MDR vs MSSP: Which Should You Choose?

 By
Jason Miller
·
10 minute read
By
Jason Miller
·
10 minute read
An in-house Security Operations Center (SOC) equipped with cutting-edge technologies and tools and fully staffed with educated and experienced cybersecurity professionals who work around the clock is the most comprehensive way to protect your organization against modern cybersecurity threats. Unfortunately, most companies can't obtain or afford a full in-house Security Operations Center. As cyber threats surge and the need for cybersecurity continues to increase in every industry, the talent gap grows, making it difficult to source the talent needed to staff an in-house Security Operations Center. Furthermore, the cost of staff at a Security Operations Center 24/7 is out of reach for most businesses. For this reason, more and more businesses are turning to outsourced cybersecurity solutions.
It's never been more obvious that businesses of all types and sizes are at risk for cyberattacks. However, organizations across different industries use and store different types of data, and therefore, need different levels of protection. As a result, it can be difficult to understand what your business needs for effective cybersecurity. As technology evolves, so do cyberattacks and third-party cybersecurity offerings. In a world of confusing anagrams, it can be difficult to understand what you need and what you'll actually receive when you invest in a specific cybersecurity service.
Two of the most commonly advertised cybersecurity offerings are MDR and MSSP. They are frequently confused and sometimes used interchangeably. However, there are significant differences between the two, and choosing the right one could be the difference between preparing for a cyberattack and fighting one. By learning exactly what MSSP and MDR mean, and how they are different, you can better determine which is right for your organization.
What Is MSSP?
A Managed Security Service Provider (MSSP) is a third-party company that provides outsourced monitoring and management of security systems and devices. MSSPs use high-availability security operation centers (SOCs) to provide 24/7 services designed to reduce the number of on-site security personnel needed by an organization. Common services provided by MSSPs include managed firewall, intrusion detection, virtual private network, vulnerability scanning, antiviral services, and SIEM monitoring.
The role of an MSSP can vary depending on the company you choose and your specific needs. Typically, an MSSP is used to supplement the existing cybersecurity efforts of an organization or provide the bulk of cybersecurity initiatives for an organization without a security team. For this reason, services can vary widely. For instance, an MSSP may provide a large corporation with co-managed SIEM to extend the hours of operation and personnel of an on-prem Security Operations Center. MSSPs may even help decision-makers create a full cybersecurity strategy from scratch when working with a company with few cybersecurity resources.
Services provided by an MSSP are often customizable to a company's budget and threat level. It's common for businesses to choose some products and services offered by an MSSP to meet their specific needs. Services provided by an MSSP may include:
- Infrastructure Management
- Risk and Vulnerability Assessments
- Employee Cybersecurity Training
- Antivirus Management
- System Monitoring
- Risk and Vulnerability Assessments
- Compliance Management and Reporting
- Penetration Testing
- Patch Management
- SIEM Management
- Managed Detection and Response
What Is MDR?
Managed Detection and Response (MDR) is a group of services that provides customers with remotely delivered modern Security Operations Center functions. MDR provides a turnkey experience, using a predefined technology stack supplied by the provider to rapidly detect, analyze, investigate, and actively respond through threat mitigation and containment.
It typically offers customers 24/7 continuous real-time threat monitoring of their network (including events/logs, suspicious activity, and alerts) as well as professional incident response.
MDR services can vary widely from one provider to another, and some providers may use the term MDR to provide sub-par services. There are certain features that must be present to classify a service as MDR. These include:
- Being a turnkey, fast to deploy service
- Be fully managed, not a technology, and not fully automated
- Have a wide range of use cases
- Include skilled threat analysis, interpretation, and actionable services
- Have the capability to respond quickly and remotely
To reach these goals, MDR providers utilize a tech stack of privately owned or carefully curated tools to monitor your network, identify threats, and automate responses. Still, not all tools are created equal, and providers offer different levels of services in an MDR solution. To achieve the most effective level of cybersecurity, a capable MDR solution should provide these components:
- Threat Intelligence
- 24/7 Coverage
- Incident Investigation
- Incident Validation
- Threat Containment
- Threat Monitoring
- Remote Response Services
- Advanced Analytics
- Human Expertise
MDR vs MSSP: What's the Difference?
MSSP services and MDR services both offer managed services that depend on tools and technologies supplied by the provider, available for a predictable monthly fee. Both solutions offer significant benefits toward improving security and lowering security costs while addressing the talent shortage in the industry. However, the two solutions offer considerably different services.
When you consider that MSSPs have been around for decades, it's easy to see how their evolution might be disjointed in comparison to the modern solution of MDR. Traditionally based on supplying technology services for cybersecurity as technology advanced and network threat sources grew, MSSP services are usually composed of separate tools that work to address different attack areas and threats. These tools are typically defensive in nature and work solely to avoid network breaches. Incident response from MSSP services is typically restricted to an alert when suspicious behavior is detected.
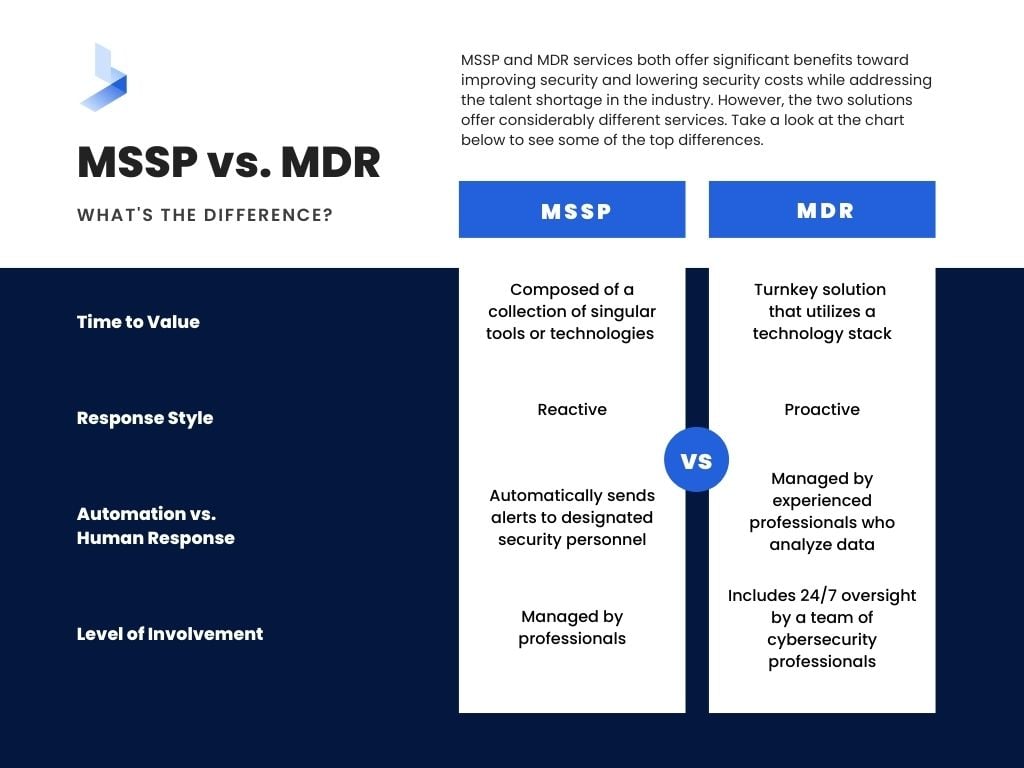
MDR is a relatively new offering that utilizes the most up-to-date technologies to address modern cyberattacks with integrated tools that work together to provide proactive threat hunting, detection, and response. MDR is human-operated, with live threat hunters monitoring customer networks in real-time for both indicators of attack and indicators of compromise. For this reason, MDR is more likely to offer a solution that can completely replace Security Operations Center team operations.
These are some of the main differences between MSSP services and MDR that may affect your organizational security:
- Time to Value
MDR is a turnkey solution that utilizes a technology stack designed to work seamlessly to provide complete visibility into your entire network for threat detection, automated responses that reduce dwell time, and 24/7 oversight and correspondence with a remote Security Operations Center. MSSP services are usually composed of a collection of singular tools or technologies designed to target a specific element of response. These tools often require optimization by your existing security team. - Response Style
MSSP is generally reactive while MDR is proactive. Since MSSP services are largely automated, responses are generally composed of alerts that occur after an action has taken place. MSSP alerts are often limited to the notification that suspicious activity has taken place. MDR is built around response and utilizes automated tools to provide an active response (that ranges from alerts to shutting down a compromised section of the network) in relation to specific threats. This includes incident validation which defines the nature of an attack in the alert sent to your staff. - Automation vs Human Response
Traditional MSSPs are designed to send alerts automatically to designated security personnel. MDR services are managed by experienced professionals who analyze data and provide specific guidance on how to proceed. - Level of Involvement
A quality MDR solution includes 24/7 oversight by a team of cybersecurity professionals who learn about your environment to provide guidance, feedback, and direction for how to better position your organization for cybersecurity success. While MSSP services are managed by professionals, much of the process is automated, which means your security team will be required to be more hands-on throughout the use of cybersecurity tools, and even more so, in incident response.
Choosing Between MSSP and MDR
Cyberattacks in the past few years have made it clear that cybersecurity is a concern for all businesses in every industry. Critical infrastructure breaches and attacks that reveal how one company's cybersecurity can have a domino effect on many others make it clear that cybersecurity is more than a worthy investment. As the threat landscape continues to grow, it will be essential for all organizations to have a reliable level of cybersecurity to protect the consumers and businesses that depend on them.
MSSP and MDR services offer some of the most critical components of managed security sought after by companies hoping to improve their cybersecurity posture. Yet, it can be difficult to understand which services will work best for your organization. MSSP services touch on a wide range of cybersecurity services but stay closer to the surface level. MDR offers advanced monitoring and threat resolution with an in-depth focus on the threats most likely to affect your organization.
Who Needs MDR?
Managed detection and response focuses on detecting cyber threats and responding as quickly as possible. It's not an exaggeration to say that any company or organization where the cost of data loss is greater than the cost of addressing security threats would benefit from MDR. Sometimes referred to as Security Operations Center as a Service or XDR (extended detection and response), MDR is the most proactive approach to cybersecurity today.
MDR can be especially beneficial for companies in these situations:
- Under regulatory requirements to uphold a high level of security
- You lack the resources to include 24/7 monitoring and intelligent response
- You don't have a fully-staffed Security Operations Center
- Your organization lacks the personnel equipped to handle professional cyberattack response
- Your current security efforts are undermined by false alerts
Who Needs MSSP?
MSSPs do not offer as in-depth services as MDR. However, there are reasons you may consider these services. For instance, MSSP services increase cybersecurity hygiene in an organization that doesn't store sensitive data and lacks a cybersecurity monitoring system. On the other hand, a large organization with a fully staffed in-house Security Operations Center might have the skill set within the company to manage modern cybersecurity tools and save money by outsourcing select tasks to an MSSP.
Why Choose MDR Over an MSSP?
It's estimated that by 2025, 50% of businesses will depend on MDR for cybersecurity. As the complexity and effectiveness of cyberattacks grow, businesses are forced to seek preventive measures. Unfortunately, the growing need also contributes to the growing talent shortage in the industry.
Remote work, accelerated cloud migration, and increased dependency on IoT devices mean that organizations are always struggling to cover new assets required to compete in today's business world. Yet, attempting to accomplish this with disjointed MSSP tools requires IT professionals to engage in manual processes to oversee a continually growing web of tools and solutions. MDR uses integration to provide multiple security offerings into one unified solution. Instead of individual tools that work in silos, MDR utilizes tools that work together and share critical information to identify attacks and provide a suitable response before damage occurs.
Effective Incident Response
A survey conducted by the World Economic Forum highlighted, among other things, the effect of the skills shortage on organizations. In a group of more than 120 global cyber leaders, 59% of all respondents stated that they would find it challenging to respond to a cybersecurity incident because of the shortage of skills within their team. This is a problem that is unlikely to change with an investment in MSSP services since they're primarily focused on alerts triggered when suspicious behavior is detected. Most MSSPs require an organization to depend on its internal team for incident response.
MDR places a strong focus on incident response and utilizes the integration of tools for a connected reaction that automates relevant responses based on specific threats. These capabilities can generate a range of responses based on the severity of an attack. For instance, a response can be as simple as the automated removal of known malware or as complex as a chain of events required to isolate a compromised endpoint or shut down a network before additional damage can occur.
In addition to automated responses that launch in seconds, the incident response from your MDR provider's remote Security Operations Center follows as necessary. Human response to suspicious behavior or an attack in progress might include tracking the pattern of the attack to determine if the attacker is still within the system and blocking access to critical data. 24/7 incident response provided by MDR can reduce the dwell time of an attacker from days to mere minutes.
Detection for Discrete Threats
MSSP services are mainly focused on keeping threats out. Yet as attacks grow in sophistication, it's impossible to ensure your network will never be breached. Some of the most effective modern cyberattacks depend on a "low and slow" approach that allows a threat actor to move discreetly through an organizational network, taking as much time as necessary to reach an impactful objective. Phishing attacks, stolen credential attacks, and business email compromises are some of the most common attacks launched by threat actors. These actions are typically only a single part of a larger attack.
MDR builds security layers based on the behaviors associated with modern attacks to recognize suspicious behavior on an otherwise valid account. A combination of human-controlled tools and artificial intelligence (AI) recognizes behaviors that deviate from routine network activities and responds to halt an attack in progress. Instead of responding to an attack when malware locks users out of the system, security professionals are able to address an attack in the early stages when an attacker is seeking information or attempting to gain more powerful credentials.
MSSP services focused on keeping threats out are ineffective in this area because the actions appear to be carried out by an approved user, and therefore, legitimate. Essentially, blocking tools like firewalls are effectively doing their jobs, but attackers are allowed to enter through user behavior like unsuspectingly clicking on a malicious link within a phishing email. This type of back door entry goes unrecognized and traditional tools fail to even generate an alert.
Avoid Alert Fatigue
Any IT team that has faced the process of optimizing security tools understands that not all threats are real. False alerts are a major issue in cybersecurity. Thousands of activities occur on a business network each day. It would be impossible for humans to comb through every single action to determine which behaviors might signal a threat. When a security system alerts your IT team of every potentially suspicious action without context, time is wasted and alert fatigue quickly sets in. Imagine if 100 shadows passed by your window in an hour and none of them were due to an attacker. Within a single day, you would likely assume most shadows were irrelevant. Alert fatigue works the same way, quickly desensitizing team members to information that signals a real threat.
MDR tools and technologies utilize data supplied by humans and machines to add context to alert information. With the added information, alerts are categorized and many false positives are eliminated before they ever reach your team. When alerts do reach your team, they include a high level of detail that determines the threat is likely valid along with concrete steps for remediation.
Human Driven Solutions
Quality MDR solutions include a team of cybersecurity professionals that work as an extension of your team. Instead of depending on completely automated responses, your network is monitored around the clock by a team of humans who have the ability to react to a threat as needed. One of the critical components of MDR requires that the service is neither technology nor fully automated. This requirement means that incident response is never dependent on fully automated solutions.
This critical distinction means professional cybersecurity experts constantly monitor your network to detect threats in real-time and remediate them before harm is done. Instead of receiving a vague notification about a threat, organizations benefit from preventative actions taken by experienced professionals to remediate a threat right away.
Finding an Effective MDR Solution for Complete Protection Against Modern Cyberattacks
While there is a specific definition used to describe MDR, there can be vast differences in the services offered by different providers. Few businesses have the budget and resources to employ a full-scale in-house Security Operations Center that operates 24/7. Hundreds of cybersecurity providers seek ways to fill the void with outsourced services designed to maintain compliance and improve the cybersecurity hygiene of organizations desperate to avoid the effects of a successful cyberattack. Some MSSPs provide MDR services among their offerings. However, it's important to consider that some companies use language suggestive of MDR services without offering all of the critical functions of managed detection and response. For instance, a response can cover a wide range of services, and some companies may only offer an automated alert system as a means of response.
When seeking MDR services for your organization, it's important to consider what you hope to accomplish and your organization's current level of cybersecurity. By learning how the tools and practices supplied by your MDR provider accomplish specific tasks to detect and eliminate threats, you can ensure you'll be getting the level of protection your organization needs. For effective managed detection and response, an MDR solution should contain these components.
- Log management with SIEM
- Endpoint detection and response
- AI for proactive threat protection
- User entity behavior analytics (UEBA)
- SOAR to decrease response time
- Network monitoring for complete visibility
- Expert level analysts that act as an extension of your team
At BitLyft, our cybersecurity experts have always strived to provide solutions that keep up with the speed of today's most advanced modern attackers. MDR with BitLyft AIR goes above traditional MDR services to protect against past, current, and future threats with tools and professionals that detect attacks through the study of threat-based behavior rather than anomalies in your network.
BitLyft combines the power of SIEM for complete visibility, security automation that provides lightning-fast responses tuned to your environment, central threat intelligence (CTI) for proactive protection, and an expert security team that monitors and protects your network 24/7. By combining multiple cybersecurity offerings into one single solution BitLyft AIR® finally provides businesses of all sizes with cybersecurity protection that rivals that of an on-prem Security Operations Center. To receive a demo, and to learn more,schedule some time with our team of security experts to get started today.