Protecting Yourself from the Most Common Ransomware Attacks

 By
Jason Miller
·
7 minute read
By
Jason Miller
·
7 minute read
Despite the efforts of law enforcement, ransomware is thriving. It was the top cybersecurity issue for businesses in 2021, accounting for 21% of all cyberattacks. While that percentage was down 2% from 2020, largely due to law enforcement successes, the Verizon 2022 Data Report Investigation revealed a 13% increase in 2022. This year-over-year increase is as big as the last 5 years combined, and likely represents the ability of ransomware groups to disband and reformulate to stay hidden from law enforcement.
Ransomware is not a high-level problem restricted to large conglomerates and Fortune 500 companies. The attacks target companies of all sizes within virtually every industry. Assuming your business is too small or unimportant for an attack is equivalent to burying your head in the sand to avoid a tornado. So, what can you do to protect your organization from ransomware?
By learning about ransomware, how it works, and the ways you can prevent infiltration, you can develop a cybersecurity plan to assess your individual risks.
What is Ransomware?
The US Cybersecurity and Infrastructure Security Agency (CISA) defines ransomware as "an ever-evolving form of malware designed to encrypt files on a device, rendering any files and systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption".
In other words, ransomware is the tool used in an attack that prevents an organization or individual from using their own files or systems until they pay for the information or devices to be unlocked. What the definition doesn't reveal, is that payment often doesn't yield success, and even if it does, it can lead to another attack in the future.
Ransomware is designed to cause expensive downtime that will prompt organizations to pay quickly. It often also takes advantage of other techniques to increase urgency, including payment deadlines and threats to leak sensitive information. Many types of ransomware are designed to spread through a network. For this reason, organizations may be required to shut down systems to avoid further damage. Unfortunately, these actions can add to the costs of downtime, encouraging businesses to pay up to get back on track. The situation becomes even more urgent when attacks are launched on critical infrastructures like utility companies or healthcare facilities.
Most Common Types of Ransomware Attacks
All types of ransomware seek to extort money from organizations or individuals to access files, devices, or entire networks. However, different attacks use different methods to obtain and secure the information within your network. These are the most commonly used types of ransomware attacks.
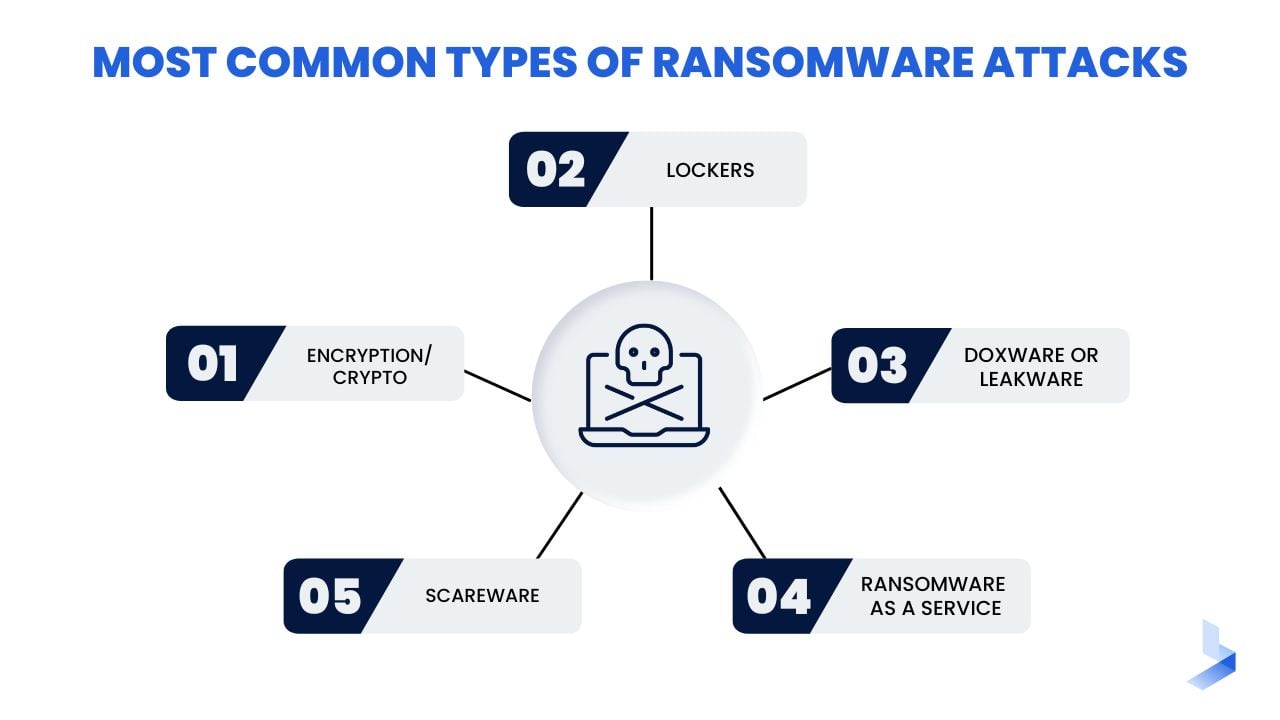
- Encryption/Crypto Ransomware: One of the most well-known and commonly used, crypto-ransomware encrypts files and data within a system, making the content inaccessible without a decryption key.
- Lockers: Screen lockers deny access to the system so users can't reach the information and systems needed to run the organization. Affected devices typically display a lock screen that displays the ransomware demand. Sometimes, a countdown clock is added for urgency.
- Doxware or Leakware: This type of attack may be combined with another ransomware type, like encryption, or used alone. It threatens to distribute sensitive personal or company information online. A typical attack includes the threat of leaking customer data.
- Ransomware as a Service (RaaS): Often distributed on the dark web, RaaS describes malware hosted anonymously by a professional hacker or ransomware group that handles all aspects of the attack. RaaS lets users launch attacks without any cybersecurity knowledge and has led to an increase in ransomware attacks as a result.
- Scareware: Often utilizing pop-ups, scareware is fake software that claims to have detected a virus or other issue on your computer and directs you to pay to resolve the problem. Some types of scareware lock users out of the device while others simply flood the system with pop-ups.
How Does Ransomware Work?
Most ransomware attacks begin long before a ransom is demanded. To implant ransomware in a network, attackers must gain access to distribute the malware. The top two vectors for ransomware are phishing and unpatched vulnerabilities. In some cases, attackers exploit unpatched vulnerabilities to gain access to a network and launch ransomware. In others, legitimate users are targeted with phishing emails that include links or downloads. The most effective emails appear to come from within the company or from a company the user is already acquainted with.
Once the ransomware is deployed, the information within the system is encrypted so it cannot be used. Upon encryption, users are typically notified on a lock screen that the information is inaccessible and a ransom is required. The notice will include the amount required, and instructions to purchase a specific type of cryptocurrency to pay the ransom. Often, a deadline is included, and a countdown clock may be displayed on the lock screen.
Ransomware Prevention Tips
By the time a victim receives a ransom notice, the attacker has already reached their objective. Unfortunately, this is often the first sign the organization is under attack. Like many situations, in the presence of ransomware, an ounce of prevention is worth a pound of cure. There are many steps organizations can take to avoid falling victim to ransomware.
Keep Devices and Software Updated
Organizations that develop computer systems and software work tirelessly to identify vulnerabilities and flaws in the system. When such issues are discovered, patches and updates are quickly implemented to repair the vulnerability. Unfortunately, users often delay using available patches and updates. Hackers seek system flaws that are likely to occur across multiple networks and find ways to exploit them as a means of entry into a network. Installing patches and updates as soon as they're available can help you avoid vulnerabilities.
Educate All Network Users
According to Verizon's 2022 Data Breach Investigations Report, 82% of breaches involve a human element. Modern phishing attacks aren't easy to spot. They often exploit stolen credentials and masquerade as business transactions. While phishing is one of the most common attack vectors, it isn't the only one. By educating all employees within an organization about potential attacks as well as good cybersecurity hygiene, you can eliminate the most common entry point for ransomware.
Utilize Multi-factor Authentication
The use of stolen credentials is a common way for hackers to advance through a network to successfully deploy ransomware. Multi-factor authentication (MFA) is simply a requirement for users to enter two forms of identification to access the network or important files. When a single credential is compromised MFA can provide an additional barrier to prevent an attack on your network.
Use Strong Cybersecurity Tools
Every device and piece of infrastructure within your organizational network should be protected with comprehensive security software. Beyond simply putting cybersecurity tools in place, make sure you're getting the most out of your security package by changing default settings and utilizing enhanced features for higher levels of security.
Develop and Enforce Strict Cybersecurity Policies
It's not enough for individuals to know the dangers of existing cyber threats. Organizational policies should integrate cybersecurity into all tasks. Your organization should have policies for password requirements, downloading attachments and using links, sharing information, and using email.
| Related Reading: Ransomware TTPs: Our Best Tips for Detection and Response |
Detecting Ransomware with Advanced Monitoring
Preventing ransomware is your best form of protection. Unfortunately, it's not always possible. Even with the strongest security measures in place, certain unexpected events could allow hackers to breach your system. Ransomware is delivered in a variety of different ways. If you can detect suspicious activity before ransomware is deployed, it's possible to stop hackers before they reach their objective.
We mentioned that ransomware attacks frequently begin with a phishing email or exploitation of a system vulnerability. For various reasons, the window between the breach of a network and the launch of a ransomware attack can range from minutes to months. During this window, hackers may lie low to avoid detection or work to advance permissions to gain authority and launch a more devastating attack. Referred to as LOTL (living off the land) attacks, these attacks typically masquerade as legitimate activity and can go undetected for months.

Network monitoring tools collect data surrounding all of the activities that take place within your network. The data is then categorized and normalized to provide important information about the events that take place in your network. With the assistance of machine learning (ML), these tools can establish a baseline to define the normal behavior of network users. When legitimate users participate in activities that fall outside of the normal baseline, the system triggers alerts.
How is this important in the fight against ransomware?
Many ransomware attacks utilize stolen credentials or email compromise to masquerade as legitimate users within a network. This makes attackers more difficult to detect. When your organization uses advanced monitoring tools to recognize unusual behavior, it puts professionals in a position to quarantine affected devices or take other measures to halt an attack in its tracks.
From Detection to Response: Ransomware Response Tactics
Alongside taking preventative measures, it's essential to have a ransomware response plan in place. Your plan should include tactics that help you protect your network if an attack occurs. To minimize potential damage from attacks, it's essential to back up important data and segment network systems so you can contain an attack if it occurs.
The way an organization responds to a ransomware attack can significantly minimize damage to your network. Use these tips to limit damage when your network is the target of a ransomware attack.
Don't Pay the Ransom
All security and law enforcement agencies are in agreement on this point. While your first instinct may be to pay up, there are reasons why it's not a foolproof idea. First, there's no proof the attacker will provide an encryption key. Even if you pay the ransom and all is well, paying can set a dangerous precedent. Your organization may be targeted a second time by the same criminals or another attacker. Yet, according to research, 65% of people pay the ransom after being hit with a ransomware attack. Sometimes, healthcare facilities and utility companies may be forced to pay for the quickest resolution possible, which is one reason the percentage of payments is so high.

Quarantine the Damage
Once you determine an attack is in progress, it's time to take action. By containing the damage, you can limit the damage caused by an attack. This is accomplished by isolating affected systems. When the rest of the network is no longer connected to the infected systems, operations can continue while the recovery team addresses the attack.
Perform Legal Obligations
Depending on your industry, you might have certain obligations in the event of a cyberattack. This may include informing customers or reporting the attack to law enforcement. Even if your organization is not legally obligated to disclose ransomware attacks, you should consider the potential dangers of hiding the event.
Recover Data and Restore Systems
Once the attack is contained, response actions include restoring systems to return your network to normal. If you've followed the 3-2-1 best practice of backups, you can restore the network to the "last known good version." During the restoration process, the IT team should take precautions to make sure any necessary patches and updates are applied.
Perform Post-mortem Analysis
Download a Free Incident Postmortem Template
After the storm, it's important to stand back and inspect the damage to understand what happened. Your incident response team should analyze data to determine how the network was breached, the TTP used by the attacker to carry out the attack, potential motives for the attack, and areas where your incident response process fell short. The information from this analysis can be used to reduce vulnerabilities and strengthen your organizational cybersecurity posture.
Network Level Protection from Ransomware
Ransomware isn't going anywhere. As technology changes and grows, hackers will find new ways to exploit vulnerabilities to extort money from businesses. That's why businesses need ransomware protection designed to protect their organizational network from end-to-end with tools and strategies that prevent attacks, detect intrusions, halt attacks in progress, and mitigate damage from attacks.
BitLyft AIR is an automated threat detection and remediation platform that combines multiple security offerings into one single solution. The platform includes comprehensive network monitoring, automated responses to threats and incidents, crowd-sourced immunization through central threat intelligence, and the assistance of an off-site SOC. We provide organizations with a complete end-to-end solution for your extended detection and response protection plan at a fraction of the cost of an in-house team. Request a demo to learn more about how we can help you protect your organization from all types of ransomware.

