualified auditor. Besides carrying out the examination itself, they are able to help you better understand the scope and details of what the description and assertions include.
Businesses with an extensive cybersecurity scope, multiple devices, networks, apps, and SaaS solutions may have need for an SOC for Cybersecurity examination. It can help show the importance of investing further IT security teams and the tools they used to secure the organization.
BitLyft is a SIEM provider and offers competitive pricing. We have a world-class team of professionals who will guard your date and ward off cyberattacks before they can cause damage to your infrastructure.
Our services aim to provide you with a simple no-nonsense solution to keep your business safe from online threats. If you’d like to learn more, don’t hesitate to get in touch with us today to speak to one of our friendly representatives.
