Cybersecurity 101: How Software Updates Can Keep Your Data Safe

 By
Emily Miller
·
5 minute read
By
Emily Miller
·
5 minute read
When you think of the victims that hackers target, what's the first thing that comes to mind? Probably data centers, personal computers, or mobile devices. But you'd also be correct to say hospitals, ATMs, and airports.
Hackers aren't always looking to take forbidden fruits hidden behind layers of state-of-the-art security. Often, they're looking for low-hanging fruit. And the best low-hanging fruit is a system that's behind on software updates.
Hospitals, ATMs, and airports, in this instance, often use old, unsupported software. Add in the fact that they store sensitive records for thousands of customers, and they're the ideal target for bad actors. All it would take to keep them out is a simple solution: to update devices.
In honor of National Cybersecurity Month, we're going back to the basics. Join us in this episode of cybersecurity 101 as we discuss software updates.
The Cyber Threat Landscape: How Do Hackers Select Their Targets?
As the old saying goes, you need to know your enemy. Understanding what a hacker wants and what they're willing to do to get it teaches us some important lessons.
Like anyone, hackers are often looking for the path of least resistance. While some are out there in search of a challenge, most want easy successes with minimal risk.
Contrary to what Hollywood might depict, your average hacker isn't looking for a grand finale. They want data that they can sell off easily on the dark web.

Google's server farms, for example, are a big nut to crack. It would take a sophisticated attack on multiple fronts to compromise their systems. Hackers would be at constant risk of betraying identifying characteristics that authorities could use to track them down later.
Or they could go for something they know: old, unsupported operating systems.
Crawling the Web for Exploits
Your operating system is the bread and butter for everything you do. From the bus interface to the kernels, it determines how you interact with other devices on a network--or the internet. The way it is structured and the manner in which it handles user permissions dictates the attack vectors it presents.
Hackers invest countless hours probing an operating system for exploits. All it takes is something small: swiping low-level credentials and then bumping them up to admin privileges. A few megabytes of code is sufficient to achieve this, such as with the Stuxnet worm.
Finding old, unsupported operating systems is easy. Hackers make use of crawlers, programs that "crawl" the internet in search of specific devices.
They release these crawlers across the internet. The crawlers go from device to device, knocking on ports.
Every device has unique identifiers. One of these identifiers concerns which operating system it's running and which version of that operating system it is. An operating system that's behind on updates thus becomes a juicy, red target to any crawler.
It's foolish to assume that as long as you behave on the internet, you'll never get hacked. But hackers are on the lookout for exploits. If you have one, they're going to rush to utilize it before you patch your device.
Some might make the mistake of assuming that because their devices work on a subnet, they're safe as well. But details about operating systems have a way of leaking out. And word travels fast when a company is using old operating systems.
How OS Developers Handle Software Updates
The only effective way to subvert this is through software updates. OS developers tire day and night doing the reverse of hackers: finding what holes they've discovered and patching them. They identify zero-day exploits as they appear--both on the darknet and when put to use.
This is a neverending game. When you patch one exploit, you invariably create another. As long as there are doors to open, hackers will find ways to bypass the proper channels to open them.
Patching an OS takes hundreds of skilled coders and software engineers. But as time goes by, their mother corporation will release new operating systems. Naturally, these operating systems take precedence.
That's why OS developers like Microsoft put an expiration date on their operating systems. This expiration date is telling users one thing in no uncertain terms: you need a newer operating system.
Unfortunately, our lax cyber security policies lead companies to ignore this advice. A shocking 15% of endpoint devices use Windows 7. This despite the operating system going the way of the dodo nearly 3 years ago.
If you think the situation with Windows 7 is bad, just take a look at Windows XP. Microsoft released it in 2001 and ended support in 2014. And yet, over half a percent of endpoint devices continue to use Windows XP.
We've only discussed operating systems here, but the same extends to user applications. Everything from an enterprise-level hypervisor to a humble calculator app needs updates. It's a common tactic for hackers to start small and work their way up.
Best Practice for Software Updates
A security breach is a big deal, and all it takes are malware attacks that target outdated software. A security breach could leave your company reeling from the remediation costs.
Fortunately, there is hope. Solid cyber security policies can make all the difference. Let's discuss a few simple solutions and types of cyber security to avoid said malware attacks.
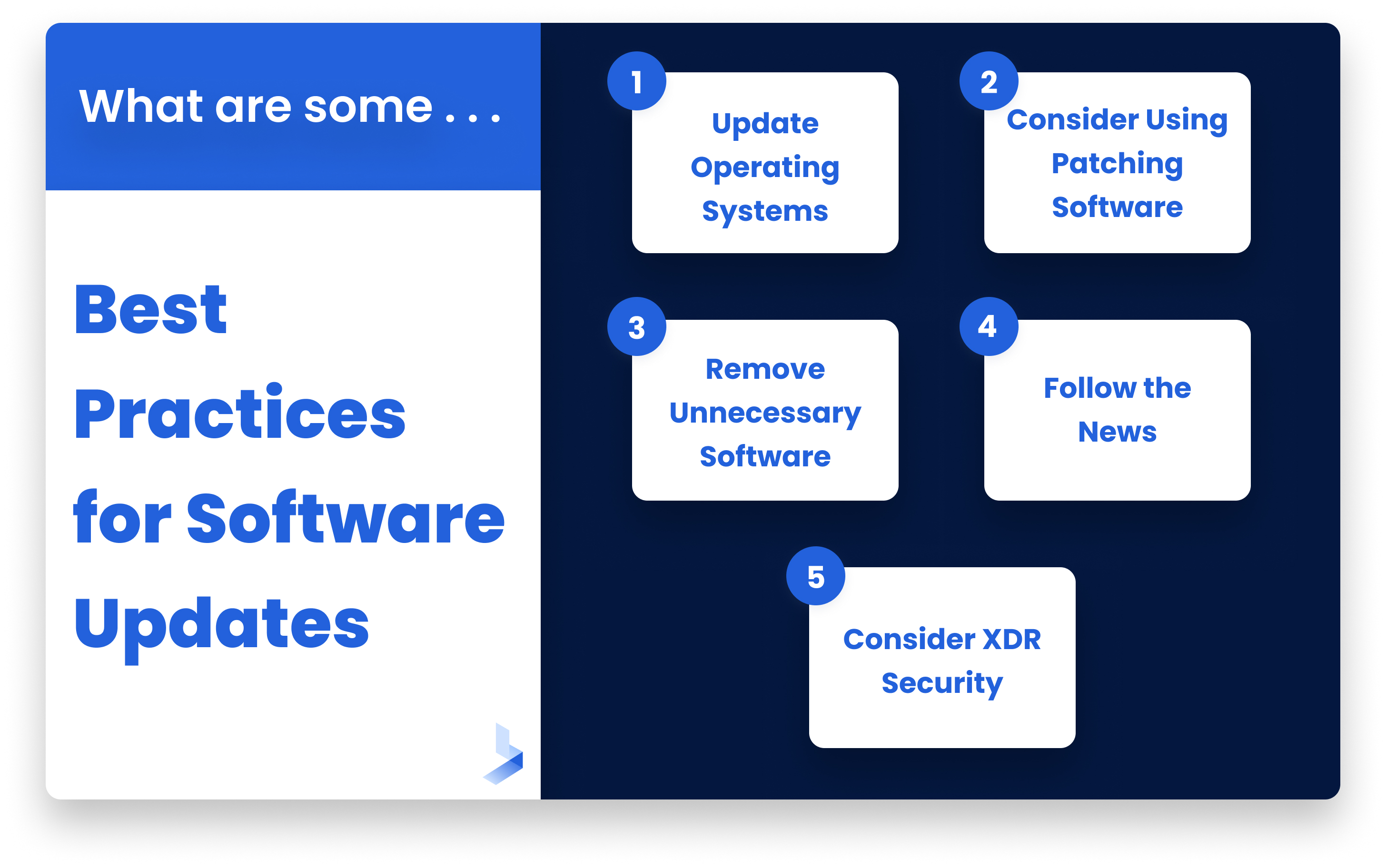
1. Update Operating Systems and Software Without Delay
This may seem obvious, given everything we've discussed. But even veteran security experts feel the urge to delay updates. It's no wonder that many people force their computers to delay updates by a week or longer.
Treat every update with the utmost severity. There's no telling if the patches included could be for critical system bugs. Do everything in your power to update devices the moment updates are available.
As mentioned earlier, this includes everything. Any piece of software presents a vulnerability, even if that software doesn't have admin permissions.
2. Consider Using Patching Software
A network is a complicated thing. There are so many devices running so many disparate operating systems. The update process for a server rack BIOS will be entirely different from the update process for a bog-standard Windows machine.
Patching software is a tool many security experts turn to. It may not update all your software, but it updates the majority. Schedule this software to run on a daily basis to update things as updates appear.
This may require occasional service interruptions. It's best for your IT team to schedule regular downtime when they can update everything at once. Having rolling updates without service disruptions is also a solid strategy to keep your system patched.
3. Remove Unnecessary Software
Evaluate every piece of software that your company makes use of. Ask the hard questions: do we really need this? Can we make do without it?
Even enterprise-grade computers arrive loaded with bloatware. This might be as simple as Microsoft Teams, despite the fact that your organization uses Slack exclusively. It's best to delete Teams if your organization has no use for it.
Think of software as additional attack vectors in addition to regular system processes. Every piece of software you install gives a hacker a brand new list of exploits.
Further, you're relying on the company that produces said software to provide prompt updates. There's a good chance that that company may delay updates or hardly release them at all.
This might be the time to evaluate your company's chosen software. Infrequent updates are a clear sign it's time for a transition. Trust companies that treat their software with care.
4. Follow the News
When updates arrive on your devices, they usually don't include a changelog. A changelog is a list that shows what the update addresses and the serious vulnerabilities it intends to patch. To most users, one update is no different than the last.
Every company concerned about the cyber threat landscape needs to stay on top of developing stories. Just recently, Apple pushed a rapid update to address a serious security vulnerability. Anyone who didn't follow the news probably ignored or delayed the update.
5. Consider XDR Security
As we've discussed, software updates are reactive. Developers build them in response to diagnostic logs and user reports. Without malware attacks to reproduce, the best they can do is scan the code for potential vulnerabilities.
The solution is Next-Gen XDR. XDR (extended detection and response) beats hackers to the punch. It's an active, automated, comprehensive solution that substitutes many types of cyber security.
When you can't update your software, XDR identifies potential security flaws. It helps your organization to build a holistic security plan unique to your network. It makes up for software weaknesses between updates.
| Related Reading: XDR Security 101: Understand Its Power, Unleash Its Potential |
Get XDR Security for Your Organization
Software updates are not optional; they're necessary. They provide patches that address known vulnerabilities. Failure to update your system in a timely manner gives a hacker a big window of opportunity.
Updating devices is just one step in a successful cybersecurity plan. The next is finding an affordable, bespoke security option for your organization.
XDR provides the last solution you'll ever need. Check out BitLyft today and strengthen your company's security posture.
