What is a SIEM and does my company need one?
SIEM, or Security Information and Event Management, solutions are a comprehensive collection of rules and technologies that provides detailed information on your IT infrastructure. It is designed to offer a view into the entirety of an organization’s security scope, including workflow, log management, and compliance. From growing small businesses to enterprise-level organizations, our reliance on a wider variety of IT systems is growing, and our security scope grows with it.

Let’s look at what SIEM tools provide, whether they might be right for your organization, and what you should look for when choosing one.
What does a SIEM provide?
SIEM solutions come in different shapes and sizes, suited to the needs of a diverse range of businesses. However, there are some commonalities among SIEMs, including:
- Event and log collection
- Dashboards and views of your organization’s entire security scope
- Field mapping or normalizing data into more readable forms for IT security purposes
- Correlating data to offer context and create relationships related to rules, architecture and alerts
- Adapting your IT security processes to a wide range of formats, types, compliance requirements, and changes
- Reporting and alerting
- Log management, often to ensure event logs are stored in a central location to make it easier for IT security staff to find and manage
There are more advanced SIEM solutions that also include user and entity behavior analytics (effective at spotting abnormal use of authorized accounts) and security orchestration and automated response (which helps you secure and react to potential risks much more quickly.)
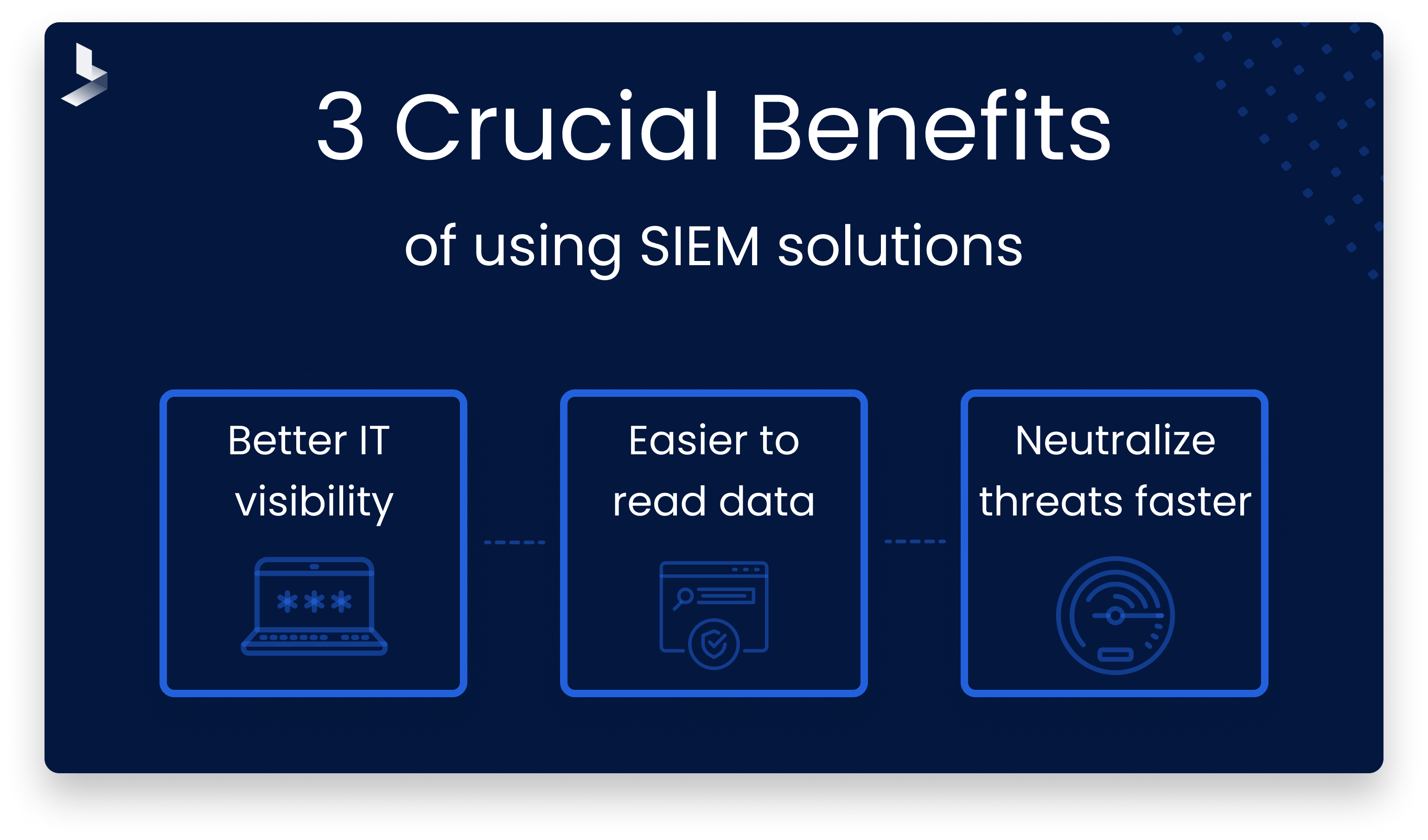
The following are some of the crucial benefits that your organization can enjoy as a result of implementing SIEM solutions.
3 Benefits of Using a SIEM Solution
They ensure better IT environment visibility
The log management capabilities offer much better visibility over your security scope through data aggregation. As an organization’s IT environment grows, a lot of that visibility can be lost as logs are buried in different apps, databases, devices, and SaaS solutions. These blind spots create an opportunity for hackers, since they are often unmonitored, and weaknesses are often neglected.
Security event information is retrieved from across your entire IT environment which gives you a centralized location for the data your team needs to act on potential risks. It can eliminate blind spots by making sure your team doesn’t have to check multiple different log sources and ensures malicious activities don’t remain concealed.
It makes your security data much easier to read
Just as logs and event data are generated across a host of different apps, devices, SaaS solutions, and so on, they are also likely to be created differently. They each produce plain text data which is generated, formatted, and sent in many different ways. As such, trying to find correlations between them or to make sense of them in the same context can take a tremendous amount of effort.
SIEM solutions collect and centralize data, they also ensure its normalized. This means that they reformat that data into whichever form best suits your IT security team. This helps you quickly correlate events from across different systems that can happen as a result of a security event.
They help you react quicker to potential threats
SIEM ensures that your IT security team has their finger on the pulse of different threat intelligence feeds. With threat detection and security alerting capabilities, your team can solve security events immediately. They can also begin implementing practices and technologies to protect you from threats that have yet to happen.
Furthermore, SIEM solutions are growing better at recognizing potential threats that often can’t be spotted by human effort alone. For instance, they can monitor abnormal activity that, in one part of your network, might not normally be strange but, across multiple parts of it, could be a sign of a security event. From there, your team is alerted, and can secure the environment, investigate the potential threat, and react much more quickly. Stopping cyber-attacks in real time isn’t easy but being alerted to them in real time gives you a much better chance of managing it.
Choosing the right SIEM solution for your organization
The range of benefits mentioned above cover only some of the advantages that SIEM solutions can offer your IT security team. Hopefully the examples above are enough to help you decide whether or not SIEM solutions are right for you AND which solutions work best for your needs. Here are a few factors that can help you determine what you need:
- Can it accommodate the number of systems, applications, and devices that fall under your security scope?
- Can it scale with both current systems and the projected growth or your scope?
- Is it compatible with your existing log systems?
- Do you have a need for forensic analysis capabilities?
- Do you have an additional need for advance features like entity behavior analytics (UEBA) or security orchestration and automated response (SOAR)?
- Do you prefer to have your SIEM solutions on premise on Cloud-based?
Addressing these questions can make it much easier to narrow down your SIEM options and to make sure your solutions provider matches your needs.
Is a SIEM solution right for you?
If your organization has a large security scope, including a range of devices, apps, SaaS solutions, and networks, or your scope is growing fast, then SIEM solutions is essential for helping your IT security team manage it all. You will be able to identify and react to security events much quicker, and even have the capability to protect better against newly identified threats that haven’t happened yet.
Our services aim to provide you with a simple no-nonsense solution to keep your business safe from online threats. If you’d like to learn more, don’t hesitate to get in touch with us today to speak to one of our friendly representatives.
We’ll help explain the managed detection and response services we offer and how they can be customized to your exact needs.