Is Elastic Stack (ELK) the Best SIEM Tool?

 By
Jason Miller
·
10 minute read
By
Jason Miller
·
10 minute read
Attacks on computer devices and networks are constantly on the rise. No longer are the risks of cyberattacks limited to financial institutions and insurance organizations. Businesses large and small within every industry are a target. As businesses and organizations recognize the potential dangers of these threats, comprehensive security plans are becoming a necessity.
Still, for many organizations, recognizing the requirements of a completely protected network can be difficult. While technology is advancing the way business is done in every industry, certain elements have come together to create a perfect storm that cybercriminals can take advantage of. Restrictions related to the COVID pandemic have escalated remote work on a scale larger than ever before. Meanwhile, the Internet of Things (IoT) is experiencing exponential growth. These elements combined with the rise in malware technology and the increase in sophisticated attacks leave businesses and organizations exposed.
For organizations seeking a complete cybersecurity solution, visibility is key. Within any network, thousands of actions take place every day. These actions are compiled as data entries. Since each entry represents a single action, simply reading through the data to search for suspicious activity is impossible. Your network's data must be categorized and normalized before specialized software is used to automate the search for suspicious entries.
For most organizations, the system used to manage data and monitor logs of data entries is a Security Information and Event Management (SIEM) system. Supplied by different providers, a SIEM system is made up of several elements that take care of log management, security information management, and security event management. Deciding which SIEM solution is the best for a specific organization usually depends on unique factors within the company's existing infrastructure, staff, and resources.
What is the Elastic Stack?
Since SIEM systems are made up of multiple tools used to categorize data and detect potential threats, different options are available. The Elastic (ELK) Stack is one of the most popular open-source tools used within many SIEM systems. The ELK system stacks Elasticsearch, Logstash, and Kibana to create a complete open-source log management system utilized by a variety of businesses. Open-source software is software that is accessible to the public and can be modified and shared to create complete platforms. These capabilities can help eliminate expensive start-up costs and can be easily utilized by highly trained IT and cybersecurity professionals.
ELK is an open-source log analysis and management platform. Described as SIEM for the modern security operations center (SOC), ELK performs a variety of tasks with high levels of success. The ability to scale data across multi-cloud environments and utilize powerful dashboards to analyze all types of data make ELK a winning log management choice for many experienced SOCs. Yet, does this make it the best option for SIEM? Learning about the complete out-of-the-box capabilities of ELK and comparing these capabilities to other SIEM options can help you decide.
ELK SIEM Capabilities
ELK SIEM is a popular tool for a reason. With a variety of log management capabilities and considerable options for scalability, ELK is a good choice for many organizations. Still, to determine the use of ELK as a complete SIEM tool, it's important to consider each of the capabilities and how they're performed.
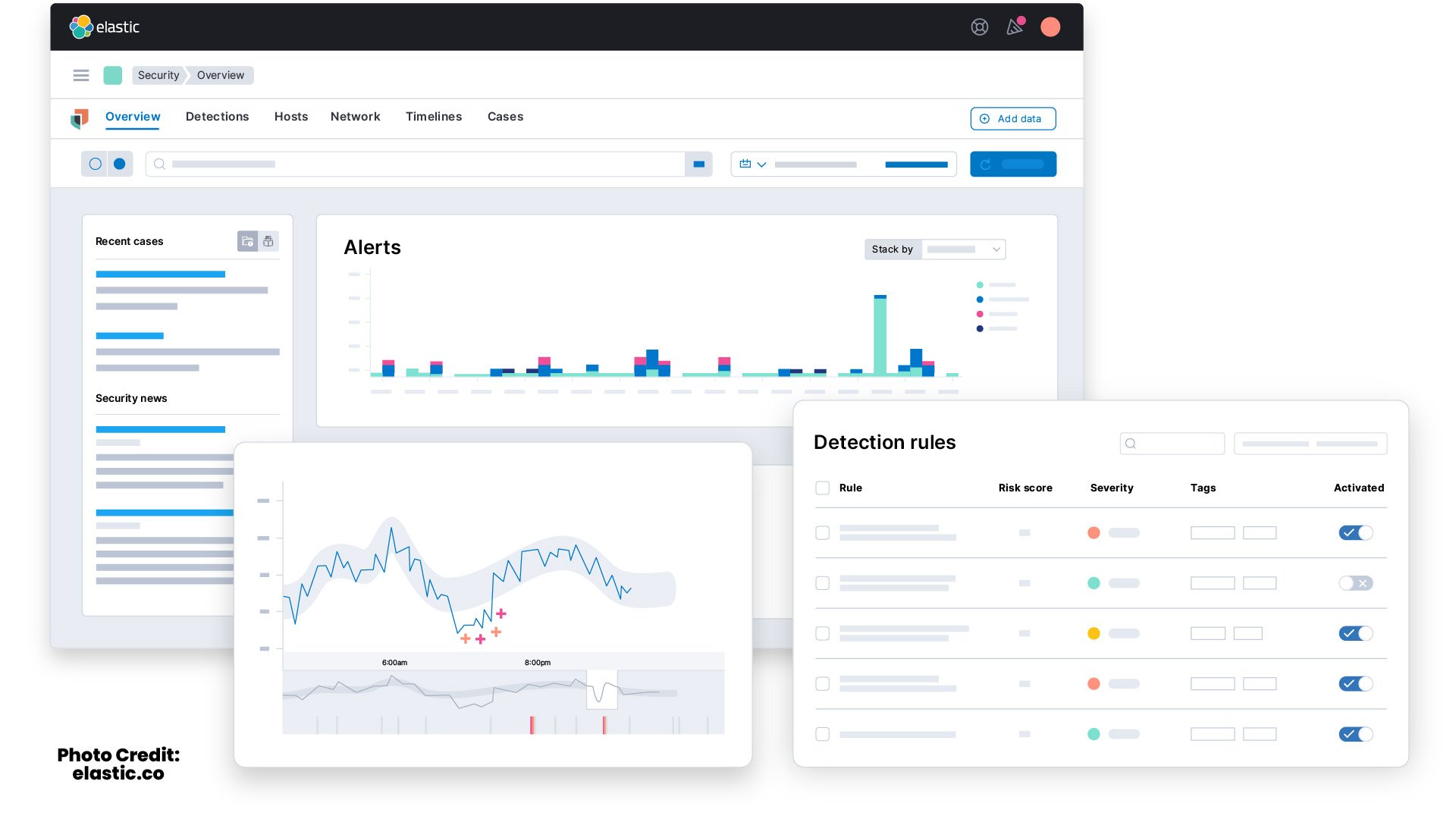
Log Collection
One of the most vital capabilities of any SIEM is the ability to collect data from a variety of sources like servers, databases, security controls, network infrastructure, and external security databases. The ELK stack performs log collection through Logstash and a fourth component to the stack, called Beats. Once downloaded, Beats and their separate modules must be configured to define what log to track. After Beats collects log data, the data can be bundled and processed by Logstash.
Log Processing
To be useful, data entries must be normalized, or translated into meaningful field names, for categorizing, analyzing, and storing. This activity, also called parsing, is essential to understanding the data collected by any SIEM system. With the addition of integrative plugins and careful configuration, Logstash can break up your logs, enrich specific fields with geographic information, for example, drop fields, add fields, and more.
Storage
After data is collected and parsed, it must be stored in data banks for access. In the ELK stack, Elasticsearch completes the tasks of indexing and storage. With benefits like open-source availability, easy set-up, speedy utilization, and scalability, Elasticsearch is one of the most popular databases available. Besides simply deploying Elasticsearch, you'll need to plan for scalability and long-term capacity. If you're deployed on the cloud, an auto-scaling policy may be necessary.
While ELK does have storage capabilities, it's important to note the lack of long-term retention provided by the system. Historical data is essential to perform investigations on attacks that evolve slowly over months. Additionally, many government compliance frameworks require the use of archives of up to 365 days for a successful audit. Since the ELK stack doesn't include archiving capability, security professionals will be required to create an architecture for retaining data.
Querying
Log queries enable you to conduct an investigation into previous security events. This is essential to pinpoint weaknesses that allowed attackers into the network or to reach their goal. Log querying in ELK stack is typically done through Kibana. The level of log query success you reach depends heavily on successful configuration of log processing or parsing with Logstash.
Visibility with the Use of Dashboards
Supplying security professionals with complete visibility into the activity of a network is essential to providing adequate security. This is accomplished through the use of dashboards that allow analysts to see multiple points of information on one screen. Kibana supports a wide variety of visualization types including pie charts, graphs, geographical maps, single metrics, data tables, and more. While these methods are effective, and dynamic when combined, the results are not automatically generated by the software. Instead, dashboards must be created by IT or cybersecurity professionals.
What Are the Functions of SIEM?
For any organization upgrading or implementing a successful cybersecurity system, SIEM is the word that pops up everywhere. The reasons for this are clear. Modern SIEM tools, especially Next-Gen SIEM, have been generated from decades of security efforts that have evolved along with the advance of cyberattacks that consistently grow in scope and sophistication. The results of this evolution make SIEM the hub of both cloud-based and on-premise SOCs. A complete SIEM system includes the following functions.
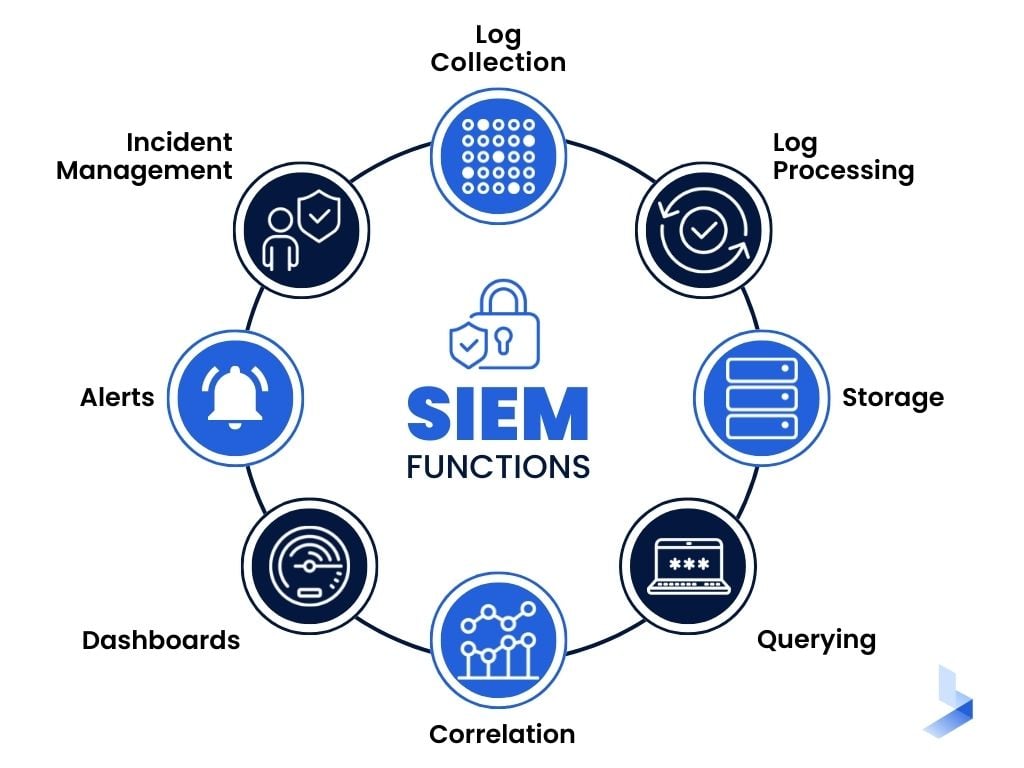
Log Collection
Data collection is the beginning step of SIEM, and like ELK stack, it's included in all comprehensive SIEM systems. SIEM software is available from a variety of vendors, and once the software is downloaded, it's capable of performing data collection services. However, for SIEM software to reach its intended capabilities, it must be customized and configured to collect the right data and parse it properly. For organizations that outsource cybersecurity, these tasks are usually completed by your software provider. Companies that depend on an on-premise SOC take care of the configurations while implementing SIEM software as part of a new system.
Log Processing
Most comprehensive SIEM systems have the ability to parse event data from common systems without being customized. However, to improve the way data can be stored and used in the future, it's typically useful to fine-tune the way information is parsed and processed.
Storage
Most effective SIEM systems utilize cloud storage to provide scalable storage options that have built-in backup features. Cloud storage provides SIEM systems the ability to keep up with your organization's need to continually consume and parse more and more information. This means a SIEM system is prepared to automatically scale storage usage as your company grows. More importantly, it has the capability to meet the long-term storage and archiving demands necessary for government regulatory compliance.
Querying
Like ELK stack, your SIEM system's querying capabilities depend on the early and ongoing stages of log processing configuration. While SIEM systems have querying capabilities out-of-the-box, the success rate and speed of the results depend on your system's customized ability to parse your organization's unique data. If your company utilizes the benefits of SIEM as a Service (SIEMaaS) these configurations will likely be completed by your security provider.
Correlation
The ability to review stored data in a way that connects related events from different data sources is referred to as correlation. Many sophisticated attacks use a single vulnerability to gain access. After gaining access to the network, the attacker uses covert actions to move laterally throughout the system until sensitive data is reached. The ability to connect multiple actions across different streams of data unveils these covert attacks and sends out alerts of suspicious activity. Correlation capabilities are a capability included in SIEM systems that the ELK stack doesn't have. This means event correlation is left up to security analysts when ELK stack is used for SIEM.
Dashboards
SIEM tools utilize dashboards for complete visibility of the events occurring throughout a network. Many SIEM systems come with pre-made dashboards that use multiple visual aids to help identify trends, detect unusual behavior, and monitor the general health of a security environment. While pre-configured dashboards may not have all the visual tools that exist in ELK stack's Kibana, they're immediately capable of sharing data without the creative efforts of on-site IT professionals.
Alerts
The ability of a SIEM system to generate alerts based on patterns of suspicious activity is a key aspect of success. When correlated data shows a suspicious pattern of behavior within the network, an effective SIEM system sends out an alert to a specified person or team within an organization. The importance of immediate alerts cannot be overstated, since the ability to successfully interrupt or halt an attack depends heavily on speed. While ELK stack doesn't provide a built-in alert system, the capability can be added with a plugin that integrates with ELK tools.
Incident Management
The ability to perform automated actions in relation to a threat is referred to as incident management. For instance, when a SIEM system has the ability to isolate a threat to the affected part of a network, all other departments can keep working as usual. Additional actions include threat mitigation through alerts and categorization of threats by importance.
The ability to add a plugin that provides alerts in ELK stack doesn't include the capability of reacting to these alerts. While an in-house SOC team can have a written procedure in place for managing incidents and alerts, the lack of automated response can delay vital actions.

| Related Reading: What is SIEM and Why Is it Useful? |
Is ELK a True SIEM Tool?
ELK does take care of log collection, processing, and storage. However, it doesn't accomplish event correlation, alert capabilities, and incident management out of the box. In its raw form, ELK could be a building block of a comprehensive SIEM system. However, it doesn't check all the boxes of a comprehensive SIEM system.
So, if ELK stack isn't a true SIEM, where does its popularity come from? The ELK stack is a combination of highly effective open-source log management tools. These tools can be used by a highly trained SOC team to create some of the major building blocks of a comprehensive SIEM system at a lower cost than seeking a complete system from a system provider. An accurate description of the ELK stack is a DIY tool that allows companies to build a complete security system with a variety of added tools, resources, and professional in-house staff.
ELK vs Securonix SIEM
When comparing ELK stack to SIEM systems, it's necessary to take certain elements of your existing organization into consideration. At startup, ELK stack is cheaper. It has also been suggested that ELK provides an alternative with no false alarms. Yet, the answer to avoiding false alarms isn't to omit alerts completely. To effectively compare ELK stack to SIEM, you need to understand the benefits of each system and how they relate to the unique needs of your organization. Here are five important comparison points to consider.
Cost
When running a business, the cost of any tool or service is always something to consider. However, with any tool that will be utilized over time, up-front cost is only one of the expenses to think about. Security software is designed to automate and improve some of the tasks required to implement a robust cybersecurity system. Ongoing maintenance and qualified security professionals make up the rest of the package.
- ELK Stack Cost: The ELK stack tools are easy to find and free to use. Additional costs to consider include professional staff for setup and configuration, potential costs for add-ons to complete SIEM features, professional upgrade costs, scalability costs, archiving costs, and infrastructure costs.
- SIEM Cost: The upfront cost of implementing a SIEM system will depend on the type of SOC your company uses. On-premise SIEM requires an organization to have the necessary infrastructure and staff in place to implement and manage the system. Your up-front costs will depend heavily on the infrastructure and security staff you already have in place. Cloud-based SIEM can be self-managed or managed by your MSSP. A self-managed system will cost more upfront for the purchase of company-owned software, but eliminate the monthly provider fee. If you already have an in-house security team in place to manage the system, costs will be limited to the purchase of new software and upgrades. Many companies choose to utilize the benefits of SIEMaaS from a provider. The entry costs are more affordable with this option, but a monthly provider fee is required to cover a fully managed security solution.
Implementation
Both SIEM and ELK stack require considerable setup and configuration efforts. To implement an effective security system, proper configuration should be completed by trained professionals with experience in cybersecurity.
- ELK Stack: There are many guides to provide information about how to get started with ELK. This means you can access and launch the system with little upfront cost. However, fine-tuning the system, creating dashboards, and planning for long-term storage typically requires the assistance of security professionals.
- SIEM: Software to get your SIEM up and running can be purchased from a variety of providers. Implementation costs depend on whether your company uses an on-prem SIEM or MSSP managed SIEM. Since SIEM software provides all the necessary capabilities, implementation costs will be limited to the time and resources needed for proper configuration. If you use SIEMaaS, the configuration costs will be included in your package.
Scalability and Upgrades
No security system should be considered a set-it-and-forget-it solution. To keep up with the constantly growing attack surface that exists with today's technology, your system needs to constantly grow and change.
- ELK Stack: Planning for data archiving, scalability with a growing business, and updates are essential when you rely solely on ELK Stack for security. Scalability costs may include architecture to support scalability and additional tools for archiving. When upgrading ELK Stack, it's essential to pay attention to replication and data synchronization while upgrading one node at a time. Otherwise, essential data could be lost. This could mean you'll need to seek professional services to handle an upgrade.
- SIEM: Most SIEM systems utilize cloud storage for long-term data storage and backup capabilities. This means they're built to naturally grow with your business. When using an MSSP managed SIEM service, upgrades will be provided by your security vendor. While there might be an added cost for new software, upgrades will most likely be included with routine maintenance costs.
Customer Support
One of the biggest issues facing the growing cybercrime epidemic is a global skills shortage in the cybersecurity industry. This means that recruiting qualified professionals to build an on-premise security team can be difficult, if not impossible. As a result of the skills shortage, many companies attempt to utilize existing IT staff or less experienced data analysts for security tasks, making customer support more important than ever.
- ELK Stack: ELK stack is an open-source log management tool with a supportive community. However, there is no managed support available in the event of an emergency.
- SIEM: Organizations that utilize the benefits of cloud-based SIEM typically have more options when it comes to customer support. A fully managed SIEM system is remotely managed by a team of professionals provided by your security vendor. On-prem SIEM systems can often access emergency services on an as-needed basis from the security provider as well. However, this may come at an additional cost.
Beyond Log Collection
There's no doubt that SIEM systems have more capabilities to offer out of the box. However, ELK stack can be used with additional plugins and integrative tools for a solution that is similar to a complete SIEM system. It's important to note that log management alone is not a complete SIEM solution. SIEM provides these benefits that go beyond log collection for a complete security solution.
- Advanced Log Ingestion: An advanced SIEM tool should come with many more pre-built security use cases for each log ingestion or log type.
- Alerts: Without the ability to provide timely alerts, ELK stack users depend solely on data analysts to manually provide alerts when suspicious behavior occurs. SIEM alerts can be configured to alert the correct personnel and even automate certain actions.
- Correlation: SIEM systems automatically correlate data from multiple locations for a more complete picture of how events connect within a network. Correlation can be used to detect patterns of unusual behavior.
- User Entity and Behavior Analytics: UEBA monitors typical behavior within a network and recognizes abnormal behavior. The automatic detection of behavior anomalies within valid user accounts is a powerful tool against persistent and ongoing threats that move discreetly throughout a network.
- Built-in Compliance: SIEM systems can be configured to provide streamlined compliance procedures and automated audit reports.
While ELK stack provides some high-quality tools for log management and compliance, it can't be used alone as a complete SIEM solution. It's also essential to understand that ELK is designed to be used with the monitoring capabilities of professional data analysts. While the upfront costs of ELK stack are attractive, the long-term costs of scalability and system management will quickly add up. Learn more about the benefits of a complete cloud-based SIEM system from the security experts at BitLyft Cybersecurity.
