What is LogRhythm SIEM?

 By
Jason Miller
·
5 minute read
By
Jason Miller
·
5 minute read
In an increasingly connected world, the specter of cyber threats looms large over organizations of all sizes and industries. No one is immune to the relentless attacks of criminal hackers and the devastating consequences of cybersecurity incidents. To protect your organization's digital assets, it's crucial to invest in the right software solution to combat cybercrime effectively. Among the plethora of options available, one stands out for its remarkable capabilities—LogRhythm SIEM.
If you're a regular reader of our blog, you've likely come across LogRhythm before. As an innovative product that has captured our attention and earned our trust here at BitLyft, we're excited to shine a spotlight on the features that make LogRhythm an exceptional security information and event management software solution, particularly for small and medium-sized businesses. Read on to discover how LogRhythm SIEM can help fortify your organization's cybersecurity posture and safeguard your critical data.
What is LogRhythm SIEM?
LogRhythm SIEM is a comprehensive security solution designed to consolidate log management, security analytics, and endpoint monitoring/forensics. Its primary objective is to detect threats and minimize an organization's risk exposure.
Developed by seasoned security experts specifically for their peers, LogRhythm SIEM reflects a deep understanding of what constitutes an effective SIEM tool. This all-in-one package offers a plethora of features, including threat lifecycle management, security automation and orchestration, targeted searches, and compliance reporting, equipping security professionals with a powerful arsenal to combat cyber threats.

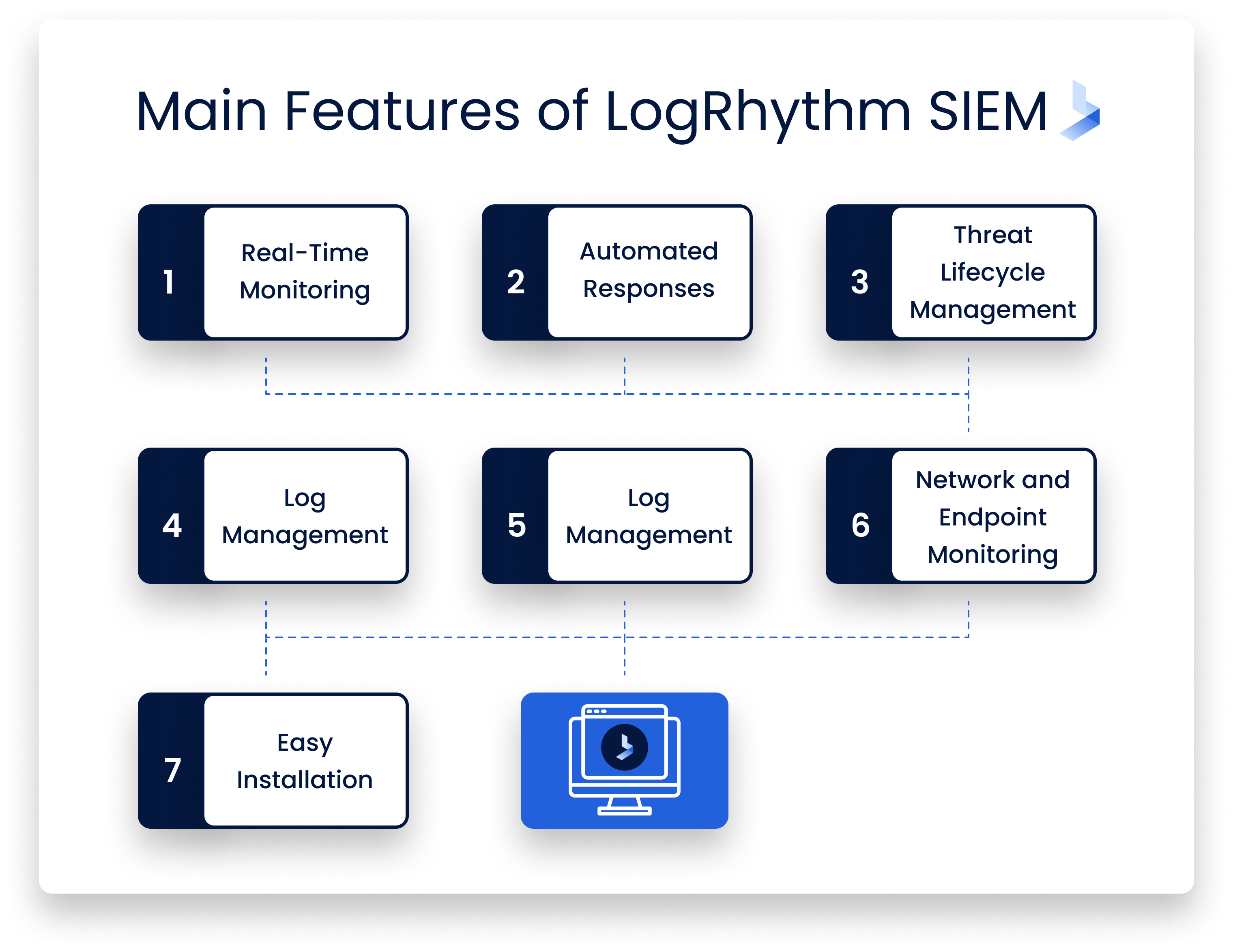
What are the main features of LogRhythm SIEM?
LogRhythm SIEM is a powerful and feature-rich security solution that enables swift identification, rapid response, and effective neutralization of potential threats. Engineered with user-friendliness in mind, LogRhythm SIEM ensures a seamless adoption process and ease of use for security professionals across the board.
Let's delve into some of the key features that set LogRhythm SIEM apart:
Real-Time Monitoring
A vital aspect of effective SIEM software is its ability to function in real-time, and LogRhythm excels in this regard. By leveraging Automated Machine Analytics, the platform scrutinizes all security events and associated forensic data, empowering security teams with real-time intelligence reports on potential threats. What sets LogRhythm apart is its ability to prioritize these threats based on their risk level, enabling security professionals to address the most pressing issues first. This dynamic prioritization streamlines the decision-making process and enhances your organization's ability to protect its digital assets from the most critical threats proactively.
Automated Responses
A crucial aspect of working in cybersecurity is the ability to respond instantly. When LogRhythm SIEM identifies a threat, you can call upon the SmartResponse Automation Framework to carry out different tasks. These can be decided by you before any events occur, so the system just kicks into gear and investigates certain threats or responds to them the moment they’re alerted upon. As you can imagine, this streamlines the whole process of identifying threats and dealing with them. Many can be handled without you having to do anything.
Threat Lifecycle Management
This is actually the name of a unique feature that you won’t see in any other SIEM. LogRhythm SIEM is designed to make your security operations far more efficient than they’ve ever been before. It is the only platform out there that currently has something called end-to-end threat detection. What this means is that you manage threats from the beginning all the way through to the end, all in one place. It makes the operation far more contained and easier to manage, while also lowering the cost of your cybersecurity software. Instead of needing a system to detect and system to respond/recover, it all takes place on the one platform.
Log Management
Storing and logging data is a vital part of any SIEM. With this one, you have one of the most effective and efficient log management systems around. You can store terabytes of data every single day, and you’ve also got immediate access to it. This is beneficial in instances where you need to find specific items of data for certain investigations. It’s very easy for you to search for what you need using structured and unstructured methods as well.
Network and Endpoint Monitoring
You have much greater access to endpoint and network activity when you use LogRhythm SIEM. It provides you with detailed forensic sensors that are built into the platform. As such, you can view any abnormalities in behavior to respond to any incidents in a far better way. It seems like a simple feature, but it allows you to manage network activity and endpoints with far more control and confidence.
Detect Threats Through Data Analysis
The beauty of this platform? It uses data analytics to detect threats way before they become serious problems. The idea is simple; data analysis from LogRhythm lets you see the footprints of every device in your network, which allows you to view advanced threats against it. It’s almost like predicting something will happen based on previous behavior. The advantage of this is that you obviously end up with rapid threat detection meaning you can deal with potential issues in advance of them actually causing problems.
Easy Installation
This isn’t much of a technical feature, but it’s still beneficial for everyone that wants to use this platform. LogRhythm SIEM, when in the hands of a seasoned and trusted security team, can be installed in far less time than some of its competing products. This means that your security partner can get it up and running in no time. There’s no waiting around, so it’s an excellent option for your security software solution. To make things even better, you don’t have to worry about your network being affected while it’s installed. You can carry on doing what you’re doing while this installs in the background, so there’s no worry of any downtime.
Moving to the next generation of SIEM
Embracing the next generation of SIEM technology is crucial to reducing the time required for detecting and responding to cyber threats. LogRhythm's move to Next-Gen SIEM incorporates three essential components that provide unparalleled security for your organization:
- Rapid Threat Identification: A cutting-edge SIEM solution must recognize threats early in the attack lifecycle, minimizing or eliminating any adverse impact on your business.
- Enhanced Visibility: Visibility is a crucial aspect of any robust SIEM system. Eliminating blind spots, enabling visibility across various domains and systems, and accelerating threat investigation and incident response are all critical features.
- Faster Response Time: A swift response to cyber threats is vital for maintaining organizational efficiency and promptly resolving issues. Next-Gen SIEM solutions must empower businesses to react quickly and effectively to emerging threats.
LogRhythm's Next-Gen SIEM solution ensures that organizations have all the necessary tools at their disposal to identify and tackle security threats with unparalleled speed and efficiency.
How does the LogRhythm Next-Gen SIEM differ from the first version?
LogRhythm’s Next-Gen SIEM Platform unifies next-generation SIEM capabilities, resulting in real-time deep visibility into IT environments. This ensures end-to-end threat management. Organizations can detect compromised systems and accounts, and insider threats with ease using LogRhythm Security Analytics. It does this by combining Network Behavioral Analytics (NBA) with integrated User and Entity Behavior Analytics (UEBA). The embedded security orchestration, automation, and response (SOAR) capabilities of LogRhythm delivers automation-enabled and efficient workflows across incident response and threat investigation.
What should you look for in a Next-Gen SIEM?
Simply using logs to identify suspicious behavior patterns is not enough. The LogRhythm SIEM solution offers rapid threat detection and response. It also uses many automated features to determine which threats are real and which ones aren’t.
There are a number of key features of the LogRhythm SIEM platform including:
- An open platform. This means it can easily be integrated with any infrastructure components you already have in place.
- Data preparation. The taxonomy of activities from log and machine data is standardized. This leads to more accurate detection of threats.
- Scenario analysis. This captures potential threat scenarios resulting in more efficient and faster threat detection analytics.
- Behavior analytics. This feature monitors your employees’ and users’ online behaviors and detects any significant changes in their actions. This leads to quicker threat detection and employee education.
With the ever-increasing cyber threats businesses face today, implementing an effective SIEM solution is crucial to mitigate substantial risks. However, it's not about choosing just any SIEM; it's about selecting the right next-generation solution tailored to your needs. LogRhythm, an award-winning option, is an excellent choice for bolstering your organization's cybersecurity.
An Effective SIEM Tool
LogRhythm SIEM is seen by many as a revolutionary security platform. It’s built by professionals for professionals, which means you’re greeted with a range of features that tackle some of the main sticking points usually associated with SIEM.
With the right system in place, you have a quick way of identifying suspicious activities and neutralizing them almost instantly. But LogRhythm, like any SIEM, is a tool. And a tool is only as effective as the expert that wields it.
If you’re interested in whether LogRhythm is a good fit for your IT infrastructure, reach out to us. At BitLyft, we’re highly trained with utilizing LogRhythm technology. Our managed SIEM services through BitLyft AIR® might be the perfect fit for your needs. We’d love to have a short conversation about your company’s cybersecurity goals, and whether LogRhythm could be a great fit for your business.

