What to Expect When Working with BitLyft Cybersecurity
 By
Emily Miller
·
3 minute read
By
Emily Miller
·
3 minute read
Sifting through cybersecurity companies can be a challenging experience. From cost planning and vendor selection, to figuring out which solution is right for your organization, the entire process can become quite lengthy.
Whether you’ve been on the hunt for managed detection and response for a few years or a few months, you probably know that there’s no shortage of options.
If you’re thinking about choosing BitLyft for MDR security, you’re probably wondering what you can expect when working with our team.
First of all, go ahead and practice taking a few deep breaths. When you form a partnership with BitLyft, you can breathe a little easier knowing that we are on your side. No more fighting those cyber battles alone. With that said, here’s a quick overview of what you can expect when working with our team, starting with the onboarding process.
BitLyft Cybersecurity Onboarding Process
- Step 1: Kickoff call
- Step 2: Implementation
- Step 3: Follow up call
- Step 4: Ticket completion
- Step 5: System overview
Step 1: Kickoff Call
Every new relationship at BitLyft begins with a kick off call. During this time, we’ll go over a few important items that will help us better understand your network like log sources, firewalls, and installation agents.
It’s a pretty comprehensive list, but don’t worry, we’ll send it to you ahead of time.
Step 2: Implementation
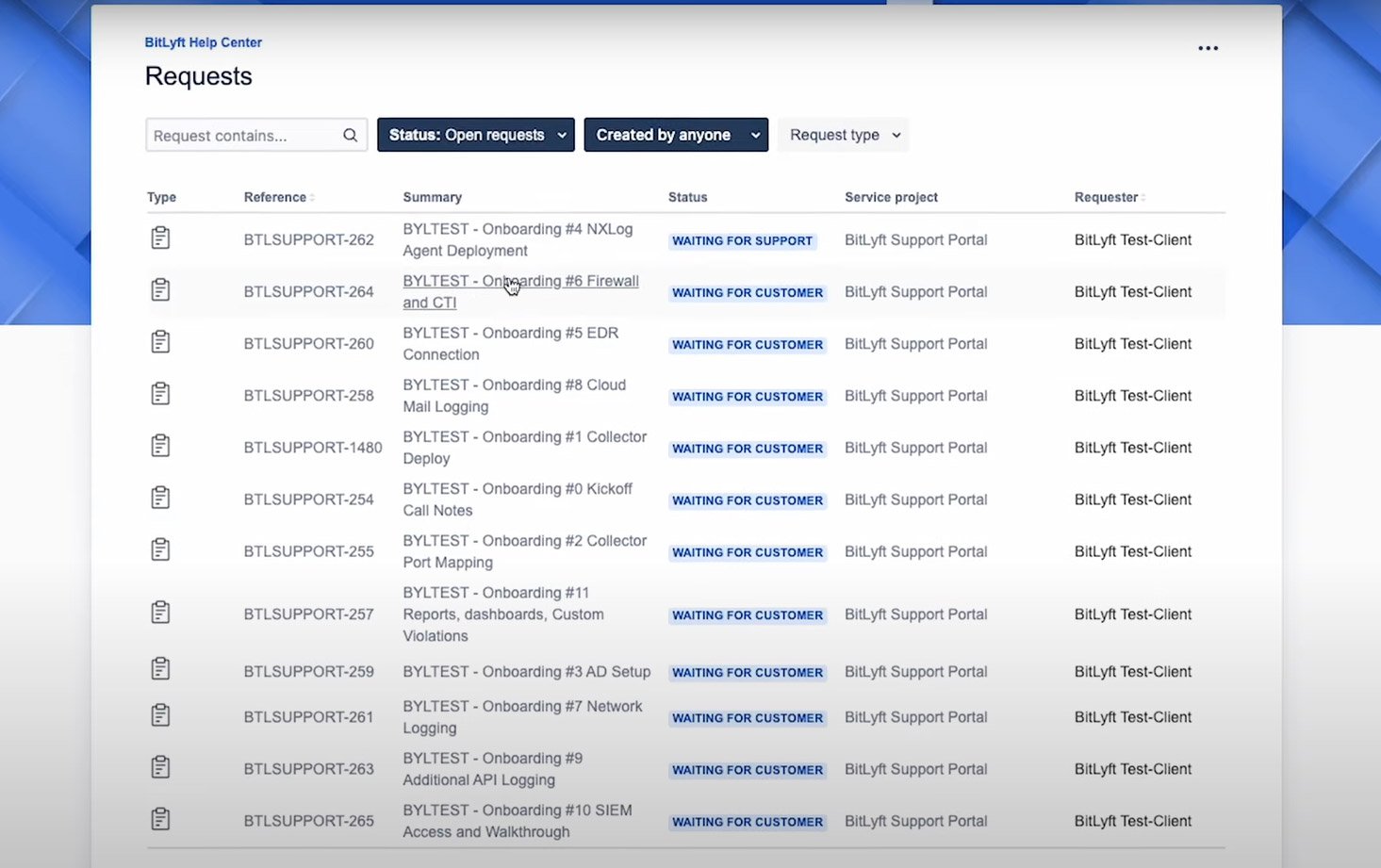
Once our team has collected all the necessary data, it’s time for implementation.
As we begin to understand your environment, our team will start adding tasks to your plate. These tasks are given a priority, and will need to be completed in that order.
Step 3: Follow Up Call
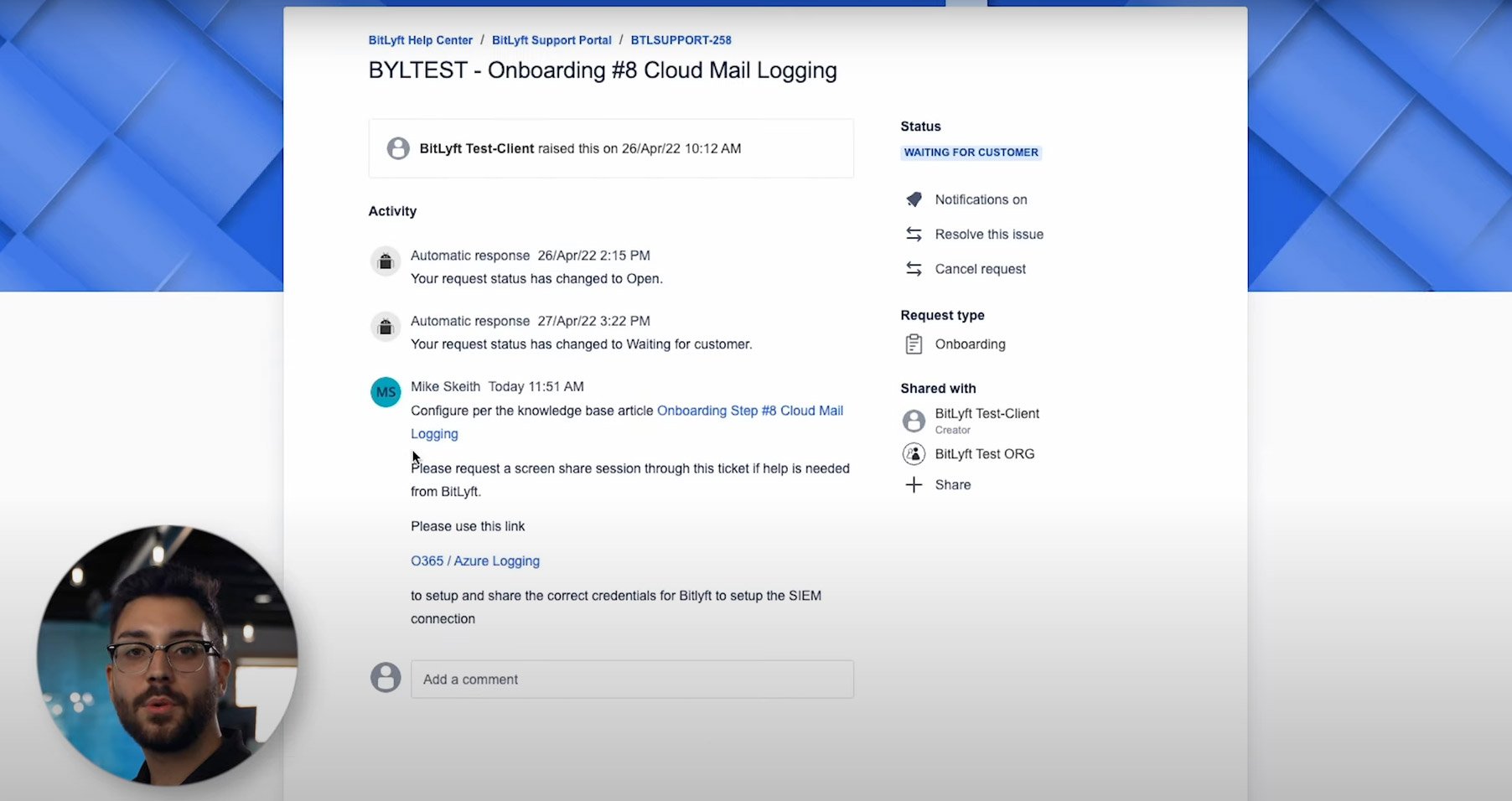
After our team has created the tickets, we’ll follow up with another call to show what we’ve done.
In this example, tasks were created for bringing in cloud mail through Microsoft Office 365 and for endpoint detection and response logging—or EDR—with Cylance. We’ll not only go over all of these items, but we’ll also help familiarize your team with some of the features in the system. Like how to review threat policies or how to open an incident as opposed to a normal support ticket.
Finally, we’ll work toward gaining an understanding of your expectations and feedback for the system.
Step 4: Ticket Completion
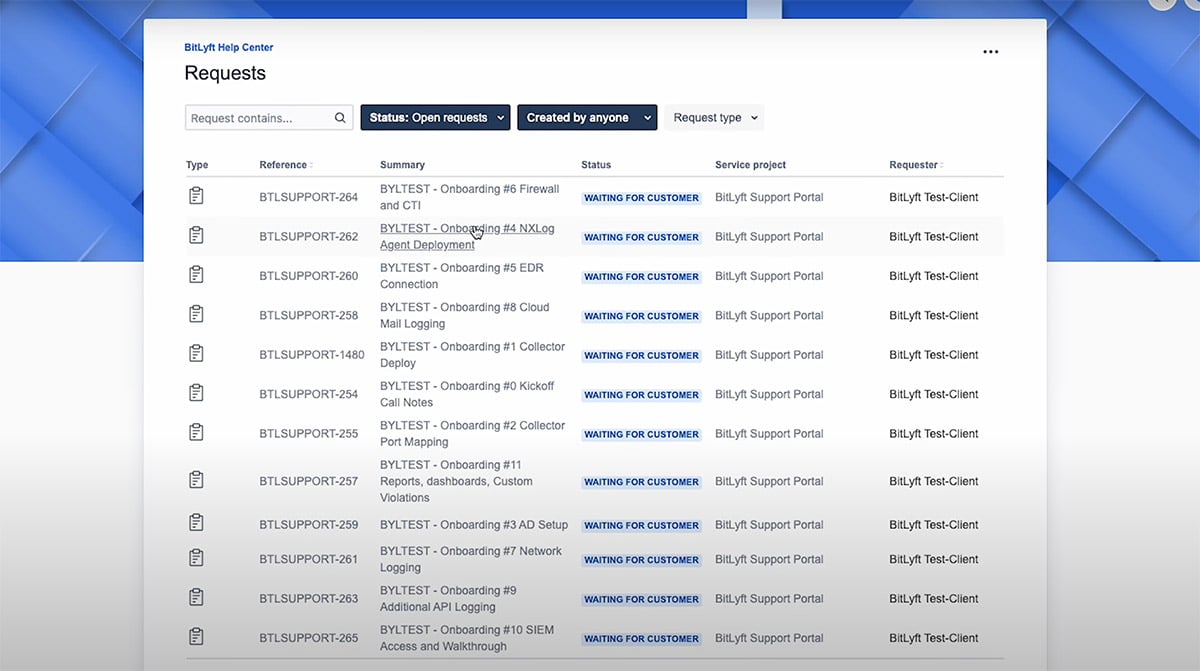
This is where the fun really begins. At this point, it’s time for you to log in to the portal and start setting it up.
Some items you’ll work on include, adding your information to the client communication ticket, adding inventory information for Microsoft NXlog agent, and adding your public IP to the firewall ticket.
Our team is always here to help throughout this process.
Step 5: System Overview
Finally, we’ll give you an overview of how everything is setup. We’ll teach you the best practices inside the portal like, which type of request to open at what time. How to understand and review the rules that are provided for you. And we’ll also explain what we’re monitoring. From this point forward, we’ll continue to update the tools and make adjustments to the system as necessary.
And that’s just the beginning of our relationship!
Frequently asked questions about working with BitLyft
At this point, you might be asking yourself one of these common questions. Like, what happens if we find something in your system? How do we respond when new threats emerge? Or maybe what does our relationship look like on a day to day basis?
Great questions.
What happens if we detect a threat in your system?
First of all, if we suspect something amiss in your network, you can be sure to hear from us. BitLyft utilizes a group messaging system and we’ll notify your team in accordance to the contact highest on your priority list. From then on, we’ll work with your team to further troubleshoot the issue.
How do we respond to emerging threats?
BitLyft AIR® utilizes managed detection and response to monitor your data 24/7 and we’re constantly working to stay on top of current trends. As we become aware of alerts and new threat intelligence, we are sure to implement these changes across all of our clients’ systems.

What does our relationship look like on a day to day basis?
Well, that’s completely up to you. We are here to help as much, or as little, as you want. We can either talk multiple times a week if that fits in your schedule, or we can just remain on call.
Keeping up with cyber threats is no easy task. And it’s definitely not something you should have to do alone. At BitLyft, we don’t just support your security team—we become a part of it. And if we’re not already, we hope to become a part of yours. If you’re ready to have your cybersecurity done for you, click on the link to get started.
