What Does a Virtual Security Analyst Do and Should I Hire One?

 By
Jason Miller
·
5 minute read
By
Jason Miller
·
5 minute read
As per the World Economic Forum Global Risk Report, the rate of detection for cyber threats is a measly 0.05 percent in the US. Every online business will experience some sort of cyber threat in its lifetime. It's inevitable, whether it's explicitly targeted or accidentally bot-attacked.
A virtual security analyst is someone who can help you with all your security needs, without having to bring them on staff. They can help you with everything from penetration testing to vulnerability assessments.
In this guide, we will discuss the benefits of partnering with a virtual security analyst and how they can help improve your cybersecurity posture.
Read on to get acquainted with the threat landscape and the virtual solution to its dangers.
Virtual Security Analyst: What Are They?
A virtual security analyst is a cybersecurity specialist who provides services to organizations on a contractual basis.
They are usually self-employed or work for a security consulting firm. This type of security professional offers expertise and skills to help organizations improve their overall security posture.

Furthermore, a virtual security analyst can help you with all aspects of your security operation, from planning and design to implementation and monitoring.
In other words, they can serve as your organization's cybersecurity team, even if you don't have one in-house.
Benefits of Partnering With a Virtual Security Analyst
There are many benefits of partnering with a virtual security analyst. Here are just a few:
Save Money
Hiring a full-time in-house security team can be expensive. Not only do you have to pay their salaries, but you also have to cover the cost of benefits, office space, and equipment.
When you partner with a virtual security analyst, you only have to pay for your needed services. This can help you save a significant amount of money, especially if you don't need around-the-clock security.
Expert Guidance
Virtual security analysts have the skills and knowledge to help you implement adequate security measures.
If you are not sure where to start or what steps to take, they can provide guidance and recommendations. This way, you can be confident that your organization is taking the proper steps to improve its cybersecurity posture.
Incident Response
If an incident does occur, a virtual security analyst can help you investigate and resolve it quickly.
They can also put together a plan to prevent future incidents from happening.
This is extremely important because the faster you can resolve an incident, the less damage it will cause to your organization.
Compliance
If your industry is regulated, then you likely have to comply with specific security standards.
A virtual security analyst can help you develop and implement the necessary controls to meet these compliance requirements.
They can also monitor your environment to ensure that you remain compliant over time.
Team Extension
A virtual security analyst can be an extension of your in-house security team.
This way, you can get the benefits of having a full-time security team without actually having to add a headcount.
This can be extremely helpful if you have a small security team or if your team is already stretched thin.
How Do Effective and Ineffective Virtual Security Analysts Differ?
Not all virtual security analysts are created equal. There are some that are extremely effective and others that are not so much.
Here's how they differ.
Effective Virtual Security Analysts
They have a strong understanding of cybersecurity.
They keep up with the latest trends and threats. They have experience working in various industries. They have a solid understanding of compliance requirements.
They possess strong technical skills. They have excellent communication skills. They are able to work independently.
They are proactive and take a proactive approach to security
They are always machine learning and constantly trying to improve their skills. They are team players and understand the importance of working together.
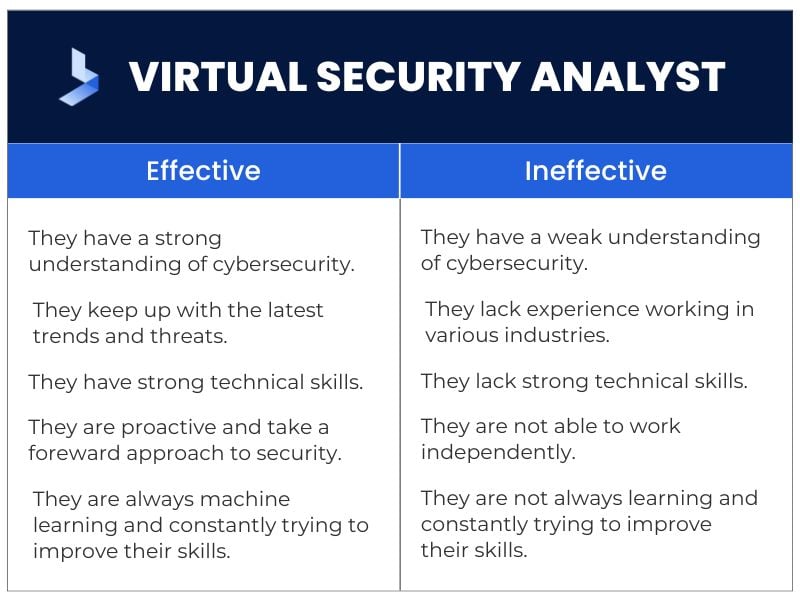
Ineffective Virtual Security Analysts
They have a weak understanding of cybersecurity. They are not up-to-date on the latest trends and threat intelligence.
They lack experience working in various industries. They do not have a solid understanding of compliance requirements.
They lack strong technical skills. They have poor communication skills.
They are not able to work independently. They are reactive and take a reactive approach to security.
They are not always learning and constantly trying to improve their skills. They are not security teams and do not understand the importance of working together.
As you can see, there is a big difference between effective and ineffective virtual security analysts.
When choosing a virtual security analyst, it's essential to make sure that they possess the qualities of an effective one.
If they don't, they are likely to be in more trouble than they're worth and could end up doing more harm than good.
How to Choose the Right Virtual Security Analyst for Your Organization
When you are looking for a virtual security analyst, there are a few things that you should keep in mind. Here are a few tips on how to choose the right virtual security analyst for your organization:
Experience Levels
When you are looking for a virtual security analyst, you should always consider their level of experience.
An inexperienced analyst may not have the knowledge or skills necessary to protect your organization adequately.
On the other hand, an experienced analyst will have the necessary expertise to help you improve your cybersecurity posture.
Proactive Approach
A good virtual security analyst is proactive about their work. They don't wait for an incident to occur before taking action.
Instead, they are always looking for ways to improve your security. This might involve implementing new controls or monitoring your environment more closely.
Being proactive helps to ensure that incidents are caught early and resolved quickly.
Responsive Analysis
If an incident does occur, you should choose a virtual security analyst who is responsive and takes quick action.
They understand the importance of resolving incidents quickly. The faster an incident is resolved, the less damage it will cause to your organization.
Additionally, a responsive analyst will keep you updated throughout the process and provide guidance on how to prevent future incidents from happening.
When you are looking for a virtual security analyst, you should look for someone who is knowledgeable about cybersecurity.
They keep up with the latest trends and threats. This way, they can be sure that your organization is protected against the latest cyber attack.
Choose a Great Communicator
An effective virtual security analyst is a good communicator. They understand the importance of communication in cybersecurity.
Communication is critical in cybersecurity because it helps to build trust and foster a good working relationship.
By choosing a virtual security analyst who is experienced, proactive, responsive, knowledgeable, and a good communicator, you can be sure that your organization is in good hands.
Common Mistakes Made With Virtual Security Analysts
There are a few common mistakes that organizations make when working with virtual security analysts. Here are a few of the most common mistakes
1. Not Defining the Scope of Work
One of the most common mistakes when working with virtual security analysts is not defining the scope of work.
When you are hiring a virtual security analyst, you should take the time to sit down and define what you expect from them. This includes their responsibilities, deliverables, and timeline.
If you do not define the scope of work, it will be challenging to hold the analyst accountable for their work. Additionally, it will be difficult to gauge whether or not they are meeting your expectations.
2. Not Establishing Clear Expectations
In addition to not defining the scope of work, another common mistake is not establishing clear expectations.
When you are working with a virtual security analyst, you should make sure that they understand your expectations, such as deep neural network usage.
This includes the level of service that you expect, the timeframe in which you expect tasks to be completed, and any specific deliverables that you are expecting.
If your expectations are unclear, it will be difficult for the analyst to meet them. Additionally, it could lead to frustration on both sides.
3. Not Meeting Regularly
Another common mistake when working with virtual security analysts is not meeting regularly.
It is essential to meet with your analyst regularly, even just for a quick check-in. This will help ensure they are on track and meeting your expectations.
Regular meetings allow you to give feedback and make necessary changes to the scope of work with artificial intelligence.
Virtual Security Done Right
A virtual security analyst can be a valuable asset to any organization. They bring with them a wealth of knowledge and experience that can help to improve your security posture.
When choosing a virtual security analyst, it is essential to consider their level of experience, their knowledge of cybersecurity trends and cyber threats, and their communication skills.
By taking the time to choose the right virtual security analyst for your organization, you can be sure that you are investing in your cybersecurity.
Get in touch with us to talk to an expert and find the solution for you.

