What Is Vulnerability Management? How Does It Work

 By
Jason Miller
·
10 minute read
By
Jason Miller
·
10 minute read
In the business world, it's important to be able to protect your company from cyber-attacks. This is where vulnerability management comes in.
Vulnerability management is a process that helps organizations identify and address security vulnerabilities. This occurs before hackers can exploit them.
In this blog post, we will discuss what vulnerability management is, and how it works. We'll also cover some of the benefits of using this process.
So keep reading to discover vulnerability management tips to ensure that you can make the most out of your security.
Vulnerability Management Definition
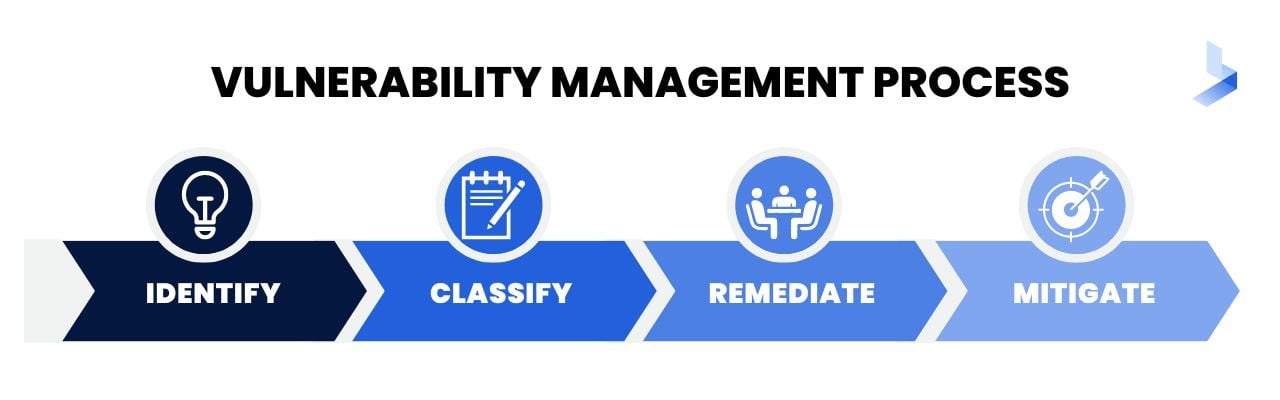
Vulnerability management is the practice of:
- identifying
- classifying
- remediating
- mitigating
This applies to vulnerabilities within the system. It's a proactive process that helps organizations reduce their exposure to security risks.
Security Vulnerabilities
The first step in vulnerability management is to identify potential security vulnerabilities. One can do this through manual inspection or by using automated tools.
Once identified, the next step is to classify the severity of each vulnerability. This helps organizations prioritize which vulnerabilities need to be addressed first.
Vulnerability Scanner
After the vulnerabilities you've identified and classified, the next step is to scan for them.
One can do this using a vulnerability scanner. This is a tool that automates the process of identifying security vulnerabilities. Once the vulnerabilities have you've scanned, they can be remediated.
Risk-Based Vulnerability Management
The final step in vulnerability management is to mitigate the risks. Those that are associated with the vulnerabilities.
One can do this by implementing security controls. It can also be done by taking other measures to reduce the risk exposure.
Types of Vulnerabilities
Many types of vulnerabilities can exist in an organization's systems and networks. Some of the most common include:
Unpatched Software Flaws
Also known as zero-day vulnerabilities, these are security holes in software or applications that have not yet been patched or fixed by the vendor. Because attackers are aware of these weaknesses, they can exploit them to gain access to sensitive data or systems.
Outdated Software
Software that is no longer supported by the vendor (e.g., Windows XP) is also a vulnerability because there are typically no more security updates released for it. This leaves organizations using outdated software at risk of being compromised by attackers.
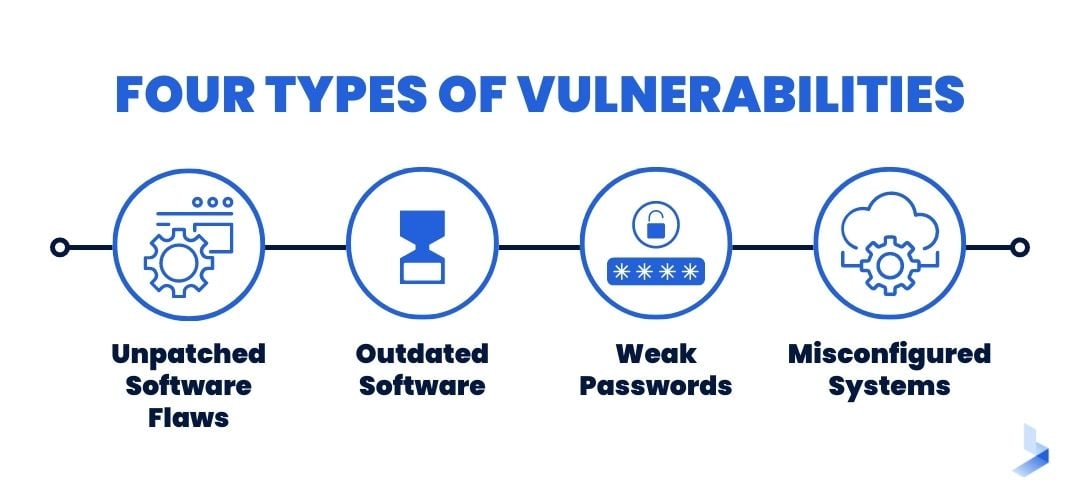
Weak Passwords
One of the simplest ways for attackers to gain access to systems is by brute-forcing their way in with weak passwords. Passwords that are easy to guess or are reused across multiple systems are a major security risk.
Misconfigured Systems
Incorrectly configured systems can also leave organizations vulnerable to attack. For example, leaving port 22 (the default SSH port) open on a public-facing server makes it an easy target for attackers looking to gain access to the system.
Who Should Consider Using Vulnerability Management?
Vulnerability management is a process that can be beneficial for any organization. It's especially important for companies that store sensitive data or that are at high risk for cyber attacks.
Should you implement a vulnerability management program, well, ask yourself the following questions:
- Do we have sensitive data that needs to be protected?
- Are we at high risk for cyber attacks?
- Do we need to comply with industry regulations?
- Do we have the resources to manage vulnerabilities effectively?
If you answered yes to any of these questions, then vulnerability management is something you should consider.
Should You Utilize Vulnerability Management Solutions Or Focus On In-House Prevention?
There are a few different options when it comes to vulnerability management. You can choose to focus on in-house prevention. You can utilize vulnerability management solutions.
In-house prevention is the process of identifying and fixing vulnerabilities early. One can do this through manual inspection, code review, and automated tools. In-house prevention is a good option for organizations that have the resources to do it.
Vulnerability management solutions are tools that help organizations. They automate the process of identifying, classifying, and remediating vulnerabilities.
These solutions can be beneficial for companies that don't have resources. Resources are needed to manage vulnerabilities effectively on their own.
No matter which approach, the important thing is having a vulnerability management program. It's the best way to reduce your organization's exposure to security risks.
The Benefits & Importance of Vulnerability Management
Vulnerability management is a critical part of any organization's security strategy. By proactively identifying and addressing vulnerabilities, organizations can reduce their risk exposure. Thus, they can minimize the impact of potential cyber-attacks.
Regarding cybersecurity, there is no such thing as being too prepared. Vulnerability management is one way that organizations can protect themselves. They will be secure from the ever-changing landscape of cyber threats.
Cyber attacks are becoming more sophisticated and targeted. Thus, making it essential for organizations to have a comprehensive vulnerability management program.
There are several benefits to implementing a vulnerability management program, including:
Reduced Cyber Attack Risk & Industry Compliance
By identifying and addressing vulnerabilities before they can be exploited, you reduce the risk of being attacked by hackers.
Many industries have regulations that require organizations to address security vulnerabilities. Vulnerability management is the best way to meet these requirements.
Improved Security Posture & System Visibility
A well-run vulnerability management program can improve your organization's overall security posture.
Vulnerability management gives you increased visibility into your systems and networks. This can help you identify issues before they become problems.
If you're not already using a vulnerability management process, now is the time to start. Implementing this process can help you reduce your organization's exposure to security risks. This keeps your data safe from potential attackers.
What Are the Roadblocks to Vulnerability Management?
Despite the many benefits, there are a few roadblocks that can prevent organizations from this process. One of the biggest roadblocks is a lack of resources. Organizations often don't have the manpower or budget to implement vulnerability management.
Another common roadblock is a lack of awareness. Many organizations are not aware of the importance of vulnerability management. They don't know how it can benefit their organization. Without this knowledge, they are less likely to prioritize this process.
Finally, some organizations may have difficulty identifying all of their potential vulnerabilities. This can be due to a lack of experience or technical expertise. However, there are many tools and resources available that can help with this task.
Despite these roadblocks, it's important for organizations to implement a vulnerability management program. By doing so, they can reduce their exposure to security risks and keep their data safe from potential attackers.
How Does Vulnerability Management Differ From Vulnerability Assessment?
Vulnerability assessment is a process that helps organizations. It identifies and quantifies vulnerabilities in its systems. It's a passive process that provides a snapshot of an organization's current security posture.
Vulnerability management, on the other hand, is a proactive process. It helps organizations remediate vulnerabilities and reduce their exposure to security risks.
Both vulnerability assessment and vulnerability management are important parts of an organization.
However, vulnerability management goes one step further by helping organizations mitigate the risks. This makes it a more comprehensive and effective approach to protection.
Regarding cybersecurity, there is no such thing as being too prepared. Vulnerability management is one way that organizations can protect themselves. The ever-changing landscape of cyber threats is dangerous.
Cyber attacks are becoming more sophisticated and targeted. Thus, organizations must have a comprehensive vulnerability management program in place.
Protecting Your Enterprise From Exploits
No organization is immune to security risks, but vulnerability management can help reduce your exposure to them.
By implementing this process, you can proactively identify and address vulnerabilities. This occurs before hackers can exploit them. In today's changing landscape, vulnerability management is an essential part of any organization.
The best practices go as follows:
Utilize Traffic Scanning & Filtering
Traffic scanning identifies and analyzes network traffic for potential security risks. One can do this using a variety of tools. For example, including firewalls, intrusion detection systems, and web filters.
By scanning incoming traffic, you can identify potential threats. Thus, you can take measures to mitigate them.
Install Anti-Malware Software
Anti-malware software is designed to detect and remove malicious software from your system. This type of software can be subject to use to protect your computer. It secures viruses, worms, Trojans, and other types of malware
It's important to keep your anti-malware software up-to-date. This will ensure that it can protect against the latest threats.
Patch Your Systems & Applications
The most effective way to reduce your security risks is to keep your systems up-to-date. This includes applying the latest security patches as soon as they're released.
By patching your systems, you can close potential security holes from hackers.
Implement Strong Password Policies
Another way to reduce exposure to security risks is to implement password policies. This includes requiring employees to use complex passwords that are difficult to guess.d
It's also important to ensure that passwords are changed regularly. Ensure they're not reused across multiple accounts.
Install Intrusion Prevention & Detection Systems
Intrusion prevention and detection systems detect and prevent malicious activity on your network.
These systems can be subject to use to identify and block potential threats. For example, such as denial-of-service attacks and malware infections. By installing an IDS/IPS system, you can help reduce the impact of potential cyber-attacks.
Develop & Test Disaster Recovery Plans
Disaster recovery plans designs help organizations recover from major disruptions. For example, natural disasters or cyber-attacks.
These plans should develop in advance and tested regularly. By having a well-tested disaster recovery plan in place, you can minimize the downtime and disruption caused by an incident.
Conduct Regular Security Training for Employees
Employees are often the weakest link in an organization's security. This is why it's important to conduct regular security training for all employees. These trainings should cover topics such as proper password usage, email safety and social engineering attacks.
Educating your employees about security risks is great. You can help reduce the likelihood of a successful attack.
How Are Vulnerabilities Discovered?
Vulnerabilities can be subject to discovery in several ways. These include network scanning, code analysis, and manual testing.
By using these methods, you can identify potential security risks. And by consequence, take steps to mitigate them.
Network Scanning
Network scanning is the process of identifying systems and devices on a network.
One can do this using a variety of tools, including port scanners and vulnerability scanners. By scanning your network, you can identify potential security risks and take steps to mitigate them.
Code Analysis
Code analysis is the process of reviewing source code for potential security risks. One can do this manually or using automated tools.
By analyzing code, you can identify potential security holes that hackers could exploit.
Manual Testing
Manual testing is the process of manually testing systems. It also applies to applications for security risks.
One can do this by running tests against known vulnerabilities. You can also try to exploit vulnerabilities.
By conducting manual testing, you can identify potential security risks. Thus, you can take steps to mitigate them.
| Related Reading: Vulnerability Scanning: Here's Everything You Should Know |
How Are Vulnerabilities Assessed?
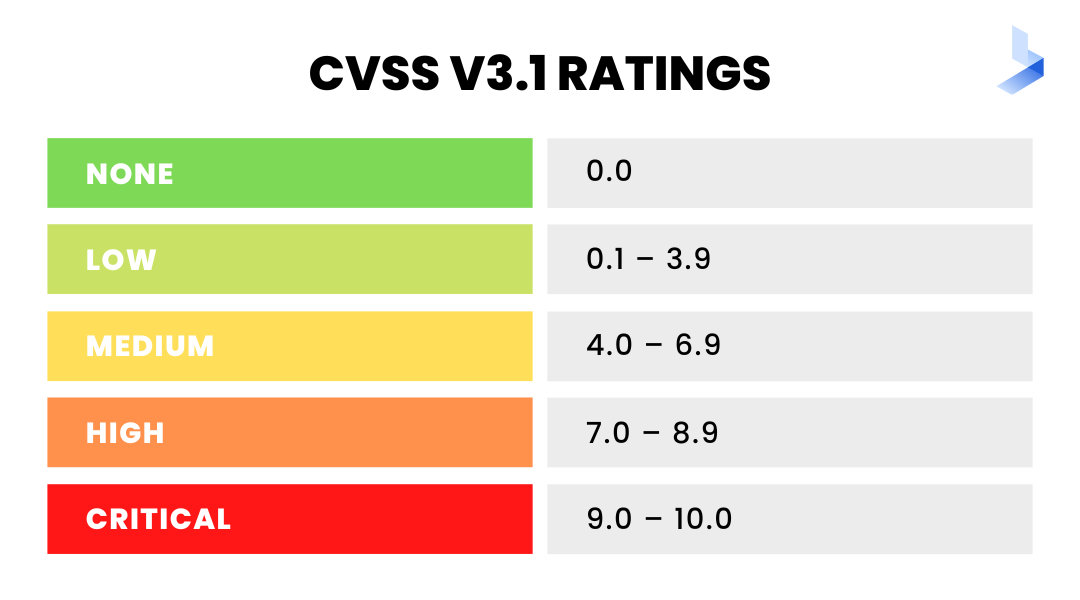
Once vulnerabilities are discovered, they must be assessed to determine the risk severity. This assessment is typically done using a scoring system. For instance, the Common Vulnerability Scoring System (CVSS).
The CVSS is a numeric score that ranges from 0-100. The higher scores indicate greater severity. After a vulnerability you've scored, it's often classified as low, medium, or high risk.
Low-risk vulnerabilities are typically those that can be easily mitigated. They have little impact on an organization.
Medium-risk vulnerabilities are those that may require more effort to mitigate. They could still have a significant impact on an organization.
High-risk vulnerabilities are those that are difficult to mitigate. They could have a catastrophic impact on an organization.
Once vulnerabilities you've scored and classified, they can be prioritized for remediation.
This is typically done by sorting vulnerabilities from highest to lowest risk. By prioritizing vulnerabilities, you can ensure that the most critical risks go addressed.
How Are They Remediated?
There are a variety of methods that can be subject to use to remediate vulnerabilities. The most common method is to apply security patches.
Software vendors typically release security patches to address known vulnerabilities. By applying patches, you can close the security holes that hackers may exploit.
In some cases, it's not possible to apply a patch, or there is no patch available. In these cases, other mitigation measures must be taken to reduce the risk posed.
These mitigation measures may include disabling features or services. It might also cover restricting access or implementing workarounds. By taking these measures, you can help reduce the likelihood of a successful attack.
Furthermore, it's important to remember that vulnerabilities can't always be completely remediated. In some cases, the only way to eliminate a vulnerability is to replace the affected system.
However, this isn't always practical or feasible. As such, it's important to focus on reducing the risk posed by vulnerabilities. This occurs rather than trying to eliminate them entirely.
Should Remediation Be Verified?
After vulnerabilities you've remediated, it's important to verify the mitigation is effective. One can do this by conducting a new scan of the system or application.
If the vulnerability is still present, then additional steps may need to be taken to mitigate it. By verifying that remediation efforts are effective, you can ensure that your systems are secure.
How to Integrate a Vulnerability Management Process In Your Enterprise
Now you understand what vulnerability management is and how it works. But, you may be wondering how to integrate it into your organization.
The first step is to assess your current security posture. This will help you identify where your weaknesses are and what needs to be improved.
Outline Your Objectives
After you've assessed your current security posture, you'll need to define your objectives. What are you trying to achieve with your vulnerability management program?
Do you want to reduce the number of vulnerabilities? Do you want to improve your patch management process? By outlining your objectives, you can ensure that your program focuses up.
Outline Organizational Roles and Responsibilities
Another important step is to outline the roles and responsibilities of each team. Who will be responsible for conducting scans?
Who will be responsible for patching systems? By defining these roles and responsibilities, you can ensure everyone knows their part.
Develop Standard Operating Procedures
Once you've defined objectives and responsibilities, you'll need to develop operating procedures. These procedures should outline the steps that need to be taken to remediate.
By having standard operating procedures, you can ensure everyone is following the process. This ensures vulnerabilities are being properly addressed.
Implement Automation Tools And Techniques
To effectively manage vulnerabilities, it's important to implement automation tools and techniques.
Automation can speed up the process of conducting scans and applying patches. By automating these tasks, you can free up your team's time so that they can focus on more important tasks.
How to Choose the Right Vulnerability Management Solution: What Should It Have?
Now that you understand what vulnerability management is, you're progressing. Knowing to integrate into the organization, you wonder how to choose the right solution. There are a few important factors to consider when choosing vulnerability management.
First, you must ensure that the solution can be easily integrated. It must be compatible with your existing security infrastructure.
If the solution isn't compatible with your systems, it will likely cause more problems. Make sure to check compatibility before making a purchase.
Second, you need to make sure that the solution offers comprehensive coverage. It should be able to scan for vulnerabilities across your systems and applications. Otherwise, you'll likely miss critical vulnerabilities.
Third, you must ensure that the solution is easy to use. It should have a user-friendly interface so that you can easily conduct scans. If the solution is too complicated, then your team will likely never use it.
Finally, you need to make sure that the solution is affordable. Vulnerability management solutions can be very expensive.
You'll need to make sure that it fits within your budget. Otherwise, you'll likely never be able to justify the cost.
By considering this, you can ensure you choose the right vulnerability management solution.
Common Mistakes Made With Vulnerability Management
Now you know what to look for in a vulnerability management solution. However, you need to be aware of the common mistakes that are made.
One of the most common mistakes is failing to conduct regular scans.
Vulnerabilities can pop up at any time. So it is important to scan your systems for potential issues regularly. If you only scan periodically, then you're likely to miss critical vulnerabilities.
Another common mistake is failing to patch systems promptly. Once a vulnerability is identified, it's important to apply patches early. Otherwise, attackers may be able to exploit the vulnerability before it's patched.
Finally, another common mistake is failing to train employees properly. They must know how to use the vulnerability management solution.
If your employees don't know how to use the program, then it's likely that they'll never use it. Make sure to provide adequate training so that everyone knows how to use the program.
By avoiding common mistakes, you can ensure your organization's vulnerability management is successful.
Vulnerability Management Done Right
Vulnerability management is a critical part of any organization's security posture. By understanding what it is, you can ensure your organization can manage vulnerabilities.
By implementing the right tools and processes, you can reduce vulnerabilities. Thus, improve your overall security posture. With vulnerability management, you can keep your organization safe from potential threats.
Looking for more information on vulnerability management and how it can help? Get in touch with us, and we will set you up with the best possible solution for you.
