What Is Managed Detection and Response (MDR)?

 By
Emily Miller
·
10 minute read
By
Emily Miller
·
10 minute read
You may have heard the term Managed Detection and Response (MDR) service thrown around in recent news or conversations, but what does it actually mean?
How can it help protect your business from cyber threats? Well, it is known that companies that take a proactive approach to secure their business will ensure a lower risk of security issues.
In this blog post, we will explain everything you need to know about MDR services and how they work. We'll also discuss how they differ from other common security solutions, such as managed security services or cybersecurity insurance.
Keep reading to delve deep into the world of improving your company's security posture via proven human expertise.
What is Managed Detection and Response?
Managed detection and response is a type of security solution that proactively monitors your networks. It also assesses systems for signs of malicious activity.
MDR services use a combination of advanced analytics, and machine learning. They also involve human expertise to investigate potential threats and take action to stop them.
MDR services are designed to complement your existing security solutions. For instance, firewalls, intrusion detection systems, and antivirus software.
They can also be used as a standalone security solution for businesses. This is true for companies who lack the resources or expertise to implement their own cybersecurity program.
How Does Managed Detection and Response Work?
MDR services use a combination of automated security tools and human expertise to monitor your networks.
The first step is to collect data from your networks and systems, including logs, traffic data, and other types of information. This data is subject to analysis using advanced analytics. Machine learning algorithms also work to identify potential threats.
Once a threat is subject to identity, the MDR service will take action to stop it. For example, blocking malicious traffic or quarantining infected files.
The core capacities of an MDR are:
Prioritization
Managed prioritization of alerts saves your security teams time by only having to focus on the most serious threats. Prioritization is based on the type of threat, its potential impact, and other factors.
Furthermore, MDR services can help you investigate and respond to incidents, even if you do not have a dedicated security team.
MDR providers will work with you to understand the scope of the incident and take action to contain it. They will also provide guidance on how to prevent similar incidents from happening in the future.
Investigation
The investigation looks for indicators of compromise, such as unusual network traffic or file activity.
Moreover, MDR services can provide forensics analysis. This is to help you understand how an incident occurred and what data was compromised. This information can help to improve your security posture and prevent similar incidents from happening in the future.
Reporting
MDR services provide detailed reports that can help to improve your security posture and prevent future attacks. These reports can also help to satisfy compliance requirements.
Furthermore, MDR services can help you develop an incident response plan. This plan will outline the steps that need to be taken to effectively respond to incidents.
Remediation
MDR services can also help you resolve any issues that may have been caused by a security incident.
This may include restoring files that were deleted or corrupted by malware and resetting passwords. It also covers taking other steps to return your systems to a known good state.
Remediation also covers the process of identifying and repairing any underlying vulnerabilities. This may include patching software and updating passwords. It will also involve steps to prevent similar incidents from happening in the future.
Threat Hunting
MDR services can also proactively hunt for threats that have not been detected by your existing security solutions. This is done by analyzing data for signs of unusual activity or known indicators of compromise.
Threat hunting can help you find sophisticated attacks that have evaded your other security controls. It can also help you identify vulnerabilities that could be subject to exploit in the future when avoiding a security assessment.
Training
MDR services can provide training to your staff on how to effectively use the MDR service and how to respond to incidents. This training can help improve your organization's overall security posture.
In conclusion, MDR services can provide a comprehensive solution for detecting, investigating, and responding to threats. They can also help you remediate the underlying vulnerabilities that allowed the incident to occur. MDR services can provide a valuable addition.
Alternatives to MDR Services
There are several alternatives to MDR services, including managed security services (MSS) and cybersecurity insurance. Managed security services are similar to MDR services in that they provide proactive monitoring and incident response services.
However, MSS providers typically do not have the same depth of knowledge or experience as MDR providers. In addition, managed security services can be more expensive than MDR services.
Cybersecurity insurance is another option for businesses looking for protection from cyber attacks. This type of insurance covers the cost of damages caused by a cyberattack, such as data breaches, business interruption, and reputation damage.
Cybersecurity insurance can also provide coverage for legal expenses incurred in the aftermath of an attack. However, it does not provide the same level of protection as MDR services.
In addition, MDR services can provide a comprehensive solution for detecting, investigating, and responding to threats. They can also help you remediate the underlying vulnerabilities that allowed the incident to occur. MDR services can provide a valuable addition to your organization's security posture.
How Managed Detection and Response Works?
MDR services use a combination of technology and human expertise to monitor, detect and respond to cyber threats.
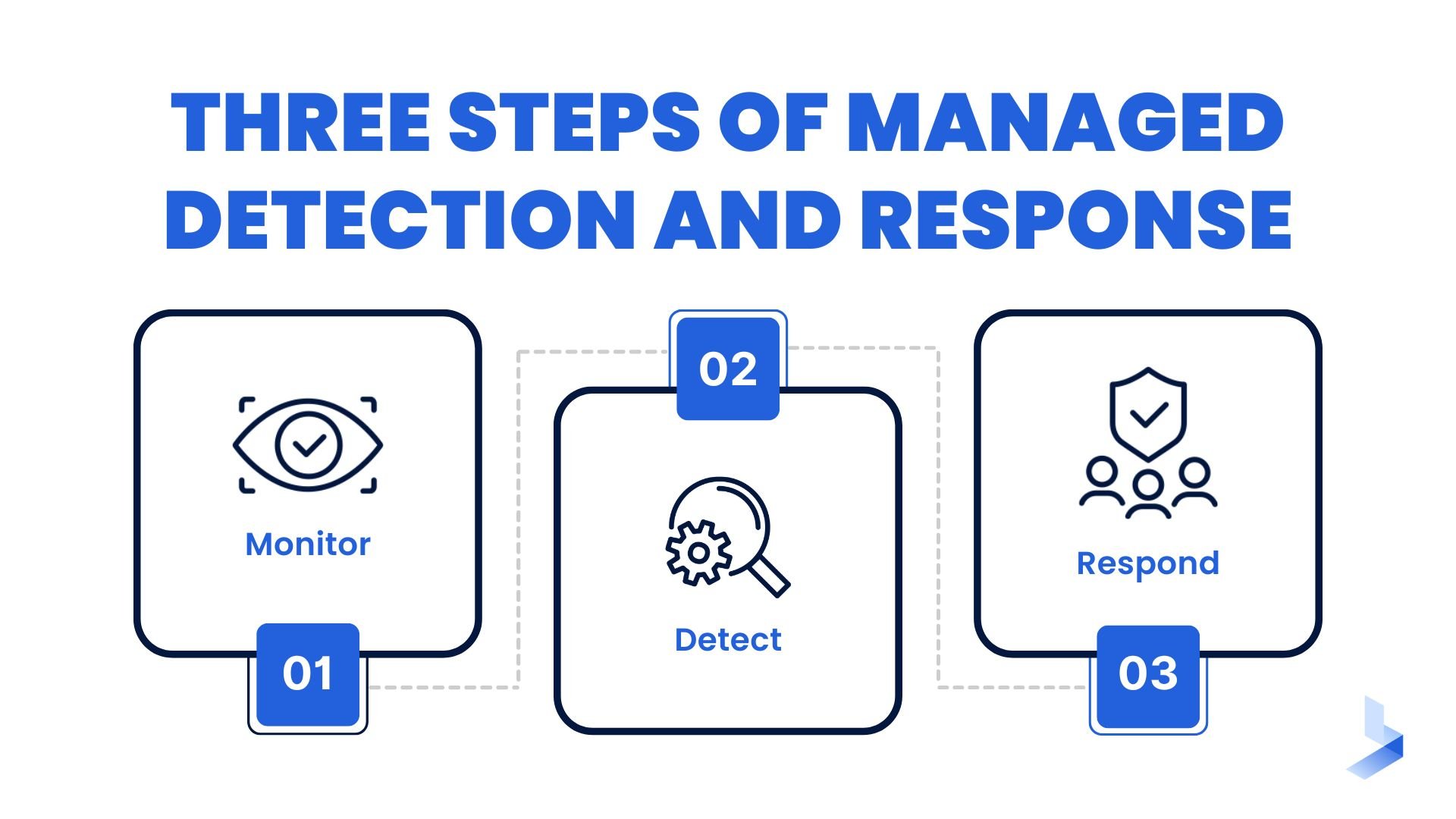
The security technologies component includes advanced analytics and machine learning. These are used to identify unusual or suspicious activity.
The human component consists of experienced security analysts. They investigate potential threats and take action to stop them.
MDR services are typically delivered as a cloud-based solution. This means that they can be quickly deployed and scaled to meet the needs of your business.
There are many benefits of using an MDR service, including:
Reduced risk of cyber attacks: By proactively monitoring your networks and systems for signs of malicious activity, MDR services can help reduce the risk of cyberattacks.
Improved Security Posture
MDR services can help improve your security posture by providing expert guidance. Usually, it covers how to best protect your business from cyber threats.
Faster Response Times
In the occurrence of security events of a cyber attack, MDR services can help you quickly identify and respond to the threat. This can help minimize the damage caused by an attack and get your business back up and running as quickly as possible.
Lower Costs
MDR services can help save you money by reducing the need for costly security solutions. For instance, managed security service or cybersecurity insurance.
Furthermore, MDR services can help you meet your compliance obligations, such as the EU General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS).
Who Should Make Use of MDR? Who Does It Benefit Most?
Organizations that can benefit most from MDR services are those that:
Have limited in-house security resources: MDR services can help businesses with limited security resources by providing expert guidance and support.
Are understaffed: MDR services can help businesses that are understaffed by providing additional resources to help them detect and respond to threats.
Lack of expertise: MDR services can help businesses that lack expertise in cybersecurity by providing access to experienced security analysts.
Face complex threats: MDR services can help businesses that face complex threats by providing advanced analytics and machine learning capabilities.
In conclusion, MDR services can provide a comprehensive solution for endpoint detection, investigating, and responding to threats.
They can also help you remediate the underlying vulnerabilities that allowed the incident to occur. MDR services can provide a valuable addition to your organization's security posture.
If you are looking for an insurance policy that covers the cost of damages caused by a cyberattack, MDR services can be a better option for you.
Cybersecurity insurance can also provide coverage for legal expenses incurred in the aftermath of an attack, but it does not provide the same level of protection as an MDR service.
What Is GDPR?
The General Data Protection Regulation (GDPR) is a regulation of the European Union (EU) that became effective on May 25, 2018.
It strengthens and builds on the EU’s current data protection framework, the General Data Protection Regulation (GDPR) replaces the 1995 Data Protection Directive.
The GDPR sets out the rules for how personal data must be subject to collection, processed, and stored by organizations operating in the EU.
It also establishes new rights for individuals with respect to their personal data. Finally, it creates enforcement mechanisms to ensure that organizations comply with the GDPR.
What Is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards. They came from major credit card companies to protect cardholders’ data. PCI DSS applies to all organizations that process, store, or transmit credit card data.
The PCI DSS includes 12 requirements for security management, policies, procedures, network architecture, software design, and other critical protective measures. Organizations must implement all 12 requirements to be compliant with PCI DSS.
MDR services can help you meet the compliance obligations of GDPR and PCI DSS.
How Much Do Managed Detection and Response Services Cost?
Managed detection and response services typically cost between $1000 and $5000 per month.
The exact cost will depend on the size of your organization and the complexity of your network. MDR services are usually priced as a subscription fee, which means that you will pay a monthly or annual fee for the service.
Some MDR providers offer discounts for prepaying for a year or more of service. You may also be able to negotiate a lower price if you are willing to commit to a longer-term contract.
How Do I Choose a Managed Detection and Response Service Provider?
There are many factors to consider when choosing an MDR service provider, such as:
- the size of your organization
- the complexity of your network
- your compliance obligations
- your budget
- your specific security needs
You should also consider the reputation of the MDR service provider and whether they have experience working with businesses like yours. Make sure to read online reviews and check references before making your final decision.
Let's take a look at each factor in greater detail.
Organization Size
The size of your organization will determine the number of devices and users that need to be subject to protection. A small business with a few dozen employees will have a different set of security needs than a large enterprise with thousands of employees.
Complexity of Network
The complexity of your network will also affect the type of MDR service you need. A simple network with a few hundred devices is easy to protect. But a complex network with thousands of devices and multiple locations can be more difficult to secure.
Compliance Obligations
Your compliance obligations will dictate the type and level of protection you need. For example, if you are required to comply with PCI DSS, then you will need an MDR service that provides comprehensive coverage for credit card data.
Budget
Your budget will determine how much you can afford to spend on an MDR service. Keep in mind that MDR services are typically priced as a subscription fee, so you will need to factor in the cost of the service over time.
Security Needs
Your specific security needs will also influence your decision. For example, if you are concerned about malware, then you should look for an MDR service that offers comprehensive malware protection.
Reputation and Experience
When choosing an MDR service provider, it is important to consider their reputation and experience. Make sure to read online reviews and check references before making your final decision.
You should also ask the MDR service provider about their experience working with businesses like yours. Make sure they have the experience and expertise you need to protect your business.
Evaluating Proposals the Right Way
When evaluating proposals, be sure to consider:
- the price of the service
- the features and capabilities of the service
- the experience of the provider
- the terms of the contract
You should also ask each provider how they would handle a security incident at your organization. This will give you a sense of their response times and their ability to resolve incidents quickly.
Once you have selected an MDR service provider, be sure to sign a contract that clearly outlines the scope of the service and the terms of the agreement.
Business Challenges for MDR Adoption and Integration
While MDR services can offer many benefits, there are also some challenges that need to be considered.
One of the biggest challenges is integrating the MDR service into your current security infrastructure. This can be a time-consuming and difficult process. The primary culprits in this regard are:
Resources & Staffing
You will need to allocate the necessary resources (people, time, and money) to get the integration project off the ground. The staffing aspect is critical, as you will need to have the right people in place to manage the project.
Complexity of Environment
The more complex your environment, the more difficult it will be to integrate the MDR service. This is because you will need to account for all of the different devices and systems in your network.
Downtime & Disruption
Another challenge is that the integration process can cause downtime and disruption to your business. This is why it is important to work with a provider that has experience integrating MDR services into complex environments.
Tool Sprawl
As your organization grows, so does the number of security tools you need to manage. This can lead to "tool sprawl" which makes it difficult to keep track of all the tools and their corresponding licenses. This is also recognized in other types of software segments, not just MDR.
Complexity
As your network grows in complexity, it can become more difficult to manage and monitor all of the devices on your network. This is especially true if you have multiple locations or a large number of users. Complexity has to be managed and integrated over time so that security changes can adjust accordingly.
Alert Fatigue & Dread
Another challenge is "alert fatigue." This occurs when you are bombarded with so many security alerts that you start to ignore them. This can lead to "security dread," which is a state of anxiety caused by the constant fear of being hacked.
Common Mistakes Made When Utilizing MDR Service
Despite the challenges, there are many organizations that have successfully implemented an MDR service within their enterprise.
However, there are also some that have not been as successful. Here are some of the most common mistakes made when utilizing an MDR service:
Not Defining the Scope of the Service
One of the most common mistakes is not defining the scope of the service. This can lead to confusion and frustration on both sides. Be sure to clearly define what is included in the service and what is not.
There's also the potential for overlap between the MDR service and your existing security tools and services. To avoid this, be sure to map out all of your current security tools and services before signing up for an MDR service.
Failing to Test & Evaluate
Another mistake is failing to test and evaluate the MDR service before signing a contract. This is a critical step in determining whether or not the service is right for your organization.
Also, be sure to ask the provider for references and case studies. This will give you a sense of their experience and expertise.
Not Incorporating into Existing Tools & Processes
Another mistake is not incorporating the MDR service into your existing security tools and processes. This can lead to duplication of effort and wasted time and money.
Besides that, not having a clear plan on how to use the data and information provided by MDR services can also lead to problems.
Not Monitoring & Managing the Service
Once you have implemented an MDR service, it is important to monitor and manage it on an ongoing basis. This includes ensuring that the service is meeting your expectations and that it is up to date with the latest threat intelligence.
Not to mention, you also need to have a clear understanding of your organization's goals and objectives. Without this, it will be difficult to determine whether or not the MDR service is a good fit for false positives.
Failing to Communicate
Finally, one of the most common mistakes is failing to communicate with all stakeholders. Be sure to keep everyone in the loop regarding the status of the project and any changes that are made.
In addition, it is important to have a clear and concise communication plan in place before implementing MDR solutions. This will ensure that everyone is on the same page and that there are no surprises.
MDR Service Done Right
Despite the challenges, there are many benefits to using an MDR service. When done right, an MDR service can help you protect your organization from advanced threats.
Be sure to define the scope of the service, test and evaluate it before signing a contract, and monitor and manage it on an ongoing basis.
By doing these things, you can ensure that your MDR service is helping you meet your MDR security operations center. If you're interested in eliminating cyber threats via MDR, get in touch with us and we will help you achieve this.
