Closing the Security Gaps in Financial Services

 By
Jason Miller
·
5 minute read
By
Jason Miller
·
5 minute read
The need for good cybersecurity practices continues to be of utmost importance in our ever changing digital age. This is especially true for cybersecurity financial services. Protecting the personal and financial data of customers should be the first priority of financial services everywhere. Having good cybersecurity practices makes your company appear more trustworthy and protects both customers and services from hackers and malicious actors.
With more data breaches showing up in the news every year, it is important for every connected company (especially financial services) to protect their data and keep it secure. The financial and insurance sectors have been the most consistently attacked for the last three years in a row, and 19 percent of all attacks happened in 2018 alone.
The Equifax Hack of 2017
One of the biggest illustrators of why financial services should do everything in their power to up their security game is the Equifax breach of 2017. Still one of the biggest financial hacks of all time, the hack started with something simple and easily addressable by the company. A Twitter user notified Equifax of a potential security risk on their website. The vulnerability in question was a cross-site scripting bug. The bug was reported in 2016 and still wasn’t patched by the time of the hack.
The fact that the bug went unfixed was like a shining light on the financial firm’s security practices. The biggest vulnerability that resulted in the Equifax hack was a web app vulnerability that allowed non-privileged users to get access to admin functions. This vulnerability, known as remote code execution, results in the compromise of a web server and all the applications that depend on it.
Security researcher and ethical hacker David Hoyt posted screenshots to Twitter showing the vulnerability working on a website owned by Equifax, TransUnion, and Experian. With the big hack occurring between May and July, the firm had plenty of time to address the security issue, but failed to do so. Squashing the bug could have prevented the hack from happening at all, a perfect example of why companies should address cybersecurity issues the moment they are discovered.
As a result of the Equifax hack, up to 143 million Americans’ personal data was exposed. Identity thieves and fraudsters bought and sold some of this data on dark web marketplaces. Social security numbers, first and last names, birth dates, addresses, drivers license numbers and even credit card numbers were exposed and sold on the black market. Unquestionably the biggest financial hack in history, it could have all been avoided had Equifax addressed their security issues in time.
What Are Some of the Global Cybersecurity Practices in the Financial Services Market?
As a financial service, every company should take care to implement good cybersecurity practices and review them as needed to avoid breaches like the Equifax hack. Many firms follow tried and true practices such as having annual audits of cybersecurity practices, implementing changes to those practices when potential vulnerabilities are identified, utilizing bug bounties, practicing incident response and deploy tools for consumer peace of mind such as two-factor authentication.
Some of the best cybersecurity practices for financial services can be:
- Auditing cybersecurity practices and implementing changes when necessary. Every financial firm should have their security practices documented and should review these practices annually. If security flaws are identified, they can be addressed quickly, fixing any security bugs before hackers and other bad actors can find their way in.
- Taking advantage of bug bounties. Many financial services, tech companies, and even the United States government have utilized “bug bounties” for the identification of bugs in websites, servers, web applications, and more. With bug bounties, ethical hackers help companies identify bugs and submit them to companies so they can fix them before black-hat hackers exploit them for their own nefarious gains. Services such as HackerOne and Bugcrowd exist for bug hunters to find open bug bounties, and work as intermediaries between the companies and bug hunters.
- Using proven incident response practices. Develop incident response plans using tools such as artificial intelligence and machine learning and utilize technology that can assist in threat detection. Knowing how to identify a threat in real time can help security teams kill any vulnerability before it becomes known to malicious actors.
- Building trust with customers using digital security tools. Enabling security tools such as two-factor authentication can help build trust with customers. Customers want to know that their data is in good hands, and a great way for organizations to prove that they are serious about security is by putting security tools directly in the hands of the customers who use their services. Security features like two-factor authentication and biometric authentication in mobile applications can really help foster trust.
- Making security central with everyone at the organization. Many employees aren’t aware of some of the best cybersecurity practices within their companies. While hackers are aware that humans are the biggest security risk in any organization, many employees may not be aware of all of their company’s security practices. Making security a central point and making sure everyone is aware of the best practices can go a long way to helping protect the data they have promised to defend.

These are just a few of the ways financial services and other organizations around the world work to make sure that customer data is protected and safe from hackers.
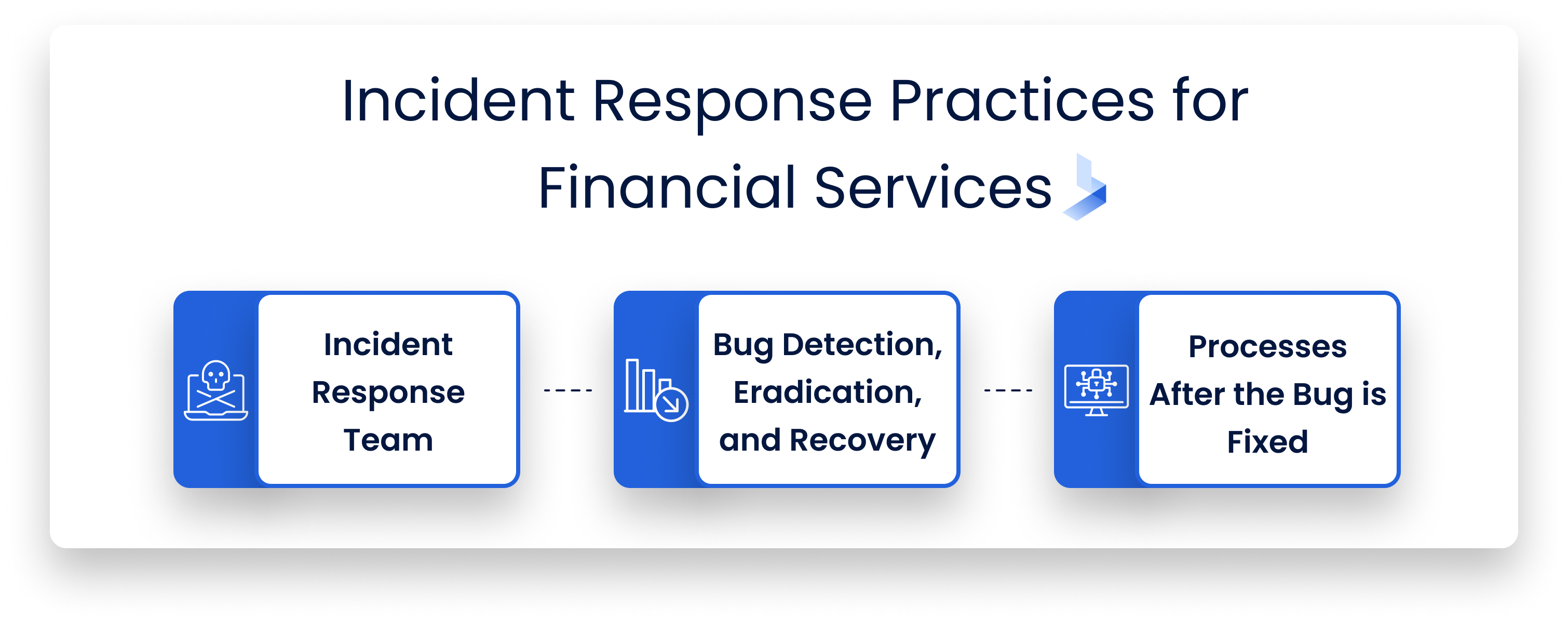
What are Some Acceptable Incident Response Practices for Cybersecurity Financial Services?
Cybersecurity should never take a backseat for any organization protecting personal customer data, and financial services are no exception. Developing, documenting, and maintaining solid incident response practices go a long way in making sure any organization’s security practices are bulletproof.
- Build a Computer Incident Response Team within the organization. A Computer Incident Response Team is a specialized group of experts within the organization that react to security incidents. These specialists can come from different facets of the organization, such as IT experts, network administrators, corporate representatives, and legal representatives. IT experts and network admins work to identify and close security bugs, while the corporate and legal representatives work to report the incident to regulatory agencies.
- Bug detection, eradication, and recovery. Security teams can utilize machine learning and artificial intelligence tools to analyze their networks and systems in real time to detect any possible security threats. When a bug is detected, the team should then work to clean up and delete the infected files, remove malware, and restore data from backups.
- Processes for after the bug is fixed. The work doesn’t always end after the security bug is detected is removed. It is then important to make sure the bug was documented, and the steps the team took to fix it should be outlined. This could come in handy if regulatory agencies need to do any follow-up on the incident. If malware was discovered, all permissioned users should have their passwords reset. It is also important that security teams scan their networks to ensure nothing further was done by the attackers.
Having a solid incident response plan is important for every organization! Incident response plans should be documented and adhered to by the security team, and all employees need to be made aware of practices to ensure they aren’t phished or social engineered by malicious actors.
How to Plan for the Future of Cybersecurity
In our ever-changing and connected world, there are constantly new threats popping up on the security horizon. It is highly important for cybersecurity financial services to adapt their practices when new threats are discovered and when new tools become available.
With the world going more wireless and adopting new Internet of Things technologies, along with vast amounts of data moving to cloud storage solutions, hackers and malicious criminals now have more digital targets than ever before. Luckily, new technologies are also emerging that organizations can deploy to protect their customers’ private data.
Blockchain solutions are becoming more and more popular, offering better privacy protection and faster, more efficient transaction times. Blockchains are immutable, transparent, and have proven security.
It is also important to remember that a vast majority of computing is now done on mobile devices and wearables. Ensuring the employees of your organization is running the most up-to-date software on their mobile devices (like their smartphones and tablets) and on their computer workstations ensure that these devices are kept safe from attacks.
Risk simulation tools aided by artificial intelligence can also help in the risk assessment department in the near future. Authentication for all mission-critical devices should also be kept safe. The device, its location, and device behavior can be monitored through adaptive authentication technologies.
It is important to make sure all cloud storage options are protected, encrypted and made available only to permissioned users. Ensure all employees are trained in the best security practices, and keep all computers and mobile devices up to date on the latest security patches from the manufacturers.
Act like your business is the target of criminal hackers. This can be a great motivation to keep your security top-notch, because after all, its not a question anymore of if your company will be hacked, but when.
BitLyft helps businesses just like yours with risk assessment and putting protocols in place to mitigate risks in the future. We will start with a FREE ASSESSMENT and go from there.
