Why You Should Trust Securonix SIEM to Protect Against Cyber Attacks
Cybersecurity is among the top concerns for organizations across all industries. While these types of attacks have always grown alongside technology, recent advances in remote work, the increase of IoT devices, and pandemic disruptions have significantly advanced the number and sophistication of attacks against businesses of all sizes. In 2021, cyberattacks were up 50% in comparison to 2020. Software supply chain attacks have increased by a whopping 650%, and 84% of all attacks in 2021 were distributed by email. If your network is completely safe, you're among a scant minority since cybercriminals can penetrate 93% of company networks. The trend is expected to continue in 2022 as predictions suggest a ransomware attack will occur every 11 seconds. Quarter 1, 2022 reports offer little hope, as 92% of data breaches reported in the first quarter are due to cyberattacks.
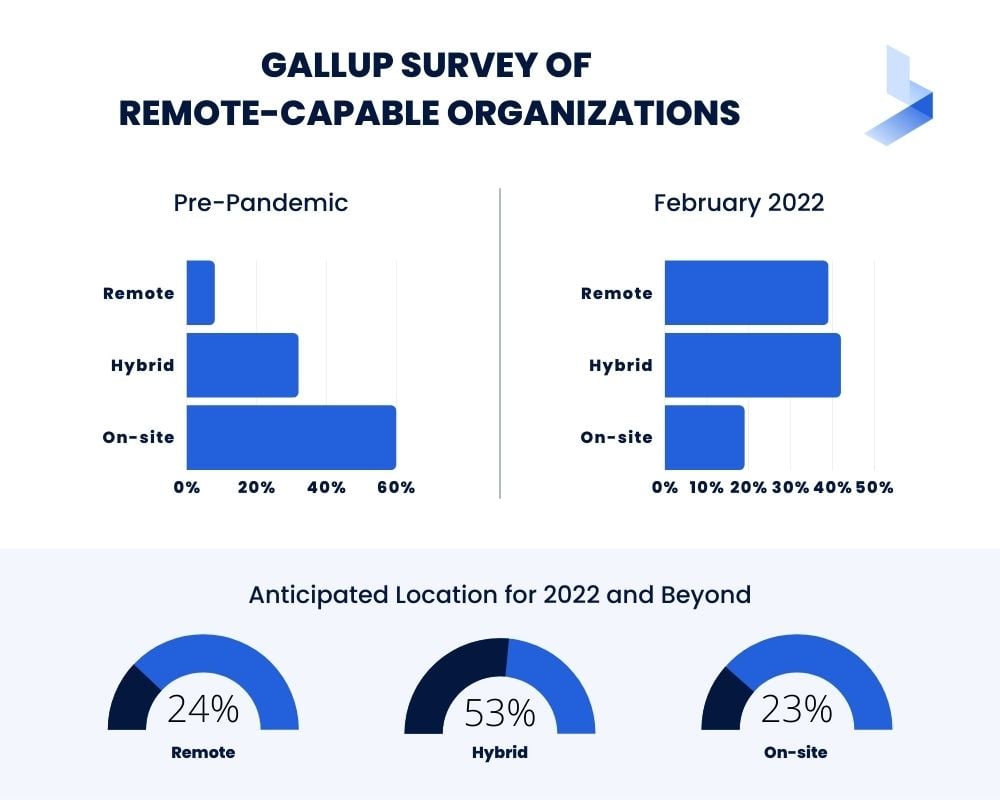
While a return to physical work is expected in many industries during 2022, there will still be considerable changes taking place. A Gallup survey of remote-capable organizations reveals how numbers have changed since the pandemic began.
- Pre-pandemic: 8% were exclusively remote 32% were hybrid, and 60% worked fully on-site
- February 2022: 39% are exclusively remote, 42% are hybrid, and 19% work fully on-site.
- Anticipated Location for 2022 and Beyond: 24% will remain exclusively remote, 53% will be hybrid, and 23% will have a complete on-site workforce.
The technology to achieve this dramatic change exists. However, it requires organizations to keep a vigilant watch as new vulnerabilities arise with the advances in remote technology. Even as many employees agree they prefer a hybrid schedule, most aren't in sync about how many days they want to spend at the office. 4 in 10 employees want to be in the office 2-3 days a week, while another 3 in 10 prefer only 1 or 2 days on-site. This means employers will likely allow varied schedules for different workers.
On top of changing workplace models, the complexity of supply chains is expected to lead to more potential attacks in the future. Governments are beginning to implement regulations to stop these attacks. This means the education sector and manufacturing companies will be required to maintain compliance with new regulations as well. Supply chain attacks have the potential for a wide reach and can affect businesses in virtually all industries.
Other attacks predicted to reign in 2022 include sophisticated deep fake technology, attacks that exploit the use of mobile devices for shopping and business, attacks that prey on IoT vulnerabilities, credential stuffing, and phishing attacks. These types of attacks target businesses of all sizes in all industries. This means organizations will have to be prepared with security solutions that provide complete visibility into their company network, endpoint activity, and cloud platforms and storage.
Why SIEM for Cybersecurity Challenges?
A robust SIEM system is one of the most integral parts of any cybersecurity system. An acronym for Security Information and Event Management, SIEM systems use historical data to investigate the way attacks occur, and real-time monitoring to provide alerts for suspicious events as they occur. Essentially, SIEM leverages data collected from multiple sources to provide a complete picture of the activity that takes place within your network.
SIEM tools analyze data, correlate events, monitor threats, generate alerts, collect and build reports, trigger automated threat response actions, and help organizations maintain compliance regulations. The activity in your SIEM system begins with the collection of data from multiple sources. The data is then normalized into digestible information and categorized by priority level. Through machine learning, the system can recognize suspicious behavior and provide incident response.
SIEM provides the technology that security analysts need to track an attacker's virtual footprints to recognize attacks and gain insight into the actions of threat actors. They can help you determine attack vectors, detect suspicious behavior, and help you improve your overall security posture. Yet, not all SIEM systems are created equal. Since SIEM tools are offered by a variety of cybersecurity vendors, different offerings include varying levels of protection depending on the technology stack offered by the provider.
Why Securonix SIEM Provides Superior Protection Against Sophisticated Cyberattacks
Securonix SIEM is a cloud-based, Next Generation SIEM designed to combat advanced threats with an analytics-based approach for the modern hybrid enterprise. An industry leader for cloud SIEM, Securonix has been named a leader for 3 consecutive years in the Gartner Magic Quadrant for SIEM. Securonix built a SIEM platform designed from a unique perspective to focus on security analytics and the use of machine learning for threat detection instead of focusing on the presence of known tools and malware used by threat actors. These features make Securonix the best SIEM choice to protect against modern cybersecurity threats.
Centralized Log Collection Improves Visibility Across a Diverse Environment
At its core, SIEM software is designed to collect log data and analyze that data for threats. Yet, as companies grow and add more diverse applications to their environment, log collection becomes a bigger challenge. Effective log collection lies in the ability to filter and ingest the data to successfully identify suspicious behavior. To address the growing threats related to remote work, third-party software, IoT devices, and supply chain vulnerabilities, companies need advanced log collection that simplifies data ingestion, compliance, and security operations.
Securonix SIEM applies advanced log collection powered by NXLog to make sure companies can implement a scalable data aggregation system. Securonix log collection can collect and normalize data from all log sources by standardizing on a single key technology. Since event log parsing takes place on the host level, the solution can read multiple log sources and send logs to multiple destinations using a single service. Flexible log collection that includes both agent-based and agentless collection capabilities can collect unstructured and structured logs from a variety of endpoints. These include servers, client devices, applications, and virtual machines from all segments of your infrastructure, and convert them into a structured format.
Administrators can view this information in a structured format on a centralized dashboard that compiles necessary logs. The result is complete visibility of all activity across your organization including remote devices, IoT devices, third-party software, and supply chain correspondence. This is to address the vulnerabilities introduced by a diverse technological environment.
Data Enrichment Enhances Threat Detection and Response
For most SIEM systems, collecting ample amounts of data is not an issue. Modern organizations have a multitude of security devices across the complete environment to adequately collect massive volumes of data. The problem arises when a flood of unstructured data from multiple sources converges in one place in different formats at different times. Without the proper context, raw data pools in your SIEM system and overwhelms your security analysts with false alerts.
Data enrichment works to add context to the information entering your SIEM system. Raw data appears as a single line of code made up of numbers and text. Data enrichment translates the same information into a detailed event. It describes the policy violated and details about the user, like user ID, name, location, and management chain. Contextual information used to enrich security data may include:
- User Identity and access level
- Asset information
- Access privileges
- Non-technical feeds (like background checks and badge data
- Vulnerability data like scan reports
- Network maps and geolocating
While many SIEM systems are equipped to enrich raw data with relevant context, scalability issues when handling big data often become a problem. Securonix SIEM is built on big data architecture to address scalability from the outset. It also enriches events in real-time, at ingestion, to be simultaneously shared with analytics teams and available to external apps outside of the SIEM. Advanced data enrichment features from Securonix SIEM address sophisticated threats in these ways.
- Correlation of activities to the entity (such as user, host, or IP address) to enable clustering of events and the ability to search enriched events by pivoting on any entity.
- Real-time enrichment provides point-in-time context to compiled data to provide an accurate timeline of events to be used in analytics and threat hunting to significantly reduce investigation time.
- Data is enriched in real-time with threat intelligence for real-time analytics, behavior profiling, risk boosting, and updating watchlists.
- Built-in playbooks automatically enrich events with contextual data to improve automated responses based on past precedents for specific events and more complex responses through playbooks.
Built-In UEBA Identifies Insider Threats
Signature-based threat identification is no longer sufficient for revealing the bulk of attacks used by modern threat actors. Today's sophisticated attacks are low and slow attacks that camouflage themselves and hide within your network until a specific objective is achieved. Some of the most common effective cyberattacks prey on human behavior as an invitation into the network. These attacks include phishing, business employee compromise (BEC), credential theft, man-in-the-middle attacks, and trojan horse malware. Each of these attacks allows bad actors to disguise themselves in the system as authorized users. Earlier versions of cybersecurity software assumed that the activities of an authorized user were accepted as legitimate. To eliminate today's sophisticated cyberattacks, organizations require tools that can identify when an authorized user acts suspiciously.
User and Entity Behavior Analytics (UEBA) uses machine learning to establish a baseline of normal user behavior within your organization's network. From this established baseline, the system can then detect and trigger alerts for unusual behavior. Many security vendors offer UEBA as an individual product or service. Securonix incorporates UEBA directly into the SIEM for advanced user context applications out-of-the-box.
Securonix UEBA leverages sophisticated machine learning and behavior analytics to analyze and correlate interactions between users, systems, applications, IP addresses, and data. Powerful machine learning deployed by Securonix detects unusual behavior conducted by users and connects related events and compares them to threat models to identify suspicious behavior. By combining machine learning with user information, threat models, and external information, Securonix UEBA can connect activities and information into threat chains that more clearly define malicious behavior. This ability vastly decreases false positives that plague many less advanced SIEM systems and increases the chances of detecting advanced persistent threats (APTs).
Out of the Box Use Cases Improves Threat Detection
Outdated SIEM solutions are focused on IP-centric enterprises. Some newer systems implement rules-based logic security use cases focused on simple threat scenarios. Unfortunately, without the use of external threat intel and collaborative development, these types of models for threat detection are woefully inadequate against modern sophisticated threats.
Securonix SIEM is built on data analytics to identify chains of behavior that indicate a threat. While some SIEM systems are basically a blank slate before installation and optimization, Securonix SIEM is packaged with out-of-the-box applications delivered in the form of threat models and built-in connectors that enable rapid deployment and quick time-to-value.
SIEM systems largely focused on infrastructure and compliance monitoring identity singular anomalies, which can either look innocuous in isolation or turn up multiple times, causing redundant alerts. In contrast, Securonix threat models are built to predict and detect the kill-chains of events that could be part of an advanced attack. These models can rapidly scan through historical or real-time data to predict and detect advanced threats. Instead of a SIEM that notes isolated events, Securonix clusters the events into groups that make attack identification easier. Some of the key packaged applications include:
- Data Security Analytics
- Privileged Account Analytics
- Cyber Threat Analytics
- Identity and Access Analytics
- Application Security Analytics
- Cloud Security Analytics
- Fraud Analytics
- Patient Data Analytics
Along with out-of-the-box threat models, Securinix customers have access to the Threat Model Exchange, an online library where customers access and share the latest threat models. These models are continuously updated against the latest cyberattacks by the Securonix Cyber Research Team. Customers access the online library from the Securonix app interface and can download and deploy the latest threat models with only a few clicks.
The use of threat models offers rapid deployment and faster time to value, eliminating the burden of creating and managing complex correlation rules. It also takes the guesswork out of optimization by utilizing events that are most likely to be used in modern, sophisticated attacks. This means organizations can immediately receive updated information about suspicious behavior most likely to indicate an attack.
Superior Remote Work Protection
Organizations are turning to remote work across several industries, and hackers have been taking advantage of vulnerabilities presented by these sudden changes. As companies develop permanent remote or hybrid workplaces, these attacks aren't likely to slow down. With remote work already in progress, it's critical to provide a secure option without further delays.
As a UEBA and analytics-based SIEM, Securonix was immediately poised to address the challenges of remote work in a variety of ways. With the ability to ingest and analyze access permissions along with the ability to integrate with identity access management and identity governance administration tools, Securonix SIEM can compare permissions against job roles to detect suspicious behavior and recommend corrective action. The combination of these tools and advanced abilities addresses common remote work vulnerabilities, including:
Data Compromise
Remote work increases the risk of data compromise significantly. Securonix's built-in UEBA alerts rare or sudden increases in access to sensitive data to note potential data exfiltration.
Credential Theft
A remote work environment can lead to credential sharing and other security challenges related to unauthorized access. To eliminate vulnerabilities, it's essential to create use cases catered to credential sharing. Securonix uses machine learning and identity context checks to detect credential sharing or credential theft, including land speed analysis, physical and geolocation correlation, and rare logins that match with other users.
Email Phishing Campaigns
Phishing attacks are at an all-time high across business and remote devices. Securonix uses machine learning to analyze email data, senders, domains, subjects, attachment names, etc., to detect phishing attacks. Common techniques the SIEM seeks include typo-squatting, new domains, spear-phishing targeting a specific peer group, and emails from suspicious domains.
Account Compromise
A huge surge in remote logins makes user accounts more vulnerable to attacks due to more potential weaknesses in the authentication process. Securonix uses machine learning and identity context correlation to detect account compromise. These include enumeration behavior patterns to detect sophisticated brute force attacks, rare login behaviors, a spike in failed logins, and logins from fake accounts.
Cloud Platform Attacks
A remote workforce increases the utilization of cloud platforms that may not be protected by your network security system. Securonix's next-gen SIEM is a cloud-based application with the unique ability to monitor enterprise and custom applications with packaged connectors and content for all major cloud applications and services. These include Microsoft Office 365, Salesforce, Box, AWS Azure, Google Cloud Platform, and others.
Remote Device VPN Access
Remote authentication and VPN devices can present new vulnerabilities in your network. Securonix monitors activities on VPN and remote authentication devices including a spike in failed logins, bulk password resets, suspicious connections, privilege escalations, etc.
Endpoint Attacks
Increased phishing activity leaves remote devices more vulnerable to human error, compromising and ultimately, your network. Securonix monitors both hosts and endpoints for suspicious behavior patterns, including command and control communication, suspicious process execution, anomalous connection patterns, and communication to newly registered and unregistered domains.
Non-Compliance on Remote Devices
While this doesn't address attacks, non-compliance can lead to expensive fines and even the loss of critical licensing. Securonix entity-based monitoring enables the ability to create use cases that monitor software license usage.
Integration Capability Protects Against Third-Party Attacks
Remote work, IoT devices, cloud storage, and third-party platforms create potential vulnerabilities that leave devices and networks open to cyberattacks. Modern SIEM systems must go beyond organizational infrastructure and in-house monitoring to protect your entire environment from attacks. Threat actors prey on popular platforms to find vulnerabilities that cross multiple networks. For instance, the ability to access a network through a vulnerability in Office 365 creates opportunities to target multiple organizations.
Securonix SIEM integrates with all of the most popular third-party applications and cloud platforms used by modern enterprises. This integration enhances your data security by monitoring all aspects of the cloud and streamlining remediation of email-borne threats before damage occurs. SIEM integrations provide complete protection across all platforms. Common business platforms that Securinix protects through integration include:
- Google Cloud Platform
- Microsoft Azure
- Microsoft 365
- Salesforce
- AWS
Protect Against Modern Sophisticated Attacks With Advanced SIEM Capabilities
SIEM is a crucial part of any cybersecurity solution. However, outdated or incomplete SIEM systems can give your team false confidence and leave your network even more vulnerable to attack. Securonix SIEM checks all the boxes for modern security with a cloud-native application that offers scalability suited to big data and analytics-based threat detection and response capabilities. It offers a complete solution for log collection and full visibility into every corner of your network. Out-of-the-box threat modules and integrated UEBA apply crucial context to the data for easier threat identification and faster incident response. The ability to integrate the SIEM with third-party apps and cloud platforms provides vital protection against threats that target popular business platforms. While modern attacks work to exploit multiple vulnerabilities and remain hidden disguised as legitimate behavior, modern security tactics can detect and respond to cyberattacks.
Managed SIEM from BitLyft offers premium protection for your network with the most comprehensive modern protection available. Our experienced security team installs and optimizes your SIEM to provide greater visibility to your log and event environment. Custom tuning refines your SIEM to eliminate false alerts and detect relevant threats. Ongoing management keeps your network protected against evolving threats. Next-Gen SIEM combined with cybersecurity expertise combats APTs with the most up-to-date talent and technology. Schedule an appointment with BitLyft to learn more about how we can help you achieve your security goals.
