What is the Cybersecurity Executive Order? EO 14028 Explained

 By
Emily Miller
·
7 minute read
By
Emily Miller
·
7 minute read
President Biden issued Executive Order 14028, "Improving the Nation's Cybersecurity," on May 12. This strengthens the country's cybersecurity and safeguards vital networks. These networks underpin our economy and way of life, which is why their security is paramount.
But what exactly does this cybersecurity executive order entail? How will the executive order impact the IT industry?
If you want to learn more about the new executive order 14028, you've come to the right place. Keep on reading to find out more about this cybersecurity executive order.
Key Points of Executive Order 14028
- Executive order 14028 eliminates obstacles to sharing threat information. This means threat information can get shared between the public and private sectors. The EO guarantees that IT service providers may communicate with the government. It also obliges them to provide specific breach data.
- It modernizes and improves the strength of cybersecurity standards. This includes the federal government. The EO requires the adoption of multi-factor authentication. It also requires encryption within a certain time frame. Additionally, it aids in the Federal Government's transition to secure cloud services. The government also is transitioning to a zero-trust architecture.
- Executive order 14028 improves supply chain software security. By setting the smallest security requirements for software supplied to the government, software security increases. What's more, it establishes a pilot initiative to build an "energy star" label. This is so that the government and the general public may find out if the software is safe.
- The order also puts a Cyber Safety Review Board into place. The EO creates a Cyber Safety Review Board that has the power to meet after a serious cyber event. They do so to assess what transpired and offer specific suggestions for enhancing cybersecurity. The board will be co-chaired by government and private sector leaders. This body comes from the National Transportation Safety Board.
More Points of EO 14028
- Executive order 14028 develops a standardized playbook for handling cybersecurity incidents and flaws. The EO establishes a common playbook for government departments and agencies. The playbook helps agencies when responding to cyber vulnerability incidents. The playbook will make sure that every government agency reaches a specific standard. It also helps the agency be ready to take consistent action to recognize and reduce danger. It will also act as a model for the private sector to follow. This will help when coordinating response operations.
- Detection of cybersecurity incidents on federal government networks is also improved. An endpoint detection and response (EDR) system for the government is possible by the EO. The EO increases the capacity to identify hostile cyber activities on federal networks.
- Enhancing investigative and remediation capabilities is another benefit. The EO establishes cybersecurity event log specifications for federal departments and agencies. This is to enhance an organization's capacity to identify intrusions. It's also to help counteract those that are already underway. Additionally, it assesses the scope of an incident after it has already happened.
What Does Executive Order 14028 Signal?
When broken down simply, executive order 14028 signals two things.
First, it suggests strengthening government systems to make them more difficult to breach. It promotes particular initiatives, such as zero trust architecture, to upgrade cybersecurity. Additionally, it exploits the federal government's $70 billion IT budget. This adds pressure on the industry to include security in all software from the start.
It establishes a target for more efficient responses from the federal government. It removes restrictions on IT service providers' sharing of information with governmental bodies. It also mandates that they disclose cyber events. The EO also harmonizes the incident response playbook used by several agencies.
It is an issue of trust and national security. The confidence we put in our digital infrastructure, according to the EO, "should be proportional to how trustworthy ... that infrastructure is.."
The response to nation-state supply chain assaults will continue to include more steps. Sean Joyce, leader of PwC's global and US cybersecurity, stresses more action. He says, "The United States needs a more structured approach to cyberthreats." Governments have already been slow to update our laws, rules, and corporate obligations. They are also slow to adapt to a digital, borderless world.
What Is Cybersecurity?
The practice of defending against and recovering from cyberattacks is cybersecurity. Your sensitive data is at risk from cyberattacks. Cyberattacks are becoming more complex and dynamic as hackers use innovative techniques. These techniques combine social engineering and artificial intelligence (AI) to breach security measures.
The world is becoming more and more dependent on technology. This dependence will only increase as we develop new technologies. These technologies connect our gadgets via Bluetooth and Wi-Fi in the future.
Intelligent cloud security solutions must get implemented. So should strict password regulations like multi-factor authentication. This is to reduce illegal access to safeguard consumer data. This can happen while embracing new technologies.
Why Is Cybersecurity so Important?
Cybersecurity is crucial since it guards against data breaches. This covers delicate information and information systems used by the government and businesses. Your company cannot protect itself against data breach operations without a cybersecurity program.
Due to increased worldwide connection and the use of cloud services, risks are rising. The probability that your firm may experience a cyber attack is also increasing. This is a result of the widespread bad setup of cloud services. It's also a result of increasingly savvy cybercriminals.
Individuals cannot exclusively rely on standard cybersecurity tools like firewalls and antivirus software. This is because hackers are growing more cunning. Plus, their strategies are becoming more resistant to traditional cyber defenses. To keep secure, it's crucial to cover all aspects of cybersecurity.
Cyber risks might originate at any level. To inform personnel about typical cyberthreats, workplaces must offer cybersecurity awareness training.
Because of the prevalence of data breaches, cybersecurity is important across all sectors. It's not only for those with strict regulations like the healthcare sector. Following a data breach, everyone is in danger of incurring irreparable harm to your reputation.
Who's Affected by Executive Order 14028?
Federal executive agencies must update their technological infrastructure and security procedures.
New cybersecurity requirements will be in contract conditions for federal contractors. This includes COTS software companies. They will have to divulge more details about cyber incidents.
Software supply chain security and transparency will get attention from the private sector. Companies that make software and IoT devices should prepare for new security regulations. They should also prepare for assessment standards as a result.
The EO also charges NIST with two labeling initiatives for consumer Internet of Things (IoT) devices and software, with the aim of incentivizing manufacturers to build goods and informing consumers about those items designed with more awareness of cybersecurity risks and capabilities.
Impacting the IT Industry
IT services are the application of technical and business know-how to help firms create, manage, and access information and business processes.
Because IT service deals with cybersecurity and data protection, the new executive order is making it easier for IT support to implement higher-quality software.
Cybersecurity will improve dramatically as the IT industry is given the tools to better prevent and manage cyber threats.
Zero-Trust Maturity Model
In the face of a network that is perceived as compromised, zero trust offers a set of concepts and ideas that are intended to reduce ambiguity in enforcing precise, least privilege per-request access choices in information systems and services.
Achieving the highest level of granularity in access control enforcement will help prevent unwanted access to data and services. In order to provide fine-grained security restrictions across individuals, systems, data, and assets that vary over time, zero trust represents a transition from a location-centric paradigm to a more data-centric one.
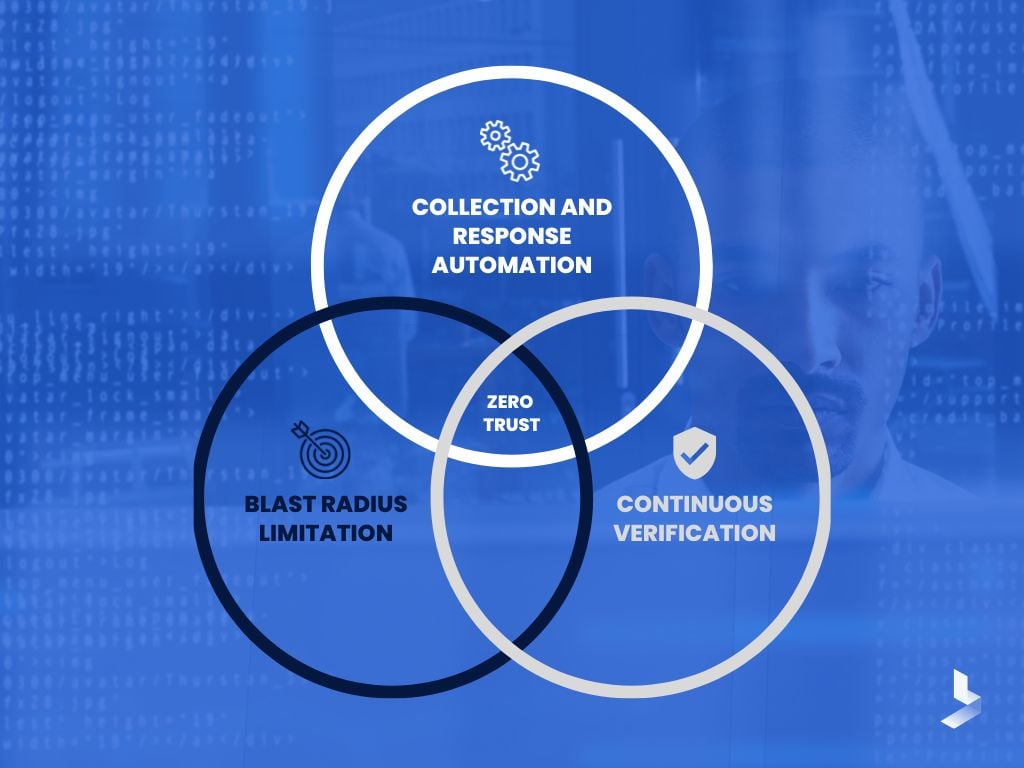
This gives security policies the visibility they need to be developed, put into practice, enforced, and evolved. A more fundamental shift in an organization's cybersecurity culture and attitude may be necessary as a result of zero trust.
Agencies will embrace zero-trust cybersecurity concepts. This means that they will modify their network infrastructure. This is in accordance with Executive Order 14028.
The Cybersecurity and Infrastructure Security Agency (CISA) created a zero trust maturity model. This is to give agencies a road map and resources to reach an ideal zero-trust environment.
Biden's EO mandates that agencies develop strategies to adopt the Zero Trust Architecture.
Applying Zero Trust Principles to Enterprise Mobility is a document that CISA has issued. It aims to assist government agencies. It also helps other businesses on their path to zero trust. The widespread usage of mobile devices and business security management capabilities, get addressed.
Playbooks for Addressing Cybersecurity Incidents
An efficient strategy for managing vulnerabilities and events is collaboration. This means across all federal government entities. Two playbooks created by CISA in accordance with Section 6 of E.O. 14028 are for this purpose.
Federal systems, data, and networks get affected by these events and vulnerabilities. Playbooks give the federal business a common set of processes. These processes outline how to detect, coordinate, remediate, recover, and track effective mitigations.
These playbooks advance federal government practices for cybersecurity response. They do so by standardizing shared practices. These practices bring together the best people and processes to drive coordinated actions. They do this by building on lessons learned from prior incidents. What's more, they incorporate industry best practices.
These playbooks advance federal government practices for cybersecurity response. They do so by standardizing shared practices that bring together the best processes. This helps to drive coordinated actions. They do this by building on lessons learned from prior incidents. Plus, they incorporate industry best practices.
The uniform practices and guidelines outlined in these playbooks:
- Improve coordination and efficiency of the impacted organizations' reaction
- Track successful cross-organizational activities
- Permit cataloging of occurrences for improved event management in the future
- Assistance in research and analysis
These playbooks should get used by agencies to assist in defensive cyber operations. This is so that reaction times are predictable, efficient, and coordinated. These playbooks allow organizations to concentrate on the standards for coordination and reporting. They also contain the criteria for responding. Agencies, including CISA, can comprehend the effects of proven hostile cyber activity. They can also respond to vulnerabilities.
The Incident Response Playbook
By releasing the Federal Government Cybersecurity Incident and Vulnerability Response Playbooks, CISA has completed its mission. These documents offer guidance on how FCEB agencies should react to security events including vulnerabilities and take corrective action.
The Incident Response Playbook outlines the steps of the incident response stages. These stages get specified by the National Institute of Standards and Technology (NIST). They offer a standardized response method for cybersecurity issues.
Additionally, it explains the steps FCEB authorities should take during a cyberattack.
The Vulnerability Response Playbook
The Vulnerability Response Playbook standardizes top-level procedures that agencies must adhere to. They must refer to it when reacting to high-priority vulnerabilities. However, current vulnerability management programs should not get ignored.
It also identifies and fixes vulnerabilities. These vulnerabilities get noticed by the impacted agency or others working in the area.
Since cybersecurity risks sometimes don't appear odd at first look, it's crucial to confirm security. Examine everything you receive much more thoroughly before replying to an email or clicking a link. If it has grammatical problems, uses bizarre language, is unusually urgent, or otherwise appears wrong, it may be a trap.
The same idea holds true for internet networks, hardware, and software. Never put your confidence in free WiFi since it might be used for MITM attacks by anyone. Similar to this, before downloading and installing an application, be sure the developer is reliable.
This should be applied to commercial partners as well.
Now You Know All About Cybersecurity Executive Order 14028
To better fight against criminal cyber attacks, President Biden issued an Executive Order. This EO's mission involves strengthening the nation's cybersecurity.
Get More Cybersecurity News Updates
BitLyft is here to help you keep up with the ever-changing cybersecurity landscape. Sign up for our email newsletter to get all the latest information about cybersecurity news, topics and trends.
