Busted! 5 Misconceptions that Make SMBs Vulnerable to Cyber Attacks

 By
Emily Miller
·
9 minute read
By
Emily Miller
·
9 minute read
Modern business moves faster than ever before with an interconnected environment that breaks down location barriers, streamlines supply processes, and connects businesses of all sizes with consumers across many platforms. Yet this interconnected business environment also exposes businesses to new risks in the form of cyberattacks from sophisticated hackers. National headlines about major attacks on oil supply lines, food supply chains, and leading companies make it clear that no industry is immune to attack. However, many companies still mistakenly believe their business isn't an attractive target for cybercriminals.
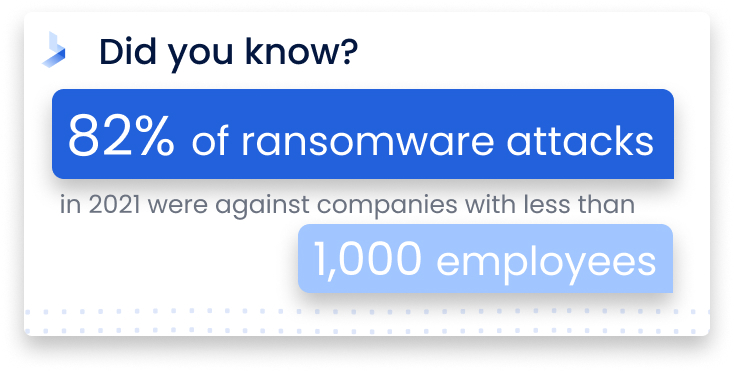
The truth is, the size of your business doesn't make you immune to cyberattacks. In fact, it might even make your business even more vulnerable. Sixty percent of small to medium businesses (SMBs) experienced at least one attack in the last year, and 18% have experienced six or more. Still, 44% of respondents indicated that they don't have a comprehensive and updated cybersecurity plan in place. While the frequency of attacks is rising, businesses aren't strengthening their cybersecurity defenses. As a result, SMBs make highly attractive targets for continued cyberattacks. Eighty-two percent of ransomware attacks in 2021 were against companies with fewer than 1,000 employees, and 37% of companies hit by ransomware had fewer than 100 employees. What's more, employees of small businesses experience an astounding 350% more social engineering attacks than those at larger enterprises.
 Still, many business owners mistakenly believe that their small to medium business isn't an attractive target for attackers. As smaller businesses struggle in an uncertain economy, the situation could become more threatening. Limited knowledge and accepted myths often lead small business owners to think that cybersecurity is a luxury they can't afford. This article addresses common misconceptions about cybersecurity for SMBs. We'll explore five common myths and share compelling evidence about how these misconceptions leave SMBs even more vulnerable to attacks than their larger counterparts.
Still, many business owners mistakenly believe that their small to medium business isn't an attractive target for attackers. As smaller businesses struggle in an uncertain economy, the situation could become more threatening. Limited knowledge and accepted myths often lead small business owners to think that cybersecurity is a luxury they can't afford. This article addresses common misconceptions about cybersecurity for SMBs. We'll explore five common myths and share compelling evidence about how these misconceptions leave SMBs even more vulnerable to attacks than their larger counterparts.
Misconception 1: SMBs Aren't Attractive Targets for Cybercriminals
Many business owners believe that their business is too small to be an attractive target for cybercriminals. The truth is, all businesses have valuable data that can be used for ransom demands or sold on the black market. Since small businesses don't have the resources that large corporations do, cyberattacks are more likely to be successful. As a result, attacks on small businesses can be more lucrative than those on large enterprises. Hackers can find ways to access valuable company information or customer data. No matter the size of your business, this data can be valuable leverage for a ransomware attack or sold on the dark web.
Examples of Cyber Attacks on SMBs
All cyberattacks come with serious consequences, but small businesses are likely to be more heavily impacted by an attack than larger companies. Small and medium businesses have fewer resources and smaller budgets. As a result, they're more vulnerable to attacks and any loss is a major financial blow. The average data breach cost for businesses with fewer than 500 employees is $298 million, and this figure doesn't even include indirect costs like downtime, decreased morale, and reputational damage. Such losses can cause catastrophic damage to small businesses, forcing many to close their doors.
Consider the devastating impact of these examples.
An attack on Efficient Escrow of California began with a form of "Trojan horse" malware that allowed thieves to gain access to the company's data. Once the hackers were in, they wired $432,215 from the firm's bank to an account in Moscow. The transfer was followed by 2 additional transfers, totaling $1.1 million. Unable to replace the funds, the company was forced to shut down just 3 days after reporting the loss.
Green Ford Sales, a car dealership in Kansas, lost $23,000 when hackers broke into their network and swiped bank account info. They added 9 fake employees to the payroll in less than 24 hours and paid them a total of $63,000 before the company caught on. Only some of the transfers could be canceled in time.
5 Reasons SMBs Are Appealing Targets for Cyberattackers
New technology, an increase in remote work, and increased dependency on endpoints have rapidly expanded the threat landscape, giving hackers more entry points to exploit. While small to medium businesses may lead to smaller rewards, certain features make them especially attractive to cybercriminals.
- Small businesses are less likely to have the education and resources to recognize and stop an attack.
- Your business is likely connected to larger businesses through vendor and supply chain relations.
- SMBs can become victims of supply chain attacks even when they're not a direct target.
- Small businesses can't afford downtime and often feel they must pay ransoms to avoid additional losses.
- SMBs are more vulnerable to social engineering because of limited basic security tools.
Misconception 2: Budget Constraints Limit SMBs' Cybersecurity Capabilities
"We can't afford to spend more money on cybersecurity." Small to medium businesses are often forced to cut costs wherever possible. When you're working on a shoestring budget, cybersecurity can seem like a luxury you can't afford. The truth is, even a small breach will cost you significantly more than an effective cybersecurity solution. Modern cybersecurity options for businesses have evolved to include remote and hybrid solutions that offer customized protection at an affordable price.
The Cost of Cybersecurity vs the Cost of a Breach
Effective cybersecurity comes from a variety of sources, including best practices and off-site support. The overall cost of a data breach also comes from several sources, some of which are difficult to put a price on. Direct and hidden costs of a data breach range from ransom demands and compromised data to incident response and reputational damage. Regulatory fines and legal costs often have a major impact as well. We've noted that the average cost of a breach for SMBs is nearly $3 million. It's not an expense that most businesses can afford to cover.
Cybersecurity costs vary depending on your organizational needs. However, all of the efforts you apply have one thing in common. They offer an impressive and long-term ROI. For example, in the event of a data breach, organizations using security automation save an average of $3 million compared to those without. Once these services are implemented, they scale with business growth and the introduction of new devices and endpoints. Employee education is another investment that pays off. Your employers are the first line of defense between hackers and your network. By educating your employees and implementing and enforcing best security practices, you can build a culture of security that protects your network against known and evolving threats. While you may think you can't afford to invest in cybersecurity, the truth is, you can't afford not to.
Cost Effective Cybersecurity Options for SMBs
It's true that developing an on-site security operations center (SOC) is not within the financial reach of most SMBs. Luckily, most growing businesses will benefit more from outsourced cybersecurity services along with other cost-effective options. By combining best practices with powerful tools, you can create an effective defense without breaking your budget. For example, these small investments will have a major impact on your cybersecurity posture.
- Cybersecurity training for employees: In-house or outsourced training is relatively inexpensive and can teach employees how to recognize suspicious behavior and common attacks.
- Company policies and procedures that follow best practices: Implementing policies like multi-factor identification, strong password usage, and safe data sharing practices will improve your overall cybersecurity posture.
- Threat intelligence: Cyber threat intelligence can be derived from a variety of sources that are publicly available like cybersecurity blogs, news reports, public block lists, or from private commercial sources provided by cybersecurity vendors. This data protects your network against known threats.
Misconception 3: Existing Security Measures are Sufficient for SMBs
Many business owners are comfortable with the use of basic security tools and assume they provide adequate protection. While tools like antivirus and firewalls provide valuable perimeter defense features, they're not enough to protect your network against some of the most common modern attacks. Modern businesses need a comprehensive security strategy, including firewalls, 24/7 log monitoring, encryption, and patch management.
How Modern Attacks Circumvent Basic Tools
Basic cybersecurity tools defend your network perimeter similar to the way your locked doors and windows protect your home. However, today's threat landscape thrives on deceptive attacks that ask for permission to enter and masquerade as legitimate network traffic once they get inside. It only takes one successful phishing email to get past basic cybersecurity tools.
Advanced security solutions can be tailored for SMBs. They're designed to pick up where basic tools leave off to alert to attacks inside your network, protect cloud-based assets, and defend your network around the clock. For example, endpoint protection eliminates vulnerabilities presented by remote devices and other endpoints connected to your network. Intrusion detection recognizes suspicious behavior and internal threats to allow you to detect an intruder before damage occurs. Managed detection and response (MDR) is the most comprehensive cybersecurity solution, providing your business with advanced tools and assistance from an off-site team of experienced cybersecurity professionals.
Selecting the Most Suitable Cybersecurity Solution for Your SMB
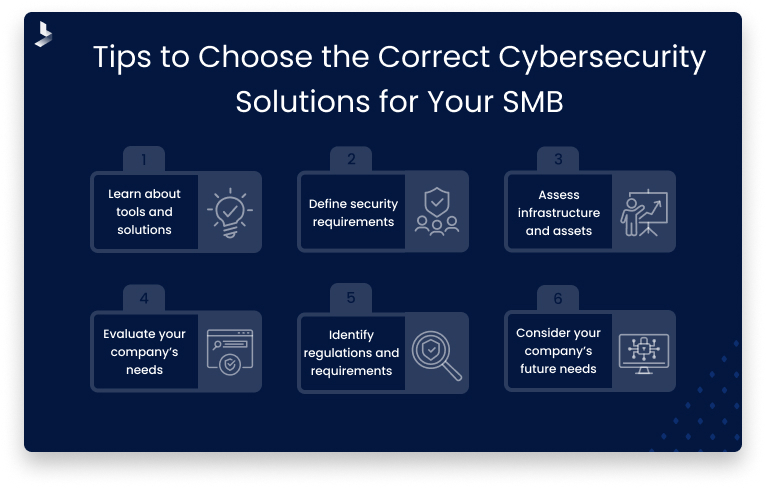
Finding a customizable cybersecurity solution can help you stay within your budget while getting the exact level of security you need. Take these steps to select the most suitable cybersecurity solution for your small or medium business.
- Learn about cybersecurity tools and solutions.
- Define your security requirements and what you hope to achieve with your cybersecurity investment.
- Assess your infrastructure and the assets you need to protect.
- Evaluate your personnel needs.
- Identify industry regulations and compliance requirements.
- Consider your future needs.
Misconception 4: SMB Data is Less Valuable to Cybercriminals
It's a common misconception that the data stored by large conglomerates and Fortune 500 companies has a higher value. The truth is, all data holds value for cybercriminals. Small and medium businesses store customer data like payment details and personal information, just like larger companies do. This data can be sold on the dark web to be used for identity theft or to access financial accounts. Sometimes, hackers steal data to use as extortion for ransom. Unfortunately, paying the ransom doesn't always mean the data won't be released. Data stolen from SMBs is used in the same way as date stolen from larger companies, and it's often easier to get.
Consequences of Data Breaches for SMBs
Data breaches have serious consequences for all businesses. Small businesses typically face steeper challenges during the recovery process. Wondering how data breaches affect SMBs? Damages may include:
- Direct financial losses: Cyberattacks result in direct costs like damages, ransom payments, free credit monitoring for customers, security consultants, public relations, etc.
- Reputational damage: Customers may be wary of conducting business with businesses that have been hit by attacks, and customers affected by a breach are likely to churn.
- Legal implications: Legal costs in the form of settlements and attorney fees are often higher than expected.
- Regulatory fines: Every business is responsible for providing reasonable protection for sensitive data. A breach can signify that your organization hasn't met industry regulations, resulting in non-compliance costs of fines, penalties, and lawsuits.
- Downtime: Even limited downtime can cost your business millions.
Implementing Robust Data Protection Strategies for Your SMB
It's virtually impossible to run a business without collecting and generating data. To protect customer and company data, businesses need safe practices for data storage and sharing. There are many steps you can take within your organization to adequately protect sensitive data.
- Protect data during both transmission and storage with encryption.
- Implement data loss prevention tools to monitor where data travels and block unauthorized data flows.
- Implement and enforce strong password policies and multi-factor authorization.
- Limit access to sensitive data as needed for job roles.
- Consider cloud-based security to protect your IT infrastructure against breaches.
Misconception 5: Reactive Cybersecurity Measures Suffice for SMBs
Many business leaders think that putting a cybersecurity plan in place prepares the company to deal with an attack. While a response plan is a good first step in the right direction, an untested plan can actually give you a false sense of security. Companies that depend on reactive cybersecurity only respond to an attack when damage has already occurred. In most cases, this means the attacker has already reached their goal, and you'll be facing significant costs to mitigate the damage.
The Costs of Delayed Response
Modern cyberattacks often take a "slow and low" approach that allows cybercriminals to spend more time within the network to gain higher levels of access and mine large amounts of data. The longer an attacker lingers within your system, the more effective their attack can become. The average time to detect and contain a breach is 277 days. Companies that can shorten the time to 200 days or less save an average of $1.12 million. The ability to detect a breach before damage occurs can mean avoiding ransom demands or data loss and keeping your organization's reputation intact.
Developing Proactive Cybersecurity
Reactive security describes the actions you'll take to mitigate damage caused by an attack. Proactive cybersecurity uses tools and tactics to identify suspicious behavior and stop an attack before any damage occurs. Cybersecurity tools that detect and respond to threats, use artificial intelligence and machine learning to identify suspicious behavior and send relevant alerts. These tools can even be programmed to take automatic response actions to mitigate the threat.
A proactive cybersecurity strategy requires:
- 24/7 log monitoring
- User and entity behavior analysis
- Automated alerts
- Incident response
- Endpoint protection
For most SMBs, managed detection and response (MDR) is the most cost-effective way to achieve proactive cybersecurity. A high-quality MDR solution provides your business with modern tools to detect threats and automatically respond to suspicious behavior and active attacks. Perhaps more importantly, MDR gives you access to the experience and education provided by a remote cybersecurity team. With limited start-up costs and professional implementation, even small businesses can quickly improve their cybersecurity posture.
Don't Wait for Your SMB to Become a Victim of a Cyber Attack
The idea that smaller businesses aren't likely to be targeted for a cyberattack is a myth that is likely to leave your organization vulnerable. While attacks on large businesses make headlines, it's often smaller businesses that end up closing their doors because of the damage caused by a cyberattack. Every company stores valuable data, and those with a false sense of security are most likely to suffer the consequences. The number of attacks targeting small businesses is continually rising. Don't let your business contribute to the rising percentage in the coming year.
Cybersecurity is an ongoing process, demanding constant vigilance and adaptation. If you're unsure about the safety of your organization's digital assets, we can help. Contact the cybersecurity professionals at BitLyft to learn more about customizable security designed to work with the needs and budgets of companies of all sizes.

