What Are LOTL Attacks? All You Need to Know About Living Off the Land

 By
Emily Miller
·
11 minute read
By
Emily Miller
·
11 minute read
Cybersecurity incidents are endemic in today's digital business world. 2021 set new records for data breaches, with over 18.5 million records exposed in the span of 12 months.
Cybersecurity incidents like data breaches can have devastating consequences for a digital business. The average cost for a data breach is $4.24 million. These costs are often passed on to the customers, making a business less competitive.
.jpg?width=735&height=272&name=Average%20Cost%20of%20a%20Data%20Breach%20(1).jpg)
Clearly, digital business owners need to do everything in their power to ensure their websites, apps, and digital assets are as safe and as secure as possible.
Which brings us to LOTL attacks.
Today, we're going to take a deep dive into LOTL attacks. We're going to answer the question "What are LOTL attacks?", discuss some of the risks they pose to you and your company, and take a look at some ways you can prevent malicious actors from impacting your cloud services and operating system.
What Are LOTL Attacks?
The 2020 Cyber Threatscape Report revealed a disturbing trend. Cybersecurity professionals detected a marked increase in every kind of cybercrime at the beginning of the pandemic. Even more disturbing, these analysts detected a noticeable rise of LOTL attacks from cybercriminals backed by national governments alongside independent agents.
These threats are called living off the land attacks LOTL. LOTL is when cybercriminals use legitimate admin tools in order to compromise a network without setting off any major alarms. It often begins with a hacker gaining access to a network through another technique, such as phishing, which has been seeing a precipitous rise in recent years.

One of the things that make LOTL attacks unique is that they don't leave any files behind. This is why they're sometimes called fileless malware. When there are no executable files or malware to detect, many cybersecurity suites simply won't realize that anything suspicious has taken place.
Common Types Of LOTL Attacks
This doesn't mean that LOTL attacks don't pose any threats to your network security, though. Instead of malware and executables, though, living off the land attacks leave behind dangerous PowerShell scripts or exploitative code that cybercriminals can take advantage of after the fact.
PowerShell scripts are by far the most common type of LOTL attack against Windows-based machines. Linux-based systems are vulnerable to malicious files written in PHP, though.
LOTL attacks can even make use of seemingly innocuous commands like WGET. These can be used to launch a suite of attacks, none of which leave suspicious files behind.
LOTL attacks can lie dormant for a long time, which is one of their major risks. Once a hacker's gained entry to your system or network, there's no rush for them to reveal their presence.
In fact, it's often to their benefit to leave compromised systems alone for as long as possible. If a compromised system isn't detected within a month, it's a good sign they have the keys to the kingdom.
LOTL attacks can live very nearly anywhere. They can be a chunk of code on your RAM that turns out to be malicious actors, for example. They can even reside at an endpoint, just waiting for a chance to do their damage.
Why Cybercriminals Live Off The Land
Modern cybersecurity solutions have gotten incredibly sophisticated. Rudimentary security solutions like antivirus software are constantly syncing with a database with the latest information about known malware and threats.
More advanced cybersecurity like SIEM use even more cutting-edge tools to deter hackers. They employ an impressive array of machine learning and AI to build complex models of both your users and network.
This means cybercriminals and unauthorized users need to figure out other ways to penetrate your system. This is the main reason for the rise of LOTL attacks, as they're much less likely to set off warning sensors.
This is one reason LOTL attacks are so effective. A recent report found fileless attacks to be around ten times more successful than malware.
Many security operations centers (SOC) sensors won't be set off tools employed by LOTL attacks. If LOTL attacks do install malware, it won't be until far later. By then it might be entirely too late.
By that point, the hacker might install ransomware and lock you out of your network. That's a good example of why you need to be on guard against LOTL attacks. The fact that many of these groups may be backed by official governments is another giveaway, as they might be using some of the most sophisticated tools available to perpetrate their crimes.
Why Have LOTL Attacks Become So Popular?
It's been said that the best way to predict future behavior is by looking at the past. A cybersecurity report from 2019 found that around 40% of cyberattacks occur using official tools and features.
The fact that LOTL attacks are becoming so prevalent means that they're also developing a reputation. This means there are starting to be an increasing number of LOTL TTP tools out there. These include everything from MetaSploit to PowerSploit to Exploit Pack.
Many widely available malware tools and packs come bundled with LOTL attacking software, as well.
Originally, most LOTL attacks exploited existing admin tools like PowerShell, Windows Management Instrumentation (WMI), CMD, or Psxec.exe. These tools let unauthorized users monitor what happens inside of your network. It also gives them lateral access to other parts of your system.
Despite the fact that LOTL attacks are so popular and prevalent, they're still notoriously hard to track by IT teams and cybersecurity professionals.
How LOTL Attacks Work
LOTL attacks are nothing new. There are vulnerabilities in every major operating system that leave them open to LOTL attacks. Still, somehow, cybersecurity teams never manage to fully close the gaps.
These are a few examples of LOTL attacks that Windows is especially vulnerable to.
Dual Use Tools
Dual use tools are the most common vulnerability exploited by cybercriminals to gain unauthorized access to a network. Dual use tools are legitimate admin tools, such as a resource that enables remote access, for example.
This allows threat actors to avoid detection from system admins and IT professionals.
FTP clients are a good example of a tool with official applications that can be exploited for malicious purposes.
PsExec is one of these tools. It's an internal tool from Microsoft that is used to run software on other systems.
Dual use tools can give hackers access to your network, run commands, or steal data. They can even be used to download malware or other programs, which could give them even greater access to your system.
Fileless Persistence
Fileless persistence is a kind of LOTL attack where a corrupted asset can remain on a network after a reboot, despite nothing having been installed. These vulnerabilities are known as fileless malware. It's often achieved by harmful scripts being stored on the Windows Registry, like changes to the Visual Basic Scripting (VBS).
Memory-Only Threats
These harmful assets are executed straight from a system's memory. This form has been well-established for some time. It's one of the longest-running types of cyberattacks that still works today.
In 2001, the malware Code-Rode raged through the rapidly expanding internet. The Code-Red worm exploited a vulnerability in the Microsoft IIS webserver.
Memory-only LOTL attacks can be installed and run directly onto a system's memory. Although they're easily fixed, usually only requiring the system to be restarted, that network remains at risk until a security patch is put into place.
Non-Portable Executable (PE) File Attacks
Some libraries themselves are vulnerable to exploitation. Non-Portable Executable (PE) files can infect libraries and tools like JavaScript or PowerShell without installing an .exe file, dynamic-link library (DLL) files, or even .doc files thanks to macros and scripts.
These infections mean that otherwise official tools can carry and spread infection.
How to Prevent LOTL Attacks
Now let's take a look at some different ways you can protect your network against LOTL attacks. These tips should help get you thinking as both a hacker and an IT professional, helping you to protect your system in as many ways as possible.
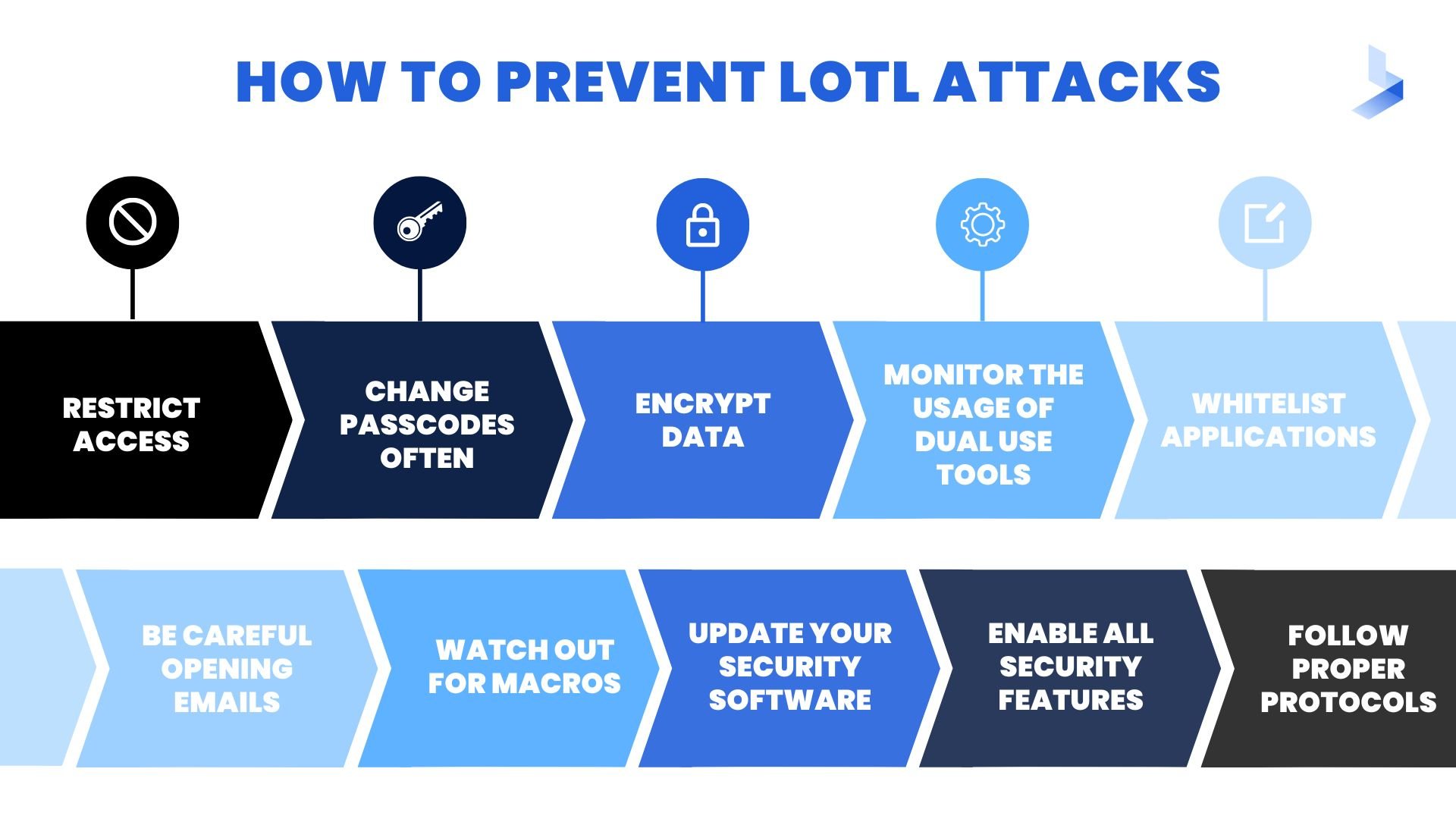
- Restrict Access
- Change Passcodes Often
- Encrypt Data
- Monitor the Usage of Dual Use Tools
- Whitelist Applications
- Be Careful Opening Emails
- Watch Out for Macros
- Update Your Security Software
- Enable All Security Features
- Follow Proper Protocols
- Search-and-Filter
Restrict Access
The first, most obvious, and most direct way to make sure LOTL attacks don't take your network offline is to make sure that no one can access everything. There are numerous ways you can restrict access throughout your network to prevent thieves from getting the keys to the kingdom.
Two-factor authentication should be installed throughout your system. This includes endpoints, devices, cloud servers, and even VPNs. Credential authorization is another useful way to note only authorize users but also keep track of their actions.
You can also put firewalls in place throughout your network. You might set a firewall to alert a SIEM system that someone is trying to access your root kernel, for instance. Attempts to modify the Windows registry are also often placed behind a firewall.
Change Passcodes Often
Lost or compromised passwords are another common source of LOTL attacks. This could be anything from a login to an API key to any number of other authorizations giving someone access to your network.
If you want to ensure your network is safe and secure, first of all it's vital you keep track of all login credentials when they're issued. If at all possible, you should keep track of passwords that may have been lost or compromised, as well, if you have any way to track that.
Either way, it's a good idea to change your entire network's login data regularly so as to ensure information security. How regularly is up to you and your team but at least a few times a year is a safe bet, if you want to make sure your network is secure.
Once you decide on a schedule, you can even set up a system to automate the changes. That way it will never be overlooked or neglected.
Encrypt Data
Inside your system, it's vital that you the data exchange between your tools and system functions is encrypted and secure. This way, a hacker won't be able to do much damage if they do gain access to your system.
Hackers can even sometimes exploit official tools like certification management programs. The Windows program CertUtil has even been exploited by cybercriminals, who then make the program download malicious scripts and compromised certificates.
Monitor The Usage of Dual Use Tools
It's important to note which tools on your system could potentially be putting you at risk. It's even more important to know what those tools are doing, so you can spot any suspicious behavior should something happen to come up.
To use our previous CertUtil example, you might keep an eye out for suspicious traffic. If you notice CertUtil.exe downloading 16GB of data, that should raise some warning bells. That would be a lot of certificates.
You might integrate these activities into a SIEM workflow, even, to keep a closer eye on any potential security risks. SIEM uses modern tools like machine learning to build robust models for software and users alike.
This way, the second a program starts acting strange it's recorded in the data log and your IT team is alerted immediately.
Whitelist Applications
It's better to exercise too much caution than not enough. If you really want to make sure your network is secure, you might limit the access of virtually every program. Then you can use whitelisting judicially to allow access as needed.
This method has a few different benefits. Whitelisting is it gives you greater control over each individual user and what they have access to, which is its major benefit.
Be Careful Opening Emails
Phishing is how a lot of hackers get access to a network in the first place. It's vitally important your entire team knows to be careful when opening emails from unknown or unusual sources.
Opening an email and following one single CTA could put you, your organization, your users, and all of their data at risk. It can be a very costly, and even dangerous, mistake.
Phishing emails are another great reason why you should really consider having a SIEM system in place. SIEM can create detailed behavior analytics for each user throughout your enterprise. This data model can include details about what websites they visit and who they get emails from.
This way, even if a phishing email doesn't set off any antivirus sirens, it might still get picked up by the SIEM.
Watch Out For Macros
.Doc files aren't the only type of file that are at risk for suspicious scripts and macros. You want to watch out for Microsoft Office documents asking you to enable macros, as well, as these can be used to trigger harmful scripts.
Update Your Security Software
Cybercriminals never sleep. As soon as there's a new piece of software or update, they're hard at work reverse-engineering it to exploit it for any vulnerabilities.
That's why it's important to keep all of your cybersecurity tools up to date. Most modern cybersecurity receive updates with all of the latest malware and viruses. Regularly connecting to these servers will ensure your network is secure from any and all risks, as soon as they arise.
This is yet another strong selling point for SIEM. SIEM solutions can often pick up on security threats before they're known threats. It employs sophisticated tools like pattern recognition to compare behavior against other known security risks and threats.
This prevents your network from getting infected by a brand new virus that hasn't made its way into the latest database yet.
It also means you don't have to worry about updating your antivirus manually. SIEM updates itself, continually, so there's no risk of a major upgrade getting overlooked.
Enable All Security Features
Your network can never be too secure. It's in your best interest to enable as many advanced security features as possible if you're serious about network security. At the very least, it keeps you alerted to what's happening inside your network so you can react accordingly.
Most modern systems have built-in two-factor authentication. This is wise to enable, as it lets you know not only who's in your system but also what they're doing. If your network doesn't have advanced two-factor authentication, there are all manner of available tools that you can use simply by inserting a widget or a few lines of code.
Login notifications are another common security feature found in most modern networks. This alerts you and your IT team anytime someone logs onto the network. Just as importantly, it can be set up to log that login data so you have a record of who's accessing your network and what they're doing.
These data logs can be invaluable for troubleshooting in the wake of a data breach. It can create robust user behavior models that can help prevent your system from getting exploited it the future.
Follow Proper Protocols
You know how the accepted security wisdom is to never save passwords or stayed logged in on a shared computer? If you want to prevent LOTL attacks, you should assume that every computer is a shared computer.
Which is to say that you should always be following the latest best practices around making sure your network remains secure. To start, that means you and every member of your team needs to log out of the system as soon as they're finished using it - every single time.
All it takes is one computer accidentally left logged in for a cybercriminal to install some sort of trojan horse or leave themselves a backdoor to enter your network at a later date.
It also means you and your team need to follow the guidelines around creating strong passwords. There can't be any birthdates, no pet names, no 'passwords'. All passwords need to contain a combination of capital and lowercase letters, numbers, and symbols.
Search-and-Filter
If you've got a SIEM solution in place, following a search-and-filter approach to cybersecurity can offer some extra security for your system.
First, you'll need a list of all known threats that could negatively impact your network. This is why it's a good idea to follow this approach as part of a SIEM system. SIEM systems are constantly being updated, so they'll have a list of all of the threats that could infect your network.
Once you have that list, the SIEM system will start to scan your system for all known threats. It will also browse for known dual-use tools, suspicious looking scripts and macros, and unusual software behavior.
At first, these searches will turn up lots of users with admin privileges. That's because many of these tools have official applications, which is why they're used for LOTL attacks. Add these users to the filter column and continue on with your sweep.
Once you've got a list of users complete, create some groupings so you can monitor user behavior. You might notice one user group that's consuming a lot of data, for instance. These user groups warrant further investigation.
This is also an important step in creating a baseline of user model behavior.
The data itself can also be used to illustrate useful baselines. Your SIEM might use this data as a baseline for standard data usage, for example. This model can then be used to create an alert when there's a spike in data usage or similar unusual behavior.
Living Off The Land Attacks: Final Thoughts
We're only going to keep seeing more LOTL attacks as the years tick on. Cybercriminals will continue to find and exploit vulnerabilities wherever they can. This makes LOTL attacks particularly appealing as they're actual, verified tools that are less likely to set off alarms for malware.
Detecting LOTL attacks requires a bit of creativity as well as some technological savvy. It's in your best interest to make sure your network is secure against LOTL attacks, though, so you can rest assured that absolutely nothing can derail your network.
Are You Looking For Next-Gen Cybersecurity?
Cybercriminals never sleep! As soon as a new product or update is released, hackers are hard at work reverse-engineering it in search of vulnerabilities.
You need high tech security if you want to stay safe in today's business world. If you're ready to find out how next generation cybersecurity can protect you against high tech threats like LOTL attacks, get started today!
