Cybersecurity Compliance by Industry: Choosing a Framework that Fits

 By
Mike Skeith
·
11 minute read
By
Mike Skeith
·
11 minute read
A Comprehensive Guide to HIPAA, FERPA, PCI DSS, GDPR, NERC CIP, and More
Companies across all industries store, share, and use valuable information to complete essential business tasks. However, the information that keeps your business running also serves as a powerful attractant for cybercrime. To maintain the responsibility of protecting organizational and customer information, most companies are obligated to follow specific government regulations. For many businesses, this means following the complex requirements of multiple frameworks and regulations.
Regulatory non-compliance leads to steep fines and penalties. Perhaps more importantly, it can lead to expensive breaches and attacks that cost businesses thousands of dollars in damages and reputational deterioration. This whitepaper outlines the various regulations across different industries and offers best practices for maintaining compliance.
Healthcare: HIPAA and HITECH
Professionals in the healthcare industry are tasked with protecting the privacy of sensitive medical and personal information. Most businesses in the industry are required to maintain compliance with HIPAA and HITECH regulations.
HIPAA
The Healthcare Insurance Portability and Accountability Act of 1996 (HIPAA) (also called the privacy rule) outlines the use and disclosure of individuals' health information to maintain patient privacy. The privacy rule is designed to assure individuals' health information is protected while allowing the flow of information needed to promote high-quality healthcare. It applies to health plan providers, health care providers, healthcare clearinghouses, and business associates. HIPAA protects individually identifiable health information.
To comply with HIPAA, all covered entities must:
- Ensure the confidentiality, integrity, and availability of electronic protected health information (e-PHI)
- Detect and safeguard against anticipated threats to the security of the information
- Protect against anticipated impermissible uses or disclosures that are not allowed by the rule
- Certify compliance by their workforce
Best Practices for Maintaining Compliance
- Understand key definitions and disclosure permissions in the security rule
- Identify information systems that house e-PHI
- Conduct a risk assessment to identify e-PHI and potential vulnerabilities
- Create and deploy organizational policies and procedures that assign responsibility for each control to specific individuals or teams
- Limit employee access to sensitive information to the minimum amount of information needed to complete tasks or goals
- Backup all patient records in a different location
- Utilize modern security measures to protect against attacks
- Regularly review compliance to recognize changes in HIPAA regulations and ensure policies are effective and regulations are being followed
HITECH
The Health Information Technology for Economic and Clinical Health (HITECH) Act of 2009 was enacted to promote the adoption and meaningful use of health information and technology. It addresses the privacy and security concerns associated with the electronic transmission of health information. The HITECH Act applies to healthcare organizations and medical practices that benefit from Medicare and Medicaid programs. It also applies to covered entities and business associates as well as software developers and vendors of personal health devices.
To comply with HITECH, organizations must:
- Undergo HIPAA certification
- Protect e-PHI
- Generate prescriptions electronically
- Implement clinical decision support
- Use computerized provider order entry (CPOE) for medication, laboratory, and diagnostic imaging orders
- Provide timely patient access to electronic files
- Ensure care is coordinated
- Participate in the health information exchange
- Participate in public health reporting
- Issue notifications to affected individuals within 60 days of the discovery of a breach of unsecured protected health information and breaches of 500 or more records
Best Practices for Maintaining Compliance
- Train employees and business partners on HITECH requirements
- Develop and implement policies and procedures to ensure the privacy, safety, and integrity of PHI
- Limit employees and business partners to sensitive information to the minimum amount of information needed to complete tasks or goals
- Review all internal practices and policies to be sure they are compliant
Higher Education: FERPA
Higher education institutions house sensitive student and employee information, research data, and information from government agencies. To protect this information, organizations are required to maintain FERPA compliance.
FERPA
The Family Educational Rights and Privacy Act (FERPA) is a federal law that protects the privacy of student education records. It gives parents and eligible students more control over their education records and prohibits educational institutions from disclosing personally identifiable information in education records without written consent. The law applies to all schools that receive funds under an applicable program of the U.S. Department of Education.
To comply with FERPA, educational institutions must:
- Undergo mandated FERPA training for teachers, administrators, or other school officials
- Advise students of their rights annually
- Consent to allow parents or eligible students to view records at any time with signed consent
- Protect personally identifiable student data
Best Practices for Maintaining Compliance
- Establish a clear understanding of protected student records
- Implement clear role-based access controls to establish who can access student records
- Utilize modern security tools to prevent unauthorized access to data
- Encrypt data at rest and in transit
- Test and remediate vulnerabilities
- Monitor systems for suspicious activity
- Maintain updates as regulations change
Finance, Fintech, and Software: PCI DSS, GDPR, and CCPA
As a highly targeted industry, financial regulatory compliance typically includes stricter restrictions than those imposed on other industries. Regulations for finance, fintech, and software typically fall under PCI DSS, GDPR, and CCPA regulations.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. It applies to any entity that stores, processes, and/or transmits cardholder data. If your business accepts or processes payment cards, it must comply with the PCI DSS.
PCI DSS requirements include:
- Install and maintain a firewall configuration to protect cardholder data
- Do not use vendor-supplied defaults for system passwords and other security parameters
- Protect stored data
- Encrypt transmission of cardholder data across open public networks
- Use and routinely update anti-virus software
- Develop and maintain secure systems and applications
- Restrict access to cardholder data by business need-to-know
- Track and monitor all access to network resources and cardholder data
- Regularly test security systems and processes
- Maintain a policy that addresses information security
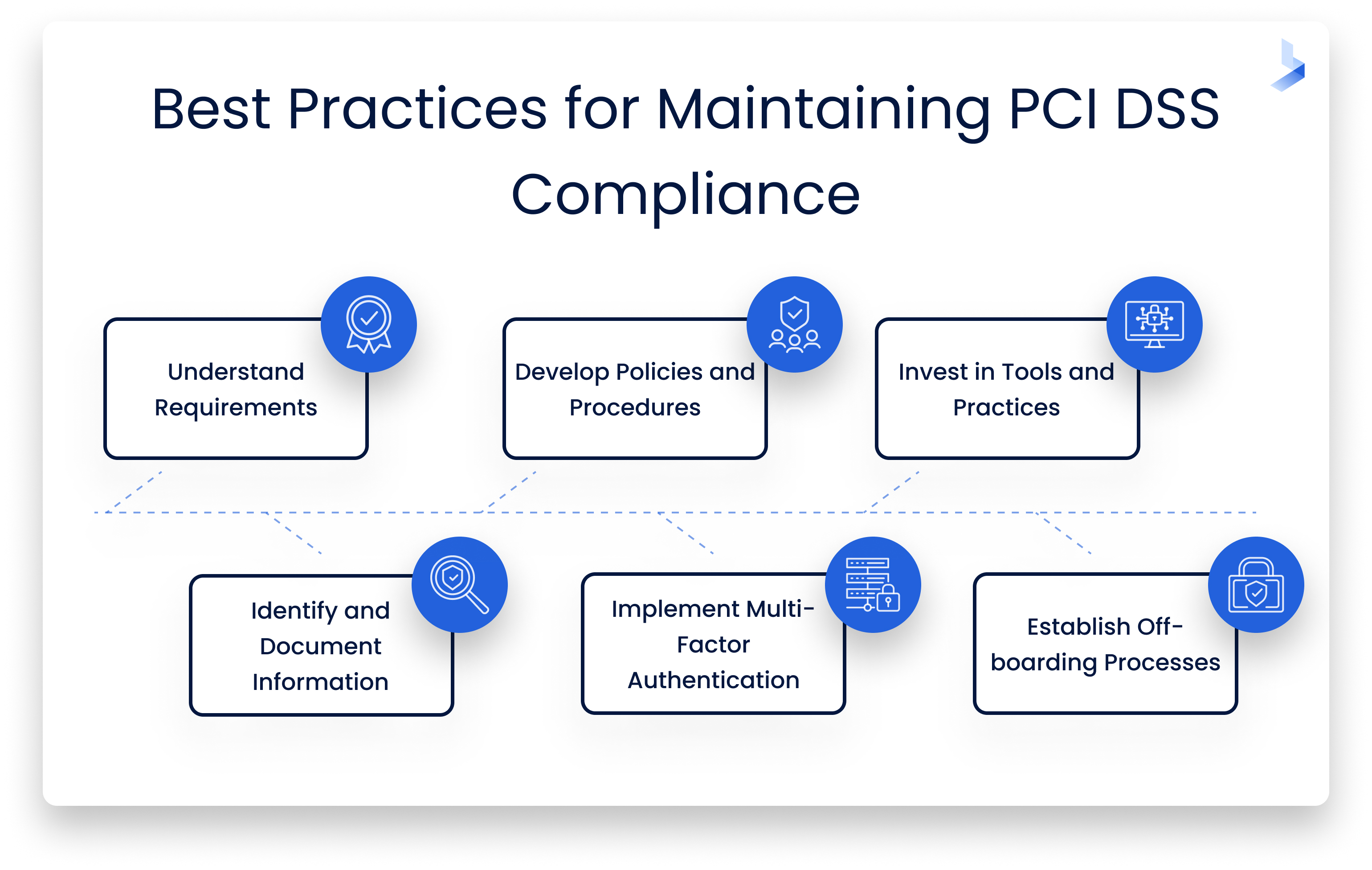
Best Practices for Maintaining Compliance
- Understand the levels and requirements of PCI DSS
- Develop policies and procedures to prepare for and conduct required annual self-assessments and compliance reporting
- Invest in modern security tools and practices for effective data protection
- Identify and document all information subject to PCI DSS compliance
- Implement multi-factor authentication for all accounts
- Establish strict offboarding processes for when employees leave your organization
GDPR
The General Data Protection Regulation (GDPR) is the toughest privacy and security law in the world. The regulation was put into effect in 2018 to protect the privacy and security of citizens in the EU. GDPR applies to any organization that processes the personal data of or supplies goods and services to EU citizens or residents.
GDPR compliance requirements for U.S. companies include:
- Conduct an information audit for EU personal data
- Inform your customers why you're processing their data
- Assess your data processing activities and improve protection with practices like end-to-end encryption and organizational safeguards
- Develop a data processing agreement with your vendors
- Appoint a data protection officer (if necessary)
- Designate a representative in the EU
- Know what to do if there is a data breach
- Comply with applicable cross-border transfer laws
Best Practices for Maintaining Compliance
- Get a firm understanding of how GDPR law applies to your business
- Classify all data
- Document data collection and processing activities
- Appoint a data protection officer to oversee data protection and strategy
- Create a written document of how your company practices GDPR compliance
- Implement modern cybersecurity tools to eliminate vulnerabilities
- Instantly report and respond to data breaches
CCPA
The California Consumer Privacy Act of 2018 (CCPA) gives California consumers more control over the personal information that businesses collect about them. The CCPA applies to for-profit businesses that do business in California and do any of the following:
- Have a gross annual revenue of over $25 million
- Buy, sell, or share the personal information of 100,000 or more California residents, households, or devices
- Derive 50% or more of their annual revenue from selling California residents' personal information
It's important to note that CCPA applies to businesses outside of California if they collect or sell PII of CA residents, conduct business in the state and meet any of the applicable standards above.
To comply with CCPA, organizations must:
- Inform protected consumers of your intention to collect personal data
- Provide consumers with clear and easy access to your privacy policy
- Supply protected consumers with their personal information within 45 days of their request
- Delete the personal data and information of protected consumers upon their request
- Allow consumers to opt out of data sales and marketing campaigns that collect personal information
- Update your privacy policy each year
Best Practices for Maintaining Compliance
- Update privacy policies and notices to reflect CCPA requirements
- Develop a data inventory strategy to track all information processing activities
- Train your employees on CCPA requirements
- Perform a risk assessment
- Implement effective security tools to ensure sound data protection
- Conduct ongoing internal data privacy training
- Review your policy annually
Manufacturing and Utilities: NERC CIP, ITAR, and EAR
Manufacturing companies are tasked with protecting government data, organizational data, employee data, and customer information. Regulations to protect this information typically fall under NERC CIP, ITAR, and EAR regulations.
NERC CIP
The North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) Reliability Standards are designed to safeguard the integrity of the utility infrastructure across North America. All bulk power system owners, operators, and users must comply with NERC-approved Reliability Standards. These entities are required to register with NERC through the appropriate regional facility.
To comply with NERC CIP, organizations must:
- Identify and classify assets
- Designate an official to be responsible for security
- Create and maintain policies for asset protection
- Provide security awareness training for employees
- Conduct employee background checks
- Develop access management controls on an as-needed basis
- Create electronic security perimeters or virtual equivalents
- Manage secure remote access points
- Create and enforce physical security plans and physical security perimeters
- Maintain system security controls with patch management, management of ports and services, malware prevention, security event logging, management of shared accounts, and password and credential management
- Develop a cyber security incident response plan that includes recovery plans, continuity of operations, and backup and restoration
- Maintain change and vulnerability management including management of transient cyber assets
- Protection of BES cyber system information through classification and protection of information and disposal of media
- Develop secure control center communications
- Create supply chain security policies
- Physical security of key substations
Best Practices for Maintaining Compliance
- Create backups for network device configuration files
- Monitor activity across all devices
- Create and enforce access policies based on task and role requirements
- Partner with a cybersecurity team with experience in utility infrastructure
- Check NERC Standards, Compliance, and Enforcement Bulletin monthly to keep up with regulatory changes and updates
ITAR
The International Traffic in Arms Regulations (ITAR) governs the manufacture, export, and temporary import of defense articles, the furnishing of defense services, and brokering of a defense article or service. Its purpose is to prevent military and defense-related items and information from falling into the wrong hands. ITAR applies to all manufacturers, exporters, temporary importers, brokers, or providers of defense articles, services, or technical data.
To comply with ITAR, organizations must:
- Register with the State Department
- Implement a documented ITAR compliance program that includes tracking, monitoring, and auditing of technical data
- Take necessary steps to protect data related to items that are on the U.S. Munitions List
Best Practices for Maintaining Compliance
- Determine whether you handle items on the USML
- Register with the Directorate of Defense Trade Controls (DDTC)
- Maintain an information security policy
- Build and maintain a secure network by installing and maintaining advanced security tools
- Regularly test security systems and processes
- Protect sensitive data with encryption
- Track and monitor all access to network resources and sensitive data
- Maintain a vulnerability management program
EAR
Export Administration Regulations (EAR) regulate the export, reexport, and transfer of some less sensitive military items, commercial items that also have military application, and purely commercial items without an obvious military use. License requirements are dependent on the technical characteristics of an item, the destination, the end user, and the end use.
To comply with EAR, organizations must:
- Classify your item using the Commerce Control List
- Establish written export compliance standards
- Develop a continuous risk assessment of the export program
- Create a manual of policies and procedures
- Provide ongoing compliance training and awareness
- Conduct continuous screening of contractors, customers, products, and transactions
- Adhere to recordkeeping regulatory requirements
- Compliance monitoring and audits
- Create an internal program for handling compliance issues
- Complete appropriate corrective actions in response to export violations
Best Practices for Maintaining Compliance
- Identify applicable items
- Conduct a risk assessment
- Assign roles and responsibilities
- Build a compliance culture
Cross-Industry Frameworks: NIST, ISO/IEC 27001, and CIS Controls
Certain frameworks exist to help organizations across all organizations achieve improved cybersecurity posture. These frameworks are not industry-specific, but they support the regulations of most industry-specific regulations.
NIST
The National Institute of Standards and Technology (NIST) cybersecurity framework helps businesses of all sizes better understand, manage, and reduce cybersecurity risks. The framework is voluntary. However, it gives businesses an outline of best practices for effective cybersecurity.
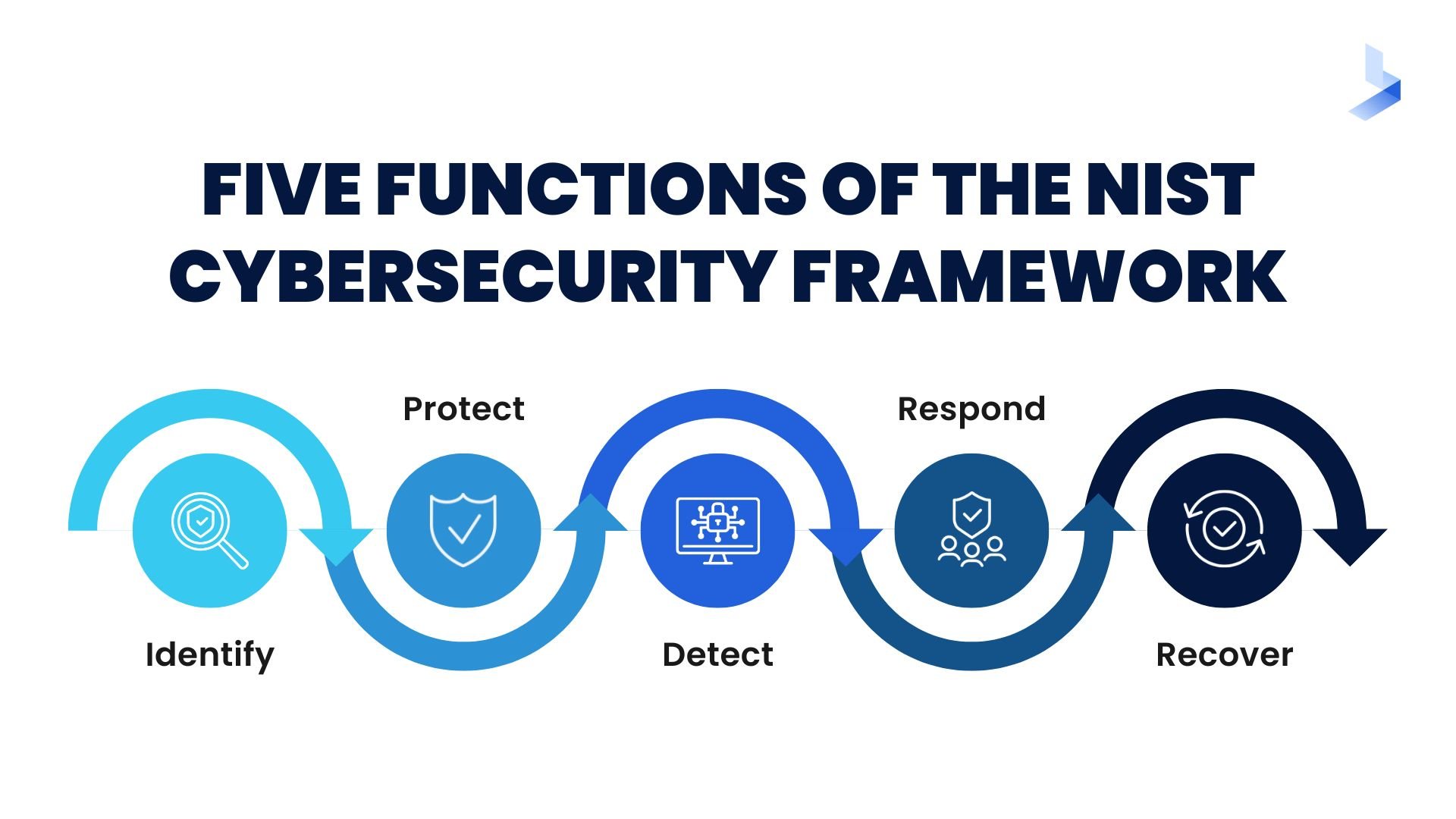
Requirements for NIST compliance include:
- Identify and categorize data that needs to be protected
- Conduct routine risk assessments to establish baseline controls
- Set up a baseline for minimum controls to protect all information
- Record your baseline controls in a written plan
- Create security controls for all your IT and online systems
- Continually monitor performance to measure effectiveness
- Find an authorized information system for all your processing needs
- Continually monitor security controls
ISO/IEC 27001
The ISO/IEC 27001 standard provides companies of any size and from all sectors of activity with guidance for establishing, implementing, maintaining, and continually improving an information security management system. It helps organizations become risk aware and proactively identify and address weaknesses. ISO/IEC 27001 certification is one way to demonstrate that you are committed and able to manage information securely and safely.
Requirements for certification include:
- Define what information assets need to be protected
- Conduct a risk assessment
- Define a plan to eliminate risks
- Keep records of training, skills, experience, and qualifications
- Monitor and measure results
- Develop an internal audit program
- Complete document review and audit for certification
CIS Controls
The Center for Internet Security (CIS) critical security controls are a prescriptive, prioritized, and simplified set of best practices that you can use to strengthen your cybersecurity posture. They can help you simplify your approach to threat protection, comply with industry regulations, and achieve essential cyber hygiene.
The CIS critical security controls include 18 controls:
- Inventory and control of assets
- Inventory and control of software assets
- Data protection
- Secure configuration of enterprise assets and software
- Account management
- Access control management
- Continuous vulnerability management
- Audit log management
- Email and web browser protections
- Malware defenses
- Data recovery
- Network infrastructure management
- Network monitoring and defense
- Security awareness and skills training
- Service provider management
- Application software security
- Incident response management
- Penetration testing
How These Frameworks Supplement industry-Specific Regulations
Voluntary frameworks are developed by government agencies and cybersecurity professionals to establish best practices to protect all businesses. Since these frameworks establish a set of controls that all companies can share, they're often used as a guide for industry regulations. When companies begin their cybersecurity journey by establishing effective cybersecurity hygiene outlined in accepted frameworks, they're more likely to meet industry requirements.
Building a Compliance Strategy
An effective compliance strategy will help you maintain industry regulations and protect your business network against expensive and damaging cyberattacks. With a firm understanding of the different regulatory compliance requirements, you can take steps to build a comprehensive compliance strategy that meets your industry requirements and cybersecurity goals. Take these steps to get started.
Assess Your Organization's Compliance Needs
Your compliance needs will be defined by the sensitive data your organization stores and shares and by industry requirements. Begin by identifying sensitive data and the systems on which they're stored. After listing this information, determine whether you're required to follow specific industry regulations or other security frameworks.
Develop a Comprehensive Compliance Program
A comprehensive compliance program identifies what data you'll protect, the steps you'll take to protect sensitive data, and who is responsible for establishing and maintaining compliance. Identify all data that must be protected and the employees who need access to sensitive data. Use the information to develop written policies and procedures that define organizational cybersecurity practices. Assign responsible individuals or teams to carry out specific tasks and center data accessibility around role-based permissions.
Leverage Technology and Tools for Effective Compliance Management
While people are a crucial part of cybersecurity, the massive amount of data created by modern enterprises demands automated systems to keep up with the flow of information. Tools that leverage artificial intelligence and machine learning can collect, parse, and analyze data in real-time. Modern tools can even detect suspicious behavior and alert security professionals to relevant threats. Your organization's cybersecurity stack should provide a layered security system that monitors external and internal threats.
The Role of Managed Security Service Providers (MSSPs) and Managed Detection and Response (MDR)
Most businesses can't afford the cost of maintaining an in-house SOC that includes company-owned infrastructure and 24/7 oversight by cybersecurity professionals. Managed security service providers (MSSPs) and managed detection and response (MDR) are options that supply businesses with remote cybersecurity programs that can help improve regulatory compliance. Managed cybersecurity services offer companies across all industries the best of both worlds by providing highly effective cybersecurity tools along with assistance from experienced cybersecurity professionals.
By investing in managed cybersecurity services, businesses can develop an effective cybersecurity program that automatically includes compliance management. Good cybersecurity and compliance go hand in hand. Managed security and MDR providers have the tools and knowledge to incorporate your compliance requirements into your cybersecurity plan. As a result, you can eliminate many of the manual tasks associated with compliance maintenance and reporting and avoid non-compliance fines and penalties.
It's important to note that MSSPs and MDR services can vary significantly by provider. To choose the right partner for your organization, it's essential to have a firm understanding of what you expect to achieve and which services will work best for your organization. Before vetting providers, learn the difference between MDR and MSSP. Seek a provider with services most likely to satisfy all your cybersecurity needs. Consider whether each provider has a successful history and experience in your industry. Most importantly, take the time to get to know your potential cybersecurity partner. Ask questions about every aspect of the services they provide and make sure the company is up to the task of providing you with the security you need to maintain compliance and prevent attacks.
Achieving Comprehensive Cybersecurity Compliance and Protection
Cybersecurity compliance is a vital requirement for your business. Failure to follow industry regulations can lead to fines and penalties that can significantly affect your business options. More importantly, maintaining compliance can help you take steps that will naturally improve your cybersecurity posture and help you avoid expensive cyberattacks. Still, navigating complex compliance regulations can be challenging. Using this guide can help you get a better understanding of your compliance requirements and the steps you need to take for effective maintenance.
If you're still unsure about your ability to maintain compliance, we can help. Strengthen your organization's cybersecurity compliance with the help of our expert services. Contact us today to learn more about our tailored compliance solutions for your industry.
