Anatomy of a Phishing Email: How to Spot a Fake

 By
Emily Miller
·
8 minute read
By
Emily Miller
·
8 minute read
Phishing emails are a major concern for business owners, and for good reason. One in 99 emails is a phishing attack, and roughly 90% of data breaches occur on account of phishing. As businesses across all industries recognize the risks presented by increasing cyberattacks and improve their cybersecurity efforts, cyberattackers turn to deceptive methods of attack. Social engineering describes a group of cyberattacks that use deception to convince users to compromise network security. Phishing emails are one of the most common forms of social engineering attack.
Phishing emails are deceptive forms of communication designed to trick the user into sharing sensitive information or performing an action that could jeopardize the security of a network. The goal of a phishing attack is to gain the trust of a user as a way to acquire access to accounts, breach a network, or deploy malware. Sometimes, a convincing phishing email can lead to a transfer of funds into an attacker's account.
Phishing attacks bypass security tools and systems by exploiting human emotions. They often rely on urgency or fear to act as a distraction and speed up response times. Attackers go to great lengths to make phishing emails look legitimate with company logos and other company signatures. Phishing emails usually include links, downloads, or instructions for the user to correct a supposed problem. If the user takes the bait, they are redirected to a fake website, download an attachment containing malware, or share sensitive information.
Modern, sophisticated phishing attacks are very difficult to detect and often mimic company correspondence or communications with vendors or other third-party business partners. These attacks frequently circumvent traditional cybersecurity tools and go directly to targets. The nature of a phishing attack makes it crucial for company personnel and employees at all levels to identify and avoid phishing emails.
This guide describes the characteristics of phishing emails, tips for identifying and avoiding them, and additional resources for further learning and protection.
What is a Common Indicator of a Phishing Attempt?
While it's true that phishing emails are difficult to detect, they do have certain characteristics that can make them more recognizable. A phishing email sent to a personal or business email may have any or all of these characteristics.
Suspicious Sender
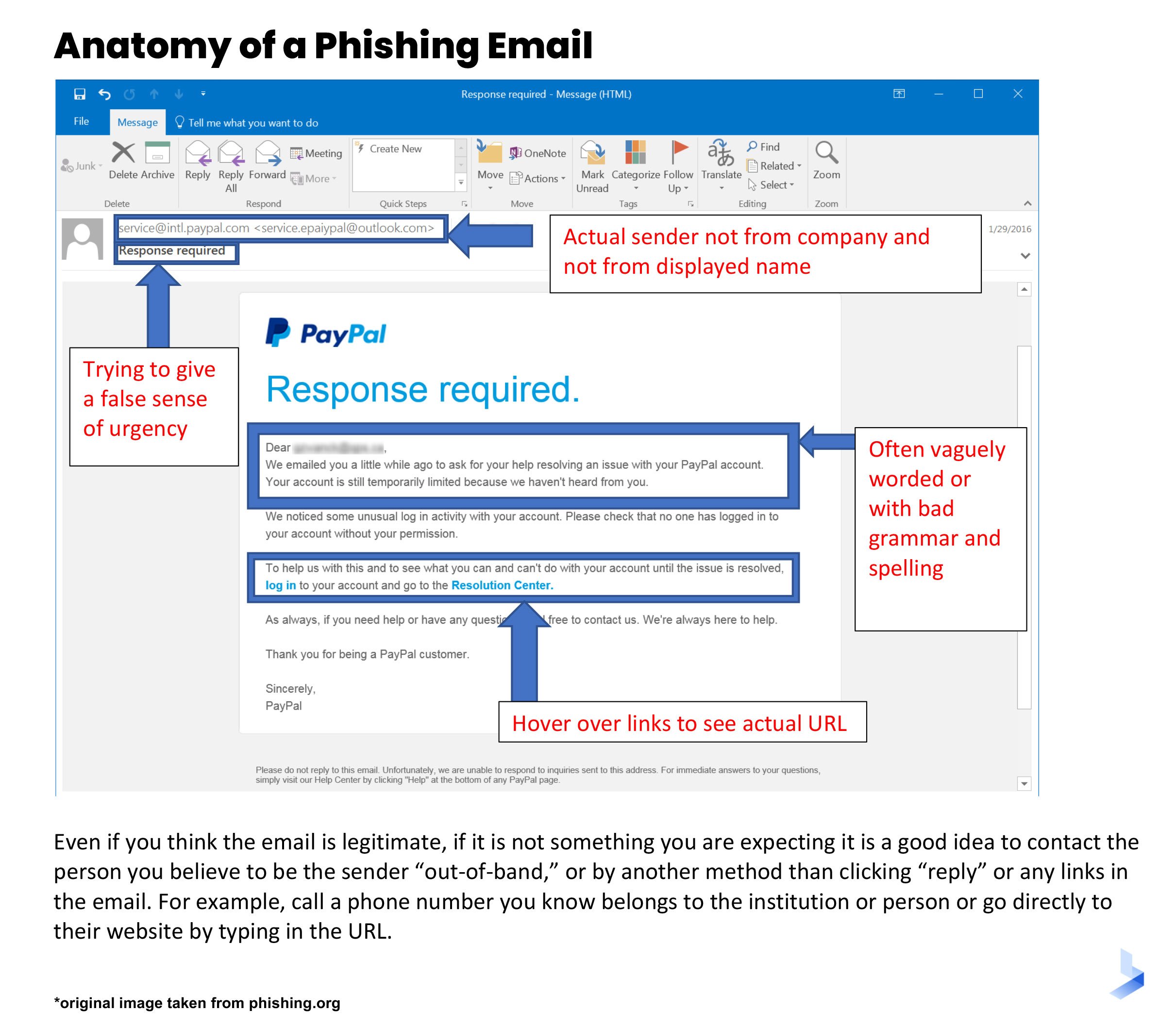
Most phishing emails claim to be sent from a trusted source. However, the attacker may not have access to a valid sender's address. Unless the hacker managed to compromise a legitimate email account, they will have to use a false "from" address. Most often, the attacker will take great pains to make the email appear genuine. To make the spoofed email address look as close to the original sender as possible, the address may have minor misspellings that are easily overlooked, or use a Gmail or Yahoo address instead of a valid corporate email.
Urgent or Threatening Language
Phishing emails depend heavily on the manipulation of human emotions. In an attempt to avoid a practical response, phishing emails often use urgent or threatening language to make the target respond quickly. It's common for these emails to say there is a problem that must be resolved quickly to avoid consequences. Some examples of common language in phishing emails include:
- A claim that suspicious activity or login attempts have occurred on your account
- A request to confirm personal or financial information
- Include a link to make a payment for products or services that have supposedly already been received
- Claim there's a problem with account or payment information
- Include a fake order confirmation or invoice
Request for Personal Information or Credentials
The goal of phishing emails is often to gain access to a company network. When attackers can retrieve personal information or login credentials, they can move discreetly through a company network to gain access to sensitive information. Most phishing emails use some type of story to request personal information. For example, the email may say you need to update your account information or provide additional information to prove your identity.
Legitimate businesses do not reach out to individuals for credit card information, social security numbers, or passwords by email. Similarly, third-party vendors or business partners won't ask for sensitive information. If an email suggests you reply with sensitive information or requires you to click on a link to provide login or billing information, it is likely a scam.
Suspicious Attachments or Links
Safe company download and information-sharing practices should discourage the use of email for attachments or redirection through links. Legitimate businesses don't send emails with attachments you're not expecting. Similarly, business partners or vendors should direct you to their websites to download documents or files. Links are also often a red flag. Inspect links to determine whether the domain matches the sender by hovering the cursor over the link to display the URL.
Tips for Spotting and Avoiding Phishing Emails
Understanding the basic anatomy of a phishing email isn't enough to prevent your company from becoming the victim of a cyberattack that begins with a phishing email. When you put specific email processes in place, employees are less likely to fall for the urgent nature of a phishing email. Beyond learning the characteristics of phishing emails, users can take additional steps to avoid falling victim to phishing emails.
Request Verification
As phishing emails and other social engineering attacks become more sophisticated and convincing, businesses need to create policies that require employees to question all forms of indirect communication. To achieve this level of security, many organizations are turning to zero-trust security models. Zero trust security starts with the assumption that everyone and everything is untrusted.
Phishing emails often appear to come from trusted senders. However, requests found in phishing emails are typically unusual. When every request requires verification, a phishing email can quickly be exposed for the fraudulent activity it is. If you receive an email from a trusted source requiring you to download materials, follow a link, make a payment, or provide sensitive information, contact the source through a different communication method for verification.
Beware of Suspicious Emails and Attachments
It's important to understand that every unsolicited email could be a phishing attack. When you receive an unexpected email that requests you to act quickly, be cautious. Take time to consider the characteristics of phishing emails and whether they apply to the email. Take these steps to consider the anatomy of a phishing email.
- Check the domain name of the sender. Does it use a corporate domain name or a public email domain like Gmail or Yahoo? When you hover your cursor over the sender's name field, does the domain name match? Remember to look closely for misspellings.
- Consider the greeting. Most companies and trusted individuals will address the recipient by name in the body of the email. Beware of emails that begin with "Dear User" or "Dear Member".
- Inspect the spelling and grammar. Check the email's domain name and entire text for incorrect spelling or grammar not consistent with the company's expected tone. Look closely for similar misspellings that appear correct. For example, an "r" next to an "n" could easily mimic an "m". Repeated exclamation points to add urgency are often found in phishing emails.
- Examine the language. Does the email pressure you to act right away? Legitimate companies do not make demands or use pressuring language.
- Consider the request. Does the email ask you to take any action that could expose sensitive information or redirect your activity to a potentially dangerous website?
- Look for links and attachments. No unsolicited email from a reputable business will include attachments or unusual links. Never download an attachment you weren't expecting, and avoid using links in emails. Instead, open a new browser window to go to the legitimate company website.
Look for Mistakes
Spelling "mistakes" create a sneaky way for hackers to create domain names that are similar to legitimate ones. One wrong letter in a domain name is incredibly easy to overlook, especially for an employee who fields hundreds of emails during a single workday. Other red flags include unusual fonts and incorrect or unexpected grammar.
Avoid the Urge to Click
While clicking on links and attachments are a convenient way to quickly get things done, it's vital to avoid the click impulse when it comes to unsolicited email. It's common for phishing emails to include attachments and downloads that go along with the request. For example, a phishing email to collect funds may include an attached invoice. An email supposedly coming from a coworker or HR staff member might claim to have related documents attached. In either of these cases, the attachment or download will likely offer a seemingly benign document matching the description. Yet, by completing the download, you could have introduced malware into the company network.
Similarly, most links found in emails use a button with hyperlinked text that describes an action like "Pay Your Bill", "Update Your Account", "Visit the Help Center", or "Change Your Payment Method". While the link makes a clean email with clear instructions, it also hides the destination address. Before clicking on any link, check where links go before opening them. On a computer, you can hover your mouse over the link to expose the destination address in a small bar. On a mobile device, hold down on the link and a pop-up will appear containing the link.
Resources for Further Learning and Protection from Phishing
Like other cyberattacks, phishing emails are constantly evolving. As such, it's vital to seek continual education about attacks on the horizon. By staying up-to-date about the changing nature of phishing attacks, you're more likely to effectively identify and avoid them. These resources can help you learn more about phishing emails and ways to identify and block them from reaching their targets.
Online Guides and Tutorials
Knowledge is power when it comes to avoiding phishing emails. Luckily, there are reputable companies that consistently update resources that assist individuals and businesses in recognizing and avoiding the dangers of phishing emails.
- Phishing.org offers resources for testing and identifying phishing attacks.
- The Anti-Phishing Working Group (APWG) provides a way for companies to report phishing attacks and publishes an annual Phishing Activity Trends Report to highlight evolving threats.
- Blogs regularly updated by cybersecurity professionals can offer a plethora of information about email threats and other cybersecurity threats that can endanger businesses and individuals.
- The Office of the Comptroller of Currency provides a series of articles to help identify, stop, and report phishing attacks.
- The Federal Trade Commission (FTC) has a phishing resource page that includes press releases, blog posts, events, reports, and videos.
- CISA provides free cybersecurity resources services and tools to reduce cybersecurity risks, including phishing.
Anti-phishing Software and Email Filters
Hackers work hard, but cybersecurity professionals work harder. Phishing emails can only be effective if they reach their intended target. When you add modern antiphishing software and email filters to your cybersecurity efforts, you can prevent phishing emails from reaching the inboxes of your employees. For example, secure email gateways filter dangerous emails before they reach the user's inbox. Security tools that feature AI use existing information to identify and block known malicious senders. The most effective tools against phishing offer a multi-layered approach.
- Advanced Email Security: Email prioritizes convenience over security. However, changing email defaults can improve security efforts. By enabling link protection and preventing email downloads, many email phishing attacks can be thwarted. When you invest in advanced email protection, a plan may include login security, email encryption, spam filtering, fraud protection, and cybersecurity education for all levels of employees.
- Intrusion Detection and Detection: Most businesses have firewalls in place to block malware from making it into the network. Yet, without systems to block malware from spreading after an entry point (like a phishing email) is exploited, phishing attacks can still be successful. AI-based detection and response systems are designed to recognize suspicious activity in a network and take action to quarantine the threat. This can stop an attacker from advancing beyond the initial action taken by the email user.
- AI-based Network Detection and Response (NDR): Network detection and response monitoring uses a baseline of normal behavior for users and entities on a network to recognize suspicious behavior. AI-based NDR tools send alerts and can take action to quarantine threats. These tools can be particularly useful when legitimate email accounts are compromised.
Cybersecurity Awareness Training Programs
Employees can't fight against attacks they have no knowledge of. Modern phishing emails aren't poorly written or easy to detect. They are sophisticated documents that accurately mirror existing brands or organizational communications almost perfectly. A phishing email is only effective when the targeted user takes the bait, making phishing awareness one of the most powerful tools in any business's arsenal. Some of the top cybersecurity awareness training programs to help identify phishing emails include:
- Cofense: Awarded "Best for Phishing" by eSecurity Planet
- KnowBe4: Awarded eSecurity Planet's Best Cybersecurity Awareness Training for 2022
- Proofpoint: Awarded a top Cybersecurity Awareness Training Program by eSecurity Planet
Avoid the Dangers of Phishing Emails with Up-to-Date Knowledge and Tools
Modern phishing attacks are sophisticated, and preventing them requires a multifaceted approach. While modern phishing emails use digital technology and convincing methods to appear legitimate, they have certain markers that can make them easier to identify. The more information your employees have about the anatomy of a phishing email and the tactics commonly used by attackers, the less likely they are to become the victim of an attack. Modern cybersecurity tools and software are also a critical part of fighting against phishing attacks. These tools identify and block malicious emails before they reach their intended targets.
Email is one of the most useful communication tools for any business. Yet, without the right precautions in place, it can represent a dangerous vulnerability to invite attackers into your network. If you're unsure about the vulnerabilities presented by your business email platform or are overwhelmed with protecting business email accounts from phishing attacks, BitLyft can help. Contact our professional team to learn more about how to keep your organization safe from phishing emails.

