Advanced Tactics for Common Cybersecurity Solutions

 By
Jason Miller
·
8 minute read
By
Jason Miller
·
8 minute read
.png?width=350&height=350&name=Average%20Tools%20Used%20by%20Security%20Teams%20(1).png) Every business faces cybersecurity risks, but companies don't face exactly the same risks. The risks to your company may depend on your industry, the information you store and share, and specific details about your unique business. Cybersecurity solutions are designed to work together to provide your organization with customized protection across your entire network. However, if you don't have a clear understanding of how these tools work and how they can be used together, you may not be getting the most comprehensive protection possible.
Every business faces cybersecurity risks, but companies don't face exactly the same risks. The risks to your company may depend on your industry, the information you store and share, and specific details about your unique business. Cybersecurity solutions are designed to work together to provide your organization with customized protection across your entire network. However, if you don't have a clear understanding of how these tools work and how they can be used together, you may not be getting the most comprehensive protection possible.
The average organization utilizes 29 different security tools, yet most of these tools are not being used to their fullest potential. This guide shares practical tips to effectively use, integrate and configure some of the most common security tools.
Advanced Tactics for SIEM Tools
Security Information and Event Management is a must-have for any organization trying to protect data and centralized information infrastructure. SIEM tools gather and normalize event data, recognize suspicious activity, send alerts for threats, and simplify compliance requirements. Your SIEM solution also provides complete visibility into the actions that take place on your network through a convenient dashboard. Highly effective SIEM software is customizable to recognize unique threats in different environments. However, if you don't take action to take advantage of all the features of your SIEM solution, you're less likely to achieve the results you seek. These advanced tips can help you get the most out of your SIEM solution.
- Seek a solution to meet your cybersecurity goals. SIEM tools come in various types with differing capabilities. For the most effective results, you should seek a solution that is scalable, captures data from multiple sources, includes artificial intelligence (AI) or machine learning (ML) based analytics, and reacts in real time.
- Choose what to monitor. More data isn't always better. Determine where sensitive information exists within your network and the types of data you want your system to collect. This may include logs from firewalls, file and directory servers, intrusion detection/protection systems, and endpoint security products. Modern enterprises are also likely to store information on cloud services and applications.
- Understand the value of integration. Your current tech stack is an important part of how you run your business. SIEM tools offer various integrations. Take the time to learn how integrations work and which solutions are most compatible with your existing products.
- Tune the system for maximum effectiveness. Feedback is priceless to eliminate false alerts and improve AI efficiency. SIEM tuning is the act of changing the way the system collects and analyzes data to make it more accurate and reduce false positives. Some steps used in SIEM tuning include adjusting detection rules, modifying alert thresholds, enabling data correlation, and monitoring activity.
- Run routine tests. Regular audits allow you to ensure the system is functioning properly and identify areas for improvement. Penetration testing and vulnerability assessments are important to ensure your security system is prepared to handle modern threats.
- Understand the limits of the system. At the end of the day, SIEM software is a tool designed to be overseen by human experts alongside other cybersecurity tools. Qualified cybersecurity personnel is still needed to properly monitor the system and maintain routine updates.

Advanced Tactics for Email Security
Hackers are aware that most businesses depend on email as a way to communicate globally and instantly transmit important documents. Unfortunately, this makes it an attractive target. Email security is the protective procedures and techniques that cover email accounts and the communications shared through them. Your email security plan should include the use of tools in your email platform and services from your cybersecurity vendor. It's important to recognize that email is not automatically secure. These tips can help you avoid the many modern cyberattacks that begin with an email.
- Train employees. 82% of breaches involve the human element. Email provides hackers with a way to interact with humans in hopes of being invited into the system. Employee training for email security best practices is essential to avoid the dangers of phishing and other socially based attacks.
- Always use multi-factor authentication (MFA). This simple process is one of the best ways to avoid impersonation attacks or those that utilize stolen credentials. MFA is the use of 2 or more forms of identification to gain access to a system. This can include verification codes, one-time passwords, facial or fingerprint recognition, security key, etc.
- Develop and enforce email security regulations. Businesses are typically optimized for convenience, but that shouldn't compromise security. Develop policies for creating strong passwords, separating personal and business email use, downloading and sharing documents, and information sharing.
- Don't depend on default settings. For ease of use, most email functions aren't set at the highest level of security. Change default settings to enable MFA, disable auto forward, and disable automatic downloads.
- Invest in a cybersecurity solution that includes email security software. A comprehensive cybersecurity solution like extended detection and response (XDR) monitors and protects your email platform with the same tools that keep the rest of your network safe.

Advanced Tactics for Endpoint Detection and Response (EDR)
The growth of IoT and OT devices alongside increased remote work means that all networks have considerably more endpoints to protect. Endpoints often have low barriers to access, making them a valuable target. Endpoint detection and response (EDR) is the system that collects data and detects attacks on your network's endpoints. These tips can help you make the most out of your EDR solution.
- Begin with proper configuration. Properly optimize your EDR system to collect relevant information, including devices and sensitive information. Consider the assets you want to protect, types of attacks to monitor, and how you can rapidly respond to attacks.
- Conduct continual tuning for consistent accuracy and improvement. Tuning and refining your EDR system will help eliminate false alerts and ensure your EDR solution is continually updated to reflect new devices as your system grows. It also allows you to take advantage of new features as vendors add them.
- Perform routine testing. To eliminate potential vulnerabilities and address evolving threats, it's essential to conduct routine tests on your EDR system. These might include penetration tests and vulnerability scans.
- Invest in an AI-powered EDR solution. Automated incident response combines EDR response with manual tools for immediate action when a threat arises. Properly configured ML will allow the system to choose between guided remediation, automated incident response, and managed threat response depending on the level and type of threat.
Advanced Tactics for Network Detection and Response (NDR)
While the loftiest goal is to keep all potential threats out of your network, some attacks will get past your perimeter defenses. Network detection and response (NDR) is the security solution that helps your organization detect and respond to threats on your network in real-time. NDR collects data from various sources to monitor traffic patterns, user activity, and the devices on your network. These tips can help you ensure your NDR system works effectively to detect and respond to malicious activity on your network.
- Choose carefully. It's important to choose an NDR security solution with features designed to protect the types and amounts of data used in your company.
- Ensure compatibility. Since NDR is designed to monitor the traffic taking place on your network, it's essential for the software to integrate seamlessly with the apps and platforms used by employees at all levels.
- Know your assets. You can't protect devices or information you don't know about. An organization must identify the assets they own and know where its data lives to deploy effective NDR.
- Keep vulnerabilities at bay. Perform routine vulnerability scans to note relevant risks to your network and improve your cybersecurity posture.
Advanced Tactics for Threat Intelligence
Threat intelligence is the data that is collected, processed, and analyzed to identify existing or emerging threats that compromise the networks of businesses and individuals. However, collecting and reviewing a large amount of unstructured data can quickly become overwhelming. These tips can help you determine the structure you need for the most effective use of CTI.
- Select your sources with care. Not every threat is relevant to your organization. By using a system that filters data by industry, network environment, and infrastructure, you can eliminate excess information to make analysis easier and more effective.
- Use tools that eliminate manual tasks with AI. A threat intelligence platform that automatically ingests and normalizes data can add context to threats and help analysts prioritize high-value threats.
- Make data actionable with the right tools. Integration is key here too. When your CTI system triggers automatic response actions, you can develop automated proactive protection as well as response capabilities like quarantining threats.
- Understand the value of real-time, actionable crowd-sourced information. Reputable cybersecurity vendors have access to information that businesses can't gather on their own. For instance, CTI from BitLyft utilizes threat information from all users and clients, along with outside sources, to validate threats as real and useful. When threats are recognized, each client is automatically updated with proactive protection.

Advanced Tactics for Security Automation
Automation in cybersecurity reduces attacker dwell time, halts malware, and improves response time. Security orchestration automation and response (SOAR) refers to technologies used alongside human actions to define, prioritize, and drive incident response activities. These tips can help you get the most out of SOAR tools used to protect your network.
- Identify security automation goals. Learn the pain points of your data analysts, including boring or unproductive tasks. This knowledge can help you identify use cases for automation. Consider how automated workflows can decrease response times and address security gaps.
- Integrate with other technologies. SIEM and SOAR work closely to create the most effective detection and response system. SIEM automatically logs activities and flags abnormal behavior. When it's connected to SOAR, automated responses can be immediately triggered to stop threats anytime day or night.
- Measure response times and make changes as needed. Response time is critical in reducing the impact of a breach. To make the most of speed provided by automated incident response, track changes as new use cases and workflows are added to the system.

Advanced Tactics for Threat Hunting and Investigation Tools
Threat hunting is the process of proactively seeking out vulnerabilities and active threats that may have been missed by other measures. Human threat hunters learn the tactics, techniques, and procedures used by attackers. The automated tools in your cybersecurity stack also play an important role in threat hunting. These tips can help you improve automated threat-hunting procedures.
- Invest in tools that automate actions based on attacker TTPs. When actions are based on known threat vectors, professional threat hunters have fewer tasks to complete. For example, SIEM software takes actions based on the MITRE ATT&CK framework.
- Consider the value of a managed security package. Managed cybersecurity solutions leverage cloud-based tools along with the assistance of professional analysts in an off-site SOC. This combination provides businesses with additional crowd-sourced information and a way to address staff shortages.
Advanced Tactics for Backups
In the event that data is destroyed, backups can save significant time and money in the recovery process. Creating a backup is the act of depositing your data in a separate, secure location away from your devices where it can be retrieved when necessary. In some cases, backup is the only method of safely retrieving data. These tips can help you utilize backups.
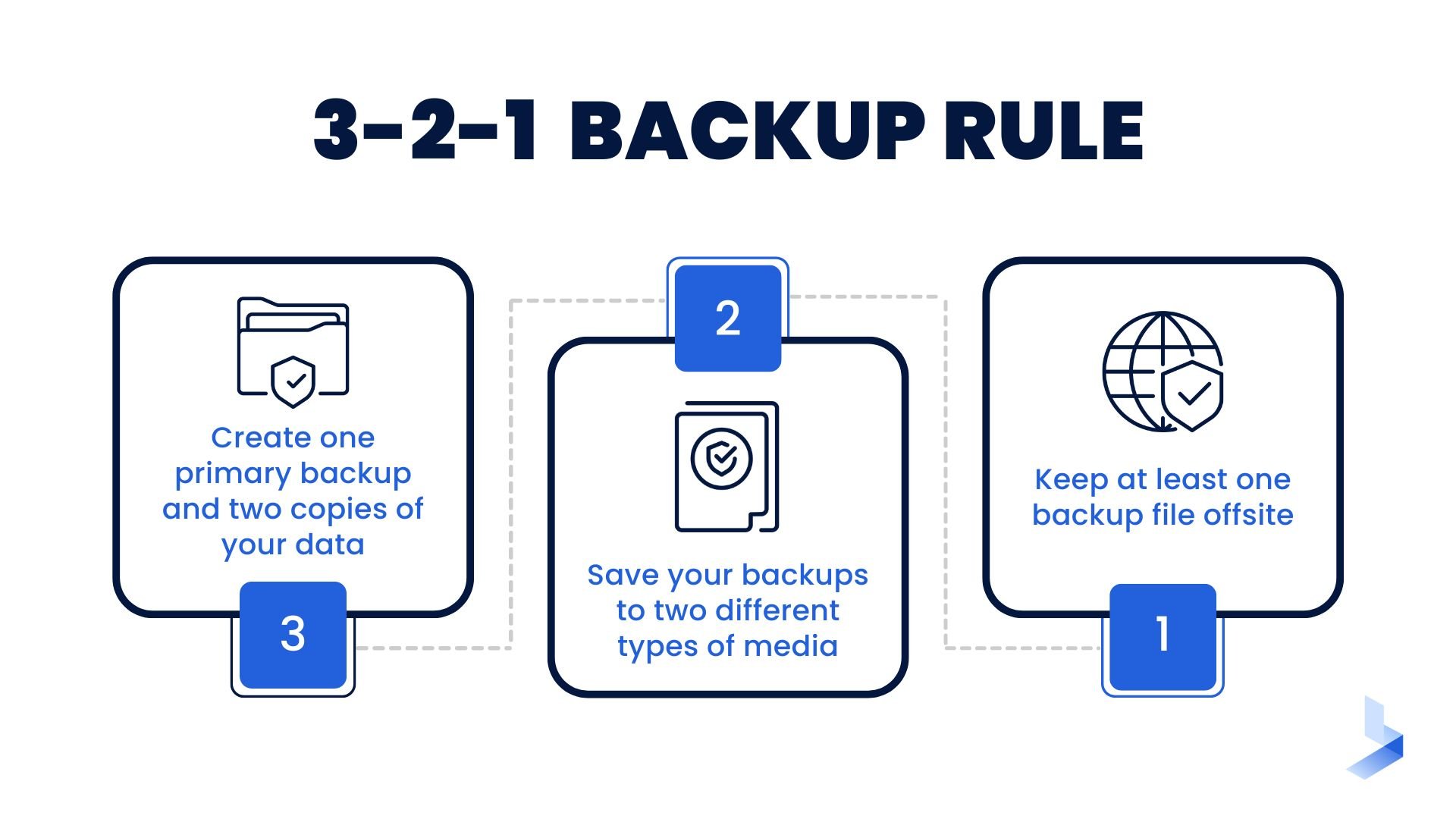
- Use the 3-2-1 backup rule. The process is completed as follows:
- 3. Create one primary backup and two copies of your data
- 2. Save your backups to two different types of media
- 1. Keep at least one backup file offsite
- Use a third-party backup program. Your computer's backup service might not be effective during an attack that shuts down network devices. When you hire a third-party organization to take care of your backups, you can take this task out of the hands of your IT or cybersecurity team.
- Use cloud storage. Cloud service providers usually offer encryption services to keep data secure while it is stored safely in the cloud.
- Test backups regularly. To ensure backups will work in the event of a successful attack, restore your backups to a test environment and check that all of your data can be accessed as expected.
Advanced Tactics for Gap Analysis
An IT security gap analysis refers to an in-depth review that helps organizations determine the difference between their current security posture and goals such as improved cybersecurity or industry compliance. To effectively identify security risks and vulnerabilities, use these tips for successful security gap analysis.
- Use an industry-standard framework. A standard framework provides baseline best practices to measure and compare against your own security practices. Industry-standard frameworks, like NIST, are often used in compliance regulations, allowing companies to reach 2 goals at once.
- Consider a third-party gap assessment. Third-party cybersecurity providers have considerable experience performing security gap analysis. By hiring a professional team, you can get a professional outside perspective on your organization's security practices.
- Perform gap assessments on third-party apps and platforms. Popular platforms and apps are often targeted by cyber attackers since they're used by so many businesses. Conducting a gap analysis on these tools will help you determine whether your business tools make your network more vulnerable.
When it comes to cybersecurity solutions, more isn't always better. In fact, using too many cybersecurity solutions can create too much noise in your environment and make it difficult to achieve complete visibility. Integration is one of the most effective ways to develop a seamless cybersecurity system that provides timely detection and response actions to keep your network safe from modern threats. Managed services take these services a giant step forward by adding the assistance of an off-site SOC. If you're confused about how to make the most out of your cybersecurity solutions, the BitLyft team can help. Get in touch to learn more about comprehensive cybersecurity that combines the best of modern tools and cybersecurity professionals.

