How to prevent the top five social engineering attacks

 By
Emily Miller
·
9 minute read
By
Emily Miller
·
9 minute read
As more and more high-profile cyberattacks become headline news, businesses across all industries are becoming aware that effective cybersecurity is a necessary part of business operations. Network security is no longer a responsibility confined to the IT department. It has become an organization-wide effort that leads to improved planning and increased protection efforts. In fact, organizations around the world spent an estimated $150 billion on cybersecurity in 2021, an annual growth of 12.4%.

While cybersecurity awareness and spending are moving in the right direction, cybercriminals aren't slowing down in their efforts to breach business networks and access sensitive data. Threat actors evolve with the changing cybersecurity landscape to find new ways around more effective barriers. One of the most effective ways hackers succeed in circumventing security efforts is a new mode of attack. This is where sophisticated social engineering attacks come into play.
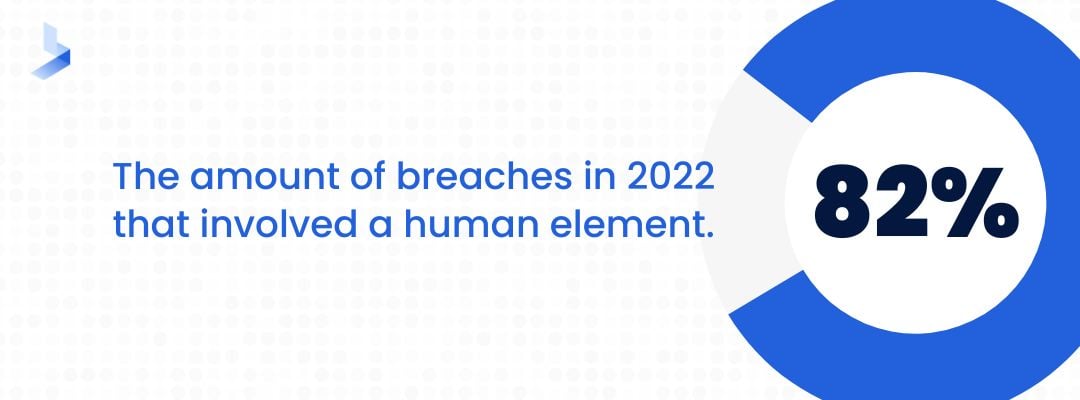
Social engineering attacks are those that target people instead of security system vulnerabilities. They are particularly dangerous because their covert nature makes them extremely hard to detect. In 2022, 82% of breaches involved the human element. While this number includes breaches caused by human errors and misuse, it highlights the number of employees that are likely to fall victim to social engineering schemes.
To avoid becoming the victim of social engineering attacks, businesses must know what to expect and how to prevent an attack before it occurs. We've identified the top 5 types of social engineering attacks as phishing, baiting, scareware, pretexting, and impersonation. This guide explores exactly what social engineering attacks are and provides more information about the top 5 types of social engineering attacks and prevention tips for each type.
What Are Social Engineering Attacks?
Social engineering describes a group of cyber attacks that use psychological manipulation to trick users into providing a hacker with an entry point. Instead of using brute force attack methods to seek and exploit system vulnerabilities, these attackers develop a false relationship with users to gain access to the network. The goal of social engineering is to gain the trust of targeted victims. This is usually achieved by masquerading as a trusted company or individual. If the manipulation works, the attacker will then ask the victim to take further action, like sharing passwords, transferring funds, or downloading files that could contain malware.

Social engineering attacks work to exploit human emotions, making them especially dangerous. Since these attacks take different forms and can use a variety of deception techniques, they are difficult to detect. As attackers become more resourceful, a variety of common social engineering attacks have emerged. To keep your business network safe, it's essential to recognize the various types of social engineering attacks and methods to prevent these attacks from reaching success.
Top Five Social Engineering Attacks
Attack Type #1: Phishing
Most people have heard of phishing attacks, but they can be very convincing and difficult to recognize. Phishing attacks are fraudulent communications that appear to come from a trustworthy source. A whopping 96% of phishing messages delivered through email, making it the number one transmission method by far. Modern phishing attacks are increasingly difficult to recognize because they use new technology to masquerade as trusted brands, reliable financial institutions, or communications from within your organization.
A phishing attack begins with a counterfeit email designed to lure a victim. The correspondence is designed to look as though it was sent by a trusted sender and usually relies on fear or urgency for a quick response. The email will likely appear remarkably similar to a legitimate company email with accurate logos and other signatures. Communication is then used to trick the victim into providing confidential personal or company information, downloading an attachment, or visiting a scam website.
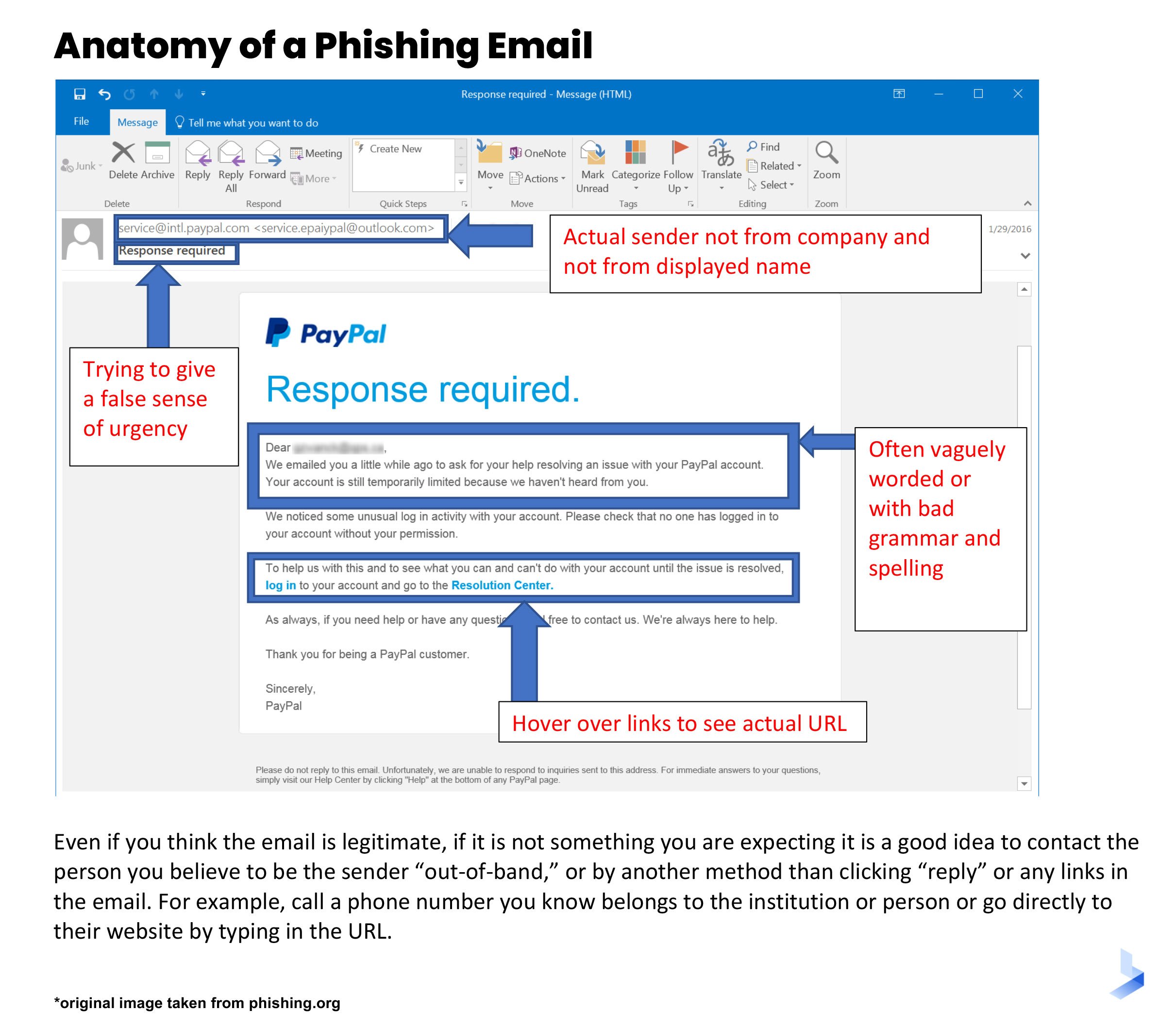
Examples of Phishing Attacks
Phishing attacks come in all shapes and sizes. Yet, most of them appear to come from reliable sources that the victim is already familiar with. These are some examples of modern phishing attacks.
- Fake Invoice Scam: Often targeted at finance departments, invoice scams usually feature an email requesting overdue payments for services already rendered. A link is often included in the email to allow the victim to view and pay the bill.
- Account Upgrade: An account upgrade scam features a realistic email from an existing company suggesting an account is about to expire. To add urgency, these emails typically represent necessary accounts like email, financial institutions, or other frequently used accounts. The email will contain company logos and instructions to act immediately to keep the account active.
- PayPal Scams: With 426 million users, PayPal is a vital tool for many people. PayPal scams are emails that include the PayPal logo and a legitimate-looking message suggesting the victim's PayPal account is closing and needs immediate attention.
- Suspicious Activity Scam: This type of phishing scam suggests the target is already likely a victim of an attack. It plays on urgency by notifying the user of suspicious activity in an existing attack.
- Google Docs Scam: An attacker using the Google Docs scam masquerades as someone the victim knows sending a document for download. This can be especially effective if it appears to come from a supervisor or colleague within a company.
- Internal Company Email: These emails often target specific victims and appear to come from a department within the victim's organization. For example, an email with a malicious attachment or link may appear to come from HR or the company supervisor or CEO.
Phishing Prevention Tips
Phishing attacks have increased by 61% in 2022, making them a major concern for businesses across all industries. So, how can you keep your business from falling victim to phishing attacks? Prevention is more effective than attempting to recognize well-crafted phishing attempts.
- Create and enforce firm organization-wide email policies regarding information sharing, links, and downloads.
- Invest in tools and services (like multi-factor authentication and email security) that stop phishing attacks from reaching their intended target.
- Educate employees about evolving phishing scams.
- Adopt a zero-trust workplace environment where verification is always required before taking action.
Attack Type #2: Baiting
Baiting attacks use false promises to entice victims to interact with some type of media. These attacks come in two forms, physical or digital. Physical attacks are the less common of the two and feature the delivery of a USB drive or CD used to pique the victim's interest. The item may be left lying on a desk or common area or delivered directly to the victim. Digital baiting attacks are far more common and can come in the form of pop-ups, emails, or other forms of digital communication. The "bait" used in these attacks may be interesting information, free products, or prize winnings.
Baiting is an efficient method for attackers because it exploits human emotions like excitement, curiosity, and greed. It also eliminates the need for the attacker to communicate directly with the victim. The goal of baiting attacks may be to gain personal information or to introduce malware into a company network.
Examples of Baiting Attacks
Since they are designed to gain the interest of victims, baiting attacks can contain any type of lure that might attract a target. However, baiting attacks are often sent to multiple targets, which can make them easier to identify. These are some common examples of baiting attacks.
- Tempting Offers: The lure of something free is one of the most common types of baiting scams. These come in the form of a pop-up or email promising anything from prize-winning to free downloadable content or discount coupons. For the victim to receive the offer, they will need to share personal information or visit a fake website.
- Malware Infected Devices: Malware-infested physical media like external hard drives and USB flash drives can be delivered in person, by snail mail, or left in common areas. They often have a title promising interesting company information.
- Online Downloads: Many websites exist to offer free downloads for products like music, movies, and games for free. Such websites are illegal and often exist solely to deliver malware.
Baiting Prevention Tips
Baiting attacks are only successful when targeted users take the bait. Tactics that block baiting messages and educate users are best to help organizations avoid such attacks.
- Employees at all levels should be educated frequently about modern baiting attacks. Companies can provide information about common attack types and organization-wide communication techniques to help employees recognize suspicious behavior.
- Set and enforce organization-wide policies defining the use of company devices. Since many baiting attacks target personal desires, prohibiting the use of devices for personal use can limit how frequently employees respond to offers.
- Invest in modern technology and professional services designed to identify and block bait attacks. Artificial intelligence (AI) based software can recognize compromise indicators of many baiting attacks and block messages from reaching targets.
Attack Type #3: Scareware
Most often a precursor to ransomware, scareware combines fear with urgency to encourage a user to click for an immediate resolution. Scareware often comes in the form of a popup that suggests the user's device has a virus or has been compromised with malware. Since the popup appears to come from a legitimate security software provider or the computer's operating system, it's particularly convincing.
Scareware pop-ups typically use urgent language, capitalization, and exclamation marks to add urgency. A timeline may be included to convince the victim to act quickly. If the user clicks on the message, they'll be redirected to a fake website to repair the supposed problem with fake antivirus software. While the download may appear to be effective, it likely contains malware and provides no actual protection or remediation. It's important to note that the close or X buttons on a scareware pop-up are often phony, and can lead to the download of malware if used.
Examples of Scareware
In most cases, scareware uses popups that state a device is infected. The message may appear to come from a well-known cybersecurity provider or a convincing antivirus name. Known scareware programs include:
- WinAntivirus
- The SpyBot
- WinFixer
- DriveCleaner
- Antivirus360
- PC Protector
- Mac Defender
Scareware Prevention Tips
Like most social engineering attacks, scareware depends heavily on the user's response. Avoidance of any interaction with the popup window is crucial to prevent an attack.
- Educate all users to avoid the click reflex. Clicking on a scareware popup can lead to immediate consequences such as redirection to a fake website or a malware-infected download. Instead of clicking on a close or X button within the popup, close the browser window entirely to avoid accidental downloads.
- Use up-to-date software and browsers throughout your company and ensure all network users are familiar with company platforms and security providers.
- Utilize technology like pop-up blockers and URL filters to prevent fake anti-virus messages from reaching users.
- Don't ignore scareware popups. Devise a policy to ensure all scareware attempts are reported, and immediately disconnect affected devices from the internet until proper legitimate scans and procedures can ensure the network is not compromised.
Attack Type #4: Pretexting
During a pretexting attack, an attacker uses a story (or pretext) to convince the target they are a trusted contact. For instance, an attacker will address the target by name, masquerading as a trusted co-worker or service provider. A threat actor may pretend to be an IT professional, HR staff member, or someone from the finance department. To be effective, this type of attack usually requires the hacker to find specific information through phishing, email compromise, or other information-gathering methods.
During the attack, threat actors typically ask victims for information needed to confirm identity or attempt to trick the victim into an action that exploits organizational weaknesses. It's common for attacks to be targeted at C-level executives or employees with more extensive privileges.
Examples of Pretexting
Pretexters use a variety of tactics and techniques to gain the trust of their targets. These attacks can be more difficult to detect since they are directly targeted at a specific victim and include valid company information gleaned from other illegal activities.
- Impersonation: An attacker may pretend to be a coworker, company CEO, client, or vendor to gather information, gain network access, or carry out malicious acts.
- Piggybacking: Hackers interrupt an already active session between a victim and a trusted source to gain access to controlled access channels.
- Tailgating: A physical tailgating attack is one where an attacker gains access to a building or restricted area by following a trusted individual inside. A digital attack is one where a hacker uses stolen information to access a restricted network.
Pretexting Prevention Tips
Successful pretexting usually relies on adequate information to be convincing. This can make these attacks seem particularly believable. In many cases, preventing a pretexting attack will rely on stringent verification methods.
- Educate users on the ways pretexters gather information and what a pretexting attack might look like in your organization.
- Use tools like DMARC and AI-based email analysis to identify and block spoofed email addresses.
- Create and enforce policies describing zero-trust methods for identity verification.
Attack Type #5: Impersonation
An impersonation attack is an attempt to gain unauthorized access to information systems by masquerading as authorized users. Impersonation attacks begin with the gathering of information about the organization and intended targets. Most impersonation attacks are carried out by email or other expected contact methods that commonly occur within the organization. Impersonators gain the trust of an employee, then ask for personal information or require actions like downloading files or transferring funds.
Examples of Impersonation
Impersonation can come in many forms, but email is the most common. While impersonation attacks are sometimes carried out through a compromised email account, there are other ways impersonation attempts can go easily overlooked. These are some of the most common examples of impersonation.
- Cousin Domain Attack: An attacker creates a website that looks nearly identical to a trusted website like the victim's bank or that of a vendor. When the similar link is added to an email, it's easy to miss the difference.
- Impersonation of a Colleague or Company Authority Figure: When an attacker makes contact pretending to be the company CEO or someone in a high-level department, victims might be coerced into providing company information.
- Impersonation of a Vendor: By posing as a third-party vendor, like an IT or cybersecurity professional, a hacker may convince the victim to provide access to the company network. A similar attack can be targeted at financial departments by impersonating a vendor that a company regularly sends payments.
- Forged Sender Attack: When an attacker creates an email with a sender address that appears to come from a known company, such as "payments@company.com" it bypasses most email filters because it looks legitimate. This brings the attacker closer to success by reaching the victim.
Impersonation Prevention Tips
Knowledge is power when it comes to recognizing and preventing impersonation attacks. Organizations should provide clear policies surrounding company communication methods so employees always know what to expect. These tips can help your organization avoid falling victim to impersonation attacks.
- Create a formal business email that is more difficult to replicate.
- Educate employees about impersonation attacks and potential red flags.
- Use modern technology like multi-factor authentication and AI-based email analysis.
Phishing, baiting, scareware, pretexting, and impersonation all have one thing in common. They require the victim to trust the attacker and take action based on that trust. These attacks are sophisticated and very convincing, making them some of the most dangerous cyberattacks affecting businesses today. Since social engineering attacks depend on human emotions rather than circumventing security tools, avoiding them requires constant vigilance and the use of highly technical preventive methods. Wondering how you can protect your organization against social engineering attacks? Contact us today to learn more.


