MDR vs SIEM: A Comparative Guide

 By
Emily Miller
·
10 minute read
By
Emily Miller
·
10 minute read
Businesses have a big decision regarding cybersecurity: should they invest in an MDR solution or a SIEM? Both offer different benefits, and it can be tough to decide which is the right option for your company.
MDR is a comprehensive solution that offers 24/7 monitoring and response services from experienced security analysts. SIEM, on the other hand, is a platform that provides visibility into your environment and helps you to detect and respond to threats.
.jpg?width=735&height=230&name=MDR%20VS%20SIEM%20(1).jpg)
In this comparative guide, we'll break down the pros and cons of each so that you can make an informed decision. We'll also take a look at some of the top MDR SIEM providers on the market today.
After reading this post, you'll know exactly which solution is right for you, so keep going.
The Importance of Cybersecurity
Cybersecurity is more critical than ever before. In the past, businesses could get away with having weak security measures in place.
However, as the world has become increasingly digitized, the stakes are much higher. Nowadays, a data breach can have devastating consequences for a company, including financial loss, damage to reputation, and legal trouble.
Businesses cannot afford to take chances with their cybersecurity. They need to have robust solutions in place to protect themselves from the ever-growing number of cyber threats.
That's where MDR and SIEM come in. These are two of the most popular cybersecurity solutions on the market, and they both offer a lot of benefits.
What Is MDR?
MDR, or Managed Detection and Response, is a comprehensive security solution that offers 24/7 monitoring and response services from experienced security analysts.
MDR solutions are designed to detect and respond to threats in real-time so that businesses can avoid the costly consequences of a data breach.
The main benefit of MDR is that it takes the burden of cybersecurity off of your shoulders. You don't have to worry about constantly monitoring your systems for threats because you have a team of experts doing it for you.
Another advantage of MDR is that it's highly customized. When you sign up for an MDR solution, you'll work with a provider to tailor the service to your specific needs. This ensures that you're getting the most out of the solution.
| Related Reading: Managed Detection and Response (MDR): All Your Questions Answered |
The Methods By Which MDR Works
Now that we've answered the question "what is MDR?" let's take a look at how it works.
MDR solutions use a combination of people, processes, and technology to detect and respond to threats in real-time.
The first layer of defense is the security analysts who are monitoring your systems 24/7. These analysts have experience in identifying cyber threats, so they can spot anything suspicious quickly.
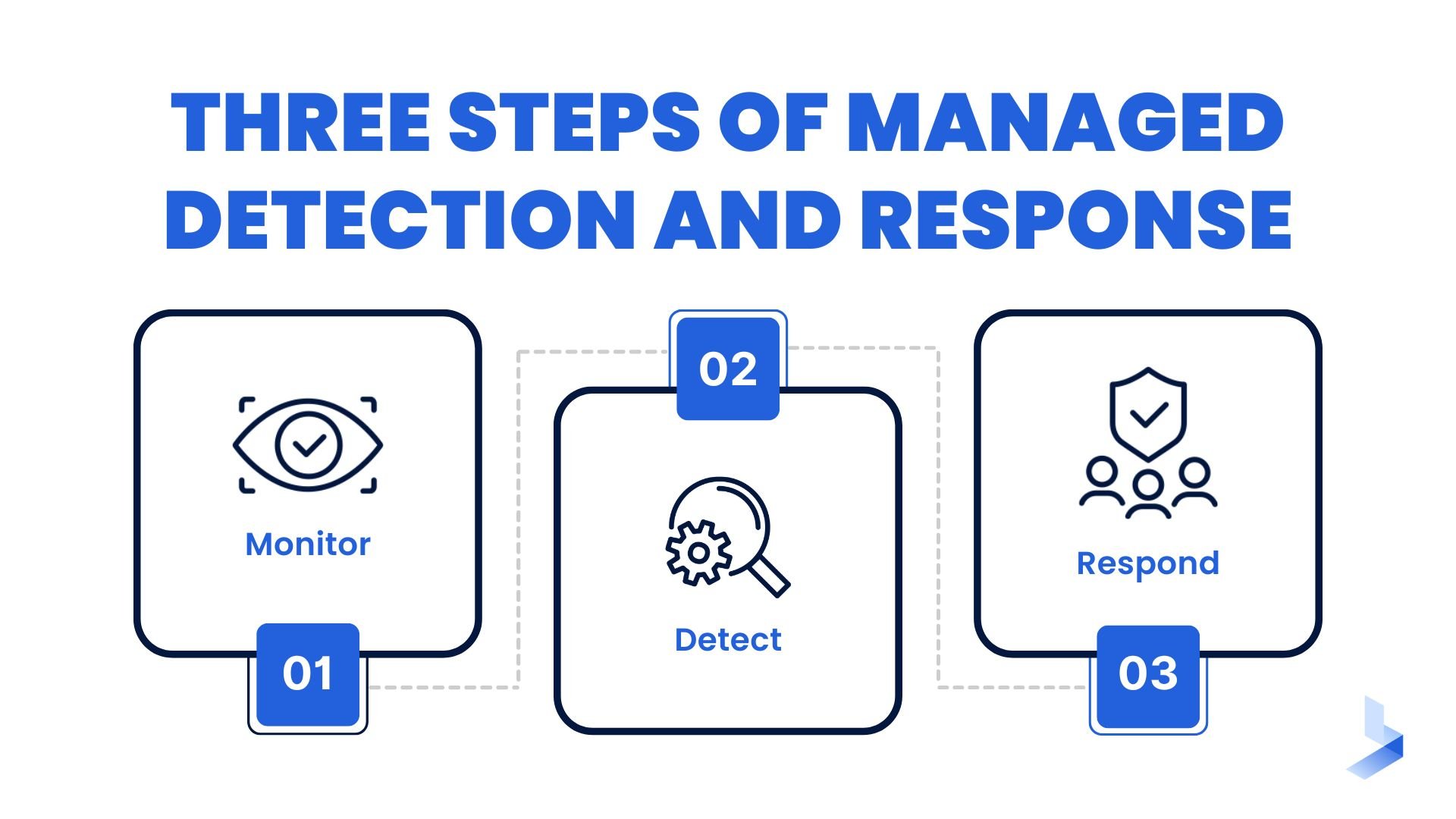
If they do detect a threat, they'll immediately start working on a response plan. This plan will be tailored to your specific needs so that you can resolve the issue as quickly as possible.
In addition to security tools, MDR solutions also make use of cutting-edge technology. This includes things like artificial intelligence and machine learning, which are used to detect threats that human analysts might miss.
Technology is constantly being updated so that it can keep up with the latest cyber threat landscape.
Let's take a look at the prominent features in greater depth.
Alert Investigation
MDR providers will have a team of analysts investigating alerts 24/seven. They will also provide you with a custom action plan for each incident.
This is usually done by providing you with step-by-step instructions on how to resolve the issue. SIEM tools, on the other hand, relies on your in-house security team to investigate and respond to alerts.
While MDR can be more expensive, it may be worth the price if you don’t have the internal resources to staff a SIEM solution properly. If you do have the internal resources, then SIEM may be the better option as it gives you more control over your environment.
Incident Triage
MDR providers will also help you prioritize and triage incidents. This is done by understanding your environment and business objectives.
They will then work with you to determine which incidents are the most critical and need to be addressed first. SIEM does not provide this service as it is up to the security analyst to prioritize and triage incidents.
MDR can be beneficial if you don’t have the experience or knowledge to prioritize and triage incidents properly. However, SIEM may be a better option if you want more control over how incidents are prioritized and triaged.
Response & Remediation
Once an incident has been subject to investigation, MDR providers will work with you to determine the best course of action for remediation. They will also provide you with step-by-step instructions on how to resolve the issue.
MDR can be beneficial as it takes the guesswork out of incident response and remediation. Nobody wants to guess what to do when it comes to cybersecurity, it's important to have a plan and execute on it when troubles comes knocking on your door.
Proactive Threat Hunting
MDR providers will also proactively hunt for threats in your environment. This is done by continuously monitoring your environment and looking for indicators of compromise. If a threat is found, the MDR provider will work with you to determine the best course of action.
MDR can be beneficial as it helps you identify threats before they have a chance to cause damage. Prevention is the best medicine in the world of cybersecurity.
Continuous Monitoring
MDR providers will continuously monitor your environment for changes. This includes monitoring for new vulnerability management, configuration changes, and user activity. if a change is detected, the MDR provider will investigate to determine if it poses a risk to your environment.
MDR can be beneficial as it helps you identify potential risks before they have a chance to cause damage. That's about half of the problem already solved, as you must first become aware of it.
What Is SIEM?
SIEM, or Security Information and Event Management, is a platform that provides visibility into your environment and helps you to detect and respond to threats.
SIEM solutions collect data from all of the devices on your network and use it to generate security alerts. This data can include everything from system logs to user activity.
The main benefit of SIEM is that it gives you complete visibility into your network. You can see everything that's happening in real-time, which makes it easier to spot potential threats.
Another advantage of SIEM is that it's highly scalable. As your business grows, you can add more devices to your network without having to worry about the solution being overwhelmed.

| Related Reading: What is SIEM and why is it useful? |
The Methods By Which SIEM Works
SIEM works in a few different ways. The first is by collecting data from various sources, including system logs, application logs, and network traffic data. This data is then normalized into a common format so that it can be analyzed more effectively.
Once the data has been subject to normalization, SIEM uses correlation rules to detect potential security threats. Of course, this can be done manually, but why waste time on this?
These correlation rules are based on expert knowledge of what constitutes a security threat and are constantly being updated as new threats emerge. Finally, SIEM produces alerts that can be subject to investigation by security analysts.
Other methods of SIEM operation include behavioral analytics, which uses machine learning to detect anomalies in user behavior, and threat intelligence, which can block known threats proactively.
Let's take a look at the prominent features in greater depth.
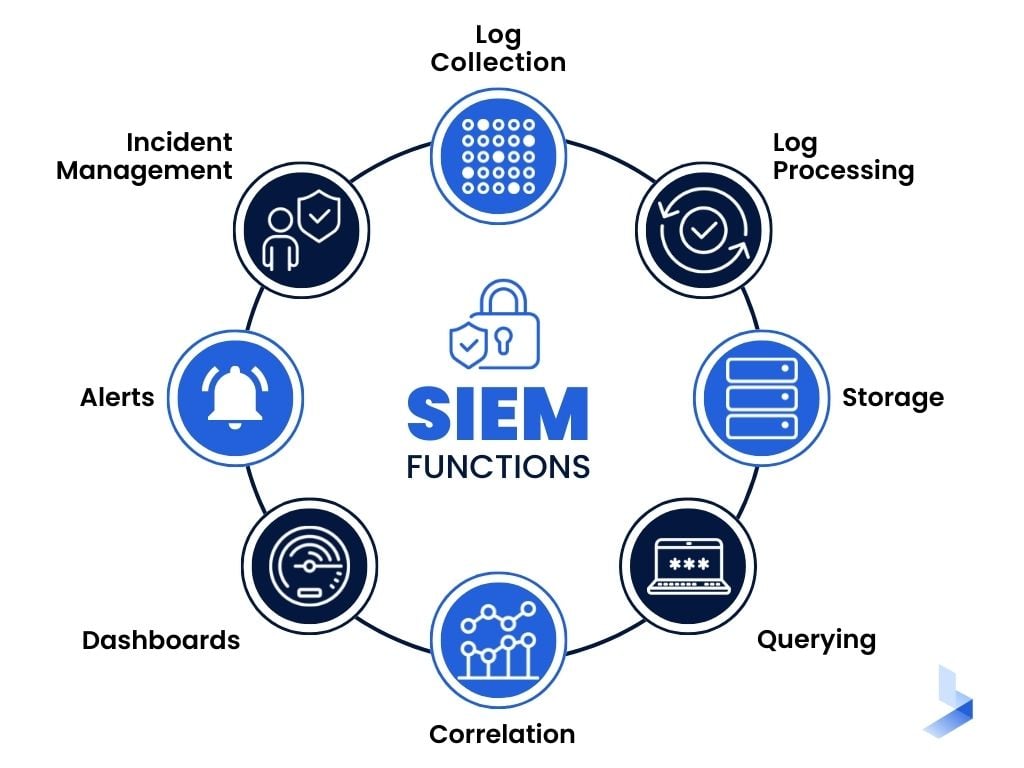
Threat Detection & Analysis
The main purpose of SIEM is to detect and respond to threats. It does this by collecting data from all of the devices on your network and using it to generate security alerts. This data can include everything from system logs to user activity.
Once the data has been subject to collection, SIEM uses correlation rules to detect potential security threats. Detection is critically important to cybersecurity as a whole.
These correlation rules are based on expert knowledge of what constitutes a security threat and are constantly being updated as new threats emerge.
Finally, SIEM produces alerts that can be subject to investigation by security analysts. These alerts contain information about the potential threat, such as when it occurred and which devices were involved.
Digital Forensics & Threat Hunting
In addition to detecting and responding to threats, SIEM can also be subject to use for digital forensics and threat hunting.
Digital forensics is the process of investigating a security incident after it has occurred. This can involve anything from analyzing system logs to interviewing employees.
Threat hunting is the proactive process of searching for indicators of compromise that may not have been subject to detection by SIEM. This can be useful for identifying advanced threats that have evaded detection.
Regulatory Compliance
SIEM can also be subject to use to help you meet regulatory compliance requirements.
This is because SIEM provides complete visibility into your environment and generates alerts when potential compliance violations are detected.
For example, if you're required to store all data for a certain period of time, SIEM can help you ensure that this data is properly stored and protected.
MDR vs SIEM: Which Is Right for You?
Now that we've looked at what MDR and SIEM are, it's time to compare them. Here's a breakdown of the pros and cons of each solution:
MDR Pros:
- It takes the burden of cybersecurity off of your shoulders
- Highly customized
- Offers 24/seven monitoring and response services from experienced security analysts
MDR Cons:
- Can be expensive
- Requires a long-term commitment
SIEM Pros:
- It gives you complete visibility into your network
- Highly scalable
- It can be subject to use to supplement other security solutions
SIEM Cons:
- Requires a high level of technical expertise
- It can generate a lot of false positives
As you can see, both MDR and SIEM have their own advantages and disadvantages. The solution that's right for you will depend on your specific needs.
If you're looking for a comprehensive security solution that takes the burden off of your shoulders, then MDR is a good option. However, if you're looking for a platform that provides visibility into your environment and helps you to detect and respond to threats, then SIEM is the better choice.
How to Find the Right Vendor for Your Security Needs?
Now that you know the difference between MDR and SIEM, it's time to find the right vendor for your needs.
Don't forget to ask about pricing and get a sense of what you'll be getting for your money. Once you've found a vendor that meets all of these criteria, you can be confident that you're making the best decision for your business.
You need to ensure that you vet possible vendors carefully to find the best one for your specific needs. Here are some questions you can ask potential vendors:
- What is included in your security solution?
- Do you offer 24/7 monitoring and response services?
- What is your approach to threat detection?
- How scalable is your platform?
- Can your platform be subject to use to supplement other security solutions?
- What are your pricing options?
Asking these questions will help you to narrow down your options and find the best vendor for your needs. Don't forget to read online reviews and get a sense of what other customers have had to say about the vendor's products and MDR services.
Why You Might Need Both Solutions
In some cases, you might find that you need both MDR and SIEM. For example, if you have a large and complex environment, then SIEM can be subject to use to supplement your MDR solution.
Both solutions work symbiotically to provide you with the best possible security for your business. For instance, here's an example of a security incident that could be subject to detection and responded to using both MDR and SIEM:
An employee clicks on a phishing email and enters their credentials into a malicious website.
The SIEM platform detects unusual activity on the network related to this incident.
The security analyst team is subject to notifcation of the potential threat and begins investigating.
The analysts use MDR tools to contain the threat and prevent it from spreading further.
Once the threat has been subject to containment, the analysts use SIEM to identify which systems were affected and make sure that they are all secured.
In this example, you can see how MDR and SIEM work together to detect, contain, and respond to a security incident.
Common Mistakes Made By Businesses In Terms of Cybersecurity
There are a few common mistakes that businesses make when it comes to cybersecurity.
One of the most common mistakes is failing to invest in a comprehensive security solution. Many businesses believe that they can get by with a basic firewall and antivirus software, but this is simply not enough.
Another mistake is not keeping up with security patching and updates. Failing to install security patches promptly can leave your systems vulnerable to attack.
Finally, many businesses don't have a formal incident response plan in place. This means that they are not prepared to deal with a security incident if one were to occur. In addition, they may not have the necessary tools and resources in place to respond effectively to an incident.
Investing in a comprehensive managed security service like MDR or SIEM is one of the best ways to protect your business from cyber threats.
Is It Expensive to Implement MDR or SIEM?
The cost of MDR and SIEM can vary depending on the size and complexity of your environment.
However, it's important to remember that the cost of implementing these solutions is nothing compared to the cost of dealing with a data breach or other security incident.
In addition, these solutions can help you to avoid compliance penalties and other costs associated with failing to meet cybersecurity standards.
Data breaches can lead to legal action, loss of customer trust, and damage to your reputation. In addition, you may be subject to requirement to pay hefty fines if you are found to violate data privacy laws.
The bottom line is that investing in MDR or SIEM is a wise decision for any business that wants to protect itself from the ever-growing threat of cyber attacks.
Outsourcing Cybersecurity vs In-House Optimization
When it comes to cybersecurity, businesses have the option of either outsourcing their security needs or handling everything in-house.
There are pros and cons to both options. For example, outsourcing your cybersecurity can be expensive. However, it can also free up your internal resources so that they can be subject to use for other purposes.
In-house optimization can be a more cost-effective solution, but it requires a significant investment of time and resources.
The decision of whether to outsource or handle cybersecurity in-house depends on the specific needs of your business. We don't recommend companies that don't already have an established security infrastructure to go in-house with optimization because the upfront cost can be prohibitive.
If you are a business that is looking to improve your security posture, we recommend investing in MDR or SIEM. These solutions will provide you with the comprehensive protection you need to keep your data safe from cyber-attacks.
At What Point Should A Business Invest In Cybersecurity?
There is no one-size-fits-all answer to this question. The decision of when to invest in cybersecurity depends on various factors, such as the size of your business, the industry you're in, and the types of data you process.
However, we recommend that businesses start thinking about cybersecurity as soon as they start handling sensitive data.
Data breaches are becoming more common, and the cost of dealing with a breach can be high. In addition, many countries have enacted data privacy laws that require businesses to take steps to protect the personal information of their customers.
Investing in MDR or SIEM is an excellent way to meet these requirements and protect your business from the growing threat of cyber-attacks.
Are There Any Alternatives to MDR SIEM?
There are a few alternatives to MDR and SIEM, such as managed detection and response (MDR) and security information and event management (SIEM).
However, these solutions are not as comprehensive as MDR or SIEM. They also tend to be more expensive.
The bottom line is that MDR and SIEM are the best choices for businesses that want to protect themselves from cyber-attacks. These solutions provide complete protection from the latest threats, including malware, phishing attacks, and ransomware.
If you're looking for an alternative to MDR or SIEM, we recommend investing in a next-generation firewall (NGFW). NGFW's offer many of the same benefits as MDR and SIEM, but they are typically more affordable.
Cybersecurity Solutions Made for You
MDR and SIEM are both great options, but it's essential to understand their differences before deciding. Luckily, our comprehensive guide has you covered.
Once you've decided which solution is right for you, it's time to find the perfect vendor. Be sure to ask about pricing and get a sense of what you'll get for your money. With the right vendor in place, you can be confident that your business is protected against all threats.
If you're not sure whether you need MDR SIEM, or if you need both solutions, then don't hesitate to reach out to a cybersecurity expert. They'll be able to assess your needs and recommend the best solution for your business.
Protecting your business against cyber threats is essential in today's world, so ensure you have the right solution. If you'd like to upgrade your cybersecurity posture, contact us now.
