WHAT IS UEBA security?

 By
Jason Miller
·
4 minute read
By
Jason Miller
·
4 minute read
UEBA Security has become a key player in the world of data protection, and it presents several excellent benefits to IT professionals.
In this guide, we’ll take a deep dive into UEBA security and explain what it is, how it works, and why you’ll find it helpful.
What is UEBA security?
UEBA stands for User and Entity Behavior Analytics.
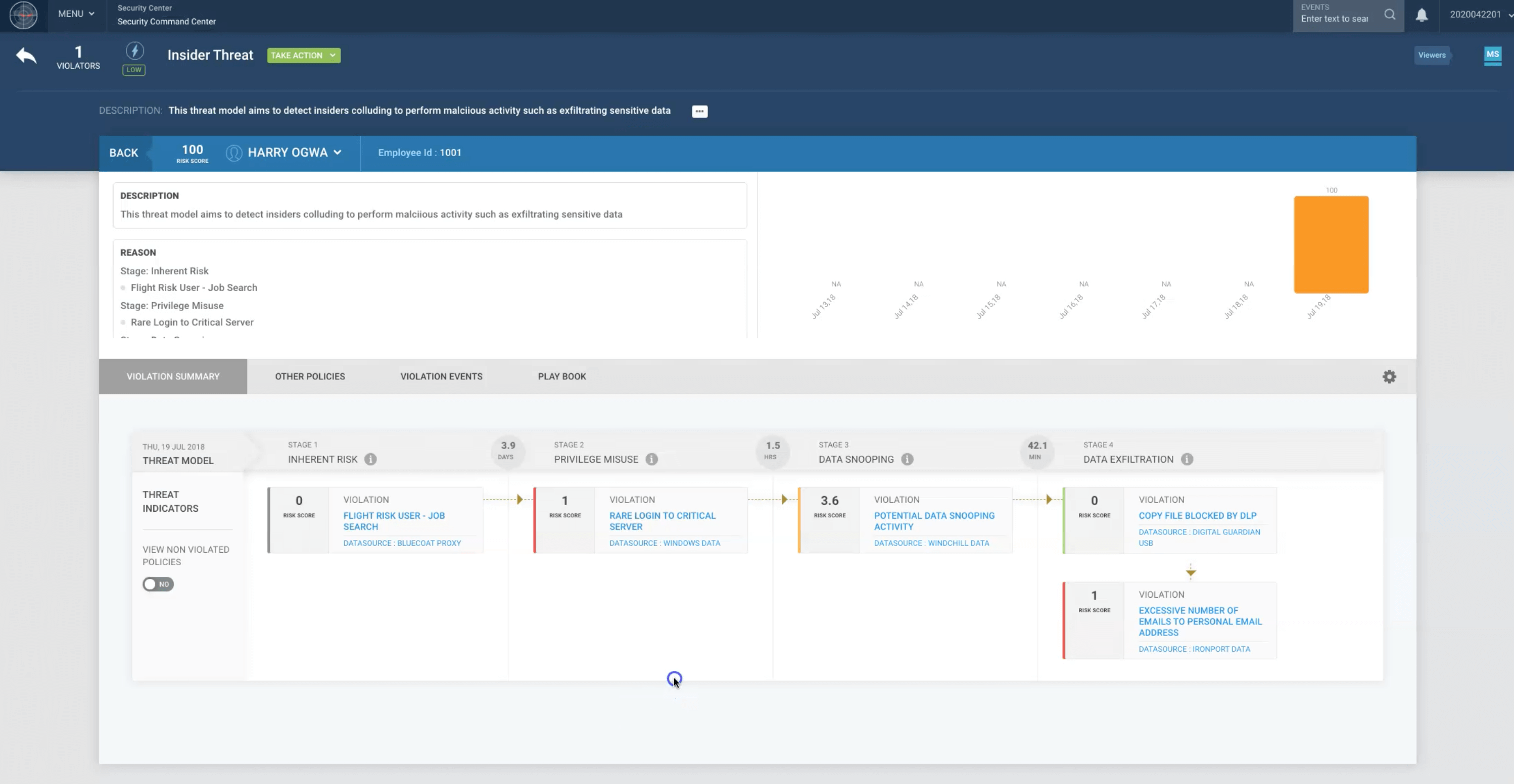
Primarily, it deals with the general behavior of the users on a system. The ‘normal’ or ‘standard’ conduct and practices are noted and used for the baseline of the analysis. When users step outside of their usual behavior, a UEBA security system detects this almost instantly.
Effectively, it helps pinpoint any anomalies in a system. For example, a user may only download a few megabytes worth of data every single day. This happens for months on end, and the file downloads remain at a relatively similar level. Then, one day, gigabytes of data are downloaded by one user. This isn’t normal behavior, so the system flags things up.
In a world where cybercriminals are developing new ways to hack into systems and breakthrough firewalls, UEBA security is a welcome addition to your arsenal against cyber threats. A lot of common security and data protection methods are no longer valid because hackers can bypass them. With UEBA, you can detect any users or things that could cause damage to your system.
Interestingly, UEBA isn’t a security measure that focuses on devices or events. It’s all about keeping tabs on the users that have access to your system. This makes it excellent at finding any insider threats from current or previous employees.
How does UEBA work?
UEBA security calls upon modern technologies like AI and machine learning. So many algorithms are run to help establish what a ‘normal’ pattern of behavior is. When this has been established, the UEBA system continues running algorithms and analyses on all the different behavioral patterns to ensure they keep aligning with what’s considered ‘normal.’ If someone’s behavior suddenly starts changing, then the system administrator is notified right away.
UEBA was born from the idea that anyone can find out your log-in details, but only you are capable of mimicking your own behavior.
So, let’s say that someone logs into your account because they figure out your email and password. Without UEBA, no threats are really detected – particularly if the user logs in from a similar location, such as the same office. It just seems like you’ve logged in, there were no failed attempts, it’s fine. However, the person who logged in won’t be able to act in the same way as you. They might do things that you’ve never done or interact with data or systems that you typically don’t interact with. With UEBA security, these bizarre behavioral patterns are identified, and an alert gets flagged up for your security team to see.
What can UEBA security help you detect?
By implementing UEBA security in your organization, you can detect the following things:
- Insider threats: Employees are often guilty of trying to steal company data and use it for personal gain or to sell for money. UEBA detects these threats because it knows what your employees are usually like. So, when someone starts behaving strangely, an alert is flagged up, and they can be investigated before the damage is done.
- Data protection breaches: UEBA tells you who has access to your most sensitive data. As such, you know when someone accesses it and whether or not they have the right clearance. If your data suddenly leaks to the public, then UEBA helps you identify who were the last people to access it.
- Compromised accounts: Any user account has the risk of being compromised and used for criminal activity, knowing who is in control of the account and making sure it is the rightful owner is truly important. Key indicators include source of login, geolocation, failed login attempts before success, and performing unusual behavior. With UEBA, you can see which accounts have been compromised and deal with them before they harm you.
- Permission changes/super users: A lot of attacks occur when someone creates a super user than has access to everything. Likewise, attacks are often down to permission changes that provide users with unwarranted access. UEBA detects any super users in the system and also alerts you to all the permission changes that happen.
- Forceful attacks: UEBA can also help detect forceful attacks from external hackers. If anyone tries to attack your cloud-based systems or authentication systems, then UEBA is alerted to this and flags it up.
What are the benefits of UEBA Security?
UEBA provides a different type of security that other systems. Firewalls prevent access, but they don’t track user habits. It only takes a second for an employee to unknowingly get redirected to a website, download malware or a virus onto your system. This can suddenly put everything at risk and makes it easy for hackers to breach. The fact is that there are so many complex cyber threats that you can’t rely on a traditional IT security setup alone.
With UEBA, you have something that detects threats as they happen. By focusing on user behavior instead of devices, you see when certain things change. You know when someone’s account is compromised because they’re suddenly behaving differently. You know when data is under threat because the permissions suddenly change and one user now has access when they never ever had it before.
If hackers do manage to get into your system and bypass your other security measures, then UEBA is there as the last line of defense. It identifies an anomaly in the network, sending signals to your security team so they can shut down the threat and prevent serious harm.
In conclusion, UEBA came about because of the bad and harmful behavior from users and entities on network systems. We strongly advised that you implement this security measure as part of your overall IT security strategy. Don’t replace things that are already in place, use UEBA to add a new level of security that adds even more protection.
BitLyft aims to provide you with a simple no-nonsense solution to keep your business safe from online threats. If you’d like to learn more, don’t hesitate to get in touch with us today to speak to one of our friendly representatives.
We’ll help explain the managed detection and response services we offer and how they can be customized to your exact needs.