The State of Cybersecurity in Manufacturing: Top Insights and Trends

 By
Emily Miller
·
10 minute read
By
Emily Miller
·
10 minute read
Cybercrime is alive and well. In fact, it's consistently growing.
However, financial services are no longer the most attacked industry by cybercriminals. Manufacturing was the top attacked industry in 2021 and was the target of 23% of all ransomware attacks.
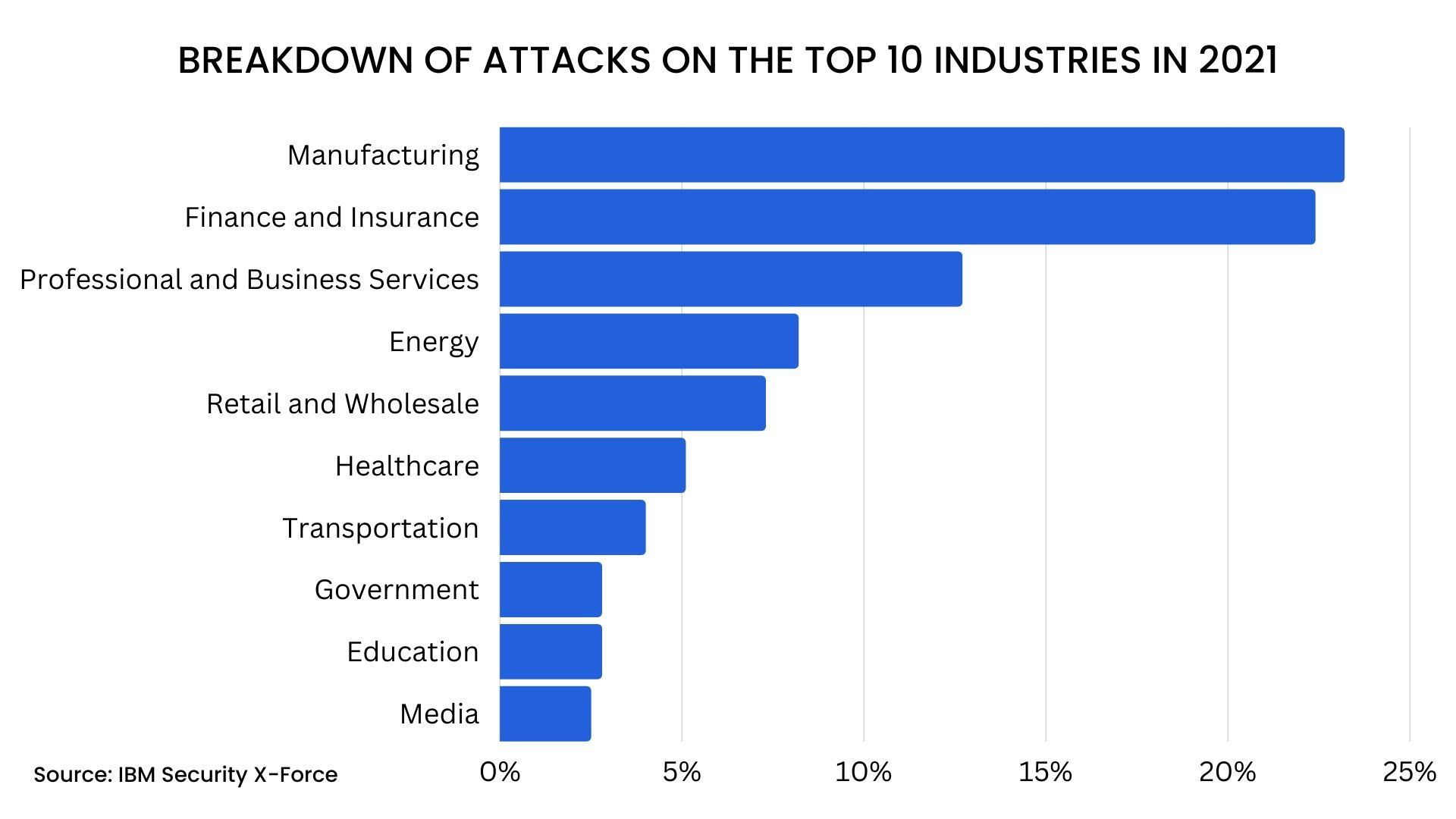
In the past, manufacturing companies were largely overlooked by hackers aiming for high-value targets like financial organizations and healthcare institutions. A variety of factors have caused a drastic shift that makes manufacturing a prime target for attacks. The evolution of technology in the industry has a major impact on the ways hackers can access manufacturing companies and disrupt services for financial gain.
Over the years, financial services, healthcare, and other top targets for hackers have increased cybersecurity efforts, making them less susceptible to a successful attack. As a result, manufacturing companies represent an easier target. Extensive supply chains in manufacturing provide hackers with additional vulnerabilities to exploit as well. In other words, manufacturing companies have presented themselves as highly valuable targets that are easily accessible.
Much of income in the manufacturing industry is project-based, leading organizations to focus on costs that boost operations, production, and performance. As a result, IT staffing, functions, and cybersecurity aren't considered core functions. Yet, the modern threat landscape makes it clear that cybersecurity can no longer be considered a by-product of the IT department.
Effective cybersecurity is an organizational requirement that affects an entire business and all of its operations. Manufacturing companies that fail to recognize the threat will make themselves an easy target for cybercriminals depending on an inadequate cybersecurity posture for easy access.
For manufacturing companies to address this critical issue, key players will have to get a clear picture of the state of cybersecurity in manufacturing, address the top concerns, and use real-time information to implement an effective, affordable solution to modern cybersecurity risks.
The State of Cybersecurity in Manufacturing
Manufacturing was the industry most impacted by cyberattacks in 2021. This trend is unlikely to change in the coming years unless drastic measures are taken to secure the networks of manufacturing companies. In the past, manufacturing networks were largely confined to a single organization. However, industry 4.0 and a deluge of operational technology (OT) advancements have changed this. Such changes aren't new. They've been occurring for over a decade. Manufacturing companies harbor a wealth of information that hackers can use to extort millions. So, why aren't manufacturing companies aware of the risks?
As it turns out, many organizations are all too aware of the effects of cybercrime. The manufacturing industry reached top ten status as the 8th most targeted industry by cyberattackers in 2019 and was launched all the way to #2 in 2020. A Trend Micro study of smart factories in the US, Germany, and Japan revealed that 61% of organizations have experienced cybersecurity incidents, 75% had system outages, and 43% had outages that lasted more than 4 days. Yet, many companies still lack appropriate measures to protect against modern attacks.
Manufacturing companies and the networks that support them are growing at the rate of technology. At the same time, the labor force in the industry is shrinking, and industry professionals are struggling to keep up with demand and maintain production. Data from the Labor Department's JOLT database shows that there were 860,000 unfilled manufacturing jobs in March 2022.
Understaffed organizations have little time to recognize the threats new technology brings to the table and shrinking budgets are another barrier to effective solutions.
As the potential threats have turned into major attacks that threaten government security and national infrastructure, the government is turning up the heat with new regulations and requirements for companies in manufacturing. Understanding these new requirements and finding the resources to comply with them adds another layer of pressure to already overstressed companies facing a deluge of attacks.
With continually increasing attacks facing the industry and new government regulations on the horizon, manufacturing companies have significant work to do to shore up their cybersecurity defenses. Yet, without such protection, manufacturing companies, the organizations that do business with them, and consumers who depend on them will be affected.
Why the Manufacturing Sector is a Target for Cybercrime
In the past, cybercrime largely targeted organizations that were responsible for storing, handling, and transporting large sums of money. The idea of attacking financial organizations for a big payoff is similar to the concept of robbing a physical bank instead of a local convenience store. Yet a recognizable shift came into play when hackers recognized the value of attacks that yield value in other ways. For instance, healthcare breaches typically offer more sensitive data than breaches in other organizations.
When the attack is easier to carry out and offers a significant financial payoff upon selling data, successful attacks are more likely. As organizations across a variety of industries implemented operational technology, attacks that could be leveraged for power became more popular. Unfortunately, the manufacturing sector has a lot to offer cybercriminals, and the industry currently provides a better likelihood of success than many high-level targets across other industries. These are the top reasons the manufacturing sector is a target for cybercrime.
- Downtime is critical in the industry. Time is money, and there is no better representation of this than a busy manufacturing company. The average downtime a company experiences after a ransomware attack is 21 days.
- Unplanned downtime can cost businesses between $926/minute to $17,244/minute, which means paying a ransom could be cheaper than excessive downtime.
- Attacks can represent critical danger. Attacks that target government agencies and critical resources can start in the manufacturing industry. For example, over 300,000 organizations are listed in the Defense Industrial Base, each of which has access to sensitive government data. While the attack on JBS Foods highlighted the dangers of an attack that interrupts the food supply, it was one of at least 40 food manufacturing companies targeted by cybercriminals in 2021.
- OT devices create opportunities. 61% of incidents at OT-connected organizations last year were in the manufacturing industry. Unprotected IoT devices create vulnerabilities that can easily be exploited to access the network. They also present opportunities for equipment sabotage.
- Manufacturing companies are often an easy target. Since they haven't been a target for as long as companies in the financial or healthcare sectors, manufacturing companies often don't have the same levels of protection in place. As a result, they represent an easy target for hackers.
- Long supply chains can apply extra pressure. Long supply chains can affect manufacturing companies in two ways. An attack on a supply company that provides software or services to manufacturing organizations can present vulnerabilities for multiple companies at once. An attack on a manufacturing company can also use the critical role of manufacturing companies in the supply chain to pressure victims to pay a ransom.
| Related Reading: Manufacturing Companies are Learning Cybersecurity the Hard Way |
Top Cybersecurity Concerns in Manufacturing
Evolving technology allows manufacturing companies to utilize cloud computing, artificial intelligence, and robotics in factories. While these tools increase efficiency and productivity, they also create a plethora of vulnerabilities that put companies at greater risk of cyberattacks. New legislature makes it clear that a drastic change is needed to improve cybersecurity in manufacturing. Yet, organizations are likely to face many issues along the way. These are the top cybersecurity concerns currently facing manufacturing companies.
Industry 4.0
The evolution of technology to connect operational devices to informational systems provides a more interconnected network. Such networks greatly improve performance and production. In manufacturing, this technological transformation (known as Industry 4.0) creates hundreds, or even thousands, of endpoints that don't always have the protection they need. Connected devices send and receive messages to a company's central network. When these devices are intercepted, they can be used to breach the network. Even worse, they could be used to allow attackers to remotely launch a harmful attack known as equipment sabotage.
Compliance
Industry compliance in manufacturing has never been simple. Manufacturers provide products for companies in a variety of industries. As a result, regulatory compliance can vary from one organization to the next, requiring some companies to follow regulations under several frameworks. These are the requirement most relevant to manufacturing companies.
- NIST: A set of recommended security requirements for protecting the confidentiality of controlled, unclassified information, NIST is self-regulated and makes up the framework for CMMC.
- CMMC: The CMMC program combines NIST and other frameworks to develop a unified framework of security. Over 300,000 organizations will need to be certified under CMMC by 2025.
- ISO-27001: Though not a federal requirement for manufacturing companies ISO-27001 is often a certification customers seek. Compliance acts as proof that your company takes data security seriously.
Recent attacks that have affected the US fuel and food supplies make it clear that certain manufacturers are an important part of critical infrastructure. The Cyber Incident Reporting for Critical Infrastructure Act of 2022 will require companies considered to be critical infrastructure to notify the Cybersecurity and Critical Infrastructure Agency within 72 hours of a significant cyberattack and within 24 hours of making a ransomware payment.
Some of the sectors that fall under critical infrastructure include communications, critical manufacturing, the defense industrial base, food and agriculture, and information technology. It's likely that many manufacturing companies will be affected by these requirements as they relate to critical infrastructure.
| Related Reading: Cybersecurity Considerations for Industry 4.0 |
Shortcomings of Cyber Insurance
Along with the increase in cybercrime, companies across multiple industries invested in cyber insurance as a way to protect against the costs related to a cyberattack. Unfortunately, this approach offers no protection against the actual effects of an attack. While an insurance policy might cover hard costs related to a ransom and recovery from the attack, insurance is not a form of protection. Besides short-term effects like business interruption and recovery, attacks on manufacturers create a ripple effect because they produce products that are going into equipment months after the attack. As a result, the reputational damage is ongoing and can cause catastrophic losses.
Alongside the lack of risk prevention offered by cyber insurance, companies that depend on such coverage are likely to see soaring costs for cyber coverage. Direct-written premiums collected by the largest U.S. insurance carriers in 2021 swelled by 92% year-over-year, according to information submitted to the National Association of Insurance Commissioners. The price increase fails to correlate with the rising costs of ransomware and other attacks, instead primarily reflecting higher rates in a growing market.
Coverage requirements are changing as well, requiring potential customers to demonstrate they at least practice basic cybersecurity hygiene to qualify for coverage. In the future, cyber insurance won't offer a cushion for companies that fail to put adequate security measures in place. Instead, it will be used to limit costs for companies that were attacked despite cybersecurity efforts.
Ransomware Attacks
Ransomware was the number one attack type in 2021. The lion's share of these attacks targeted manufacturing companies. Unfortunately, there are several reasons why manufacturing makes a perfect target for ransomware attacks. To develop specific products for a variety of companies and organizations, manufacturers depend on the use of sensitive files and other digital data (including government data).
Manufacturers are often a single step in a long supply chain, which gives attackers the advantage of targeting a company that will have the burden of affecting other businesses by refusing to pay a ransom. Downtime is especially costly in the manufacturing sector, adding to the urgency of the attack. Dependence on operational technology (much of which is part of legacy systems) offers attackers additional vulnerabilities to exploit.
Ransomware is a popular cyberattack method because it seeks to extort money from victims by encrypting files and demanding ransom for the safe return of the files. It offers a low entry barrier for criminals and a huge payoff when successful. The introduction of discreet attacks when hackers move laterally through a system and steal data before an attack, has made depending solely on backup for recovery more difficult. Known as double extortion attacks, bad actors threaten to sell stolen data if the ransom isn't paid, making refusal less likely. Ransomware is particularly effective in manufacturing making it a major concern for companies.
Supply Chain Vulnerabilities
Manufacturers are in a position to be affected by an attack that targets their suppliers and as a target within a supply chain. Hackers know that targeting supply chains generates a ripple effect across multiple organizations causing widespread damage. Consider the impacts of recent high-level supply chain attacks.
- Solarwinds: Of approximately 18,000 customers that downloaded the tainted update, around 100 companies were impacted by the attack, including 37 defense industrial base companies. The attack had the potential to do a great deal of harm and isn't the only attack of its kind. The number of incidents caused by vulnerability exploitations increases by 33% from 2020 to 2021.
- Colonial Pipeline: The effect of a single compromised password, the attack shut down operations and limited the supply of fuel for 18 states along the entire East Coast, affecting countless gas stations and hundreds of thousands of motorists.
- JBS Foods: The attack shut down 9 JBS Foods plants and disrupted the operations of all of the company's meatpacking facilities in the US. JBS USA says it has the capacity to process more than 200,000 cattle, 500,000 hogs, 45 million chickens, and 80,000 small stock (lambs, sheep, goats and veal calves) per week. A successful attack on a company of this magnitude can result in problems for the entire supply chain from cattle farmers to grocery stores.
Such attacks clarify the extensive reach of a supply chain attack and the urgency associated with paying a ransom. Effective cybersecurity solutions must provide end-to-end protection for organizational networks in manufacturing as well as seek out supply chain vulnerabilities.
BitLyft's Work in the Manufacturing Industry
BitLyft is a SaaS cybersecurity company based in Michigan and the creators of the BitLyft AIR® platform, which combines managed services with software for automated and proactive security. Our work in the manufacturing industry targets many of the issues that make manufacturers a prime target for modern sophisticated cyberattacks. By taking a proactive approach to researching and understanding federal guidelines and compliance requirements specifically for manufacturing companies that are part of the Nation's critical supply chain, our team can better understand the specific needs and challenges of manufacturing companies.

Modern cyberattacks rely on multiple network vulnerabilities to carry out slow and low attacks with widespread damage and major payoffs. These attacks are particularly effective in the manufacturing industry where multiple OT and IT points converge. To address a plethora of vulnerabilities, the effectiveness of credential theft, and limited visibility into sprawling networks, companies need end-to-end security solutions that harness the power of AI and provide insight into network activity.
Our platform uses SIEM, a remote SOC, SOAR, and CTI to protect higher education institutions from cyberattacks. By taking a proactive approach, we provide visibility into threats outside your environment and provide contextual information to define the nature of threat trends and immunize your network against them.
Case Study: UMBRAGROUP Partners with BitLyft Cybersecurity to Secure its Smart Manufacturing Operations
Headquartered in Italy with facilities worldwide, UMBRAGROUP produces ball screws, electromechanical actuators, and high-precision mechanical and mechatronic components for the aerospace market, which are critical for flight. When the Michigan branch launched operations, they were required to set up an entirely new network. Working with a small staff meant as much technology as possible needed to be automated for maximum efficiency. It also meant that cybersecurity and IT professionals were spread thin.
The company handles controlled, unclassified information, and as a DOD contractor, they were interested in maintaining the security of information. As a provider for the DOD, employees at UMBRAGROUP take pride in the work they do and the way their products serve the US air force. They view cybersecurity as their responsibility and were looking for a complete solution they could depend on to protect critical information and offer complete visibility of potential threats.
Upon connecting with BitLyft, the company's IT director Joe Sheridan was immediately impressed that BitLyft professionals wanted to learn everything about the business and adjusted to their unique needs. The proprietary BitLyft AIR® platform allowed BitLyft to automate many tasks and combine multiple security offerings into a single solution to do more with less time.
As a result, UMBRAGROUP employees can maintain their effectiveness and meet deadline requirements while BitLyft constantly monitors the network for threats in the background. Upon detection of a threat, the company is immediately alerted, so they can take effective measures immediately. UMBRAGROUP professionals want to be at the top of their game and view BitLyft as an important partner in maintaining their position.
The manufacturing sector provides an attractive target for cyberattackers. Manufacturers store and handle sensitive data. They provide parts and equipment for critical infrastructure and the US Department of Defense. As a crucial part of essential supply chains, attacks on manufacturing companies create a sense of urgency that is likely to produce rapid payments. There's no doubt that manufacturing companies will continue to be a prime target for attacks. However, with the right security solutions in place, manufacturing companies can achieve end-to-end protection with complete visibility and automated reporting and response actions.
Identifying gaps, monitoring systems, and having quick responses are the first steps to illuminating and eliminating cyber threats. We equip you with the tools, people, and knowledge to build a strong line of defense so you can focus on producing products, not running a cybersecurity operations center. At BitLyft, we have extensive experience in the manufacturing industry. Contact us to learn more about protecting your entire manufacturing network against the growing number of cyberattacks targeting the industry.
