Next-Gen XDR vs. XDR: What is the Difference?

 By
Emily Miller
·
7 minute read
By
Emily Miller
·
7 minute read
Did you know that nearly 50% of businesses fail within the first five years? The good news is that there are steps you can take in order to prevent this scenario.
By now, you've probably heard the term XDR. XDR stands for extended detection and response and is a critical part of your cybersecurity strategy.
But what are your Next-Gen XDR options? Do you go with a cloud-based or on-premises solution? How do you know which one is right for you?
Well, don't worry. Keep reading because our article, Next-Gen XDR vs. XDR security: What is the Difference, can help. It provides an in-depth comparison of the two solutions, so you can make an informed decision about which one is right for your business.

What Is Next-Gen XDR?
Next-gen XDR is a new approach to cybersecurity that combines the best features of several different technologies. This approach provides a more comprehensive view of your security posture and can help you more quickly identify and respond to threats.
Next-gen XDR is an integrated platform that brings together data from multiple sources, including EDR, SIEM, and SOC. This platform uses artificial intelligence to correlate this data and provide insights into your security posture.
This approach can help you more quickly identify and respond to threats, as well as improve your overall security posture, and we will showcase the benefits of next-gen XDR in this article.
What Is XDR?
Extended detection and response (XDR) is a security solution that integrates multiple security tools and technologies. This approach provides a more holistic view of your security posture and can help you more quickly identify and respond to threats.
The goal of XDR is to improve detection rates, shorten the mean time to detection (MTTD), and reduce false positives. By integrating EDR and SIEM, XDR can provide a more complete picture of your environment and help you detect threats that would otherwise go undetected.
Additionally, XDR can automate the investigation and response process, which can help save time and resources. Implementing an XDR solution can be a complex undertaking, but the benefits of this approach make it well worth the effort.
| Related Reading: XDR Security 101: Understand Its Power, Unleash Its Potential |
Disadvantages of Traditional XDR Security
Now that we've looked at some of the benefits of next-gen XDR, let's take a look at some of the disadvantages of traditional XDR security.
1. Lack of Integration
One of the biggest disadvantages of traditional XDR security is that it lacks integration. This is because traditional XDR security relies on multiple disconnected products and silos of data within those products. This can make it difficult to get a complete picture of your security posture and can slow down threat detection and response.
To overcome this disadvantage, many organizations are now turning to next-generation XDR solutions that offer complete integration. Next-generation XDR solutions are designed to work together from the ground up, sharing data and insights across the entire platform.
This allows you to get a complete view of your security posture and speeds up threat detection and response times.
2. Inefficient Threat Detection and Response
As enterprises become increasingly reliant on digital technologies, they are also becoming more vulnerable to cyberattacks. To address this growing threat, many organizations have adopted a security approach known as extended detection and response (XDR).
XDR security is a unified platform that combines multiple security solutions, including firewalls, intrusion detection and prevention systems, and endpoint security. While XDR security offers many benefits, it also has some disadvantages.
One of the biggest disadvantages of XDR security is its efficiency in terms of threat detection and response. This is because traditional XDR security relies on manual processes, which can be time-consuming and error-prone.
Additionally, traditional XDR security often lacks features like machine learning and artificial intelligence, which can help automate threat detection and response. As a result, organizations that rely on XDR security may be at a disadvantage when it comes to detecting and responding to common cyber threats.
3. High Costs
While traditional XDR security can be costly, there are some steps that organizations can take to help reduce costs. One way to do this is to purchase products from a single vendor. This can help to reduce the overall number of products that need to be purchased, and it can also make it easier to manage costs.
Additionally, organizations can look for vendors who offer discounts for purchasing multiple products. Another way to reduce costs is to automate some of the manual processes involved in traditional XDR security. This can help to save time and money by reducing the need for manual work.
Finally, organizations can use open-source tools whenever possible. Open-source tools are often free or low-cost, and they can provide a high level of security. By taking these steps, organizations can help to reduce the costs associated with traditional XDR security.
4. Lack of Visibility
Lack of visibility is a common problem with traditional XDR security solutions. This is because these solutions often silo data within multiple products, making it difficult to get a complete picture of your security posture. This can lead to slowed threat detection and response times, as well as an increased risk of missed or false-positive threats.
To combat this problem, many organizations are now turning to next-generation XDR solutions that provide comprehensive visibility into the entire network. These solutions use cutting-edge machine learning and artificial intelligence technologies to constantly monitor network activity and quickly identify potential threats.
As a result, they can provide a much higher level of visibility and protection than traditional XDR solutions.
5. Poor Compliance
One of the potential disadvantages of traditional XDR security is that it can lead to poor compliance in your organization. This is because traditional XDR security silos data within multiple products. This can make it difficult to get a complete picture of your security posture and can slow down threat detection and response.
Additionally, traditional XDR security often lacks features like machine learning and artificial intelligence, which can help automate compliance processes. As a result, organizations using traditional XDR security may find it difficult to meet compliance requirements.
In contrast, next-generation XDR platforms that leverage machine learning and artificial intelligence can help simplify compliance processes and improve overall compliance rates.
6. Limited Protection Against Today's Threats
While traditional XDR security can offer some protection against cybersecurity threats, it has several limitations that leave organizations vulnerable. One of the biggest limitations is that traditional XDR security silos data within multiple products.
This can make it difficult to get a complete picture of your security posture and can slow down threat detection and response. Additionally, traditional XDR security often lacks features like machine learning and artificial intelligence, which can help you more quickly identify and respond to threats.
As a result, organizations that rely on traditional XDR security may be at a higher risk for cyberattacks.
Next-gen XDR Can Help Address the Disadvantages of Traditional XDR Security
Now that we've looked at some of the disadvantages of traditional XDR security, let's take a look at how next-gen XDR can help address those disadvantages.
1. Better Integration
Traditional XDR security tools offer a limited view of your organization's security posture. This is because they only collect data from a single source. Additionally, traditional XDR tools lack features like machine learning and artificial intelligence, which can automate threat detection and response.
As a result, next-gen XDR offers better integration than traditional XDR security. Next-gen XDR integrates data from multiple sources and provides a more comprehensive view of your organization's security posture.
Additionally, next-gen XDR includes features like machine learning and artificial intelligence, which can help automate threat detection and response. As a result, next-gen XDR is a more effective tool for managing your organization's security posture.
2. More Efficient Threat Detection and Response
Just as important as detecting threats is responding to them quickly and effectively. Next-gen XDR can help you do both of these things more efficiently. By integrating data from multiple sources, next-gen XDR provides a more complete picture of your security posture.
This allows you to more quickly and accurately identify potential threats. Additionally, next-gen XDR uses machine learning and artificial intelligence to automate threat detection and response. This means that you can respond to threats more quickly and effectively, without having to rely on manual processes.
As a result, next-gen XDR can help you improve both your threat detection and response times, making your overall security posture more effective.
3. Lower Costs
As data and threats become more complex, organizations are turning to next-gen XDR for security. Next-gen XDR is a more comprehensive approach to security that can provide better protection and visibility. Additionally, next-gen XDR can be less costly than traditional XDR security.
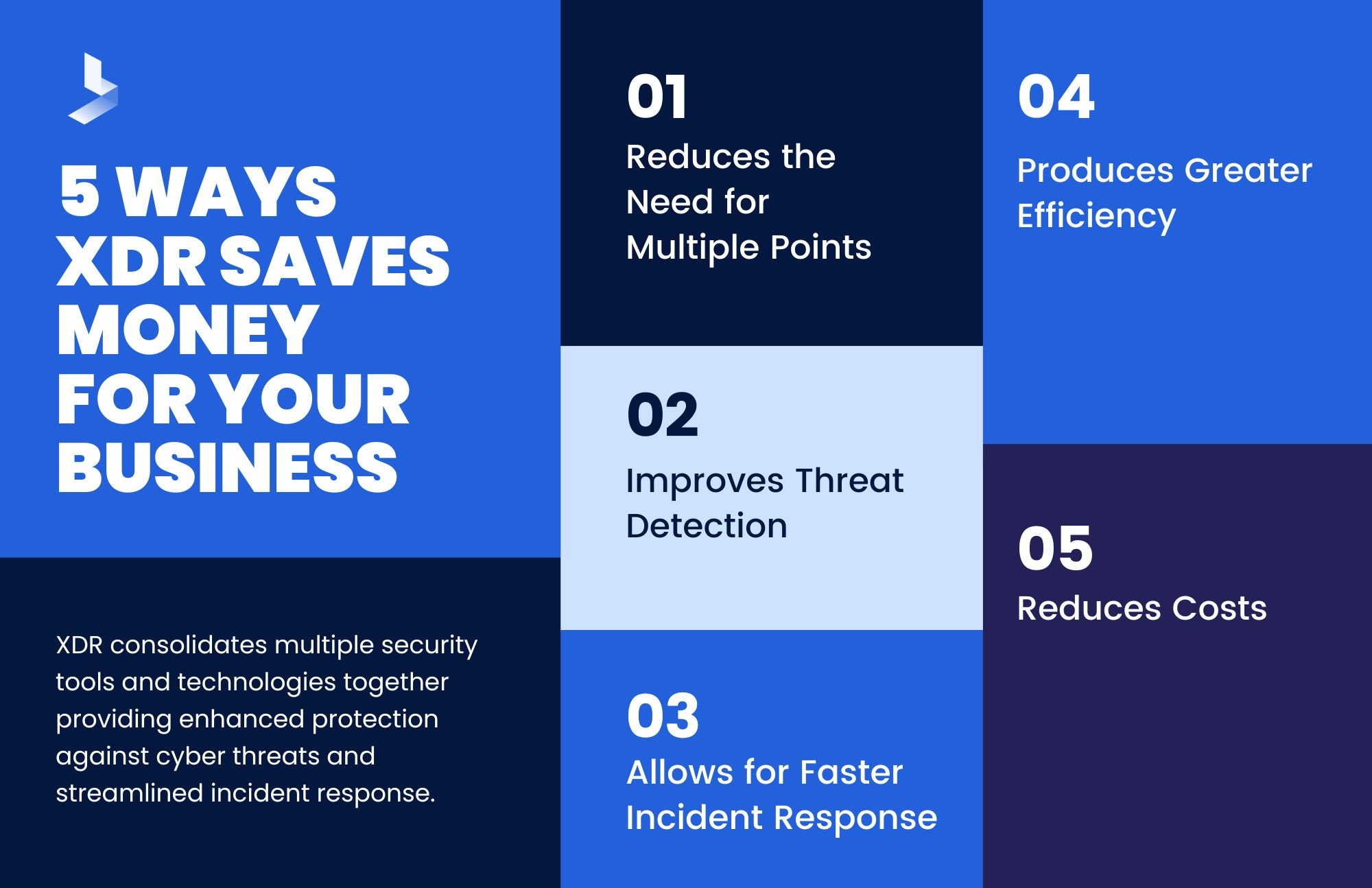
This is because next-gen XDR often requires the purchase of fewer products and can be less expensive to operate. Additionally, next-gen XDR often integrates with existing security infrastructure, which can help reduce costs.
As organizations continue to face new challenges, next-gen XDR will become an increasingly important part of their security strategy.
4. Greater Visibility
As organizations increasingly rely on digital systems and data, the need for comprehensive security solutions has never been greater. Next-generation extended detection and response (XDR) is a new type of security platform that promises to provide greater visibility into your network and more effectively identify and respond to threats.
Next-gen XDR integrates data from multiple sources and provides a more comprehensive view of your security posture. This allows you to identify potential threats and take steps to mitigate them before they cause serious damage.
Additionally, next-gen XDR includes features like machine learning and artificial intelligence, which can help you more quickly identify and respond to threats.
By implementing a next-generation XDR solution, you can improve your organization's overall security posture and better protect your digital assets from harm.
5. Improved Compliance
Organizations face compliance requirements from a variety of sources, including government regulations, industry standards, and contractual obligations. Meeting these compliance requirements can be a challenge, particularly as they often evolve.
Next-gen XDR can help improve compliance in your organization by integrating with existing compliance infrastructure and automating compliance processes. Additionally, next-gen XDR's machine learning and artificial intelligence capabilities can help you identify and respond to threats.
As a result, next-gen XDR can play a key role in helping your organization meet its compliance obligations more.
6. Greater Protection Against Today's Threats
As anyone who has followed the news knows, security threats are constantly evolving. What might have been a minor nuisance a few years ago can now pose a serious risk to your business. That's why it's important to have a security solution that can adapt to the changing landscape.
Next-generation XDR (extended detection and response) is designed to do just that. By integrating data from multiple sources and using advanced features like machine learning and artificial intelligence, next-gen XDR can provide a more comprehensive view of your security posture.
Additionally, next-gen XDR malware protection software is designed to be more agile and responsive, so you can more quickly identify and respond to threats. As the world of security becomes increasingly complex, next-gen XDR offers a powerful tool for staying one step ahead of the threats.
Next-Gen XDR vs XDR Security: Which One Wins?
Although security requirements may seem complicated to understand at first, next-gen XDR works to provide businesses with a comprehensive XDR security solution. If you're looking to improve your security posture, you should consider using next-gen XDR. This will allow you to have visibility into potential threats and the ability to respond quickly and effectively.
Want to learn more about what we can do? Be sure to reach out to us today and see how can help you.
