What is Security Logging and Monitoring?

 By
Jason Miller
·
8 minute read
By
Jason Miller
·
8 minute read
A quick question for the cybersecurity decision-makers: How do you want your cybersecurity software to be defined? Agile? Durable? Intelligent? They’re all important considerations. However, the function of a cybersecurity infrastructure is more than simply identifying and countering security threats. Your security infrastructure should be more than just a “bouncer”… something that identifies threats and throws them out of the infrastructure with its tail between its legs. It should also encompass security logging and monitoring, both of which are both integral components to maintaining a robust cybersecurity infrastructure.
Your cybersecurity software should be in a state of constant learning.
Think of an enterprise’s cybersecurity software as a digital immune system. Your immune system does more than just fight off simple infections. It learns from them. Your immune system memorizes the characteristics of the infection it just fought off so if a similar infection enters your body again, it’ll have an easier time fighting it off.
An effective cybersecurity system works in a similar way. Many Security Information and Event Management software (SIEM) vendors have begun to integrate machine learning with their AI with this exact goal in mind.
What is Security Logging and Monitoring?
Security event logging and monitoring are two parts of a singular process that is integral to the maintenance of a secure infrastructure.
Every activity on your environment, from emails to logins to firewall updates, is considered a security event. All of these events are, (or should be,) logged in order to keep tabs on everything that’s happening in your technology landscape.

When it comes to monitoring those logs, organizations will examine the electronic audit log files of confidential information for signs of unauthorized activities.
If unauthorized activities (or attempts thereof) are found, the data will be moved to a central database for additional investigations and necessary action.
In a time where digital threats are widespread and ever-changing, the data gleaned from these log files is vital in keeping the infrastructure agile and responsive.
How does log monitoring work?
Security event logging and monitoring can only work when it is part of an effective data collection and analysis process. Security logs often contain a massive swath of data. So much of it that it will be near impossible for a human eye to effectively identify threats within it.
This means there will often be missed security incidents, false flags, and duplicate information.
This means that the key to effective Security Logging and Monitoring processes is the ability to weed out unnecessary information. To focus solely on critical events that could compromise the integrity and/or availability of the confidential information.
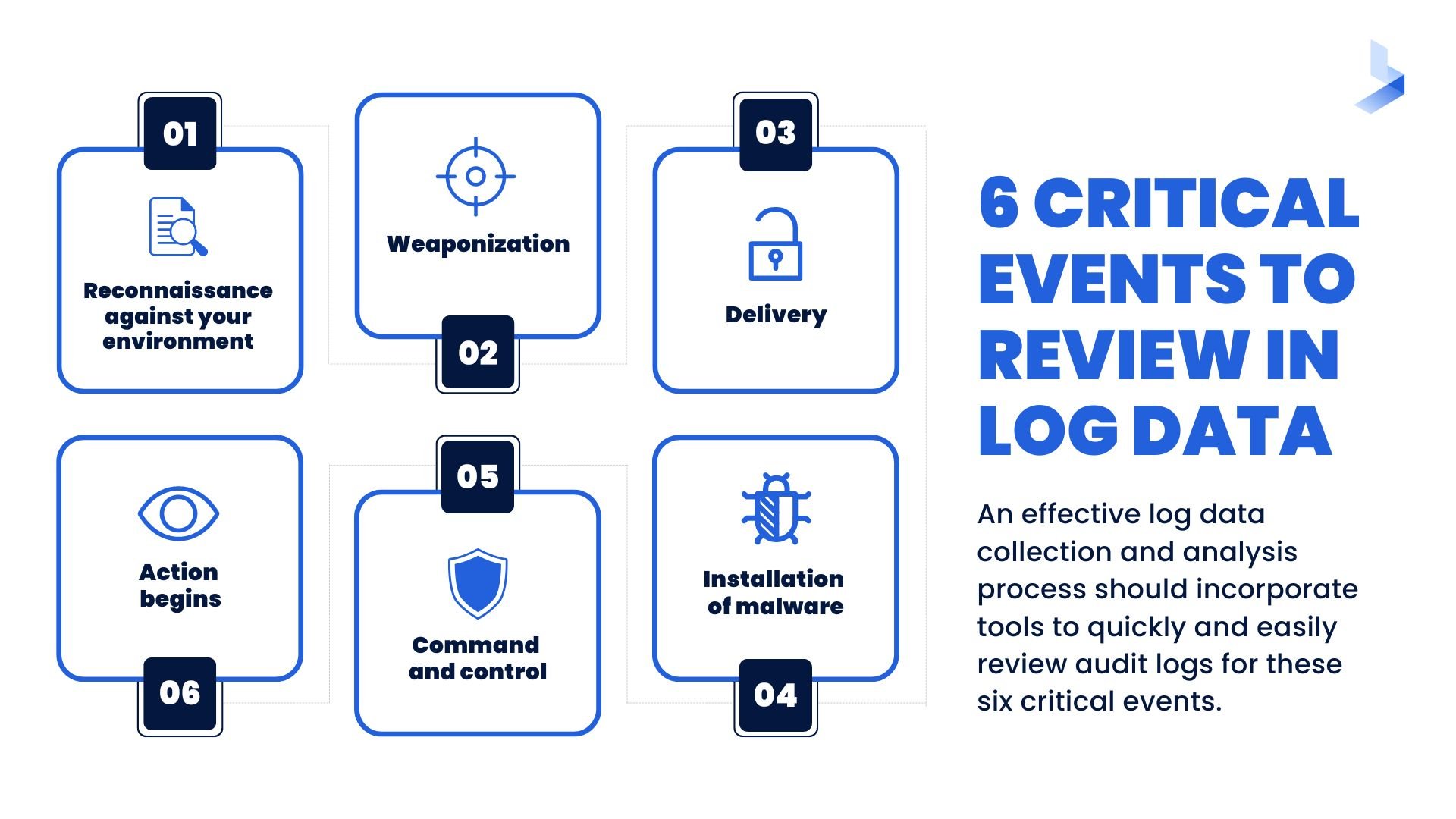
An effective log data collection and analysis process should incorporate tools to quickly and easily review audit logs for evidence of critical events like:
- Reconnaissance against your environment – where adversaries perform research on your environment… that could make you their next target.
- Weaponization – an intrusion within your environment where adversaries have decided to take action against your network and IT systems.
- Delivery – the manifestation of an exploit against a vulnerability within your network or IT systems.
- Installation of malware – observed when an adversary has modified native functionality in your environment to maintain persistence.
- Command and Control – when criminal hackers gain access to your server and systems and effectively take control of your environment.
- Action begins – determining what the adversary actions and maintaining visibility to them at all times are critical, you want to understand their desired goal and prevent the successful intrusion.
 Security Logging and Monitoring is a battle on two fronts. It requires periodic and long-term analysis of data to monitor instances to gauge the long-term effects of implemented systems and controls. All suspicious instances are reported to key personnel for immediate action, but they are also stored centrally for further analysis of long term trends.
Security Logging and Monitoring is a battle on two fronts. It requires periodic and long-term analysis of data to monitor instances to gauge the long-term effects of implemented systems and controls. All suspicious instances are reported to key personnel for immediate action, but they are also stored centrally for further analysis of long term trends.
Why Is Security Monitoring Important?
System logs are designed to provide relevant information that allows you to understand and identify issues that become threats to your network. You can typically rely on your system to collect data that reveals the activity that occurs within your network. However, these collections of data are rendered useless if relevant information quickly becomes buried in torrents of other incoming information. A quality security logging and monitoring system will help your organization complete a variety of important cybersecurity objectives.
Alerts for Faster Threat Detection
Log or infosec monitoring categorizes all actions that occur within the system. As the system learns which activities are normal, it’s able to weed out the data that reveals potential threats within an organization’s network. Real-time identification of these threats combined with an effective alert system provides you with a way to detect and interrupt potential threats more quickly.
Event Reconstruction
If a breach does occur within your organization, it’s vital to have the ability to quickly determine what happened and why it occurred. When a security event occurs, the first course of action is to visit security logs for an understanding of the vulnerabilities in your system. The ability to explain exactly what happened and the preventative measures your team is taking to prevent it from happening again helps your organization show commitment to your customers.
Prompt Identification of System or Application Issues
Outside threats aren’t the only issues your network faces. When issues arise within a system or network, productivity slows and tasks fail to get completed. For these problems to be fixed, they must first be identified, A comprehensive logging and monitoring system can provide your team with the ability to quickly find the root cause of system issues and promptly move on to the repair process. Security monitoring can even make it possible for alerts to allow system errors to be recognized before your customers or employees even file a complaint.
Faster Recovery From an Event
Events occur and you can count on them to disrupt files and cause downtime for your business or organization. It’s no secret that prolonged downtime is the enemy of good business. Log event files can help clarify what happened and recover essential files. Reconstruction of corrupted files can be completed more quickly by reversing the changes noted in the logs.
Customization for Your Organization
One of the biggest perks of an effective cybersecurity system is the ability to customize a plan to fit the needs of your organization. When your log monitoring system has the capability to identify potential threats, it could also alert the proper personnel of an issue before resulting problems arise. When your system is configured to notify targeted team members of potential threats or other issues, qualified personnel members can get started on applying the solution immediately.
Essential Data for Compliance
Compliance is a vital requirement for all types of organizations that collect and store sensitive data. For instance, all financial institutions and other companies that perform similar services (like colleges and universities that offer financial aid) are required to perform certain actions to remain in compliance with the Gramm-Leach Bliley Act of 1999. An important part of these requirements includes a yearly audit proving compliance with certain security measures like logging, monitoring, and management. As an added bonus, your monitoring software can be used to create a log to simplify the audit process.
24/7 Threat Detection
Cybercriminals often target organizations during off hours when chances of detection are less likely. Your IT team sleeps, takes vacations, and can’t be expected to monitor your network 7 days a week. Your monitoring system is always online and should have the ability to send out alerts of potential threats that occur any time of day or night.
What are the benefits of security logging and monitoring?
When you implement a robust system of Security Logging and Monitoring your organization benefits in a number of different ways.
Security logging and monitoring for the detection of security breaches
Most enterprises are afflicted by different types of security events. They can help guard against malicious external threats while also guarding against internal misuses of information. They can be detected in real-time to facilitate fast intervention while also contributing to your long-term strategy.
Security logging and monitoring for event reconstruction
Even if a breach should occur, audit trails can facilitate a reconstruction of the events leading up to the incursion. CIOs will have a clear idea of how the breach occurred and how to rectify vulnerabilities.
If a security breach were to occur, wouldn’t you like to be in a position where you could tell your board or investors exactly what happened and what steps you’re taking to prevent it from happening again?
Security logging and monitoring for faster recovery
Downtime is the bane of businesses. Audit logs can create a fast and effective recovery process. They can help to reconstruct data files which were lost or corrupted by reverse engineering from the changes recorded in the logs.
Outsource or keep in-house?
The right course of action will depend entirely on the needs of your business. Here are two key considerations:
- Do you have the tools and talent? If you’re struggling to fill key cybersecurity positions you may well benefit from outsourced help.
- Could your team be doing something more important? Log reviews and analysis tend to be time and labor-intensive activities. If your team has other, more important projects to work on, then you should strongly consider hiring additional help.
8 Considerations to Make When Choosing a Log Monitoring Tool
Most forms of software create logs of the actions that occur within a network. However, simply creating a list of activities doesn’t provide the relevant information you need to protect sensitive data against potential threats. When you’re searching for an effective monitoring system, it’s essential to find one that matches the unique needs and scope of your organization. Consider these properties when choosing the right log monitoring system for your organization.
Seamless Data Collection
Every logging system guarantees simple collection of data. Unfortunately, if the system doesn’t play nice with other applications that already exist within your network, you might be adding more work to an already overloaded schedule. A convenient security logging and monitoring system should allow you to customize your automated data collection process without additional manual tasks.
Appropriate Scalability
Having a large amount of data is the main reason security logs are impossible to manually sort and use in identifying potential risks. When organizations require a high traffic network, your monitoring system should be able to keep up with growing data. A system that is properly scaled for your network provides the speed your IT team needs to easily search for relevant data and the space to avoid unnecessary deletions.
Search Capabilities
When it comes to productivity, time is money. When your IT team is under pressure to identify and interrupt a cyber attack, every second counts. Your monitoring system must have the capability to allow users to launch a targeted search that will yield results in seconds. Efficient search capabilities can mean the difference between interrupting an attack and cleaning up the damage afterward.
Correlation Ability
Attackers use a single entry point to laterally move throughout your network in a way that is difficult to detect and does the most damage. These broad attacks mean logs across multiple departments can face damage. A monitoring system that allows you to set up tailored correlation rules to automate actions and responses across the entire network helps identify activities that seem common in one area of your network but raise questions when performed in other departments.
Security
Cyber threats and compliance issues are major problems for any organization. Finding a security logging and monitoring system that addresses these tasks during routine activity can eliminate a host of manual tasks traditionally completed by your IT team. When your organization is required to store sensitive information, you should have the ability to define users with the correct access level. Account administrators should have the ability to define access levels for other users and change the status as needed (like when user access must be suspended or deleted).
Communication/Output
Communication and collaboration are essential elements in the world of security. Data collection is typically a complicated operation that uses a variety of formats. Your security monitoring system must have the ability to output legible information to all users via the use of a dashboard, email, or report. Your system should also provide a data normalization process that generates information in the best format for your IT team.
Advanced Analytics
The ability to collect, categorize, and analyze data is essential for any organization. However, if you have a massive system that gathers hundreds of terabytes a day, you may need additional tools to simplify searches and help categorize important data. A monitoring system with advanced analytics can help you overcome the challenges that come with large amounts of data. When your system has the capability to integrate machine learning with data collection and organization, it gains the capability to identify unusual actions within the network.
Artificial intelligence (AI) tools that improve the monitoring process and streamline troubleshooting can provide ways to detect issues and threats early on. If your log monitoring system is part of a security information and event management (SIEM) system that provides crowdsourced immunization tools, you will gain the power of additional information across all organizations that use the service. Cyber threat intelligence gathers data from all clients on a platform and provides immunization from a new threat for all organizations across the platform.
Cost
Pricing models are often related to the volume of data you need to manage. Ideally, your log monitoring system should have the capability to grow with your organization while providing a considerable return on investment (ROI). The tools provided by your system will eliminate burdensome manual tasks that often take hours to complete. Additionally, when the system is more effective at identifying potential threats and helping you maintain compliance, considerable costs and fees are eliminated as well.
Planning for the future by learning from the past
Proactive security logging and monitoring are crucial for effectively responding to incidents. Plus, the longer your SIEM system is in place, the more powerful it becomes in combating future security events.
Just as a robust immune system is essential for maintaining our health, a mature SIEM is vital for ensuring your organization's resilience and longevity.
If you're seeking an expert cybersecurity partner to help your business build a strong security immune system, look no further. At BitLyft, we offer cutting-edge SIEM functionality through our managed detection and response service and platform, BitLyft AIR®. To discover how logging and monitoring can revolutionize your organization's security, request a demo today and take the first step toward a more secure future.

