Cybersecurity Maturity Model Certification (CMMC) 2.0: An Overview

 By
Jason Miller
·
17 minute read
By
Jason Miller
·
17 minute read
Is your organization up to par with the latest cybersecurity measures? If not, it should be. A recent study found that a single cybersecurity breach can cost a U.S. business over $9 million. This alarming figure is just one of many that underscore the importance of having strong cybersecurity measures in place.
One such measure is the creation of the highest priority programs released by the federal government. The CMMC 2.0 Defense Industrial Base (DIB) is a framework created by the U.S. Department of Defense (DoD). It establishes guidelines for implementing cybersecurity best practices.
.jpg?width=1080&height=400&name=Average%20Cost%20of%20a%20Data%20Breach%20(2).jpg)
Does your organization contract or subcontract with the federal government? It now needs to adhere to some strict cybersecurity measures. Read this guide to find out how to ensure your organization can become CMMC 2.0 compliant.
What Are Cybersecurity Standards?
Cybersecurity standards are a set of rules and guidelines that organizations use to ensure their systems and data are secure. These standards can be created by governmental agencies, industry groups, or companies themselves.
Cybersecurity standards typically cover areas of minimum security standards such as data encryption, access control, and incident response. They also ensure compliance with laws and regulations.
Organizations use cybersecurity standards to protect themselves from cyber threats. They also ensure compliance with laws and regulations.
What is CMMC? Why Was it Created?
The Cybersecurity Maturity Model Certification (CMMC) program is a framework that is used to assess the cybersecurity readiness of U.S. defense contractors. CMMC was created in response to the growing threat of cyber attacks. These attacks have become increasingly sophisticated and targeted in recent years.

Many companies that work with the U.S. government are now required to meet strict cybersecurity standards. This includes complying with the Department of Defense's Cybersecurity Improvement Program. The CMMC framework provides a more streamlined and efficient way for contractors to demonstrate their compliance with these standards.
The new CMMC 2.0 certification process will be conducted by third-party auditors. They will assess a contractor's cybersecurity practices against a set of criteria.
The goal of CMMC is to ensure that all contractors who do business with the U.S. government have adequate safeguards in place. This is to protect sensitive information from cyber threats.
Protecting Sensitive Information
Organizations hold a lot of sensitive information. Sensitive information includes customer data, financial records, and trade secrets. Organizations must safeguard this information. It protects organizations from theft, fraud, and other malicious activity.
The CMMC 2.0 standard includes requirements for protecting sensitive information. Here are just a few of the requirements:
- Encrypting data in transit and at rest
- Implementing access control measures
- Establishing incident response procedures
Complying with CMMC 2.0 is especially important if your organization handles sensitive data. Not only does it protect the data, but also protects your reputation.
CMMC 2.0 Defense Industrial Base (DIB)
The Department of Defense (DoD) is modernizing its Cybersecurity Maturity Model Certification (CMMC) program to further enhance the cybersecurity of the DIB. The updated program, CMMC 2.0, will provide greater clarity and certainty for contractors seeking to do business with the DoD. It will also improve the DoD's ability to prevent, detect, and respond to cyber threats.
The CMMC 2.0 program will be implemented in phases. The first phase focuses on identifying and addressing gaps in existing cybersecurity requirements. The second phase will pilot the new certification process.
Ultimately, the goal is to ensure that all contractors working with the DoD are certified under CMMC 2.0. This will help to protect sensitive or classified information. It also ensures that contractors are meeting the highest standards for cybersecurity.
Why Is CMMC Important?
The CMMC is important because it provides a framework for organizations to put in place cybersecurity best practices. This is beneficial for organizations. It helps organizations protect themselves from cyber threats.
Also, CMMC ensures compliance with laws and regulations. It provides reassurance to customers and partners. Taking these extra measures shows an organization takes cybersecurity seriously. Customers and partners can rest assured the necessary measures are in place to protect their data.
Who Is CMMC 2.0 for?
CMMC 2.0 is for any organization that functions as a contractor or subcontractor for the federal government. This includes businesses of all sizes, in all industries, that work with the U.S. Department of Defense. Organizations that are required to comply with CMMC 2.0 will need to be certified by a third-party assessor.
How CMMC 2.0 Affects Businesses and Government Agencies
CMMC 2.0 is the newest initiative from the U.S. Department of Defense (DoD). It'll require businesses and government agencies to follow certain cybersecurity standards.
CMMC 2.0 will have a major impact on how these organizations operate. They will need to invest in upgrading their cybersecurity practices and procedures.
Also, CMMC 2.0 will create new opportunities for businesses that provide cybersecurity services. There will be an increased demand for companies that can help organizations meet the CMMC requirements.
Unfortunately, CMMC 2.0 will also increase the cost of doing business with the DoD. This is because contractors will need to follow the new standards and it'll cost organizations money to do so. As such, it is important for organizations to understand the implications of this new initiative.
What is CISA and How Are They Involved?
The Cybersecurity and Infrastructure Security Agency (CISA) is a federal agency charged with protecting the nation's critical infrastructure from cyberattacks. CISA also works to improve the resiliency of the country's cyber defenses. Not only that, it helps coordinate cybersecurity response efforts in the event of a major attack.
CISA recently presented its Shields Up initiative. This is a public-private partnership that helps small businesses improve their cybersecurity posture. Taking cybersecurity a step further, CISA is implementing the CMMC program. It is a certification aimed at businesses of all sizes that wish to contract with the federal government.
The certification will be a requirement of CMMC 2.0 upon completion of its rule-making process. CMMC 2.0 includes new requirements for protecting Controlled Unclassified Information (CUI).
The CMMC program is designed to help businesses of all sizes improve their cybersecurity posture. Ultimately, it protects the nation's critical infrastructure from cyberattacks.
CISA offers resources and assistance to businesses interested in pursuing CMMC certification. They even provide a self-assessment tool and guidance on how to develop an implementation plan.
The CMMC 2.0 Standard
The CMMC 2.0 standard builds on the previous version with new requirements and recommendations. The purpose of the CMMC 2.0 standard is to help organizations protect their systems and data from cyber threats.
The CMMC 2.0 standard includes requirements for protecting sensitive information. These requirements include:
- Encrypting data in transit and at rest
- Implementing access control measures
- Establishing incident response procedures
If your organization handles sensitive information, it is especially important to follow the CMMC 2.0 standard to safeguard sensitive information.
The CMMC 2.0 standard is just one of many cybersecurity standards that organizations can use. Others include the ISO 27001 standard (developed by the International Organization for Standardization) and NIST 800-172 (developed by the National Institute of Standards and Technology).
How Is CMMC 2.0 Different From CMMC 1.0?
CMMC 2.0 is the latest version of CMMC. What sets CMMC 2.0 apart from CMMC 1.0 is the requirement of using a certified third-party assessor (C3PAO). The C3PAO performs an independent assessment of the organization's cybersecurity posture. This difference is in addition to the updates and improvements made to the model itself.
To achieve certification at any level, organizations must have a 3PAO to assess their compliance with the requirements laid out in CMMC 2.0. The DoD has said that it will begin requiring contractors to be certified starting in 2023.
The release of CMMC 2.0 represents a major change for the DoD and its contractor community. By mandating the use of a third-party assessor, the DoD is ensuring that all contractors undergo a rigorous and independent evaluation. This is for the protection of sensitive data. It also safeguards critical systems from potential cyber threats.
Benefits of CMMC 2.0 Certification
CMMC 2.0 is a new certification framework that will soon be required for all DoD contractors. CMMC 2.0 includes several important changes. It'll require contractors to achieve a certain CMMC level of maturity. Also, ensures that DoD contractors have robust cybersecurity programs in place.
CMMC 2.0 includes several new requirements. These include incident response plans and security awareness training for employees.
Achieving CMMC 2.0 certification will also ensure that your company is able to bid on and win DoD contracts. It'll demonstrate to current and future clients your company takes cybersecurity seriously. It also shows your organization is committed to protecting sensitive data.
CMMC 2.0 third-party certification will become mandatory for all DoD contractors. It is essential to start working towards certification now. By taking initiative to invest in CMMC 2.0 compliance now, your company will be well-positioned to win DoD contracts in the future,
CMMC 2.0 Levels
The goal of the CMMC is to protect DoD information from cyber threats. It will do so by ensuring that contractors who have access to this information meet minimum security standards.
The CMMC is not mandatory for all contractors, but those who wish to do business with the DoD must be certified at one of the three levels of CMMC 2.0.
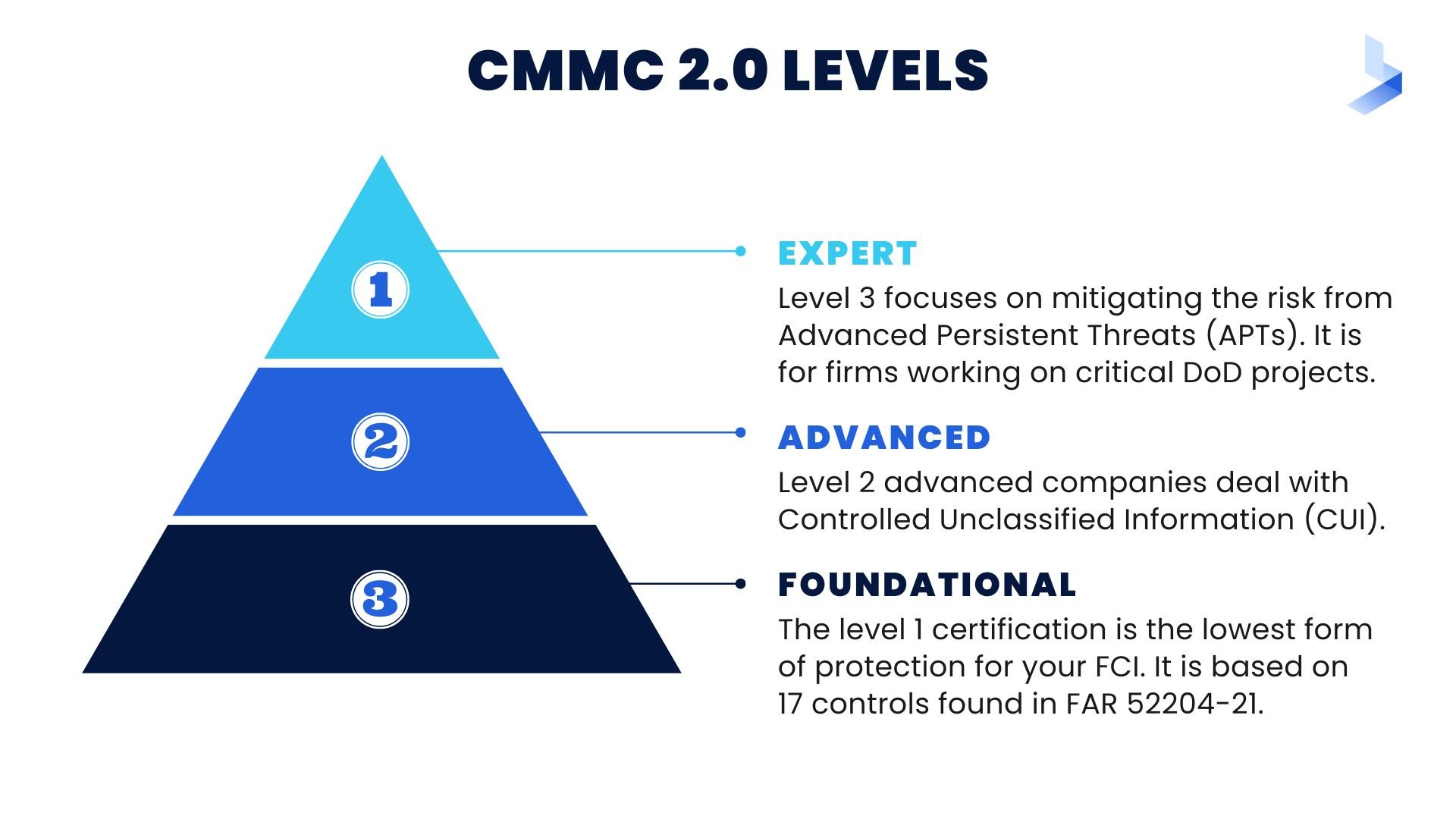
The higher the level, the more stringent the requirements. For example, Level 1 requires contractors to have basic protections in place. But Level 3 requires them to have an advanced cyber incident response plan. These three levels are:
Level 1: Foundational
The level 1 certification is the lowest form of protection for your FCI. It will be based on 17 controls found in FAR 52204-21. These prevent anyone without permission from accessing an information system containing sensitive data, such as name and social security number.
Level 2: Advanced
Level 2 advanced companies deal with Controlled Unclassified Information (CUI). The new requirements for Level 2 will be the same as NIST SP 800-171 and will get rid of any processes that were unique to CMMC. This adheres to the 14 security levels and 110 controls set by the National Institute of Technology and Standards.
They help protect CUI information. As a result, the 20 outdated requirements from DoD's old CMMC Level 3 are no longer necessary. What this means is that the new Level 2 is entirely consistent with NIST SP 800-171.
Level 3: Expert
Level 3 focuses on mitigating the risk from Advanced Persistent Threats (APTs). It is intended for firms working on DoD's most critical projects. The old CMMC Level 5 is comparable to this new Level 3. The DoD has yet to define the precise security standards for Level 3 (Expert). But it has indicated that they will be based on NIST SP 800-171 and a subset of NIST SP 800-172 controls.
Why NIST SP 800-171 and NIST SP 800-172 Play a Vital Role in CMMC 2.0
NIST SP 800-171 and NIST SP 800-172 are two of the most important standards for cybersecurity. They provide a framework for organizations to develop robust cybersecurity programs.
In addition, they ensure that contractors who have access to sensitive data meet minimum security standards. As a result, they play a vital role in ensuring the security of DoD information.
NIST SP 800-171 Explained
NIST SP 800-171 is a security control guidance document. It was published by the National Institute of Standards and Technology (NIST). NIST SP 800-171 provides recommendations for security measures that organizations can take. It will help protect their information systems from unauthorized access.
The guidance applies to all types of organizations. Many of these include government agencies, businesses, and educational institutions.
The security controls are appropriate for systems that process, store, or send federal information. They are also generally applicable to other types of information systems. Organizations can use these to supplement their existing security programs or to develop new programs.
NIST SP 800-171 is part of a larger body of NIST guidance for securing federal information systems. This guidance includes the NIST Cybersecurity Framework. It provides a comprehensive approach to managing cybersecurity risk. In addition, there are other NIST publications that address specific aspects of cybersecurity.
NIST SP 800-172 Explained
NIST SP 800-172 is part of a larger body of NIST guidance for securing federal information systems. This guidance includes the NIST Cybersecurity Framework. The framework provides a comprehensive approach to managing cybersecurity risk. There are also other NIST publications that address specific aspects of cybersecurity.
NIST SP 800-172 provides guidance on security controls. It also outlines assessment procedures for federal contractors handling Controlled Unclassified Information (CUI). NIST SP 800-171 covers basic cybersecurity hygiene, while NIST SP 800-172 covers a modest series of advanced controls.
The two standards are complementary. Organizations should use both NIST SP 800-171 and NIST SP 800-172 to be fully compliant with the requirements for handling CUI.
Key Security Requirements in NIST SP 800-171 and NIST SP 800-172
The key security requirements in NIST SP800-171 and NIST SP 800-172 include:
- The need for physical and information security
- The control of access to facilities and systems
- The protection of data
To meet these requirements, organizations must have the proper policies and procedures. These ensure the safety of their facilities, systems, and data. Some of the key security requirements in NIST SP 800-171 and NIST SP 800-172 include:
Access Control
Organizations must have controls in place to prevent unauthorized access to sensitive information. They can implement user authentication, role-based access control, and least privilege.
Audit and Accountability
Organizations must track and log all activity on their systems. This is done so that they can identify and investigate potential security incidents.
Awareness and Training
Organizations must provide security awareness and training to all employees. It is imperative that employees can understand and comply with security policies and procedures.
Configuration Management
Organizations must track and manage all changes to their systems and configurations. This is key for preventing unauthorized changes.
Contingency Planning
Organizations must have a plan in place for how to respond to and recover from a security incident. This may include measures such as data backup and disaster recovery.
Identification and Authentication
Organizations must have controls in place to verify the identity of users. This is a top priority before granting them access to sensitive information. Controls may include measures such as two-factor authentication and password management.
Incident Response
Organizations must have a plan in place for how to respond to a security incident. This may include measures such as identifying and containing the incident, performing forensics analysis and restoring systems.
Media Protection
Organizations must have controls in place to protect information stored on physical media. Examples of physical media include hard drives and laptops. This may include measures such as encryption and physical security.
Physical and Environmental Security
Organizations must have security physical controls in place. Physical controls protect their facilities and equipment from physical threats. This may include measures such as security guards and access control.
Risk Assessment
Organizations must periodically assess their risks, in order to identify and prioritize controls.
Security Assessment
Organizations must periodically assess their security controls. They need to know that they are effective.
System and Information Integrity
Organizations must have the proper controls in place. They need to make sure their systems and information are free from corruption and tampering. This may include measures such as data integrity checks and digital signatures.
Incorporating CMMI Processes
One of the key benefits of CMMC 2.0 is that it can be used in conjunction with other cybersecurity frameworks. One such framework is the Cybersecurity Maturity Model Certification (CMMI).
CMMI allows businesses to tailor their cybersecurity programs to meet their specific needs. It also ensures that they are meeting all the necessary requirements.
By using both CMMI and CMMC 2.0, businesses can create a comprehensive cybersecurity program. This program can help them protect their data and meet all the requirements of the DoD.
What Is CMMI?
CMMI is a process improvement approach. It provides organizations with the essential elements of effective processes.
CMMI is often used to guide process improvement across a project, a division, or an entire organization. It's composed of five maturity levels, each of which represents an increasing level of process capability.
Level 1
Initial Processes are characterized as ad hoc and frequently unmanaged. There is little control over these processes, and results are often unpredictable.
Level 2
Managed Processes are planned and executed in a controlled manner. Results are repeatable, but there is still room for improvement.
Level 3
Defined Processes are well-documented and standardized. The organization has complete control over these processes. Also, the results are consistent and predictable.
Level 4
Quantitatively Managed Processes are monitored and controlled using quantitative methods. Organizational performance is continuously improved through the application of these methods.
Level 5
Optimizing Processes are constantly being improved through both incremental and innovative changes. The organization has achieved a state of continual process optimization. The CMMI maturity model is designed to help organizations progressively improve their processes. By understanding where they are on the maturity scale, they can identify the areas where they need to make changes in order to improve their overall performance.
Managed SIEM and CMMC 2.0 Compliance
A managed SIEM solution is a turnkey security information and event management system. It delivers the benefits of SIEM without the hassle of managing it in-house.
A managed SIEM service provides real-time visibility into your IT environment. With this, you can quickly identify and respond to threats.
It also automates many of the tedious tasks associated with SIEM. These include log collection, normalization, and correlation. This allows you to focus on your business, not your SIEM.
A managed SIEM solution typically includes a number of components.
Centralized Log Management
It collects and stores all logs from devices across your network in a central repository for easy searching and analysis.
Security Event Correlation
It analyzes log data in real-time to identify and flag suspicious activity
Reporting and analysis
Managed SIEM generates reports on security events and trends so you can quickly spot potential threats.
Threat Intelligence
SIEM provides real-time information on the latest security threats. It also helps to proactively protect your network.
24/7 Monitoring and Support
Managed SIEM ensures your SIEM solution is always up and running. It offers around-the-clock support from security experts.
Managed Endpoint Security and CMMC 2.0 Compliance
Managed endpoint security is the protection of devices that connect to a network. This can include desktops, laptops, servers, and mobile devices. Endpoint security is important because these devices are often used to access sensitive data.
There are a number of different endpoint security solutions available. These include antivirus software, firewalls, and intrusion detection systems.
A comprehensive endpoint security solution will protect your devices from a variety of threats. This includes viruses, malware, and hackers.
Endpoint security is a critical part of becoming CMMC 2.0 compliant. By protecting your devices, you can help to ensure that sensitive data is not compromised.
Managed SOC and CMMC 2.0 Compliance
The Managed Security Operations Center (SOC) is a security service. It proactively monitors, detects, and responds to cybersecurity threats 24/7/365.
The Managed SOC team often uses the latest tools and technologies. Its mission is to constantly monitor your network for signs of unusual or suspicious activity.
When they detect a threat, the team will immediately take steps to contain and remediate the issue. The Managed SOC team will also work with you to develop a customized security plan to help prevent future attacks.
Managed Detection and Response and CMMC 2.0 Compliance
Managed detection and response (MDR) is a cybersecurity solution that is becoming more and more popular. It combines multiple security tools and technologies into a single platform. This allows for comprehensive visibility and protection for an organization's entire network.
MDR provides complete coverage of an organization's cybersecurity posture. It integrates data from disparate security solutions. This data includes endpoint protection, network security, email security, and more.
This unified view of an organization's security posture allows security teams to better identify and respond to threats. MDR solutions offer advanced capabilities. Often, this is in terms of automation and machine learning to further improve threat detection and response times.
Becoming CMMC 2.0 Certified
The CMMC 2.0 is a significant update from the previous version, and it includes new requirements at all levels. Organizations that are certified at one of the lower levels of the previous CMMC will need to make changes to their security practices. This is to ensure they meet the new standards. However, the benefits of being certified—such as being able to do business with the DoD—are well worth the effort.
To become certified at a particular level, contractors must undergo an assessment by a third-party assessor. Once certified, your organization will need to maintain its certification. This is done by undergoing periodic reassessments.
Cybersecurity is an important issue for all organizations. CMMC 2.0 is a valuable tool for ensuring that contractors meet minimum security standards. Be sure to take the time to understand the requirements of CMMC 2.0. This will ensure your organization is doing everything it can to protect itself from cyber threats.
Associated Costs of Becoming CMMC 2.0 Certified
The cost of becoming CMMC 2.0 certified will vary depending on the size and complexity of your organization. It also depends on the level of certification you are seeking.
In general, you can expect to spend between $5,000 and $100,000 on the assessment process. However, this is just a rough estimate, and your actual costs may be higher or lower depending on your specific circumstances.
In addition to the cost of the assessment itself, you will also need to invest in the resources and personnel needed to meet the new standards. This may include hiring additional staff and implementing new security technologies. Also, you may need to make changes to your processes and procedures. The exact cost of these investments will vary depending on your organization, but you should expect to spend at least a few thousand dollars.
Overall, the cost of becoming CMMC 2.0 certified is significant, but it is worth it for contractors who want to do business with the DoD. The benefits of being certified—such as increased security and improved reputation—will far outweigh the costs.
The Five Steps to Certification
CMMC 2.0 is a framework that provides guidance for implementing security controls and processes. These processes safeguard Controlled Unclassified Information (CUI).
To achieve CMMC 2.0 certification, organizations must go through an assessment process. They are conducted by a Certified Third Party Assessment Organization (C3PAO). The assessment consists of five steps:
Step 1: Prepare for Certification CMMC 2.0
To become certified, organizations must first complete a cybersecurity audit. Prepare for the assessment by reviewing the CMMC 2.0 model. Also, document your organization's current cybersecurity measures.
The assessment requires you to have a strong understanding of the CMMC model. Review it thoroughly and be sure to document your findings. This will help you prepare for the assessment and give you the best chance at success.
Step 2: Schedule an On-site Assessment with a C3PAO
C3PAOs provide on-site assessments. Their mission is to help organizations determine their compliance status. They also help organizations develop corrective action plans.
Step 3: Conduct an Opening Conference With the C3PAO Assessors
The opening conference is conducted to review the scope and objectives of the assessment. This will help ensure that everyone is on the same page and understands what is expected of them. Having a clear goal in mind will make it easier to complete the assessment requirement and get accurate results.
Step 4: Undergo the Actual Assessment
During the assessment, C3PAO personnel will observe and interview personnel. They will also review policies and procedures and evaluate technical controls.
Step 5: Participate in a Debriefing
During the debriefing, the C3PAO assessors will provide feedback on their findings. A debriefing with the C3PAO assessors is an opportunity to learn more about your performance and get feedback. It's a chance to reflect on what went well and identify areas for improvement. The debriefing can also help you understand how you can contribute to the organization's success.
.jpg?width=1024&height=768&name=Five%20Steps%20to%20CMMC%202.0%20Certification%20(1).jpg)
Organizations that successfully complete these five steps will receive a CMMC certification. Certification at any level demonstrates the commitment of an organization to protecting CUI and improving cybersecurity.
Challenges Associated With Certification Under CMMC 2.0
The CMMC is a unified standard for cybersecurity created by the U.S. DoD. The goal of CMMC is to improve the security of the defense industrial base. It does so by requiring contractors to implement specific cybersecurity controls.
The latest version of CMMC, CMMC 2.0, was released in November 2021. CMMC 2.0 does retain many of the same features as the previous version. However, there are some new challenges associated with certification under the updated standard.
First and foremost, CMMC 2.0 requires contractors to install a larger number of controls than in previous versions. This can be costly and time-consuming.
Also, CMMC 2.0 contains new requirements related to incident response and supply chain security. It may require contractors to make changes to their existing processes and procedures.
Finally, because CMMC 2.0 is still relatively new, there is a lack of trained assessors who are familiar with the standard. As a result, contractors may have difficulty finding an assessor who can properly certify their compliance with CMMC 2.0.
As you can see, CMMC 2.0 presents some challenges. But don't let that deter you. It is still an important step towards improving the cybersecurity of the defense industrial base.
How CMMC 2.0 Will Impact the Future of Cybersecurity
The release of CMMC 2.0 represents a major step forward in the effort to improve the cybersecurity of the defense industrial base. The updated standard contains new requirements. They are related to incident response and supply chain security. They will help contractors better protect sensitive information.
Block Adversaries
Besides, the larger number of controls required by CMMC 2.0 will make it more difficult for adversaries to exploit vulnerabilities. As a result, the adoption of CMMC 2.0 is likely to have a positive impact on the future of cybersecurity.
Effective Response
The increased focus on incident response in CMMC 2.0 will help organizations better deal with cyberattacks. In the past, many organizations have been unable to effectively respond to incidents due to a lack of planning and coordination. The new requirements in CMMC 2.0 will force organizations to put more thought into their incident response plans. In the end, it will improve their ability to deal with attacks.
Supply Chain Security
The supply chain security requirements in CMMC 2.0 are also likely to have a positive impact on cybersecurity. In the past, many organizations have failed to properly vet their suppliers. This has resulted in the introduction of vulnerabilities into their systems. The new requirements in CMMC 2.0 will force organizations to be more diligent in their supplier selection process. It will help to reduce the risk of vulnerabilities introduced into their systems.
Overall, the adoption of CMMC 2.0 is likely to have a positive impact on the future of cybersecurity. The new requirements will help organizations better protect their systems and data. It will ultimately lead to a reduction in the number of successful cyberattacks.
Increase in Cybersecurity-Related Jobs
The release of CMMC 2.0 is also likely to lead to an increase in cybersecurity-related jobs. The new requirements in CMMC 2.0 will force organizations to invest in personnel and resources. This is to ensure compliance with the standard.
As a result, there will be a need for more security professionals who are familiar with CMMC 2.0. Also, the increased focus on supply chain security is likely to lead to a need for more cybersecurity professionals who are familiar with supplier selection and management.
The release of CMMC 2.0 is a major step forward in the effort to improve the cybersecurity of the defense industrial base. The updated standard contains new requirements related to incident response and supply chain security. It will help contractors better protect sensitive information.
The larger number of controls required by CMMC 2.0 will make it more difficult for adversaries to exploit vulnerabilities. As a result, the adoption of CMMC 2.0 is likely to have a positive impact on the future of cybersecurity.
What to do After You Achieve Certification
After a company achieves CMMC 2.0 certification, there are a few things that it needs to do in order to maintain the certification. First, it is important to create an internal audit team. This team should be responsible for ensuring that all processes and procedures are being followed.
Second, the company should develop a plan for how to respond to incidents or breaches. This plan should include who to contact, what steps need to be taken, and how to communicate with the relevant authorities.
Finally, it is important to keep up with changes to the CMMC 2.0 standard. It'll also help make sure that all employees are aware of any changes that could impact their work.
By taking these steps, companies can ensure that they maintain their CMMC 2.0 certification. They will be able to continue to provide a high level of protection for their data and information assets.
Improve Your Cybersecurity Infrastructure
CMMC 2.0 Defense Industrial Base (DIB) is the result of a collaborative effort between the government and industry. It develops a unified framework for managing cyber risk.
The benefits of certification under CMMC 2.0 are many. They include improved cybersecurity posture, reduced risk, and increased trust between businesses and government agencies. There are challenges associated with certification. But, they can be overcome through planning and collaboration.
Cybersecurity is critical to the future of our economy and CMMC will help ensure that we are prepared for the next attack. Are you ready for CMMC 2.0? Schedule a needs assessment today to find your cybersecurity solution.
