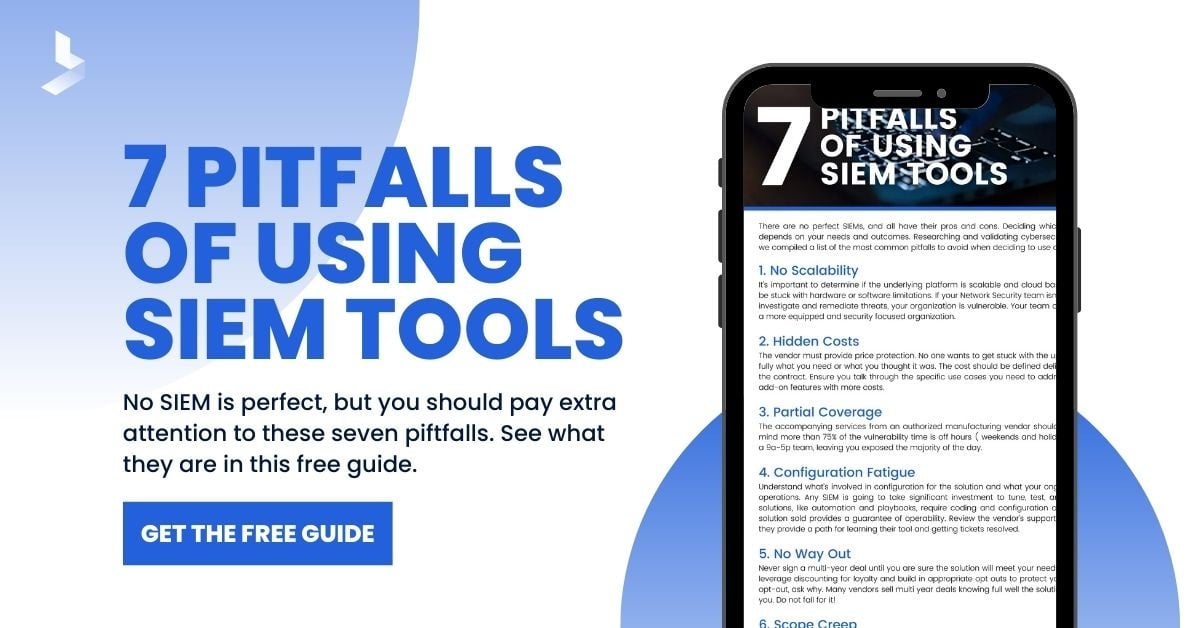
Does Your Company Need SIEM Software?

 By
Jason Miller
·
5 minute read
By
Jason Miller
·
5 minute read
Business technology never stands still. Unfortunately, the criminal hackers who try to take advantage of that technology never stand still, either. It’s important to stay vigilant at all times against security threats, and that’s where SIEM comes in.
When new technologies, new platforms and new patches are developed, they are often open to exploitation by digital malcontents. CIOs, CTOs and CISOs look to keep their businesses secure, not only to maintain operational efficiency, but also to keep the hard-earned reputation of their brands intact. A cybersecurity breach can not only be an extremely expensive prospect in the short-term, it can seriously damage their long-term image in the eyes of clients, customers, shareholders and investors.
So how can Security Information and Event Management Software (SIEM) accomplish this? First, let’s take a look and what a good SIEM actually is:
What is Security Information and Event Management Software?
SIEM software has been around for over a decade—and began life as a simple log management tool. Over the years, however, it has evolved into much more complex analytics and reporting features which can give businesses insights into virtually all activities that take place within their IT environment.
As the name suggests, SIEM combines Security Event Management (SEM) with Security Information Management (SIM). This means that it analyzes log and event data in real time while also collecting, reporting on and analyzing log data.
So what does that really mean? Effective threat monitoring! And not only that, because a mature SIEM helps facilitate proper incident response, through effective event correlation.
It also provides detailed analytics to allow enterprises an agile and proactive approach to any future threats, to make sure that your IT environment isn’t open to the same threats twice.
Today many enterprises, particularly larger enterprises, look to SIEM as the foundation of their security operations center. Over recent years, SIEM software solutions have grown increasingly sophisticated, with many providers beginning to integrate AI and machine learning based on the analytical data they provide.

How does Security Information and Event Management software work?
Every time there’s an activity on your system, that’s a security event. Every login, email, or firewall update is one of thousands of events that make up the normal activity pattern of your IT infrastructure. Which means that, if one of those events is a potential security threat, it can be alarmingly easy to miss.
That’s why SIEM logs and monitors all of those events in a more efficient way than the human eye alone can manage.
SIEM software collects and aggregates the log data which is generated throughout your enterprise’s IT infrastructure. It collects data from a wide array of sources, including applications and host systems, as well as security systems such as anti-virus software and firewalls.
The SIEM solution identifies and categorizes incidents and events for easy reporting…but this is just the tip of the iceberg.
As well as logging events, it also analyzes them and determines their threat level based on a system of predetermined rulesets. (This is why it’s important to pick the right SIEM provider who understands the rulesets needed for your organization, but more on that later.)
The primary objectives for SIEM solutions for business enterprises are;
- To generate reporting on security-related events and incidents. These might include malware activity, large quantities of failed logins etc.
- To send alerts to key personnel if analysis indicates that the behavior runs against the predetermined parameters for acceptable behavior which indicate a potential security issue.
- To help within your incident response, decreasing the time to stop the threat.
Does my organization need SIEM software?
While many enterprises see SIEM as the beating heart of their cybersecurity infrastructure, there are others who may question whether or not they need it. The choice is entirely yours, though we can tell you why so many enterprises consider it essential.
SIEM has traditionally been used in medium to larger sized organizations. Smaller businesses didn’t find it accessible due to its cost and the high levels of proficiency required by employees to maintain it. To install SIEM on-prem meant a significant investment of time, hardware, employees, and money.
However, with new ways to outsource SIEM to a cloud-based model, those barriers for entry have largely been lifted, and now organizations of any size can take advantage of SIEM’s superior protection.
Many enterprises have ended up with egg on their face when a malware breach has gone undetected. Even Google has been shaken by a breach which caused it to shut down its (admittedly ailing) social platform Google+. The goal of an SIEM is to prevent enterprises from having to endure such public blows to their reputation, as well as guarding against the downtime, cost and other logistical implications of a breach.
For many larger organizations, or those in heavily-regulated industries, compliance is also an important factor. SIEM software ties directly into more effective compliance management.
When auditors need to assess whether businesses are compliant or not, the information yielded by SIEM solutions can prove invaluable. The monitoring and reporting facilities that they provide help enterprises meet a range of essential mandates.
Finally, even if your enterprise should be subject to a breach, the last thing any CIO or CISO wants to do is face the board and tell them that… well… they have no idea what happened. The detailed reporting and analytics afforded by SIEM means that even if the worst should happen, the data gleaned can be used to proactively ensure that those threats won’t have the same impact again.
Choosing the right SIEM solution for you
With so many SIEM solutions on the market, it can be daunting to decide which is best suited to the needs of your enterprise.There are two factors to consider: SIEM tools, and SIEM partners.
Security Information and Event Management Tools
Here are some of the most well-known SIEM tools in the market today:
LogRhythm: LogRhythm is extremely popular amongst businesses looking for security, and it is easy to see why. It’s considerably easier to use and interface with existing infrastructures than some of its other SIEM counterparts. This makes LogRhythm a SIEM product that is better suited to smaller to medium sized businesses, municipalities, and other organizations. It’s also not as costly as some of the alternatives out there. The intuitive interface and flexible dashboards make threat hunting and log analysis easy and not time consuming. We at BitLyft use and love the LogRhythm product as a comprehensive security solution for most IT architectures. LogRhythm has won the Gold SIEM award for 6 years in a row from Gartner.
Splunk: Another popular solution on the market, Splunk offers detailed reporting and solid log management capabilities. It’s also an effective log aggregation tool with dashboards, but requires heavy administration and constant maintenance to keep it effective. Pricing can be a factor acquiring the software licensing and to implement. (Unfortunately, with all this, can come at a steep price tag.)
ArcSight: Another highly rated SIEM tool, ArcSight offers open architecture and astonishing levels of detail, although many users report that the learning curve is decidedly steeper than Splunk’s.
IBM: A SIEM tool from an established name in technology, IBM’s QRadar tool is also hugely popular. Users laud its ability to correlate data across our global enterprise in near real time while also integrating a lot of third-party solutions.
Security Information and Event Management Partners
Regardless of the SIEM product you choose, having the right security partner to help install, calibrate, optimize and maintain your SIEM solution is crucial to your future security success.
You’ll need to make sure that you have a team of expert analysts to help you program, monitor, and react to the data that SIEM provides. Remember, a SIEM is a tool, and a tool is only as good as the team that uses it.
If you’re interested in partnering with BitLyft to implement a strong SIEM-as-a-Service, we’d love to hear from you. Set up a short conversation today to explore a potential partnership to secure your IT environment.