Avoid the Perils of a Whaling Phishing Attack

 By
Emily Miller
·
7 minute read
By
Emily Miller
·
7 minute read
Social engineering attacks can be a major concern for businesses and individuals since they prey on the vulnerabilities of people instead of security systems. Still, not all social engineering attacks are created equal, and some attacks directly target businesses. Whaling phishing attacks (or whaling attacks) are phishing attacks with a specific target. As you might have guessed by the name, these attackers are baiting their hooks for a bigger catch. Whaling phishing attacks target C-level or senior executive employees.
By targeting high-level employees within an organization, attackers can wield more power and expect to receive higher gains. Yet, to succeed in such an attack, the perpetrator must research extensively, plan diligently, and operate seamlessly. The resulting attack can be well-crafted and particularly hard to detect. As a senior executive or C-level employee, it's vital to understand how to avoid these discreet and well-targeted attacks. This guide will help you understand exactly what whaling phishing attacks are, how to identify them, and how to protect yourself from falling victim to these attacks.
What Are Whaling Phishing Attacks?
Whaling is a sophisticated spear phishing attack where threat actors target high-level employees directly or masquerade as them to deceive others. The attacks target C-level employees and executives with the goal of gaining access to high-level information or stealing large sums of money. Like other social engineering attacks, whaling attacks rely on deception to persuade a target to take an action that will jeopardize the network.

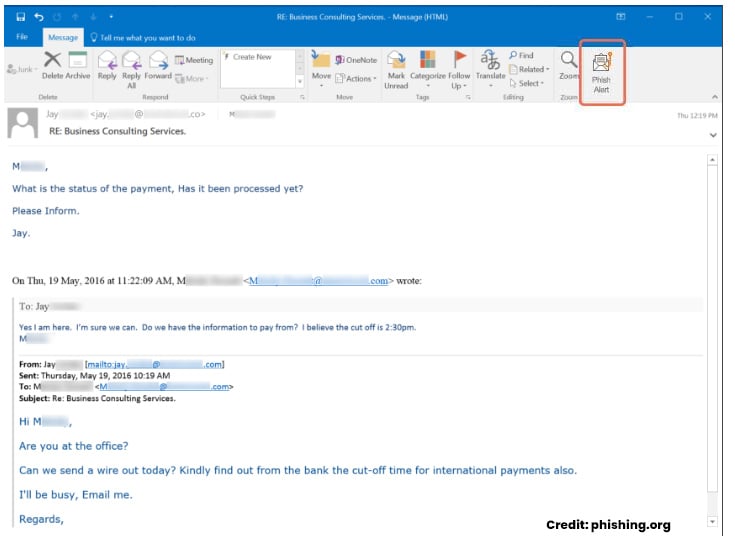
A whaling attack may come in the form of a phishing email or other deceptive communication. A scammer will conduct extensive research to learn more about the person they're impersonating and the target while planning the attack. For example, the attacker is likely to glean information from social media and other public sources. They may also engage in physical social engineering, like visiting a restaurant or coffee shop known to be popular among company employees. They may even conduct lower-level phishing attacks to learn more information that could assist in planning their true objective (the whaling attack).
When the attack is launched, it will appear to come from a trusted source. It will mirror the conversation style of the source. It will be convincing. A whaling email or even a series of texts will contain enough personal details or references to seem familiar. The request may include a link that leads to a false website or instructions that will compromise sensitive data like payroll information, tax data, or bank account numbers. Another form of attack might be a short request to make a payment to a vendor the company already works with while the attacker is waiting to intercept the payment.
How to Identify a Whaling Phishing Attack
High-level employees are more likely to be educated about the dangers of phishing attacks and familiar with the signs. Attackers are aware of this likelihood. Although it may seem like an unnecessary effort to launch such an attack, attackers take the time to prepare for a whaling phishing attack in anticipation of a high payoff. As a result, a whaling attack is much harder to recognize than a standard phishing attack. However, by knowing the signs of an attack and some tactics used in these attacks, you are less likely to become a victim if one lands in your inbox.
Whaling Red Flags
- Request Sensitivity: The goal of a whaling phishing attack is to complete a significant objective. To accomplish this, the attacker will have to include a request that deserves a look. For instance, the request may be for a wire transfer or to share sensitive data.
- Urgent Language: The request may suggest that the request needs to be carried out in a certain time frame to prevent a penalty like late payment or slowed shipment. It may include flags in the subject line like urgent or important.
- Domain Discrepancies: Hackers can often find convincing ways to spoof a known domain so that it looks practically identical to the original without close examination. Watch for the use of two lowercase letters in place of one. For example rm instead of m or vv in the place of w.
- False Familiarity: Remember that an attacker has conducted extensive research in an effort to deceive a high-level employee. Familiarity that seems real can be easily falsified with this type of research. When you consider that photos of recent events, descriptions of lifestyles, and even pets can easily be found online, it could be easy for a hacker to know just enough about you to make you feel comfortable. Another example of this is referring back to a recent meeting or event.
Examples of Whaling Phishing Attacks
Threat actors may combine several different tactics to carry out a successful whaling phishing attack. Phishing emails are the most common vector for the actual request, but many other social engineering tactics may be used to carry out the full-scale attack.
- BEC to Impersonate a Company CEO: In some whaling attacks, the hacker directly impersonates the CEO or other executive employee to build a sense of authority in requests to employees within a company. For example, an email targeted at a senior-level HR professional might request updated payroll information, or correspondence to the finance department may link to a website to make a payment. Employees may be less likely to think these requests are false and comply with the authority figure they're familiar with.
- Funds Transfer Request to High-Rank Employee: A funds transfer is one of the fastest ways for a cyberattacker to get paid. By supplying a seemingly authentic request and a believable account number, the request can be quickly met. For example, an attacker can impersonate a company partner or high-ranking employee to request a funds transfer for a seemingly legitimate reason. The request is likely to be brief and replicate the conversation style of the trusted colleague.
- Whaling Email with a Phone Call: This approach has a verification neatly built into the attack to add credibility. The attack begins with a whaling phishing email that includes a specific request. Shortly after sending the email, the attacker reaches out to the target with a call to confirm the request. This is designed to add an extra layer of trust, which is exactly why you shouldn't trust it.
Tips for Protecting Yourself from a Whaling Phishing Attack
At its core, whaling is a sophisticated phishing technique. While these attacks are more difficult to detect, many of the preventative measures that help you avoid phishing attacks can help you protect yourself from whaling attacks. Like other social engineering attacks, whaling depends on manipulation. As a result, preventative measures are often the best form of protection.
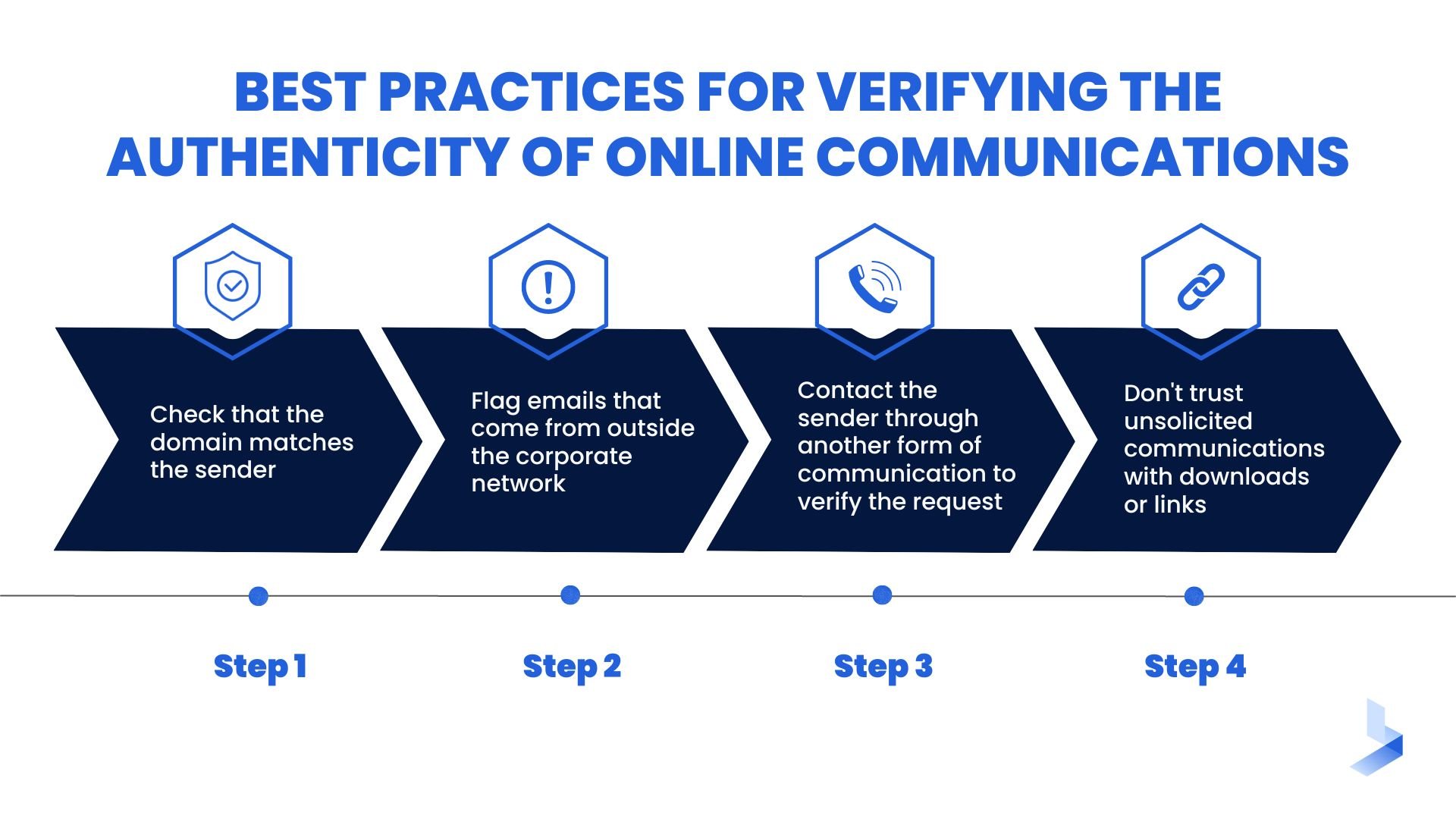
Best Practices for Verifying the Authenticity of Online Communications
Whaling attacks usually often occur through online correspondence to limit the level of deception required by the attacker. By carefully examining sensitive requests you receive online, you can avoid falling victim to an attack. Take these steps to verify the authenticity of your request before taking action that might reveal sensitive information or assist in the theft of corporate finances.
- Check that the domain matches the sender. A misspelled or hidden domain name is one of the easiest ways for an attacker to make contact with a target. When an email contains a sensitive request or suspicious language, take a moment to examine the domain name closely.
- Flag emails that come from outside the corporate network. Most phishing attacks are coming from outside your business network. By assuming all external emails have the potential to be a threat, you can give extra attention where it's needed most. When emails are automatically categorized, you can also help weed out hard-to-recognize misspellings.
- Contact the sender through another form of communication to verify the request. Any sensitive request within a business deserves a second look. If you get a request that seems out of place, simply take the time to reach out for verification.
- Don't trust unsolicited communications with downloads or links. Any link can lead to a false website and every download could include malware. This approach is part of a zero-trust security mindset that can help protect your business against many types of cybersecurity attacks. Normal business correspondence shouldn't include links or downloads the user isn't expecting.
Strategies for Safeguarding Sensitive Information and Accounts
Placing safeguards on sensitive information and accounts can help you stop whaling phishing emails from reaching their targets. Certain techniques can also help you avoid data loss when an attack occurs. Take these steps to safeguard sensitive information and accounts.
- Use multi-factor authentication (MFA) on all accounts.
- Create and enforce organization-wide policies on sending and receiving sensitive files.
- Invest in strong email gateway protection that features spam filtering and anti-malware programs.
- Use high-level privacy and security restrictions on all social media accounts to avoid leaving a treasure trove of information for potential hackers.
- Utilize high-quality email scanning and filtering technology to scan links and attachments in an email and prevent users from accessing them.
What to Do If You Fall Victim to a Whaling Attack
Even with a strong defense in place, it can be easy to fall victim to a whaling phishing attack. If you think you're the target of a whaling attack, there are steps you can take to minimize the damage.
Steps to Minimize Damage and Protect Yourself
- Disconnect your device from the network and internet to avoid any malware from downloading or spreading.
- Alert your company immediately and discuss next steps with IT professionals.
- Scan your computer and organizational network for malware or viruses that may have been downloaded as part of the attack.
- Change passwords and login credentials to avoid further damage.
- Report the attack to the Federal Trade Commission, CISA, and the Anti-Phishing Working Group to contribute to ongoing cybersecurity intelligence.
Resources for Recovering from a Whaling Phishing Attack
Recovery from a whaling phishing attack depends heavily on how quickly you recognize the attack and react to it. How you report the attack to relevant authorities may have the most impact on your recovery efforts.
- If the attack includes organizational funds, contact the relevant bank to inquire about resources for attack recovery.
- Contact law enforcement for immediate action to potentially freeze funds or track transfers.
- Contact the Federal Trade Commission.
- Contact the FBI Internet Crime Complaint Center.
- Consult a professional cybersecurity team.
Avoid Becoming the Highlight of a Whale Tale with Layered Cybersecurity
Whaling phishing attacks are particularly hard to detect. Unfortunately, they are also targeted at members of any company that are expected to know about such dangers and take a pivotal part in protecting the company. As a result, these attacks can be particularly damaging to the victims they target. The financial damage alone can be catastrophic. However, the reputational damage can be even worse.
Cyberattacks are always evolving in sophistication. Whaling phishing attacks target organizations in every industry and are carefully researched and planned down to the last detail to ensure success. As a result, they can be particularly easy to fall for. A well-crafted whaling attack can look identical to legitimate communications. It can even include correspondence that appears as though the request has been fully vetted and verified. However, you should always go the extra mile to make an active confirmation yourself.
A multi-layered approach is the best way to avoid the perils of social engineering attacks like whaling phishing attacks. When your organization applies a zero-trust approach to protecting accounts and data and utilizes highly technical tools along with trained professionals to implement highly effective security protocols, you can prevent many advanced attacks from becoming successful. If you're unsure of your organization's ability to detect and defend against whaling phishing attacks, the experts at BitLyft can help. These attacks can have catastrophic effects on a business. Learn how you can have the tools and expertise to prevent them before you become a target. Contact us today.
Download a Free Incident Postmortem Template