What is File Integrity Monitoring?

 By
Jason Miller
·
3 minute read
By
Jason Miller
·
3 minute read
Technology-focused organizations typically have a heavy reliance on IT environments. Whether it’s the use of expensive software, complicated hardware configurations or large business networks, it’s vital to utilize technology in order to become a more efficient business.
However, many of these services are typically outsourced to experts that are far more knowledgeable and experienced than your existing staff members. One of the tools that a managed security service provider (MSSP) can offer to keep your technology secure is File Integrity Monitoring (FIM).
Coping With the Growth of Your Business’s Technology
An MSSP is constantly looking for ways to secure your technology environment. This can mean configuring and monitoring firewalls to prevent unwanted network traffic from entering the local network, it could mean preventing viruses from affecting your computers, and it could mean managing virtual private networks for remote working purposes.
In addition to an MSSP helping you to secure your network and technology systems, you’ll also have employees accessing files on your network, getting their work done and generally putting a strain on your network. When they modify files for work purposes, it’s generally picked up by a security information and event management (SIEM) system that will alert your security specialists when a potential threat is detected. However, a SIEM focuses on user and entity behavior analytics so it often doesn’t directly intervene if it detects a change it perceives as regular.

This is where a File Integrity Monitor can help you ensure that your files are not accidentally or maliciously modified.
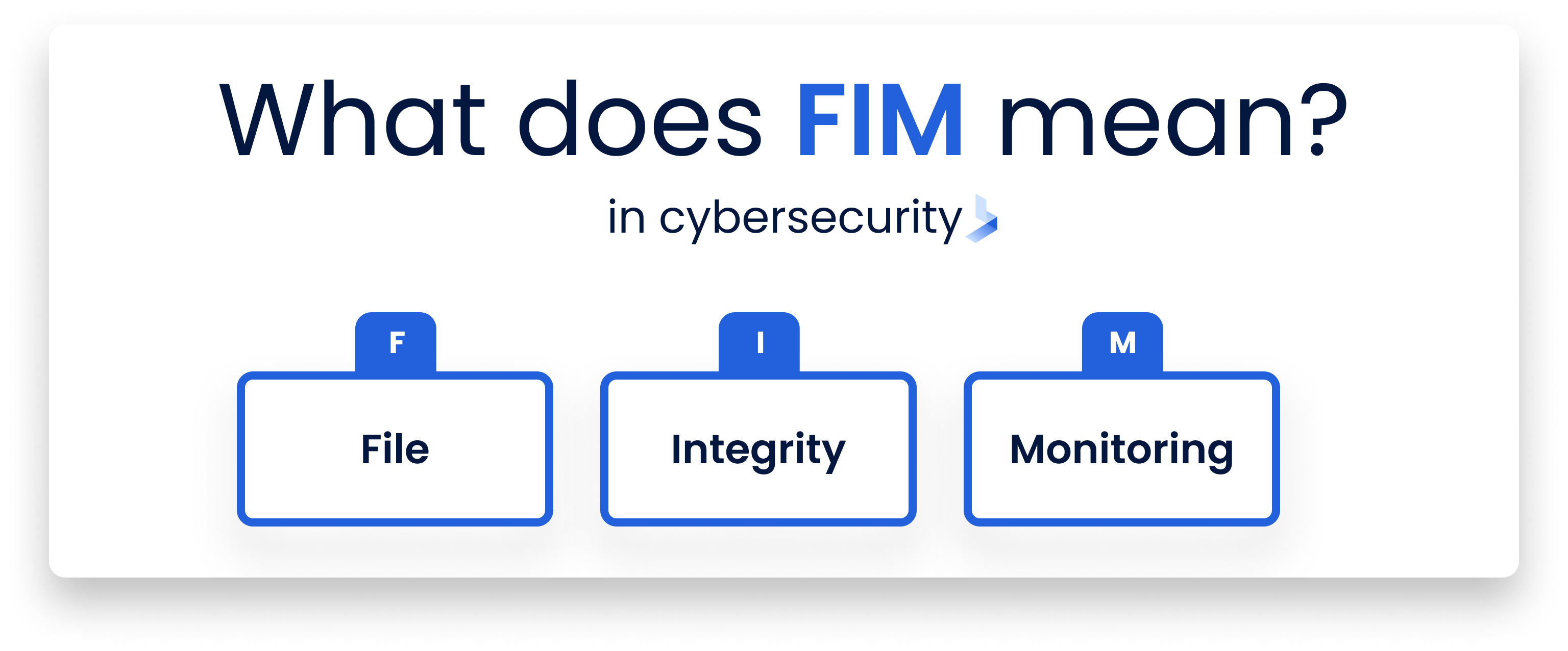
What is File Integrity Monitoring?
FIM is a crucial cybersecurity process that involves the detection and alerting of unexpected or unauthorized changes to files within a system. This includes system and application files, configuration and content files, and other critical components. The primary purpose of FIM is to ensure that these files remain unaltered and secure, therefore preserving the integrity of the system. If any changes occur—whether due to malicious cyberattacks, system glitches, or human error—FIM tools immediately notify the system administrators. This prompt detection allows for rapid response, which is key to minimizing potential damage or data loss.

How Does FIM Work?
File Integrity Monitoring (FIM), also known as change monitoring, meticulously records and scrutinizes modifications made to specific files. It involves a series of steps that begin with the formulation of a policy outlining the files that need monitoring and protection, usually critical configuration files that determine how a system operates.
After identifying the files, a baseline is established for each, considering factors like the file's creation date, version, and its most effective state. This baseline acts as a reference point, against which any subsequent changes are evaluated.
Once the baseline is configured, the FIM system vigilantly monitors the tracked files for any alterations, comparing any changes with the predefined baseline. While expected modifications are typically accepted, any unauthorized or unexpected changes trigger an alert.
Integration of FIM with a SIEM system adds an extra layer of protection, minimizing potential false positives, and expediting the response to actual threats. The SIEM system, by understanding the normal patterns of file changes, helps reduce false alarms and aids in faster response to genuine threats, such as potential cyberattacks from hackers aiming to access FIM-protected files.
Alerts are issued when unauthorized changes occur, prompting relevant personnel to investigate the alteration, potentially mitigating issues, or marking the alert as a false positive. Additionally, FIM assists in regulatory compliance, like GDPR or PCI DSS, by generating necessary reports that document file changes and the company's response to them.
Integrating FIM into SIEM and MSSP
FIM is a system that helps to protect your business-critical data and files that are essential for the efficient operation of your business. When merged with SIEM and deployed by a trusted MSSP, it helps to create a more secure system for your business.
One of the biggest reasons for merging a FIM with your SIEM: the danger of internal threats. Many people look at external threats, such as cybercriminals, and believe that they’re the biggest danger to their digital infrastructure. However, their attempts to break into your system can potentially be limited by proactive measures such as firewalls and properly configured security systems.
A potentially greater danger lies with internal threats, such as a disgruntled employee or even a potential corporate spy. Since these people have access to your system from the inside, they can wreak havoc and completely destroy your business if you don’t have countermeasures in place.
This is where a FIM integrated with a SIEM can help protect you.
It offers another secure layer of protection that protects your business-critical files from being changed through unauthorized access. With the increased power and accessibility that an employee has, they could potentially make changes to these important files for malicious reasons and they may even be authorized. However, a SIEM and FIM system will not only record the change and potentially notice that it was a malicious change, but it will also alert the relevant people immediately so they can take swift action against the employee.
When FIM and SIEM work together, especially when managed by a professional MSSP, it offers you and your business unparalleled security to ensure that your business runs efficiently and is free from the threat of malicious interference.
If you’re looking for the most mature FIM and SIEM solutions for your security infrastructure, you can rely on BitLyft. We have the tools and expertise to secure your environment for a fraction of the cost of an in-house team.
Give us a call. We’d love to have a short conversation about how we can help secure your business’ technology interests.
