What Is Cyber Threat Hunting?

 By
Emily Miller
·
5 minute read
By
Emily Miller
·
5 minute read
Did you know that it can take days, weeks, or even months to discover a security breach has happened?
Cybersecurity grows ever more complex as hackers discover novel ways to compromise their targets. From phished credentials to privilege escalation, they can do damage long before anyone is aware. That is, unless the target has deployed XDR security.
A reactive response is no longer sufficient in today's digital landscape. Threat hunting is the name of the game.
In this cyber threat hunting guide, we'll discuss how this proactive response can increase your security.
What Is Threat Hunting?
The name says it all. Threat hunting is a proactive approach where administrators seek out vulnerabilities in their own system.
While this might seem like the obvious decision, the unfortunate reality is that most companies apply a reactive approach. Whether it's a false sense of security or misaligned priorities, many wait for a hack to happen before they act.
As the saying goes in the cybersecurity community, "It's not if you'll be hacked, but when." Even the biggest companies with the most robust security experience cyberattacks on a daily basis. Companies that fail to deploy some form of proactive security end up hacked.
The Proactive Approach: Threat Hunting, Risk Assessment, and Penetration Testing
There's more than one way to skin a cat, but what method a company uses depends on its budget and threat level. To understand what role threat hunting plays in cybersecurity, we need to understand its alternatives.
The most extreme of the above approaches is penetration testing. This involves hiring a team of white hat hackers to attempt to compromise your system--doing so as external bad actors might. It's a long, involved process that allows system administrators to view their system as the outside might.
A risk assessment is a more toned-down version of a pen test. Security experts preen a system for potential vulnerabilities but don't exploit them for the purposes of further testing. They assemble a report detailing the main issues and let system administrators deal with them.
Both of the above are valid, effective approaches to evaluating system security. But penetration testing is a protracted endeavor that serves only to simulate a cyber attack. A risk assessment is a one-time examination that does not take into account a robust, changing system.
A halfway point is needed, and that's cyber threat hunting.
| Related Reading: Comparing Scanning and Penetration Testing |
Understanding Cyber Threat Hunting
Cyber threat hunting is a blend of the above proactive security measures. It's a system of active threat detection that assumes that vulnerabilities are already past the door. It combines advanced threat detection with machine learning to weed out even the most persistent threats.
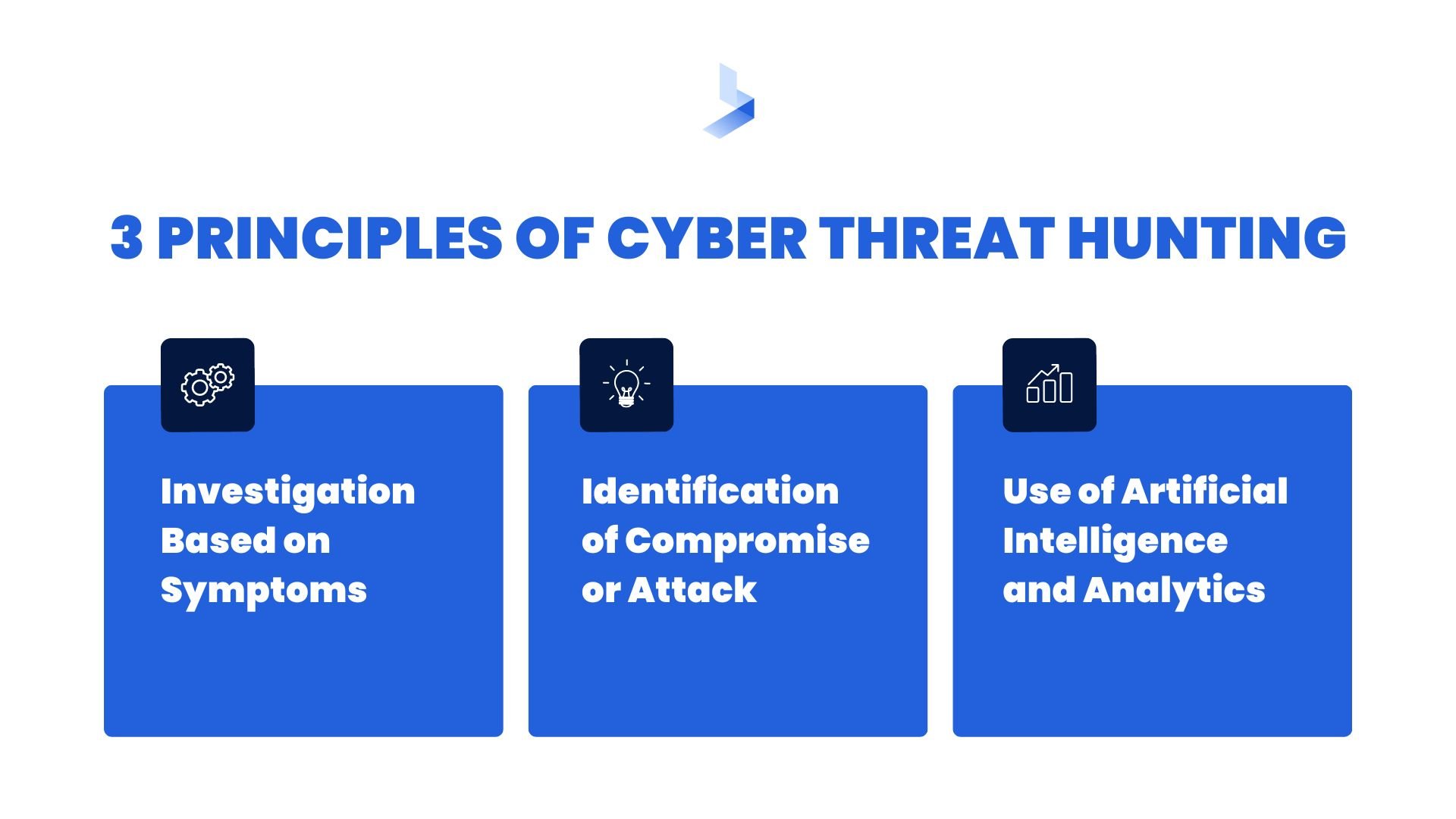
Cyber threat hunting operates on a few main principles.
1. Investigation Based on Symptoms
Cyber attacks happen every 11 seconds, so there is a massive pool of data associated with them. Security companies collate this glut of data and pare it down to something useful: an M.O. This allows researchers to determine how hackers are pulling off their breaches.
In the effort of beating them to the punch, threat hunting analyzes a system for similar vulnerabilities. This is a hypothesis-based approach that predicts what methods the hackers might have used to gain access. Rather than scanning the entire system from top to bottom, security directs its efforts to likely culprits.
2. Identification of Compromise or Attack
Once a hacker has compromised a system, there may exist signs of their activities. These might be suspicious logs or suspicious activities that fly under the radar. Successful identification of these indicators allows security experts to potentially stop a breach in progress.
3. Use of AI and Analytics
Effective time use is of the essence. Going system by system, scanning from the top to the bottom is not effective. That's where artificial intelligence comes in.
Using algorithms to parse massive datasets, analysts can find anomalies in walls of data. This allows them to pinpoint areas of investigation. Then they can hone in on these anomalies and deal with them.
Cyber Threat Hunting Tips
Cyber threat hunting is not a fire-and-forget solution. It's an active, adaptive strategy that plays out over the course of a system's existence. As such, there are a few things that differentiate a successful threat hunting strategy from an unsuccessful one.
TTP (Tactics, Techniques, and Procedures)
If ever there were a universal cybersecurity rule, it's that you need to know your enemy. Hackers are ruthless, and they spend day and night fine-tuning their exploits. They are the epitome of modern evolution, adapting to every change and always coming out on top.
Entire websites and conferences devote themselves to understanding hackers. White hat hackers present their findings to the world in an effort to protect and warn. As such, there are a lot of resources for security experts to learn from.
Threat hunting is about knowing what tactics, techniques, and procedures hackers employ. It's about using existing data, AI, and intuition to sniff out issues that go unnoticed by standard systems.
Once you understand a hacker's M.O., you can begin to make predictions. That's where the hypothesis part of threat hunting comes in. By recognizing the symptoms and the signs, you form a hypothesis about the hacker's intentions and go from there.
Establishing a Baseline
It's important to know what "normal" is so that you can compare a nominal system with a compromised one. Threat hunting is about understanding what constitutes the status quo so that anomalies leap out and appear more obvious.
Every system is different. What might constitute abnormal behavior in one environment wouldn't even move the needle in another.
Before deploying threat hunting, you need to establish a baseline. That not only includes how your system operates on a daily basis, but how admins work with it. It means knowing who has privileges, and how they use them.
Pattern Recognition
Once the baseline is established and security has a solid foundation of TTP, it's time to put the analytics to work. Like identifying symptoms of compromise or attack, there is a method to a hacker's work. The way they obtain privileges and then use them to move laterally about your network will leave a trail.
Pattern recognition isn't just about past threats, but upcoming ones as well. Once you've established a pattern, you can notice it when it happens again.
Using XDR Security in Threat Hunting
XDR (extended detection and response) is what brings threat hunting together. Since cyberattacks are a threat every second of every day, a system needs to be on its toes. Threat hunting is most effective when system administrators can sniff out anomalous changes from second to second.
Put simply, XDR is a platform of advanced tools that allows for superior moment-to-moment security. It provides a screenshot of your system's current posture, allowing you to respond to threats as they arise.
XDR differs from EDR, which focuses on endpoints alone. XDR spans everything, from cloud services to email. It's a comprehensive solution for system operators that want to leave no stone unturned.
Next-Gen XDR cybersecurity aims to make this comprehensive and automated. It attempts to make this a one-size-fits-all approach that any system admin can apply to their respective institution.
XDR cybersecurity and threat hunting go hand in hand because they focus on the following:
- Real-time analysis and response to indicators of compromise or threats
- Use of human problem-solving and AI analytics to sift through large swaths of data
- Integration of a wide variety of tools
- Proactive, preventative security rather than reactive, reparative security
What Are the Cyber Threat Hunting Benefits?
Threat hunting with XDR isn't just a comprehensive security solution. It's an investment in a company's future, given that breaches are incredibly expensive. Let's discuss just a few of the benefits.
Systemwide Visibility
Breaches happen under our noses, in the dark of our systems. Without threat hunting and XDR security, there's a lack of visibility. This lack of visibility leads to a lack of control and limits a system administrator's ability to respond to threats.
Rapid Response
Since threat hunting hones in on the tells of a threat (or threat in progress) the response is rapid. Administrators can recognize breaches as they happen, or potentially stop a breach in the making. This is far superior to discovering a breach only after the damage has been done.
Enhanced Protection
Modern-day systems span from the cloud to the endpoints. This creates a conglomeration of devices running on different code and interacting in different ways. The potential for vulnerabilities has never been higher.
Threat hunting can fill the gaps in complicated systems. Using security datasets and known patterns, it can identify novel exploits in the system before hackers reach them. This is much better security than a mere scanner that only looks for known threat identifiers.
Implementing XDR Security in Your Threat Hunting
Threat hunting is a proactive, all-encompassing strategy to nip cybersecurity threats in the bud. It makes use of a wide toolset and artificial intelligence analytics to identify triggers for compromises and threats. As such, it's capable of preventing breaches or stopping them midway.
Next-Gen XDR threat hunting is here, and it's cybersecurity's answer to the surge in security breaches. Look no further than the BitLyft solution. Beat hackers to the punch by preparing your system today.
Remember, it's not if you'll be hacked, but when.
