How to Develop, Refine, and Execute an Incident Response Plan

 By
Jason Miller
·
10 minute read
By
Jason Miller
·
10 minute read
 Did you know that there is a cybersecurity attack every 39 seconds worldwide? And if you're not prepared, an attack on your business could cost you in terms of time, money, and customers. Simply put, people don't want to work with companies they can't trust with their personal information.
Did you know that there is a cybersecurity attack every 39 seconds worldwide? And if you're not prepared, an attack on your business could cost you in terms of time, money, and customers. Simply put, people don't want to work with companies they can't trust with their personal information.
If you don't have a written incident response plan, then it's time to prioritize this for your business. Malware threats are too scary to ignore any longer. So, keep reading to learn everything you need to know from our ultimate incident response guide.
Why You Need a Written Incident Response Plan
As mentioned, cybersecurity is an ever-growing problem and affects everyone at some point. If your company hasn't already been a target of cybercrime, then you've either been lucky or were unaware of it. And as an IT specialist, you don't want to be either.
Additionally, you don't have to be a victim of a crime to experience an incident. Natural disasters happen all around us and seem to be increasing. Don't risk losing important business due to infrastructure problems such as a server going down in an earthquake, hurricane, or other natural disasters.
When it comes to information security, you can't be too careful. You need a plan that outlines how you and your team will react in the face of an incident, whether it's man-made or a natural disaster. Regardless of the size of your business or the industry you're in, you are susceptible to disaster.
There are three important reasons every company should have an incident response plan:
- Protect your data and customer personal information
- Reduce costs by minimizing response times
- Protect your reputation
Recovering from a security incident will be much less costly and more timely when you and your team follow a plan. The sooner you can recognize an incident has happened and respond promptly, and you'll be able to quickly neutralize the incident with swift action.
You don't want to risk the inevitable scramble that comes from unpreparedness. By taking the time now to write out a detailed plan, you can mitigate the future risks that might come from an attack regardless of the source.
| Related Reading: What is Security Incident Response Plan? |
How to Create an Effective Incident Response Guide
Before we jump into the details and nuts of bolts to actually create your plan, let's take some time to outline the process you'll want to follow. Don't waste your time creating a plan that doesn't solve the problem effectively or solves the wrong problem. Take the time to create an effective plan that your team can follow and quickly resolve any incident that comes their way.
Create Your Team
The first step in creating your incident response guide is to create your team. The incident recovery team is responsible for not only identifying any possible threats but also responding quickly and accurately.
Take the time to identify the stakeholders in any response. This will include both management and key team members to carry out important tasks. You'll also want to ensure that your team is multidisciplinary and includes cross-functional team embers from all departments.
Some key stakeholders every company should involve on their team include:
- A team leader and/or an incident manager
- Someone from your communications and PR team
- An HR manager or executive
- Legal representation
Having a cross-functional team makes your company more secure. The more eyes you have watching for problems across the board, the more likely you will catch an incident before it becomes too big to handle quickly.
Remember, cybercrime won't attack only your IS department; everyone is vulnerable to malware, phishing email attacks, and the like. By training everyone across your organization to be aware of these problems, you'll decrease the likelihood of becoming a victim of cybercrime.
Perform an Assessment
Now that you have your team, it's important to spend some time brainstorming possible scenarios. Remember, this will include both man-made attacks from cyber crimes as well as responding to natural disasters. As more companies become global, you'll need to assess each location for all office buildings, warehouses, servers, and other infrastructure.
At this point, you're simply gathering information. You're not yet delving into the world of creating your plan or updating your systems. Simply take the time to review your organization and identify any security weak spots where you might be vulnerable.
Regular company-wide cybersecurity risk assessments will ensure your organization is more secure and ready to handle anything that might come your way. Assess not only what might happen but also determine the likelihood and severity of each incident. This will help you better prioritize each incident in how you prepare and plan for them.
Identify Assets and Resources
From production and sales to customer information, everything in your business is at risk of falling prey to cybercrime. Don't let a zero-day warning to your supply chain constrict and already tight turnaround time. Instead, know how you'll react and protect your assets to ensure your company continues to run smoothly.
Also, what resources will your team have available during an incident response? This includes both physical and digital resources such as current backups for your network should it go down. Your team needs to know where this is housed and have the authority to restore the most current backup from before the incident.
There are several different categories of cybersecurity tools and resources available to you and your team. It's best to determine the best one for you and your situation before you need it.
Another asset to consider is any vendors you work with or hire out. For example, if you outsource your network management to a vendor, be sure to ask them for their incident response plan. This way, you know what their response will look like and how you can best integrate your plan with theirs.
Outline Your Workflow
Creating your IR plan isn't a one-and-done project. Rather, this is an ongoing and iterative process. Before you begin, outline a workflow for identifying various risks as well as how you'll prepare to respond to each one.
Everyone on your team needs to know how they'll respond if someone approaches them with a possible security breach. Additionally, what is your workflow if someone simply notices a possible security vulnerability?
You need to have a plan for who will assess the vulnerability. Who will determine if it's truly a risk or not? And who will escalate it up the chain of command to create a reaction plan should that vulnerability come to pass?
Answering these questions now will shorten your response time and save you time and further damage. The faster you can respond, the more you can mitigate the fallout that will come from a data breach or other cyberattack.
Time is the most important factor in responding to any incident. The longer your response takes, the more it could cost your company. Save your company money and damage to your reputation by having a dialed-in response workflow.
Put It in Writing
Your plan is only as good as your team's ability to execute it. It's not good enough to have your response plan in your head, or worse, in a document that only lives on your computer. You must have a written plan that is available to everyone.
Cyber attacks don't happen Monday through Friday on a nine-to-five schedule. In fact, Friday at five, when everyone has mentally checked out for the weekend, is exactly when an attack is likely to happen. Your response can't wait for someone to call their manager and find out where the plan is before they can begin to execute it.
As you move into creating your plan, remember it is imperative that your IR plan is written out and that it is housed in a location everyone can access.
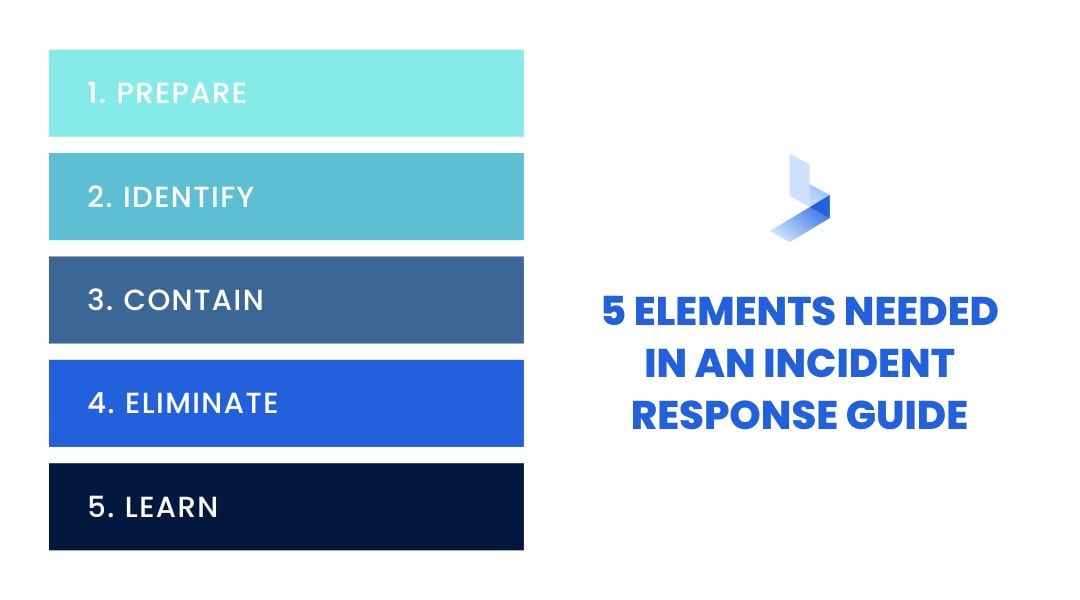
5 Elements Every Incident Response Guide Needs
Now that your foundation is laid, it's time to create your written guide. There are five distinct elements that every IR plan needs to have:
- Prepare
- Identify
- Contain
- Eliminate
- Learn
Let's dive into each one in more depth below.
Preparation Is Key
Unfortunately, when it comes to cyberattacks, we aren't talking about if but rather when you become a victim. That's why preparation is so vital to ensure that you respond in a timely and effective manner. A lot of the work you've done in the foundation above will allow you to fly through this step quickly.
Putting your team together and training them to handle any incident is vital to the preparation phase. At the very least, in this phase, everyone needs to know who they will notify should something happen. You also want to know what level of incidents you can handle in-house vs. when it's time to reach out to an outside firm.
The preparation phase also includes training everyone within your organization regarding what they should watch for and what emails or files to never click on or open. Providing the proper training is vital to ensuring the next step is adequately performed.
Identify Potential Threats
Identifying threats can come in many different forms. On the one hand, it might look like an employee calling the IT department to inform them that they accidentally clicked on a malicious email and now have malware on their laptop. Or it might come in the form of an automated security response or alarm that is triggered due to suspicious activity on your network.

Either way, you need to have a system for how your employees handle any situation that might arise. Does everyone within your organization know who to notify if something looks awry? Who is notified when an automated alarm is triggered throughout your system?
As you train their team, remind them that their job isn't to decide if something is important or not. Their job is simply to report anything suspicious and let your response team decide whether or not to implement their incident response plan. Awareness is half the battle, and your front-line employees are vital in helping you identify potential threats.
Once a potential threat is brought to the awareness of your team, it's your team's job to determine the depth of the threat, what the source was, and whether it was successful or not. Each of these factors will determine your next steps through the containment and eradication phases of your IR plan.
Contain and Isolate
This step in the process is similar to that of a triage nurse in and hospital emergency department. Your goal is to determine the severity of the problem and stop the bleeding. You won't necessarily solve the problem or cure your patient at this stage, you're simply categorizing and prioritizing each event.
Now that you've determined this is a priority event needing continuous monitoring, you'll identify the incident manager and implement your communication strategy. If you haven't already, this is also the step where you'll alert management and possibly any affected customers.
Depending on the severity level of the event, you'll need to determine if maintaining network security requires taking your system completely offline or if you can isolate it to one area that you can shut down. If you can cut off the attack from the rest of your system by isolating it, this can help the rest of your company to continue as usual and will affect fewer people, departments, and customers.
As you work through your training, you'll want to practice these steps until you can complete them as quickly and efficiently as possible. Remember, time is money, so the faster you can respond and react, the more you'll save. You must know how long it will take you to identify a breach, contain it, and then either revert to a backup or other response.
Eliminate the Threat
This phase is the long-term resolution of the event or threat of an event. You'll need to determine the root cause of the problem and remove the malware from your system. Malware threats can also be just as problematic as an actual attack and must be continually monitored and eliminated.
Depending on the event, you'll need to create and deploy any necessary patches to repair your system. Your team could remain in this phase for a while if the incident is particularly damaging. Additionally, for each incident you encounter, you will likely cycle between these two phases, contain and eliminate, several times.
As you work through this phase you will likely come a point where you need additional help from an outside expert. Cybersecurity is a complex and often endless process. Depending on the size and resources of your IT department, you could benefit greatly by bringing in an expert to patch and solve a cyberattack.
Unfortunately, small businesses are often the very victims that cybercriminals target. They know that you don't have the time or resources to devote to fixing an attack or the threat of an attack. That's why it's important to work with a partner you can trust.
Once you've deemed a threat or event over, you'll want to move on to the last step. Don't neglect to review and learn from each threat or event, or you risk opening yourself up for another attack going forward.
Learn From Each Incident
As you and your team transition back to normal operations, it can be too easy to simply change your passwords and move on. However, you can't afford to skip this last step. This phase involves taking a hard look at each step you took during your response.
The goal during this phase is two-fold. You want to update and improve your written incident response guide for future use. And you also want to improve and update your security measures so you aren't as vulnerable to future attacks.
As you learn more from each incident, be sure to update your plan. Your incidence response plan isn't written in stone; take the time to assess each incident and identify what you can learn from each one. Include these key takeaways in your plan so you can remember them later on down the road.
Hopefully, you never need to use your incident response plan. However, if you do, take the time to assess what you can learn from how you handled the situation. Every incident is an opportunity to learn from and make your plan more effective.
This phase can possibly be considered the most important of the five. How you learn from each incident and prepare for the next can mean the difference in future attacks.
| Related Reading: The Complete Guide to Creating an Incident Response Plan Template |
Best Practices for Your Incident Response Plan
As you create your written incident response guide, there are certain best practices that your team should keep in mind. These are important principles to remember for each incident you prepare for. Regardless of your industry or the type of event you're preparing for, these best practices will ensure your plan is efficient and successful.
Keep It Simple
The best plan is a simple one. During an emergency, you don't want your team confused by a complex plan. The best way to keep things simple is to have each person assigned to one role and one action plan, so they know exactly what to do when presented with an emergent situation.
We are all human, and during an emergency, many will begin to panic. By keeping your plan simple and easy to follow, you can eliminate the problems that could arise as everyone's anxiety begins to rise.
Have a Communication Plan
Part of your workflow will also include a communication strategy. Work through possible scenarios like what will happen if your email is compromised or your network goes down. What will you do if only half your team has access to either Teams or Slack or whatever you normally use for real-time communication?
Everyone on your team needs to know how to check in during a disaster. This can include if the power goes out due to a hurricane or snowstorm. Or it might include what to do if the cyberattack targeted your main lines of communication.
Consider having long-range, hand-held, portable transceivers. In many incidences, the lower the tech for communication, the better off your team might be.
Know Your Role
Everyone on your team needs to know their role during an incident response. They must also immediately know what is expected of them.
As mentioned in the first best practice, keep it simple. Don't rely on one person to take care of everything. What will your team do if that person is on vacation when an attack happens?
Everyone on your team needs to have one action they're responsible for. By spreading out responsibility, you eliminate the pitfalls that come from relying on any one individual. You can also respond faster as it will take one person, or a very small team, much longer to complete all the necessary steps.
Use This Guide to Create Your Plan Now
Every day, another business makes headlines as the latest cybercrime victim. It's a limelight no organization wants.
Waiting to respond until after a cyberattack is a costly, and potentially devastating, afterthought. What you need is an incident response plan, before a threat or breach emerges.
Ready to take that step but need a helping hand? Our team is just a click away. Our managed detection and response services include regular consultations, and our experts are ready to pave the way to a robust information security posture for your organization.
Reach out now, because waiting isn't an option when it comes to cybersecurity.
