Cybersecurity Showdown: Comparing the Top SIEM Tools

 By
Emily Miller
·
10 minute read
By
Emily Miller
·
10 minute read
In today's extensive threat environment, it's essential to have complete visibility into your entire business network and collect historical data for investigations. SIEM tools make it possible to analyze, catalog, normalize, and store massive amounts of data that provides insight into every action that takes place on the devices used to run your business. Most modern SIEM systems can also send alerts when suspicious behavior occurs, and launch automated response actions.
SIEM (Security Information and Event Management) is a type of software that collects and analyzes activity from the devices across your IT Infrastructure. It collects security data then normalizes, categorizes, and applies analytics to it to help security teams discover trends, detect threats, and enable organizations to investigate security events. SIEM provides real-time visibility into your network environment and sends alerts when suspicious behavior is detected.

Unfamiliar with how SIEM works to improve your cybersecurity posture and protect your business from threats in real-time? These articles can help you learn more about SIEM.
- Security 101: What is SIEM?
- SIEM Log Management: What it is and Why It's Vital for Cybersecurity
- Top 10 Benefits of Managed SIEM
- Getting to Know the Benefits of Securonix SIEM
- SIEM Implementation: How to Get Started with SIEM Tools
- 6 Ways to Drastically Improve Your SIEM Experience
- What is SIEM Tuning and Why Does it Matter?
- MDR vs SIEM: A Comparative Guide
What are SIEM tools?
Before we can look at the benefits of seeking security incident and event management tools, it is important to understand what these sorts of solutions are able to do. SIEM software is a combination of security information management (SIM) and security event management (SEM). These tools have the ability to monitor threats and provide real-time alerts regarding security. This enables you to boost your company’s compliance. On its own, SIM tools will collect data for analysis and reporting. On its own, SEM will centralize interpretation and store logs. When it comes to effective log management, you are going to need to use both of these tools, and they are often combined in SIEM software, rather than having to be used on an individual basis.
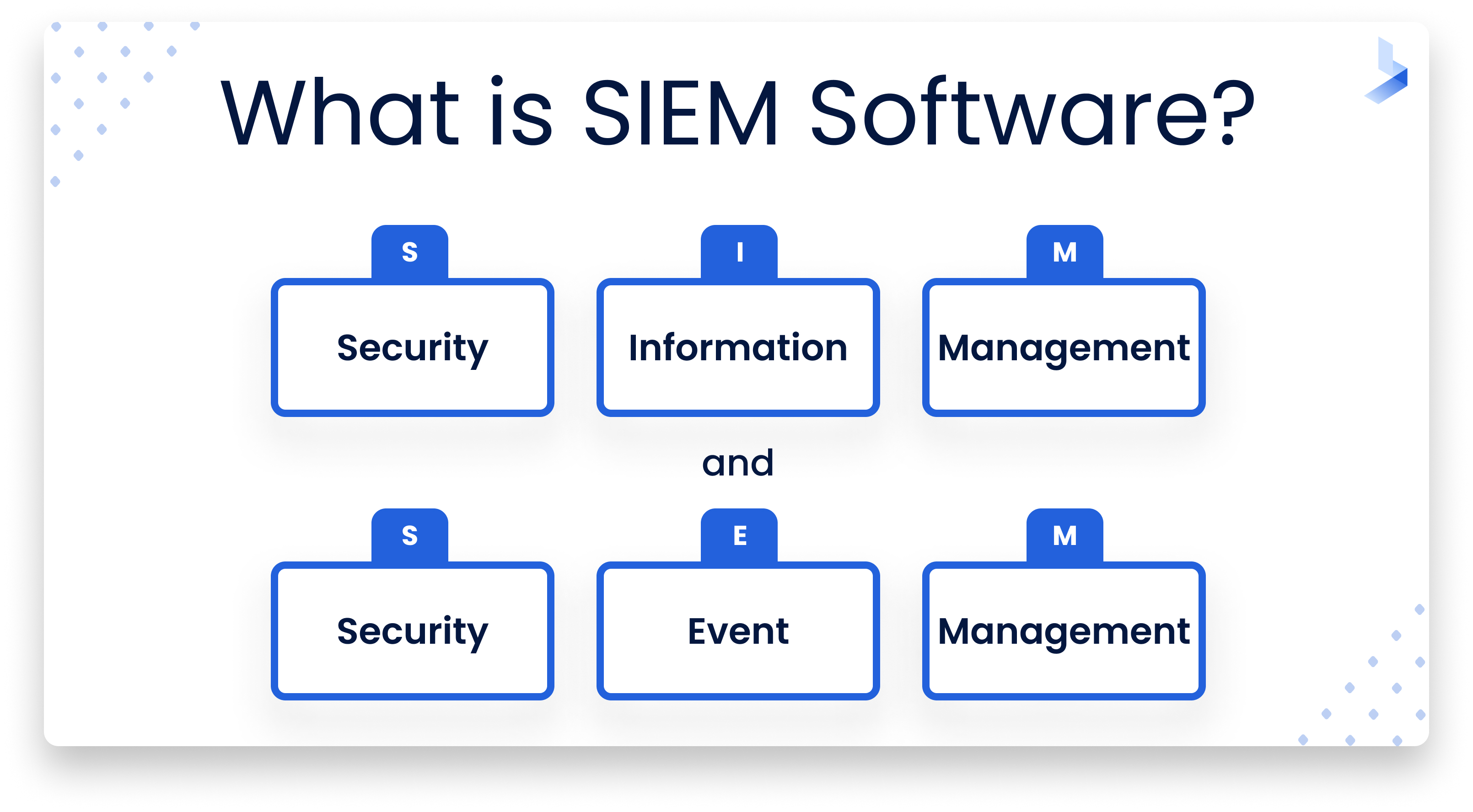
Why do you need to use a SIEM tool?
In today's rapidly evolving cyber landscape, the necessity for SIEM tools cannot be overstated. SIEM tools provide organizations with a comprehensive, centralized solution for monitoring, analyzing, and managing security events in real-time. They enable businesses to detect and respond to potential threats more efficiently, ultimately safeguarding their valuable data and digital assets.
Furthermore, SIEM tools enhance visibility across diverse systems and domains, reducing blind spots and facilitating faster incident response. By automating many security processes, SIEM tools not only save time and resources but also ensure compliance with relevant regulations and industry standards. I
n essence, employing a robust SIEM tool is a critical step in fortifying your organization's cybersecurity posture and mitigating the risks associated with today's cyber threats. Let’s take a look at some of the different benefits and features that make them instrumental today:
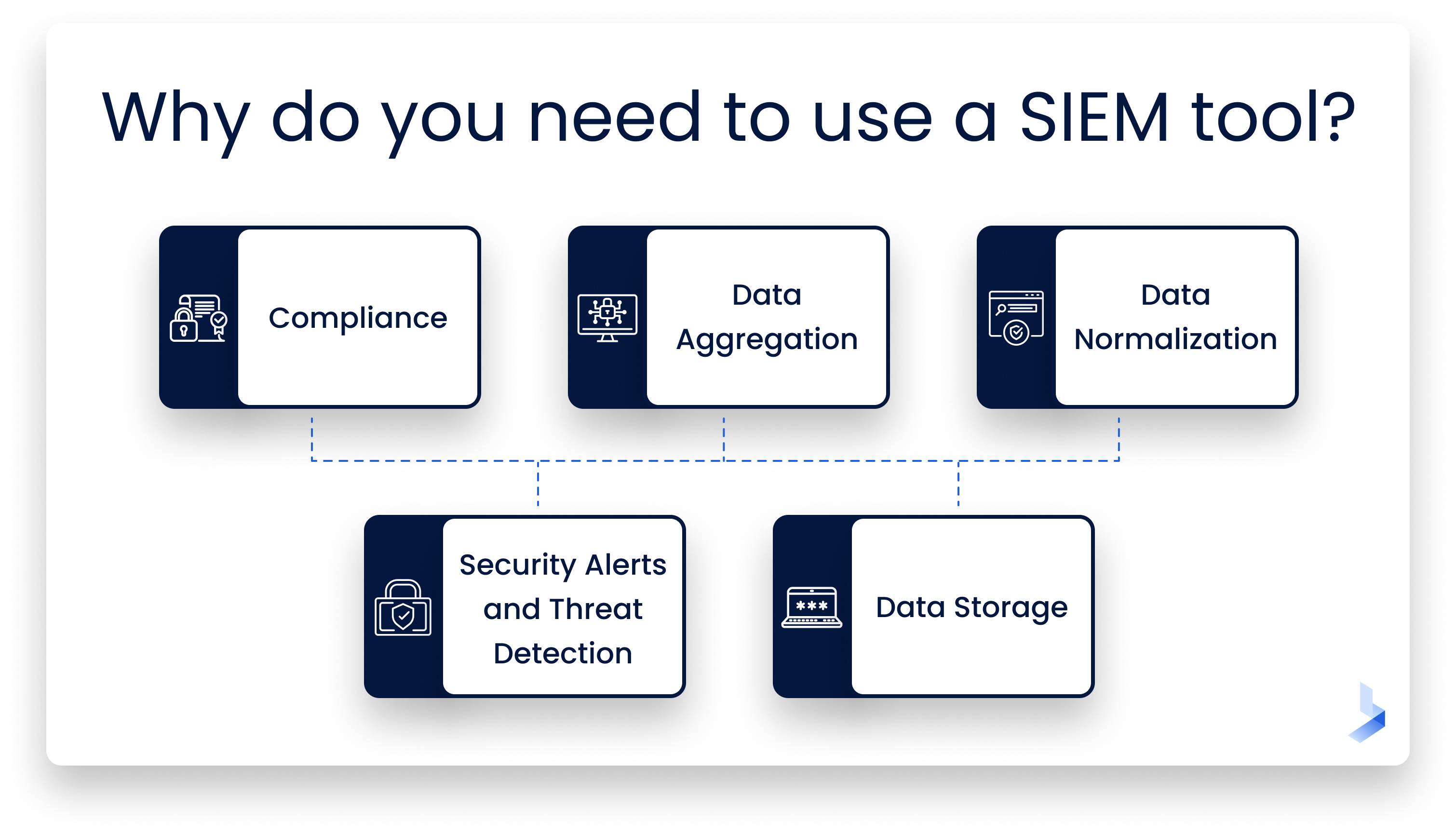
- Compliance: There is only one place to begin, and this is with compliance. SIEM tools present a great way for you to make sure that your business is compliant. Nevertheless, this does not mean that you should assume compliance is a given no matter what solution you choose. Make sure you go for one that comes with compliance assurance. After all, there is no getting away from the fact that there are going to be rules and regulations that you need to adhere to, no matter what industry you operate in. The consequences of not being compliant include massive legal costs because of a lawsuit, loss of sales, and a damaged reputation. This is why it is so important to invest in log management tools that provide you with compliance assurance so that you can have full peace of mind.
- Data aggregation: IT environment visibility is one of the main benefits of SIEM for enterprises today, even when it is used in its most basic form. Because of the log management capabilities of SIEM, visibility is assured. Under normal circumstances, as businesses scale, they start to lose visibility over their devices, users, databases, and applications. This means that third-parties can create dark places in your environment. This is something you do not have to worry about with SIEM because it basically enables you to turn the lights on, so to speak. All security information from your network will be monitored and centralized in one location.
- Data normalization: The data that you collect throughout your IT environment can come with a number of different challenges. This is where data normalization, a key benefit associated with SIEM, comes into place. Think about all the different components in your IT environment including everything from your devices and databases to login portals and applications. All of these are going to generate plain text data, potentially terabytes of it every few weeks. Collecting all of this data can be difficult in itself. Nevertheless, you then have to account for the fact that each one will generate, format, and send data profoundly in a number of ways. It is a mammoth task to try and make sense of all of this and to correlate it to security incidents. This is why these log management tools are so critical because SIEM will collect and normalize data for you. It will also present the data in any manner that is right for you and your business.
- Security alerts and threat detection: Aside from the points that have already been mentioned, it is important to use log management tools that come with security alerting and threat detection. Usually, SIEM tools are going to connect your IT security team to a number of different feeds regarding threat intelligence. This ensures you are up-to-date with everything that is happening in the world of cybersecurity. You have the power to secure your enterprise against data breach threats in the most effective manner possible. Moreover, your tools are going to be able to analyze potential threats by using the data it has collected and normalized, as they will be able to spot any data that looks misplaced and could indicate a security threat.
- Data storage: Last but not least, another key feature and benefit associated with the log management tools that are out there today is data storage. You need to be able to store your data in a secure manner whereby it can be normalized and organized, as well as being easy to retrieve whenever needed.
What are the best SIEM tools?
Log management has come a long way over the years. Initially, it did exactly what the name suggests; log management capabilities alone. However, technology advances and modern cybersecurity protocols and threats have required that log management be more robust. Now security incident and event management tools have become an imperative part of the log management software. Below, we are going to take a look at a few SIEM options in further detail, providing you with more information on the benefits associated with using log management tools like this.
While it's clear that SIEM tools are vital to any effective cybersecurity solution, finding the right option for your business can be challenging. To help you make the best possible choice, we've gathered relevant information about the top SIEM tools available.
Graylog
Graylog SIEM is part of a scalable, flexible cybersecurity platform that includes security analytics and anomaly detection capabilities with machine learning that adapts to your environment. The platform is available as a self-managed or cloud experience. The platform collects, parses, and stores logs. It provides users with intuitive dashboards to gain visibility into the entire network.
Key Features
- Archiving allows you to store older data on slow storage and re-import it as needed
- Compliance reporting built into the dashboards
- Easily updatable alerting based on a dynamic list
- Prebuilt and custom dashboards
- SOAR integrations
Pros & Cons
Reviews from Gartner Peer Insights note these pros and cons of Graylog.
Pros
- Easy log collection
- User-friendly dashboards
- Powerful log collection and search
- Low-cost options
Cons
- Steep learning curve
- Unclear pricing-- many features aren't available in the free version
- Limited support
- Resource hungry
- Limited out-of-the-box functionality and customizability can be complex
Recommended for
Graylog is ideal for a variety of customers. The company specializes in the government, fintech, education, telecom, and healthcare sectors.
Price Range
Graylog has three pricing models with different features.
- Graylog Open: Free- Self-managed and built to open source standards, support is only available through online resources including community and open groups
- Graylog Operations: Starting at $125/month (prepaid annually), Cloud or self-managed centralized log management
- Graylog Security: Starting at $155/month (prepaid annually), Cloud or self-managed SIEM services, includes technical support
LogRhythm
LogRhythm is an undisputed industry leader in the SIEM space available as a hardware appliance, software, cloud, or hybrid solution. The next-gen cloud-based platform is a full-featured SIEM solution. Logrhythm provides holistic visibility across hybrid environments to prevent, detect, and respond to cyberthreats. Users can gain complete visibility into their business networks and simplify compliance by centralizing controls into a single module,
Key Features
- 950+ third-party and cloud integrations
- 1,100+ preconfigured correlation rules
- Prebuilt threat playbooks and automated response
- Prebuilt threat analytics, threat intelligence feeds, and risk-based prioritization
Pros & Cons
Reviews from Gartner Peer Insights note these pros and cons of LogRhythm SIEM.
Pros
- Customizable dashboards and reports
- Fast response for rapid action related to validated alerts
- Easy-to-use search features
- User-friendly dashboards
- Effective real-time monitoring
Cons
- Issues with integration
- Setup can be difficult
- Some issues with long-term log retrieval
Recommended For
LogRhythm has long established itself in the SIEM solution sector. The company's SIEM tools are used across small and large businesses in many industries. LogRhythm is noted for use in the utilities, government, financial services, manufacturing, healthcare, and legal sectors.
Price Range
LogRhythm's pricing and licensing offer unlimited log sources and users. LogRhythm's software license is used for hardware, cloud, and virtual machines. LogRhythm offers three flexible pricing models.
- Software Solution: Available as a subscription or perpetual license
- True Unlimited Data Plan: Unlimited data usage during the life of your subscription term with no tiers, no fine print, and no surprises
- High-Performance Appliance: Simplified purchasing model with compatibility and performance assurance
LogRhythm doesn't offer any one-size pricing models. Customers must contact the company for more information and a custom quote.
Datadog
Datadog is a cloud-based system that monitors live events and collects them as log file entries to provide real-time visibility and historical data for threat investigation. The platform enables businesses to detect security threats in real time across applications, network, and infrastructure. Continuous scans work to help improve security posture and alerts are enriched with threat intelligence feeds.
Key Features
- Real-time security event detection
- 350+ default detection rules mapped to the MITRE ATT&CK framework
- Custom threat rule creation
- Over 600 vendor integrations
- Logged messages are categorized and retained for 15 months
Pros & Cons
Reviews from Gartner Peer Insights note these pros and cons for Datadog SIEM.
Pros
- User-friendly interface
- Easy to onboard log sources
- Timely support
Cons
- Lack of transparency in pricing model
- Doesn't support some data formats in real-time data visualization
- Requires engineering investment to get the most out of the service
Recommended For
As a cloud-based platform, Datadog is useful for businesses that run applications and services on multiple sites and cloud platforms. Services are designed for a variety of industries, including financial services, manufacturing & logistics, healthcare, retail, government, education, media, technology, and gaming.
Price Range
Datadog offers a 14-day free trial for each of its 3 pricing packages.
- Free: Core collection and visualization features with 1-day metric retention for up to 5 hosts
- Pro: $15 per host/monthly (billed annually or $18 on demand)
- Enterprise: $23 per host/ monthly (billed annually or $27 on demand)
Splunk
Splunk Enterprise Security is a SIEM platform that can be deployed on-premises or in multi-cloud environments. Splunk provides real-time data monitoring and alerts for abnormal behavior. Users can customize dashboards and alerts for complete visibility and fewer false positives. Built-in analytics allow you to react instantly to threats and conduct investigations.
Key Features
- 2,200 partners across industries
- Real-time network monitoring
- Historical analysis
- Scalable platform for ingesting data from structured and unstructured sources
- Access to 700+ detections for frameworks like MITRE ATT&CK, NIST, Kill Chain, etc.
Pros & Cons
Reviews from Gartner Peer Insights note these pros and cons for Splunk Enterprise.
Pros
- Can utilize behavior analysis to detect threats that aren't discovered through logs
- User-friendly interface
- Custom dashboard creation
- Designed for enterprises with flexible option for multiple use cases
Cons
- Steep learning curve
- May be more expensive than other options
- Complex data collection
- Integration issues and complexities added with increased integrations
- Complex search features
Recommended For
Splunk Enterprise Security is recommended for businesses of all sizes. However, cost and features may be a barrier for smaller businesses. Splunk is used across multiple industries, including communications, online services, manufacturing, financial services, public sector, and retail.
Price Range
Splunk offers a 15-day free trial of the SaaS version, Splunk Security Cloud with a processing limit of 5 GB of data per day. Splunk Enterprise pricing is based on how much data you ingest or workload demand. Different storage options are available and support is included in pricing. Potential customers must contact Splunk for a custom quote.
Exabeam
Exabeam Fusion is a cloud-based, SaaS SIEM service that provides centralized log management and extensive integration capabilities to connect with existing tools. The SIEM tool securely ingests, categorizes, and stores security data from any location for rapid search and alerting capabilities. Behavioral analytics help detect threats and automated investigation reduces manual tasks.
Key Features
- UEBA features develop baseline behavior to improve detection of insider threats
- SOAR features work with existing security measures to provide automated detection and response capabilities
- Automatic threat intelligence updates
- Improves compliance reporting with hundreds of playbooks and dashboards
- Integration options for over 500 security and IT tools
Pros & Cons
Reviews from Gartner Peer Insights note these pros and cons for Exabeam Fusion.
Pros
- End-to-end visibility
- Integration with a variety of security tools
- Baseline behavior established from activity
Cons
- Setup can be complex and may require expert assistance
- Steep learning curve
- Customer support is lacking
- Configuring new alerts can be complex
Recommended For
Cloud-based platform is ideal for large organizations that have multiple sites. It is used across a variety of industries, including financial services, healthcare, higher education, manufacturing, and government.
Price Range
Exabeam doesn't offer a free trial. There is no pricing information since pricing is based on customer needs. Potential customers must contact Exabeam for a custom quote.
Securonix
Securonix Next-Gen SIEM is an industry-leading SIEM platform that includes built-in advanced analytics, risk scoring, and threat chain modeling based on MITRE ATT&CK and US-CERT frameworks. The system collects data at scale, detects unknown threats with built-in UEBA, and automates incident response. Out-of-the-box MITRE ATT&CK based templates make deployment easy with minimal setup. The detailed and intuitive dashboard design makes it easy to identify anomalies.
Key Features
- Complete visibility into your business network through interactive dashboards
- Advanced, built-in UEBA to develop a baseline of normal behavior and alert to suspicious behavior
- MITRE ATT&CK-based analytics to detect cybercriminal TTPs
- Unlimited long term retention with over 90% compression for scalability
- Access to 350+ cloud connectors for data collection and API based cloud integrations
- All events are logged and categorized to improve threat hunting
- Reduced false positives
Pros & Cons
Reviews from Gartner Peer Insights note these pros and cons of Securonix SIEM.
Pros
- Large number of pre-packaged use cases make onboarding quick and easy
- Strong automated response to stop threats in progress
- Scalability for growing business
- Customizable dashboards
- Attentive support
Cons
- Significant learning curve for inexperienced users
- Poor effectiveness without proper implementation
- Wait times for support response
Recommended For
As a cloud-based SIEM, Securonix is effective for enterprises with hybrid and cloud-based environments. The scalability of the platform and simple pricing model also makes it a good choice for smaller businesses expecting future growth. Securonix SIEM is used across multiple industries with specialties noted in financial services and healthcare.
Price Range
Pricing for Securonix SIEM is based primarily on identity instead of quantity of events or gigabytes, making costs more predictable. Securonix SaaS deployment is available in three options, including multi-tenant deployment, isolated tenant deployment, and dedicated tenant deployment. Pricing is based on user requirements. Potential customers must call to get a custom quote.
SIEM is a critical feature of any comprehensive cybersecurity system designed to protect against modern sophisticated threats. This list reveals important facts about industry leaders and the different features that could make specific SIEM tools right for your organization. At BitLyft, we partner with two SIEM leaders, Securonix and LogRhythm. We have chosen them for their advanced capabilities and technical advantages that allow clients to glean all they need from a complete SIEM system. Contact us today to learn more about how SIEM helps protect modern businesses from sophisticated cyberthreats and how BitLyft can help you achieve improved cybersecurity posture and cybersecurity compliance.
