Unmasking Pretexting: How to Spot and Avoid a Pretexting Attack

 By
Emily Miller
·
7 minute read
By
Emily Miller
·
7 minute read
While businesses of all sizes are facing a variety of challenges in the coming year, cybersecurity remains an ongoing concern. As cyberattacks continue to grow in both number and complexity, business owners and c-suite executives are responding by bolstering cybersecurity efforts. Even with predictions of a looming recession, 65% of organizations plan to increase cybersecurity spending in 2023. This is a big step in the ongoing fight against a growing number of cyberattackers constantly targeting businesses, individuals, and even public infrastructure. Unfortunately, threat actors won't simply give up the fight. As businesses increase their security efforts, attackers constantly seek new ways to gain access to sensitive data.
.jpg?width=735&height=413&name=Cybersecurity%20spending%20in%202023%20(1).jpg)
When cybersecurity tools and methods make it more difficult for attackers to breach a network, they turn to different techniques for success. Social engineering attacks are scams that use deception to convince system users to take actions that compromise network security. Instead of trying to get past security with brute force, attackers convince system users to open a back door that allows them in. The success of social engineering attacks depends directly on the ability of the attacker to deceive a target. This is why pretexting is a particularly dangerous form of social engineering attack.
Pretexting attacks rely on research to present a believable story that will manipulate a target to take action. The more information an attacker can gather before launching the attack, the more likely the attack is to succeed. Pretexting attacks can be used to gather sensitive information, conduct a funds transfer, gain access to a network, or deploy malware. These attacks are usually extremely convincing and hard to detect. To protect yourself and your organization against these sneaky attacks, it's important to learn more about them and the ways you can avoid becoming a victim.
What is Pretexting?
Pretexting is a type of social engineering tactic that involves creating a fake identity or scenario to gain trust and obtain sensitive information or access to systems. The attack can be carried out in person, over the phone, or online and the focus of the correspondence is usually tailored to the victim's specific interests or needs.

All social engineering attacks use deception and prey on human emotions to manipulate targets into taking action. While some attacks feature wide-ranging concerns that are likely to get a response from many people, pretexting attacks are more targeted and work to deceive a specific individual. To create a convincing attack, hackers must conduct significant research. Furthermore, conducting such a targeted attack narrows down the potential victim pool. As a result, the damage from a successful pretexting attack is likely to be particularly costly.
Pretexting attacks begin with research. The attacker is likely to gather public information found online, extract information from low-level phishing attacks, learn background information by frequenting physical areas used by employees of the company, or even find ways to spend time inside the organization. The attacker will then use the information gathered in the intelligence stage to create a backstory (pretext) to establish communication with the intended victim(s).
Once a scenario is created, the attacker will launch a cyberattack in the form of phishing emails, vishing, or another communication method to gain the target's trust. The information gathered during the research stage helps the attacker appear as a trusted source so the request seems like a legitimate business transaction. For example, a pretexter is likely to use familiar terms of communication, include accurate logos and names, and form a request that is similar to that of a trusted colleague or supplier. These actions make the attack difficult to detect and more likely to succeed.
Types of Pretexting Attacks
Like other social engineering scams, pretexting attacks take a variety of forms to fit a specific organizational purpose. Some of the most common pretexting scams include the impersonation of a trusted source, investment opportunities, and convincing phishing emails.
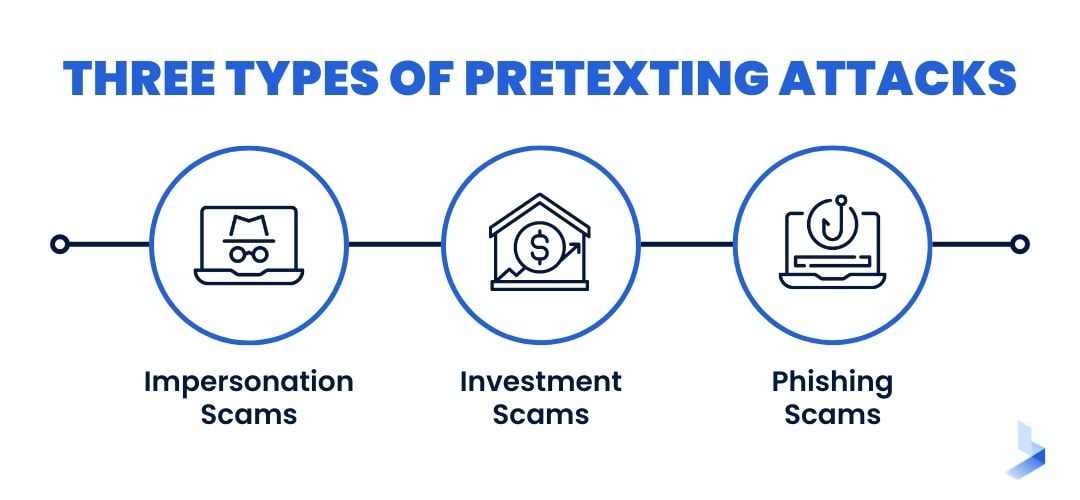
Impersonation Scams
Masquerading as someone the victim already knows is one of the most convincing ways for an attacker to gain a target's trust. To carry out an impersonation attack, the hacker will pose as someone within the same organization, a contact on social media, a supplier, or another trusted source. In most cases, the request will mirror the conversation style of the legitimate source as closely as possible. However, the undertone of the request might include urgent language to suggest the user should complete the action immediately. For example, an attacker posing as IT support might say they need to confirm account information, or a message that appears to come from the company CEO might outline a task that needs to be completed within a certain time frame.
Investment Scams
Investment scams usually target individuals directly with an offer that seems too good to pass up. These messages are frequently placed on professional or networking platforms and align with the target's interests. While a seasoned investor knows to check the legitimacy of investment opportunities, an experienced attacker will have already put provisions in place to ease doubt.
For instance, an attacker might create a website that appears legitimate and even has reviews from successful "clients". An easy payment method is likely to be available, and a convincing backstory will be put in place to provide an explanation of what upfront fees are used for. Such websites may disappear shortly after payments are received, making further communication impossible.
Phishing Scams
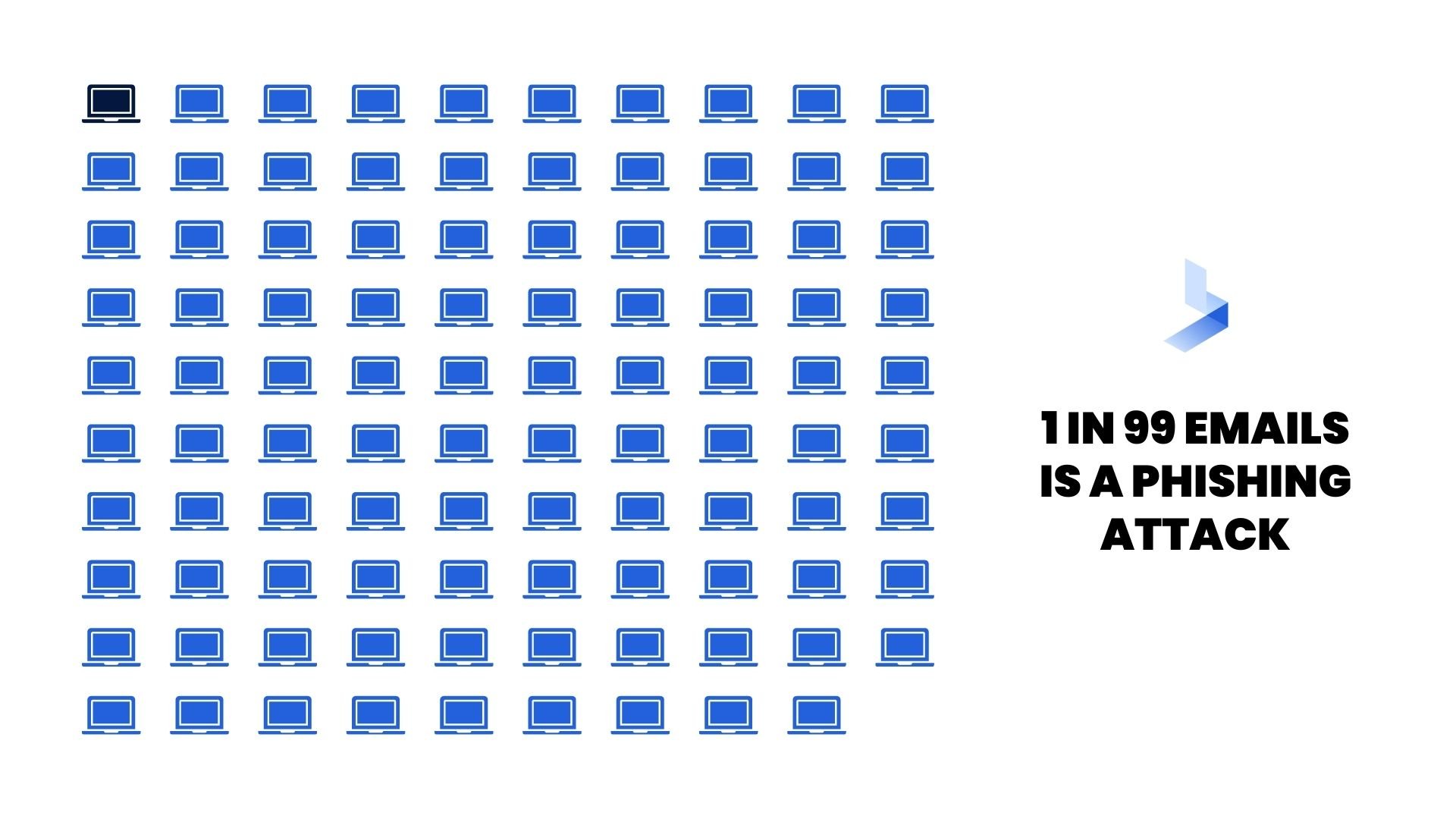
One in 99 emails is a phishing attack, making this vector one of the most commonly used methods of cyberattack. While some phishing emails are easy to spot, pretexting attacks often present more convincing communication in the form of an email. Since email is designed for convenient communication, an attacker can use a phishing email to send malicious links or downloads from anywhere. The attacker may use a spoofed email address or stolen credentials to masquerade as a trusted source.
A phishing scam built on information gathered for a pretexting scam can be particularly deceptive because it's more likely to contain context and conversation styles that are familiar to the target. Pretexting phishing scams are likely to include links, attachments, or an urgent request to complete a financial transfer or send sensitive documents to a trusted source.
How to Spot a Pretexting Attack
Pretexters go to great lengths to develop a story that will deceive their targets. This added effort makes these attacks more difficult to detect. However, there are certain red flags that can help you identify these scams before you become the victim of a larger attack.
- Urgent Language: While a pretexter will go to great lengths to convincingly impersonate a trusted source, they are likely to work to complete the attack as quickly as possible. To accomplish this, the request is likely to include a time frame or language like ASAP, "immediately", or "right away". The message may also include reasons why a delay is catastrophic.
- Unusual Requests: You may receive a text, email, or phone message that follows normal communication routes and conversation styles. Yet, the red flag goes up when the request is out of the ordinary. Any request that requires sensitive information, the transfer of funds, or unusual downloads should be considered suspicious.
- False Familiarity: A pretexting attack may open with casual communications like "Are you free right now?", "I need your help", or "Can you do me a favor?". The correspondence is likely to include your name or the names of people you know to create familiarity. Only after establishing trust, the attacker will reveal the request for money or sensitive information.
- Excuses to Avoid Ongoing Communication: A pretexting attack from a supervisor, executive, or CEO might include a reason why you were chosen to carry out a sensitive task as well as the reason they can't perform it themself. For example, communications from the CEO might say they're stuck in meetings all day, making the victim reluctant to make contact for verification.
- Spoofed Domains: If an attacker doesn't have access to a legitimate website, they'll be forced to send communications from an unknown email. To remain discreet, they're likely to use a similar email or URL domain. In these instances, the sender's email or a linked URL may include easy-to-miss spelling errors.
How to Verify a Potentially Dangerous Request
Pretexting attacks include extensive research that allows the attacker to masquerade as a trusted source. If possible, the attacker will take on the identity of someone with authority to avoid additional questions. While it can be intimidating to contact your superior or the company CEO for verification on an important request, it is a necessary step to avoid falling victim to a sophisticated attack. These tips can help you successfully verify a request instead of engaging in more communication with an attacker.
- Check an email or text for pretexting red flags mentioned above.
- Avoid responding to the request or taking actions like clicking links or downloading attachments.
- Contact the sender through an alternate communication method for verification. Instead of responding to the request, make contact with the legitimate source and explain the situation. Ask for verification of the original request before taking further action.
How to Avoid Pretexting
If you conduct personal or professional tasks online, it's impossible to completely avoid becoming the target of a cyberattack. However, there are steps you can take to keep your information secure and be a less willing target. Limiting the amount of information hackers are able to obtain and taking certain precautions can help you avoid the damages caused by pretexting scams.
Best Practices
Take these steps to protect your personal information and financial assets from the investigative techniques of attackers.
- Create organizational policies surrounding the limits of information employees can share on social media about their organizational roles.
- Avoid sharing personal and financial information online.
- Dispose of sensitive documents securely to avoid providing information to potential attackers.
- Educate employees about the techniques used in social engineering attacks.
- Use modern cybersecurity tools to monitor the network environment for malicious activity.
- Encourage employees to report all phishing attempts or suspicious activity.
- Create and enforce organization-wide policies regarding business communication, downloads, and document sharing.
Steps to Take if You Suspect You're a Target
Like other social engineering attacks, a pretexting attack is only successful if the target takes the intended action. While you can't avoid being targeted for a pretexting attack, there are steps you can take to avoid becoming a victim.
- Examine the email or text for red flags (like urgent language, spoofed websites, and suspicious requests) indicating an attack.
- Use zero trust policies surrounding business communications, downloads, links, and document sharing.
- Do not share sensitive information with unverified entities by email, phone, or text messages.
- Contact the legitimate sender through another communication platform to verify the request.
- Don't click on links in an unverified email or text or download attachments.
- Use authorized and trusted channels to verify your email address, phone number, or other sensitive information.
- Report suspicious correspondence to supervisors and IT professionals in your organization.
- Report all cyberattack attempts to the proper officials like local authorities and the Federal Trade Commission (FTC).
Social engineering attacks are sneaky scams that turn humans into a vulnerability to gain access to devices, sensitive information, funds, or business networks. To carry out pretexting attacks, hackers take painstaking efforts to collect a wealth of information that can be used to exploit a business or individual. As a result, these attacks are particularly hard to detect. When attackers use real information to convincingly masquerade as a trusted source, it can be nearly impossible to tell that you're the target of an attack.
To protect your personal information and your business, it's crucial to understand how to keep your personal and financial information out of the hands of hackers and how to identify these discreet attacks. Luckily, there are modern cybersecurity tools and techniques available to help you outsmart the attackers that attempt to take advantage of you. If you're concerned about your vulnerability to pretexting and other sneaky social engineering attacks, the experts at BitLyft can help. Contact us today to learn more about protecting yourself and your business against deceptive scams.


