What is Social Engineering? Tips for Preventing Manipulative Tactics

 By
Emily Miller
·
8 minute read
By
Emily Miller
·
8 minute read
As technology continues to advance, so do the tactics used by hackers and scammers to gain access to sensitive information and systems. One of these evolving tactics is social engineering. Social engineering attacks, which are often used in combination with other malicious activities, are one of the most prevalent threats to organizations and individuals alike. In fact, research shows that approximately 98% of cyberattacks rely on social engineering.
With such an influx of threats, it’s important that individuals and organizations protect themselves from these manipulative tactics. In this guide, we’ll explore some of the most commonly employed social engineering scams and provide best practices for protecting yourself from their manipulative tactics.
What is social engineering?
Social engineering is the use of psychological manipulation and deception to influence individuals or groups to divulge sensitive information or to perform actions that may not be in their organization’s best interest. It is one of the most common tactic used by cybercriminals to gain access to sensitive information, such as login credentials or financial information and was responsible for 255 million attacks in the first six months of 2022 alone.
Social engineering attacks are carried out through a variety of means including email, phone calls, and text messages. Attackers use techniques known as phishing, pretexting, and tailgating to gain access to confidential information like credit card numbers, or systems. Many cyber criminals rely on social media and other online platforms to collect valuable information about their victims.
The goal of a social engineering attack is to manipulate people into providing confidential information or performing an action that could be used to gain unauthorized access to an organization. Attackers use various tactics to deceive victims and gain access to confidential information or systems.

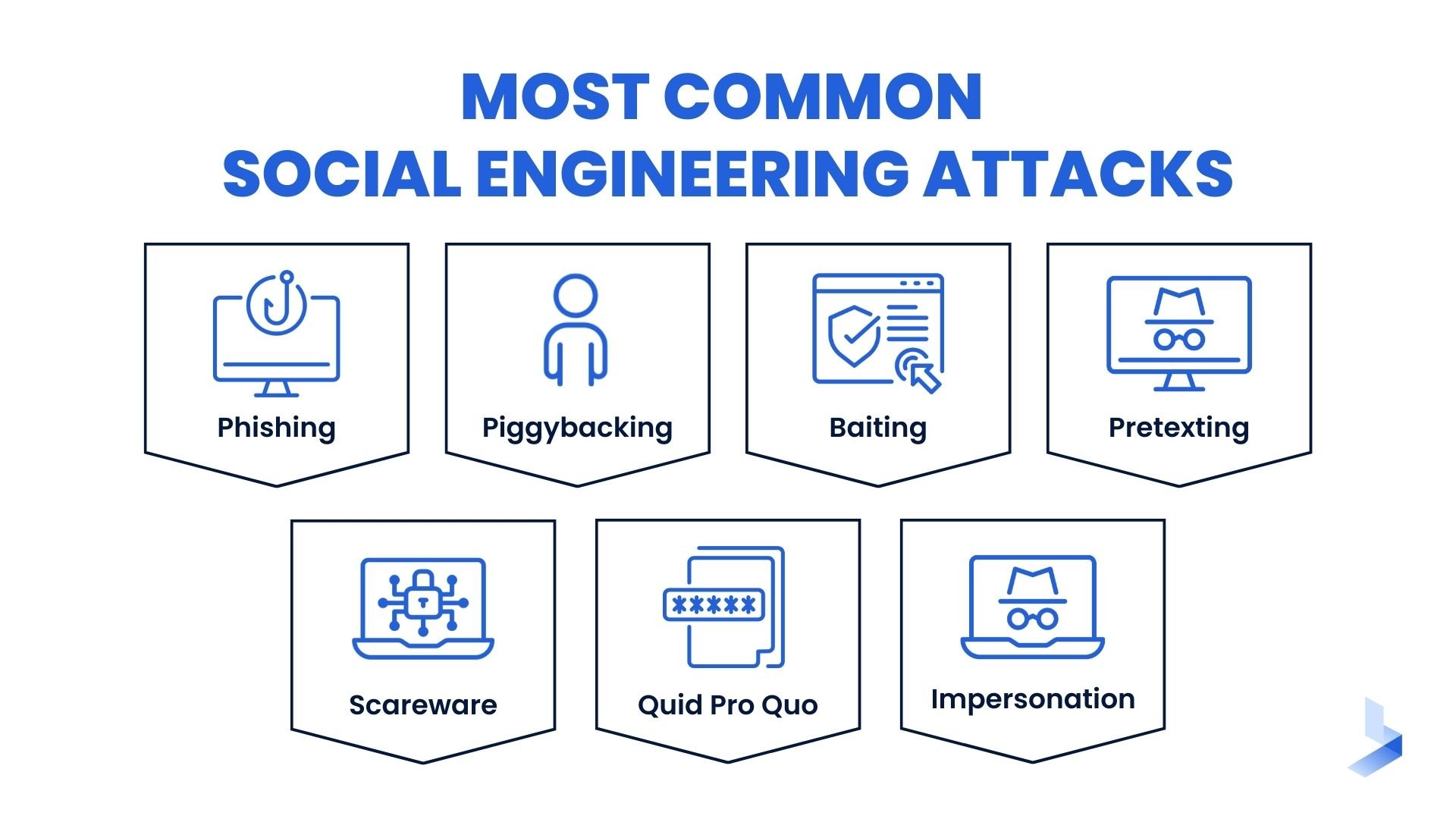
Types of social engineering attacks
When it comes to protecting yourself from social engineering attacks, the most important preparation you can have is awareness. Social engineering attacks can take many forms and it’s important to familiarize yourself with the way each functions. In addition to knowledge of the most common techniques, you should also know the warning signs of a social engineering attack. Each type of attack has its own set of risks and can be used to gain access to confidential information or systems. In the following section, we’ll break down some of the most common social engineering attacks and provide tips to protect your organization from attack.
Phishing
What it is: One of the most common types of social engineering attacks, phishing, involves the use of fake emails or websites to trick individuals into divulging sensitive information or performing actions that may not be in their best interest. These attacks often involve creating a sense of urgency or fear in order to convince the victim to take the desired action.
Phishing attacks are often disguised as legitimate emails or websites, and may appear to be from a trusted source, such as a bank, a government agency, or a well-known company. The goal of the attack is to convince the victim to click on a link or enter sensitive information, such as login credentials or financial information.
Prevention tips:
- Be cautious of unexpected emails, especially those with urgent requests or that contain links or attachments.
- Verify the sender's identity before responding to an email or clicking on any links. You can do this by hovering over the sender's name to view their email address or by contacting the sender directly through a trusted means of communication.
- Use a spam filter to block phishing emails and mark them as spam.
- Don't share personal or financial information via email.
- Use strong, unique passwords for all of your accounts and enable two-factor authentication whenever possible.
- Keep your operating system and antivirus software up to date.
- Be aware of the risks of using public Wi-Fi networks and be cautious when accessing sensitive information on these networks.
Tailgating
What it is: Tailgating, also known as "piggybacking," is a type of social engineering tactic that involves following someone into a secure area without proper authorization. This can be done in person, such as by following someone through a door into a secure office building, or remotely, such as by accessing a secure network through an open connection.
Tailgating relies on the victim's trust or willingness to allow someone else to enter a secure area. It is often used by attackers to gain unauthorized access to sensitive information or systems.
Prevention tips:
- Use turnstiles or other physical barriers to control access through secure doors.
- Use security cameras to monitor access points and identify tailgaters.
- Train employees to be aware of tailgating and to challenge anyone who tries to follow them through a secure door.
- Implement a "buddy system" in which employees must present their identification and be accompanied by a colleague to enter certain areas.
- Use electronic access control systems, such as key cards or biometric scanners, to verify the identity of individuals before granting access to secure areas.
Baiting
What it is: Baiting is a type of social engineering tactic that involves using a promise or reward to entice an individual to divulge sensitive information or perform a certain action. The promise or reward is often disguised as something desirable, such as a prize, money, or exclusive access to something. For example, a scammer might create a fake website that offers a free vacation in exchange for personal information, or send an email promising a large sum of money if the recipient clicks on a link or provides certain information. Baiting relies on the victim's greed, curiosity, or desire for something to trick them into divulging sensitive information or performing a certain action.
Prevention tips:
- Be cautious of offers that seem too good to be true.
- Don't click on links or download attachments from unknown or untrusted sources.
- Don't disclose personal or financial information in response to an unsolicited request.
- Use strong, unique passwords for all of your accounts and enable two-factor authentication whenever possible.
- Keep your operating system and antivirus software up to date.
- Be aware of phishing scams that use baiting tactics and educate yourself and your colleagues about these types of attacks.
Pretexting
What it is: Pretexting is a type of social engineering tactic that involves creating a fake identity or scenario in order to gain trust and obtain sensitive information or access to systems. This can be done in person, over the phone, or online, and the fake identity or scenario is often tailored to the victim's specific interests or needs in order to increase the chances of success.
For example, a pretexting attack might involve a scammer calling someone and pretending to be a representative from their bank, asking for sensitive information such as account numbers or passwords. The scammer might also create a fake website or email that appears to be from a legitimate company, asking the victim to enter their login information or other sensitive information.
Prevention tips:
- Be cautious of unsolicited phone calls or emails, especially those that request personal or financial information.
- Don't disclose personal or financial information in response to an unsolicited request.
- Verify the identity of anyone who requests sensitive information before disclosing it. You can do this by contacting the person or organization through a trusted means of communication or by looking up their contact information independently.
- Use strong, unique passwords for all of your accounts and enable two-factor authentication whenever possible.
- Keep your operating system and antivirus software up to date.
- Be aware of pretexting scams and educate yourself and your colleagues about these types of attacks.
Scareware
What it is: Scareware is a type of social engineering tactic that involves using fear or urgency to trick individuals into taking a certain action, such as purchasing a product or providing sensitive information. This tactic is often used in conjunction with fake websites, emails, or pop-up windows that claim to detect a problem with the victim's computer, such as a virus or malware. The message will often include a sense of urgency, such as a countdown timer or a warning that the problem will get worse if not addressed immediately.
The goal of scareware is to convince the victim to purchase a product or service, such as antivirus software, or to provide sensitive information, such as login credentials or financial information. In many cases, the product or service being offered is fake or of low quality, and the sensitive information is used for fraudulent purposes.
Prevention tips:
- Don't click on links or download attachments from unknown or untrusted sources.
- Keep your operating system and antivirus software up to date.
- Be cautious of pop-up windows or messages that warn of security threats or claim to have detected malware on your computer. These may be scareware attempts.
- Don't purchase or install any security software in response to a pop-up window or message.
- If you believe that your computer may be infected with malware, use a trusted security tool to scan your system and remove any threats.
- Educate yourself and your colleagues about scareware and other types of malware, and be aware of the risks of downloading software from untrusted sources.
Quid pro quo
What it is: Quid pro quo is a type of social engineering tactic that involves offering something in exchange for sensitive information or access to systems. This tactic is often used over the phone or in person, and the offer is usually disguised as a legitimate request or a favor.
For example, a quid pro quo attack might involve a scammer calling someone and claiming to be from a technical support team, offering to help fix a problem with the victim's computer in exchange for login information or access to the computer. Another example might involve an attacker offering a reward or incentive in exchange for sensitive information, such as a gift card or a prize.
Quid pro quo attacks rely on the victim's willingness to receive a benefit in exchange for sensitive information or access.
Prevention tips:
- Be cautious of unsolicited phone calls or emails that offer something in exchange for sensitive information or access.
- Don't disclose personal or financial information in response to an unsolicited request.
- Verify the identity of anyone who requests sensitive information before disclosing it. You can do this by contacting the person or organization through a trusted means of communication or by looking up their contact information independently.
- Use strong, unique passwords for all of your accounts and enable two-factor authentication whenever possible.
- Keep your operating system and antivirus software up to date.
- Be aware of quid pro quo scams and educate yourself and your colleagues about these types of attacks.
Impersonation
What it is: Impersonation is a type of social engineering tactic that involves pretending to be someone else in order to gain trust and obtain sensitive information or access to systems. This tactic can be used in person, over the phone, or online, and often involves creating a fake identity or stealing the identity of a legitimate person or organization.
For example, an attacker might send an email pretending to be a colleague or supervisor, requesting sensitive information or access to certain systems. Another example might involve an attacker calling a company and pretending to be a representative from a trusted vendor, requesting access to sensitive information or systems.
Prevention tips:
- Be cautious of unsolicited phone calls or emails, especially those that request personal or financial information.
- Don't disclose personal or financial information in response to an unsolicited request.
- Verify the identity of anyone who requests sensitive information before disclosing it. You can do this by contacting the person or organization through a trusted means of communication or by looking up their contact information independently.
- Use strong, unique passwords for all of your accounts and enable two-factor authentication whenever possible.
- Keep your operating system and antivirus software up to date.
- Be aware of impersonation scams and educate yourself and your colleagues about these types of attacks.
How to respond to a social engineering attack
If you suspect your organization has been the target of a social engineering attack, it should take the following steps to respond and mitigate the risk of further attacks:
- Identify the source of the attack and gather as much information as possible about the attack, including the type of attack, how it was delivered, and what information or access may have been compromised.
- Notify all relevant stakeholders, including management, IT staff, and employees, about the attack and instruct them on how to protect themselves and their systems.
- Change any compromised passwords and implement additional security measures, such as two-factor authentication, to prevent further attacks.
- Review and update security policies and procedures to address any weaknesses that may have contributed to the attack.
- Monitor systems and networks for any signs of further attacks or malicious activity.
- Consider engaging a cybersecurity professional to conduct a comprehensive review of the organization's security posture and to provide recommendations for improving security.
By taking these steps, an organization can respond effectively to a social engineering attack and help to prevent future attacks.
Conclusion
Social engineering attacks will no doubt continue to threaten organizations of all sizes. In addition to being aware of the risk and educating yourself on the various types of social engineering attacks, it’s important to practice good cyber hygiene. If you’re unsure of how protected your organization is from a social engineering attack, we recommend having your security posture professionally assessed. With the right security measures in place and a good understanding of how to protect yourself and your organization from social engineering attacks, you can help protect against cyber threats and keep your data safe.
To help organizations get started, we’ve created a cybersecurity assessment that is free, takes five minutes to complete and provides actionable insights to immediately improve your security posture. Ready to see where your business stands? Take the assessment now.

